It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: ArMaP
a reply to: combatmaster
That would be a huge waste of resources, as there would be gathering information they will never look at.
But I'm sure they do that for certain countries, organisations and ISPs.
Even so, it is more efficient to simply gather everything, rather than waste resources specifically targeting what you want which is far more tedious and dynamic and is a bigger waste of resources in the long run!
originally posted by: Vasa Croe
So I have wondered for a while if everything typed into a social media app you are on is actually captured.
Even when you backspace or clear what you just typed....basically capturing in real time.
So regardless of if you were hot-headed for a second and then deleted what you were about to post.....it would still capture your initial response or message.
Does that make sense?
I don’t think that could be implemented on a forum like ATS, but it could definitely be coded into an app and part of the T&A that nobody reads.
Think about it....keyloggers are one of the oldest tricks in the book.....
Yes, makes perfect sense.
Typically, you would write an algorithm that monitors key words so you aren't copying too much data. Even if backspaced, it would record this data.
Or
Just keylog all of it and have the al gore rythyms go through it after....either way.
But, yes they do it, for research and other less noble reasons.
Look up AutoHotKey, you could write a simple one in minutes. This is for beginners.
edit on 1/10/2021 by MykeNukem because: sp.
originally posted by: More1ThanAny1
a reply to: chr0naut
I'm calling BS on the "every keystroke" part. This is testable and is not true.
Well, they have to with browsers all using HTTPS now.
I believe that the NSA would use mostly kernel level metadata collection on compliant operating systems with key escrow held by the NSA.
The metadata about how the data is submitted is more valuable than the data itself.
a reply to: chr0naut
I am an experienced kernel level driver developer for Windows. No matter what, that keystroke data would have to travel through the network stack and would be detectable. People would have found such a thing by now. I am only talking about on Windows of course.
However, I am not denying that if one were to be spied on by the government they couldn't flip a switch and do this. I am mostly saying its not on by default.
Also, keystroke data is useless if they can't identify the machine its coming from within a subnet. So the packets sent over the network would be larger and much more detectable than just sending single bytes per keystroke because it would require a unique identifier to go with it.
-
Regarding the "user is typing..." implementation. I was responsible for developing a similar feature and the most common way to do it is to not send every keystroke. Its more efficient to fire an event using a text box "onChange" trigger to tell the other user that the person is typing. That would then timeout after a few seconds if the user stopped typing. If they keep typing that timer is reset. So it's not tracking every keystroke.
I am an experienced kernel level driver developer for Windows. No matter what, that keystroke data would have to travel through the network stack and would be detectable. People would have found such a thing by now. I am only talking about on Windows of course.
However, I am not denying that if one were to be spied on by the government they couldn't flip a switch and do this. I am mostly saying its not on by default.
Also, keystroke data is useless if they can't identify the machine its coming from within a subnet. So the packets sent over the network would be larger and much more detectable than just sending single bytes per keystroke because it would require a unique identifier to go with it.
-
Regarding the "user is typing..." implementation. I was responsible for developing a similar feature and the most common way to do it is to not send every keystroke. Its more efficient to fire an event using a text box "onChange" trigger to tell the other user that the person is typing. That would then timeout after a few seconds if the user stopped typing. If they keep typing that timer is reset. So it's not tracking every keystroke.
edit on 10-1-2021 by More1ThanAny1 because: (no reason given)
originally posted by: chr0naut
originally posted by: More1ThanAny1
a reply to: chr0naut
I'm calling BS on the "every keystroke" part. This is testable and is not true.
Well, they have to with browsers all using HTTPS now.
I believe that the NSA would use mostly kernel level metadata collection on compliant operating systems with key escrow held by the NSA.
The metadata about how the data is submitted is more valuable than the data itself.
This reads like a techno-babble.
"Kernel level metadata" in most *nix platforms won't have anything of personally incriminating/identifiable value. It's mostly concerned about things like what kernel modules are loaded, drivers in use, memory layout and servicing hooks from applications in userland.
Not to mention, e.g. Linux kernel, is among the most audited/scrutinized source code on the planet Earth.
I do remember Snowden mentioning the criticality of "metadata" for the spooks, but my understanding is that this is in relation to tracking things like phone records, from party A to party B, what time it occurred and where the participants were when the call happened.
Nevertheless, you stumbled into a worthwhile point, which is that it pays to use open source software where every line of code is audited, vs. black box/walled garden OS that can do whatever they please with no recourse.
originally posted by: More1ThanAny1
Regarding the "user is typing..." implementation. I was responsible for developing a similar feature and the most common way to do it is to not send every keystroke. Its more efficient to fire an event using a text box "onChange" trigger to tell the other user that the person is typing. That would then timeout after a few seconds if the user stopped typing. If they keep typing that timer is reset. So it's not tracking every keystroke.
It doesn't need to track every keystroke, but it's possible.
originally posted by: More1ThanAny1
HTTPS requires both browsers and websites to handshake and utilize a public key to encrypt the data for transit.
Obviously.
But if the site doesn't use HTTPS the fact that the browser can use it is irrelevant.
originally posted by: SleeperHasAwakened
Nevertheless, you stumbled into a worthwhile point, which is that it pays to use open source software where every line of code is audited, vs. black box/walled garden OS that can do whatever they please with no recourse.
Even then, wasn't there a case of something related to networks, I think, that was found to have some kind of "flaw" that was there for many years and nobody noticed?
originally posted by: ArMaP
originally posted by: chr0naut
Well, they have to with browsers all using HTTPS now.
The sites, not the browsers.
Researchers link QWERTY keylogger code to NSA and Five Eye's Regin espionage malware - CSO/IDG Communications
originally posted by: More1ThanAny1
a reply to: chr0naut
I am an experienced kernel level driver developer for Windows. No matter what, that keystroke data would have to travel through the network stack and would be detectable. People would have found such a thing by now. I am only talking about on Windows of course.
However, I am not denying that if one were to be spied on by the government they couldn't flip a switch and do this. I am mostly saying its not on by default.
Also, keystroke data is useless if they can't identify the machine its coming from within a subnet. So the packets sent over the network would be larger and much more detectable than just sending single bytes per keystroke because it would require a unique identifier to go with it.
-
Regarding the "user is typing..." implementation. I was responsible for developing a similar feature and the most common way to do it is to not send every keystroke. Its more efficient to fire an event using a text box "onChange" trigger to tell the other user that the person is typing. That would then timeout after a few seconds if the user stopped typing. If they keep typing that timer is reset. So it's not tracking every keystroke.
It would make programmatic sense to buffer keystrokes and other metadata to produce a packet of sufficient size to encrypt and compress. It still would represent every keystroke sequence and timings.
This kind of metadata may also indicate the possibility of different typists using a common terminal, or of someone spoofing someone else's account.
The metadata is clearly vital to a prosecutable case.
edit on 10/1/2021 by chr0naut because: (no reason given)
originally posted by: SleeperHasAwakened
originally posted by: chr0naut
originally posted by: More1ThanAny1
a reply to: chr0naut
I'm calling BS on the "every keystroke" part. This is testable and is not true.
Well, they have to with browsers all using HTTPS now.
I believe that the NSA would use mostly kernel level metadata collection on compliant operating systems with key escrow held by the NSA.
The metadata about how the data is submitted is more valuable than the data itself.
This reads like a techno-babble.
"Kernel level metadata" in most *nix platforms won't have anything of personally incriminating/identifiable value. It's mostly concerned about things like what kernel modules are loaded, drivers in use, memory layout and servicing hooks from applications in userland.
Not to mention, e.g. Linux kernel, is among the most audited/scrutinized source code on the planet Earth.
I do remember Snowden mentioning the criticality of "metadata" for the spooks, but my understanding is that this is in relation to tracking things like phone records, from party A to party B, what time it occurred and where the participants were when the call happened.
Nevertheless, you stumbled into a worthwhile point, which is that it pays to use open source software where every line of code is audited, vs. black box/walled garden OS that can do whatever they please with no recourse.
The kernel code of open-source operating systems is definitely well scrutinized but there also is exploit code that talks to and intercepts standard I/O. On an open-source OS, these sorts of interceptions are trivial.
I once worked on a mouse 'driver' that utilized just such I/O interception to add features like additional buttons and mouse wheels for a generic cheaply manufactured mouse and that used a completely separate open-source driver for actual I/O directly to the mouse chipset (which is quite limited in the information it can buffer and transmit).
edit on 10/1/2021 by chr0naut because: (no reason given)
originally posted by: More1ThanAny1
a reply to: ArMaP
HTTPS requires both browsers and websites to handshake and utilize a public key to encrypt the data for transit.
Which is why, for ease of access to the unencrypted data, the three-letter agencies must get in either before, or after, or both before and after, encryption.
Encrypted data transmission is a pain to those who would bulk collect. However, they have workarounds.
Why did you bail on Twitter? I was never a fan myself, though I remember reading some astronaut tweets from the ISS. But in general it seemed like a stunted form of communication.
originally posted by: MotherMayEye
a reply to: Vasa Croe
I followed you on Twitter, I don't now if you knew that or not. I am wondering if you bailed? I did on Wednesday afternoon.
I did a Tweet delete before I left. I am sure SM captures everything they can capture....including keylogging.
Thanks to Edward Snowden, we know how they get around the https encryption, on the slide with the famous smiley face, or should I say infamous?
originally posted by: chr0naut
Which is why, for ease of access to the unencrypted data, the three-letter agencies must get in either before, or after, or both before and after, encryption.
Leaked Slide Shows NSA Celebrated Victory Over Google's Security With A Smiley Face
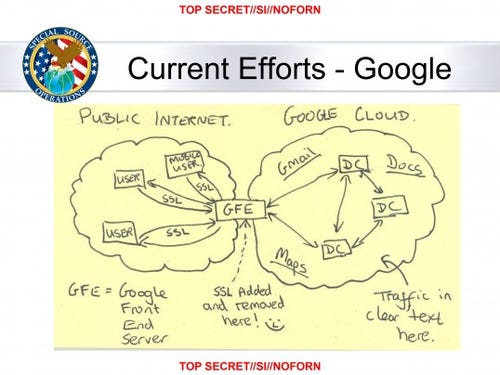
originally posted by: Arbitrageur
Why did you bail on Twitter? I was never a fan myself, though I remember reading some astronaut tweets from the ISS. But in general it seemed like a stunted form of communication.
It made my skin crawl to be on Twitter during the staged storming of the Capitol. I knew the censorship was coming but what happened after I left was way beyond what I expected.
I'm on TG now...it's so cozy. A group of us left. We still go to read some tweets offline but I can see some content that makes me sick. People celebrating the censorship feeling righteous about it...calling for more censorship and the crushing of any new platforms.
But I have noticed the occasional Trump hater that is aghast. Not many though. The content is sketchy on the Left anyway....stuff like this goes on:
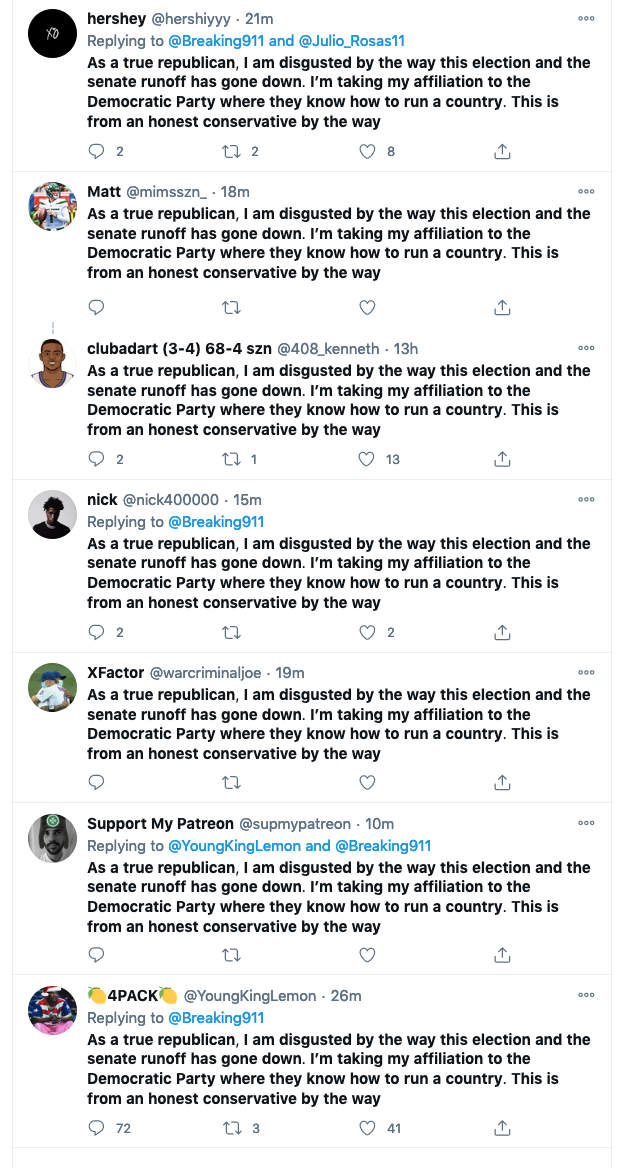
They fake being conservatives and they did it at the Capitol, too.
I have a few other quote searches that yield copy and paste bot users. For every Biden supporter on Twitter...there are 10 frauds.
a reply to: MotherMayEye
Silly games in that screenshot, I don't see how anybody on the left or on the right can take such an obvious "copy pasta" seriously. Thanks for explaining why you bailed.
Silly games in that screenshot, I don't see how anybody on the left or on the right can take such an obvious "copy pasta" seriously. Thanks for explaining why you bailed.
new topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 4 hours ago -
Maestro Benedetto
Literature: 6 hours ago -
Is AI Better Than the Hollywood Elite?
Movies: 6 hours ago -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 9 hours ago -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 10 hours ago -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 10 hours ago -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum: 11 hours ago
top topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 4 hours ago, 26 flags -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 15 hours ago, 9 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 15 hours ago, 8 flags -
Weinstein's conviction overturned
Mainstream News: 14 hours ago, 8 flags -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 10 hours ago, 8 flags -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 12 hours ago, 7 flags -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 9 hours ago, 6 flags -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 12 hours ago, 5 flags -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 10 hours ago, 4 flags -
Is AI Better Than the Hollywood Elite?
Movies: 6 hours ago, 3 flags
active topics
-
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics • 90 • : Lumenari -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs • 12 • : KrustyKrab -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues • 28 • : firerescue -
SHORT STORY WRITERS CONTEST -- April 2024 -- TIME -- TIME2024
Short Stories • 23 • : DontTreadOnMe -
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies • 16 • : Astyanax -
Truth Social goes public, be careful not to lose your money
Mainstream News • 130 • : Astyanax -
Is AI Better Than the Hollywood Elite?
Movies • 13 • : Justoneman -
Hate makes for strange bedfellows
US Political Madness • 47 • : 19Bones79 -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 689 • : daskakik -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 265 • : Astrocometus


