It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
We've had reports that some members were getting anti-virus alarms for two possible old Windows exploits--
WMF exploits
Java virtual machine (JVM) exploits
In both cases, these are rather old trojans/virus that have minimal known damage potential, and anyone with an updated Windows operating system will be fine. However, many virus alert systems will still warn you of the presence of these two.
It appears (based on the information we have for now) that one of our ad networks has an infected 728x90 "leaderboard" ad. These appear at the top and bottom of every page. We've disabled these ads until we can engage in a little better research as to what is the cause.
If you still encounter virus alerts, please let us know through the complain form.
Thank you.
WMF exploits
Java virtual machine (JVM) exploits
In both cases, these are rather old trojans/virus that have minimal known damage potential, and anyone with an updated Windows operating system will be fine. However, many virus alert systems will still warn you of the presence of these two.
It appears (based on the information we have for now) that one of our ad networks has an infected 728x90 "leaderboard" ad. These appear at the top and bottom of every page. We've disabled these ads until we can engage in a little better research as to what is the cause.
If you still encounter virus alerts, please let us know through the complain form.
Thank you.
On other item...
Any members who feel capable of helping to track down the offending advertiser and ad, please let myself or Springer know.
Thanks.
Any members who feel capable of helping to track down the offending advertiser and ad, please let myself or Springer know.
Thanks.
Wow, I didnt know that this was around, thatnks for telling us. I use windows 98, Am i at a higher risk than other members?
I got those picked up this morning and last night. I'll check my logs to see if I can find anyhting.
4FEFMNUX\exp[1]windowsmetafile In my temporary Internet files caused one instance.
[edit on 13-8-2006 by Kellter]
[edit on 13-8-2006 by Kellter]
4FEFMNUX\exp[1]windowsmetafile
0LUV2J01\exp[1]windowsmetafile
Bth of these were blocked also for bloodhound exploit 56.
The word windowsmetafile is actually wmf, code is posting entired word for aome reason.
[edit on 13-8-2006 by Kellter]
[edit on 13-8-2006 by Kellter]
0LUV2J01\exp[1]windowsmetafile
Bth of these were blocked also for bloodhound exploit 56.
The word windowsmetafile is actually wmf, code is posting entired word for aome reason.
[edit on 13-8-2006 by Kellter]
[edit on 13-8-2006 by Kellter]
Yep, I've come across it too. I'll check through my logs and see what I had found. I didn't know if it was from an ATS ad or not as I had a bunch
of windows open. But it was a WMF file and at least that is now explained. I'll keep an eye out and thank you for letting us know it was coming from
an advert here.
I had that happen, too. McAfee took care of it for me, so no big deal. I also wasn't sure that it was related to this site.
I got another one just a while ago and was going to send a u2u but I see you are looking into it, so
Is there perhaps something from my AntiVirus logs or IE Cache that would help you guys track it down? I don't know if it helps but it started last night.
Is there perhaps something from my AntiVirus logs or IE Cache that would help you guys track it down? I don't know if it helps but it started last night.
The best thing we can do is find the actual ad banner and agency its coming from.
A URL would be ideal.
IE (Right Click -> Properties -> Address)
IE (Right Click -> Copy Shortcut)
A URL would be ideal.
IE (Right Click -> Properties -> Address)
IE (Right Click -> Copy Shortcut)
I got hit with it twice yesterday.
Both times it was Bloodhound.Exploit.56
My Norton notified me that the file couldn't be repaired and that access was denied.
Temporary Internet Files/Content.IE5\6BOND672\exp[1]windowsmetafile
Couldn't get a url on it but was able to find out that expected damage was low and it's supposed to be easy to get rid of.
Here's a copy of what it said.
Bloodhound.Exploit.56Risk Level 1: Very LowPrinter Friendly Page
SUMMARY TECHNICAL DETAILS Discovered: December 27, 2005
Updated: February 10, 2006 02:47:15 PM ZW3
Type: Trojan Horse, Worm
Systems Affected: Windows 2000, Windows 95, Windows 98, Windows Me, Windows Server 2003, Windows XP
Bloodhound.Exploit.56 is a heuristic detection for the Microsoft Windows Graphics Rendering Engine WMF Format Unspecified Code Execution Vulnerability (as described in Microsoft Security Bulletin MS06-001).
Note: Bloodhound.Exploit.56 is designed to identify behavior that would occur if the Microsoft Windows Graphics Rendering Engine WMF Format Unspecified Code Execution Vulnerability (as described in Microsoft Security Bulletin MS06-001) is exploited. As Symantec becomes aware of changes to the exploit code, or if files are identified that trigger this detection but are not malicious, the detection is refined. It is important to keep your definitions up to date to ensure the most complete protection.
Behavior
Symptoms
Transmission
ProtectionVirus Definitions (LiveUpdate™ Weekly) December 28, 2005
Virus Definitions (Intelligent Updater) December 28, 2005
Threat AssesmentWildWild Level: Low
Number of Infections: 0 - 49
Number of Sites: 0 - 2
Geographical Distribution: Low
Threat Containment: Easy
Removal: Easy
DamageDamage Level: Low
DistributionDistribution Level: Low
This is what I found looking under properties.
HyperText Protocol
type- HTML Document
connection- Not Encrypted.
.
Both times it was Bloodhound.Exploit.56
My Norton notified me that the file couldn't be repaired and that access was denied.
Temporary Internet Files/Content.IE5\6BOND672\exp[1]windowsmetafile
Couldn't get a url on it but was able to find out that expected damage was low and it's supposed to be easy to get rid of.
Here's a copy of what it said.
Bloodhound.Exploit.56Risk Level 1: Very LowPrinter Friendly Page
SUMMARY TECHNICAL DETAILS Discovered: December 27, 2005
Updated: February 10, 2006 02:47:15 PM ZW3
Type: Trojan Horse, Worm
Systems Affected: Windows 2000, Windows 95, Windows 98, Windows Me, Windows Server 2003, Windows XP
Bloodhound.Exploit.56 is a heuristic detection for the Microsoft Windows Graphics Rendering Engine WMF Format Unspecified Code Execution Vulnerability (as described in Microsoft Security Bulletin MS06-001).
Note: Bloodhound.Exploit.56 is designed to identify behavior that would occur if the Microsoft Windows Graphics Rendering Engine WMF Format Unspecified Code Execution Vulnerability (as described in Microsoft Security Bulletin MS06-001) is exploited. As Symantec becomes aware of changes to the exploit code, or if files are identified that trigger this detection but are not malicious, the detection is refined. It is important to keep your definitions up to date to ensure the most complete protection.
Behavior
Symptoms
Transmission
ProtectionVirus Definitions (LiveUpdate™ Weekly) December 28, 2005
Virus Definitions (Intelligent Updater) December 28, 2005
Threat AssesmentWildWild Level: Low
Number of Infections: 0 - 49
Number of Sites: 0 - 2
Geographical Distribution: Low
Threat Containment: Easy
Removal: Easy
DamageDamage Level: Low
DistributionDistribution Level: Low
This is what I found looking under properties.
HyperText Protocol
type- HTML Document
connection- Not Encrypted.
.
I got a screenshot of the virus alert on the page I got it from, does this help?
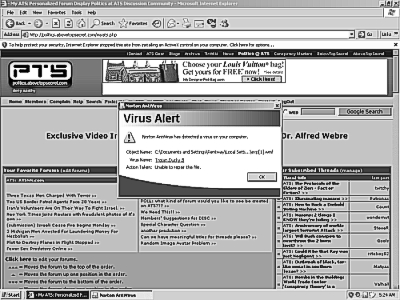
I have a high res color copy of it as well if you guys need it.
Nice to see you posting Simon, I thought you were a myth
[edit on 13-8-2006 by twitchy]

I have a high res color copy of it as well if you guys need it.
Nice to see you posting Simon, I thought you were a myth
[edit on 13-8-2006 by twitchy]
Originally posted by twitchy
Nice to see you posting Simon, I thought you were a myth
I tend to hide in the Area 51/Facilities forum...
Secure, Disclosed Location
It's the only forum with the necessary cryogenic and hyperbaric facilities.
Meanwhile, though it's irritating as hell to see something like this come to ATS in such a fashion, I just want to remind all members that it's always a good idea to keep your operating system updated regardless of what else may be going on.
Current, up-to-date and fully patched versions of Windows XP are not vulnerable to this exploit, and I believe that is true of most other versions.
So if you haven't already, I recommend visiting update.microsoft.com... and making sure your copy of Windows is up to date -- just in case.
Originally posted by SimonGray
I tend to hide in the Area 51/Facilities forum...
It's the only forum with the necessary cryogenic and hyperbaric facilities.
Meanwhile, though it's irritating as hell to see something like this come to ATS in such a fashion, I just want to remind all members that it's always a good idea to keep your operating system updated regardless of what else may be going on.
Current, up-to-date and fully patched versions of Windows XP are not vulnerable to this exploit, and I believe that is true of most other versions.
So if you haven't already, I recommend visiting update.microsoft.com... and making sure your copy of Windows is up to date -- just in case.
When I click on the AD link for www.alltheufoanswers.com I get an error message and it shuts down and closes all the sessions I had open.
I tried it on my home PC and 3 differant PCs at work. Get the same error message and same problems on all 4 PCs.
Anyone else having problems like this?
I tried it on my home PC and 3 differant PCs at work. Get the same error message and same problems on all 4 PCs.
Anyone else having problems like this?
FWIW, yesterday I was on here and FireFox decided it was going to download a WMF. I canceled it, but it struck me as really odd since it wasn't from
clicking a link or anything. The IP address I got from it was 64.34.181.51, and running a tracert on it told me the IP address was for
server2.searchplain.com. I tried going to both server2.searchplain.com and searchplain.com (without server2), and all I got was a plank page, no 404
or anything.
Don't know if it's relevant or anything, hope it helps somehow though.
Don't know if it's relevant or anything, hope it helps somehow though.
Thanks for the info...
It did not occur to me to report the specific ads I had at each of those events.
I'll be sure to check next time if it happens yet again.
It did not occur to me to report the specific ads I had at each of those events.
I'll be sure to check next time if it happens yet again.
I got a PUP from the ad that had the guy jumping out in front of the bus, I think it was a video site.
new topics
-
Russia police launch major manhunt after troops massacred by comrade in occupied Ukraine
Other Current Events: 2 hours ago -
Chinese scientists create new mutant Ebola strain with horror eye symptoms
Breaking Alternative News: 3 hours ago -
Maclemore - Hind's Hall (Pro-Palestine protest song)
Music: 3 hours ago -
Social Security projected to cut benefits in 2035 barring a fix
Global Meltdown: 5 hours ago -
Trump supporters training in the HILLS!!!!
US Political Madness: 6 hours ago -
Is the move to greenwashing solar and wind power set up for money laundering.
The Gray Area: 6 hours ago -
LIVE: Putin inauguration ceremony
Regional Politics: 8 hours ago -
Black kids in the Bronx don't know what the word 'computer' is
People: 9 hours ago
top topics
-
Trump supporters training in the HILLS!!!!
US Political Madness: 6 hours ago, 14 flags -
Black kids in the Bronx don't know what the word 'computer' is
People: 9 hours ago, 8 flags -
This is what it is all about
US Political Madness: 12 hours ago, 7 flags -
Chinese scientists create new mutant Ebola strain with horror eye symptoms
Breaking Alternative News: 3 hours ago, 5 flags -
Social Security projected to cut benefits in 2035 barring a fix
Global Meltdown: 5 hours ago, 4 flags -
Russia police launch major manhunt after troops massacred by comrade in occupied Ukraine
Other Current Events: 2 hours ago, 4 flags -
LIVE: Putin inauguration ceremony
Regional Politics: 8 hours ago, 3 flags -
Is the move to greenwashing solar and wind power set up for money laundering.
The Gray Area: 6 hours ago, 2 flags -
Aliens and Las Vegas
Aliens and UFOs: 12 hours ago, 1 flags -
Maclemore - Hind's Hall (Pro-Palestine protest song)
Music: 3 hours ago, 0 flags
active topics
-
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 1360 • : Threadbarer -
Trump supporters training in the HILLS!!!!
US Political Madness • 49 • : RazorV66 -
Israeli strikes on southern Gaza city of Rafah kill 22, mostly children, as US advances aid package
Middle East Issues • 163 • : ToneD -
Breaking--Hamas Accepts New Cease Fire
Middle East Issues • 228 • : KrustyKrab -
Is the move to greenwashing solar and wind power set up for money laundering.
The Gray Area • 6 • : TimBurr -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 851 • : fringeofthefringe -
The Reactionary Conspiracy 13. The plot’s theology.
General Conspiracies • 169 • : Ohanka -
Russia police launch major manhunt after troops massacred by comrade in occupied Ukraine
Other Current Events • 9 • : grey580 -
The Dark Pyramid of Alaska and the Why Files take on the subject
Whistle Blowers and Leaked Documents • 26 • : SprocketUK -
SC Jack Smith is Using Subterfuge Tricks with Donald Trumps Upcoming Documents Trial.
Dissecting Disinformation • 132 • : WeMustCare

