It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
I find this whole thing very suspicious and my gut tells me this guy was taken out, but I have also seen some stuff said by people who feel the same
way that really hurt our arguments.
For example, the speed. Several people have said it's impossible to get up to 100mph on that road. Pure, unmitigated bull. Spewing this bull makes us look like paranoid idiots when we say this guy was killed. I've done 100MPH on a road in my city that is much smaller and tighter than the road this guy died on. It's a 30-35mph road depending on what section you are on, it changes between a 30-35MPH speed limit. There are only two lanes of traffic going each way. There are frequently changing traffic lights every block or two. It's a very busy road that sees tons of traffic. I did this in a car much more crappy than the mercedes he had, and I did it around 3Pm in the afternoon. Got it past 100 then slowed back down, I never was close to hitting anybody or getting hit. I got lucky. Tons of people get lucking doing things like that. To say that it's impossible, or even unlikely that he could have been going that fast is just stupid. There is absolutely nothing stopping him from going that fast on that road, other than fear and morals. So yes he could have been going that fast, stop saying he couldn't have.
Second, people keep saying there is no way the motor and everything would be ejected from the car. More crap. It seems we have a lot of people who know absolutely nothing about automotive issues who are forming opinions and ideas based on nothing but their own piss poor understanding of automobiles and auto crashes. If you know nothing about cars, you have no legitimate reason to say "that couldn't have happened" Cars are incredibly fragile things at those speeds. An engine is still a mostly solid block of metal, and is the part of a car build more robust and stronger than anything else.
The only reason I brought this up, is because I truly believe he WAS killed. But when people try to prove he was killed by using examples that are totally ridiculous and just not true then you ruin our credibility. We all look like ignorant fools when someone says something that's obviously not true for anyone that actually knows what they are talking about.
Now we have people suggesting that there are multiple locations and multiple cars involved. Based on their apparent lack of ability to understand the word "perspective" Which since they don't know, means things look different at different angles. Demonstrating ignorance of this basic fact that even 5 year olds understand is again making us all look stupid.
Whether this is all being caused by shills attempting to ruin the credibility of us who DO believe he was killed by making us look foolish, or if it's just overly enthusiastic conspiracy theorist with good intentions at heart I do not know, either way I don't like it.
For example, the speed. Several people have said it's impossible to get up to 100mph on that road. Pure, unmitigated bull. Spewing this bull makes us look like paranoid idiots when we say this guy was killed. I've done 100MPH on a road in my city that is much smaller and tighter than the road this guy died on. It's a 30-35mph road depending on what section you are on, it changes between a 30-35MPH speed limit. There are only two lanes of traffic going each way. There are frequently changing traffic lights every block or two. It's a very busy road that sees tons of traffic. I did this in a car much more crappy than the mercedes he had, and I did it around 3Pm in the afternoon. Got it past 100 then slowed back down, I never was close to hitting anybody or getting hit. I got lucky. Tons of people get lucking doing things like that. To say that it's impossible, or even unlikely that he could have been going that fast is just stupid. There is absolutely nothing stopping him from going that fast on that road, other than fear and morals. So yes he could have been going that fast, stop saying he couldn't have.
Second, people keep saying there is no way the motor and everything would be ejected from the car. More crap. It seems we have a lot of people who know absolutely nothing about automotive issues who are forming opinions and ideas based on nothing but their own piss poor understanding of automobiles and auto crashes. If you know nothing about cars, you have no legitimate reason to say "that couldn't have happened" Cars are incredibly fragile things at those speeds. An engine is still a mostly solid block of metal, and is the part of a car build more robust and stronger than anything else.
The only reason I brought this up, is because I truly believe he WAS killed. But when people try to prove he was killed by using examples that are totally ridiculous and just not true then you ruin our credibility. We all look like ignorant fools when someone says something that's obviously not true for anyone that actually knows what they are talking about.
Now we have people suggesting that there are multiple locations and multiple cars involved. Based on their apparent lack of ability to understand the word "perspective" Which since they don't know, means things look different at different angles. Demonstrating ignorance of this basic fact that even 5 year olds understand is again making us all look stupid.
Whether this is all being caused by shills attempting to ruin the credibility of us who DO believe he was killed by making us look foolish, or if it's just overly enthusiastic conspiracy theorist with good intentions at heart I do not know, either way I don't like it.
As for the potential bullet holes, it could very well be true. They sure look like bullet holes to me. And that's not coming from watching a lot of
movies, that's coming from someone who has plenty of experience shooting up cars with various firearms of varying calibers. I don't mean drive by
shootings, just having old junk cars available for target practice, figured I should say that so I don't get a knock at my door.
While it's possible they are bullet holes, it's equally as possible they are just damage from the explosion and/or crash. Unless they diagram every single bit of metal and know its trajectory that flew off the car (which is likely impossible) the possibility remains it was just some chunks of metal that shot out of the car during the explosion, the thin sheet metal on newer cars can be pierced pretty darn easily.
But, the fact that the holes appear to all be uniform size and shape tells me it's less likely for several pieces of shrapnel to make exit holes exactly the same spread over that area.
I immediately thought of something like a claymore taped to his gas tank or something like that. For those that don't know how people killing mines like claymores work, they basically are a huge shotgun. There is an explosive charge that propels hundreds of ball bearings in a directional manner.
If this was placed on the back of his gas tank, after being triggered it would turn the gas tank into swiss cheese, but probably still leave it attached and relatively intact. The ball bearings might be able to tear completely out of the vehicle and exit out of those visible holes. The ball bearings could have also made their way into the body of the driver, causing him to crash, or the explosion and resulting fire caused him to crash. This would be baked up by witnesses that claim it was on fire before crashing.
I want to be clear this claymore idea is just a thought exercise and by no means am I standing behind it as being what likely happened. There are issues with this explanation as well, the ball bearings in something like a claymore are pretty small, and I'm not sure if they would make the size of holes seen in the pics.
I also don't know of claymores launch the bbs with enough force to pass through that much of the car. It's a mine for killing people not destroying vehicles, but a civilian vehicle is pretty flimsy so it might be possible.
While it's possible they are bullet holes, it's equally as possible they are just damage from the explosion and/or crash. Unless they diagram every single bit of metal and know its trajectory that flew off the car (which is likely impossible) the possibility remains it was just some chunks of metal that shot out of the car during the explosion, the thin sheet metal on newer cars can be pierced pretty darn easily.
But, the fact that the holes appear to all be uniform size and shape tells me it's less likely for several pieces of shrapnel to make exit holes exactly the same spread over that area.
I immediately thought of something like a claymore taped to his gas tank or something like that. For those that don't know how people killing mines like claymores work, they basically are a huge shotgun. There is an explosive charge that propels hundreds of ball bearings in a directional manner.
If this was placed on the back of his gas tank, after being triggered it would turn the gas tank into swiss cheese, but probably still leave it attached and relatively intact. The ball bearings might be able to tear completely out of the vehicle and exit out of those visible holes. The ball bearings could have also made their way into the body of the driver, causing him to crash, or the explosion and resulting fire caused him to crash. This would be baked up by witnesses that claim it was on fire before crashing.
I want to be clear this claymore idea is just a thought exercise and by no means am I standing behind it as being what likely happened. There are issues with this explanation as well, the ball bearings in something like a claymore are pretty small, and I'm not sure if they would make the size of holes seen in the pics.
I also don't know of claymores launch the bbs with enough force to pass through that much of the car. It's a mine for killing people not destroying vehicles, but a civilian vehicle is pretty flimsy so it might be possible.
Originally posted by JBA2848
I am still wondering are these bullet holes? They don't seem to be for trim or any thing? They don't seem to be dented from hitting something?
edit on 24-6-2013 by JBA2848 because: (no reason given)
A few pages back I asked the same thing. In the video 2:58 minutes in it shows those holes. I just don't know what the holes are from. And the fact the driver's door is all mangled (yes, from 'the jaws of life', I get it) makes it difficult to examine them.
Being shot at would explain why he ran a stoplight and sped to 100 mph before crashing. If someone shot at me I would be stomping the pedal and flying down the street to get away.
reply to post by James1982
We're not suggesting the car was moved but we are questioning if it was possible. And, if so, why? Wondering if it's possible and saying that is what happened are two different statements.
I would be more mad at those who won't even consider the possibility that he was murdered without even questioning all the oddities.
We're not suggesting the car was moved but we are questioning if it was possible. And, if so, why? Wondering if it's possible and saying that is what happened are two different statements.
I would be more mad at those who won't even consider the possibility that he was murdered without even questioning all the oddities.
reply to post by WanDash
Um...NO
How does showing me 2 photos taken from 2 different locations 180 degrees different in direction prove photoshopping?
I went back and looked again...I think I am seeing what you are referring to and I believe what you see as photoshopping I would attribute to the use of different f-stop exposures which result in major differences in perspective and exposure. The difference between an f-stop of 1.4 used with, say a 28mm lense vs an f-stop of 22 used with a telephoto lens can be remarkable. One will result in a foreshortened background and the other will achieve the opposite.
If you notice, the pictures that are of the same direction were taken at markedly different times of the day and lighting.
Um...NO
How does showing me 2 photos taken from 2 different locations 180 degrees different in direction prove photoshopping?
I went back and looked again...I think I am seeing what you are referring to and I believe what you see as photoshopping I would attribute to the use of different f-stop exposures which result in major differences in perspective and exposure. The difference between an f-stop of 1.4 used with, say a 28mm lense vs an f-stop of 22 used with a telephoto lens can be remarkable. One will result in a foreshortened background and the other will achieve the opposite.
If you notice, the pictures that are of the same direction were taken at markedly different times of the day and lighting.
edit on 24-6-2013
by bbracken677 because: (no reason given)
reply to post by James1982
Thank you James....very well put.
I am leaning more and more towards the govt having something to do with it, but from the pictures we can tell little. I really doubt the govt would do something that would be traceable in any way unless they wanted it to be a serious statement. In this case I would think a drone strike would do it, however the vehicle does not look like a soft drink can that had a serious fire cracker dropped inside it (no tearing of them metal in such a way as to suggest a serious explosive involved).
However, one thing that would be possible would be someone tailing him and, knowing his state of mind, making him aware of the tail. This would, given his state of mind, possibly result in him doing just as he did...driving recklessly at high speeds resulting in a fatal wreck. KISS works well with that scenario...simple yet effective.
Not saying that is what happened, but a definite possibility.
Questions one must ask:
1)Why was he out at 4 AM?
2)Why was he driving as he was?
2a)Was he trying to "lose" someone?
2b)Was he running from a perceived threat?
None of the above questions can be answered easily, and for those questions the photos are pretty useless. If I were investigating this, those would be my first questions, which would likely lead to other questions....you have to peel the onion to get to the truth.
Thank you James....very well put.
I am leaning more and more towards the govt having something to do with it, but from the pictures we can tell little. I really doubt the govt would do something that would be traceable in any way unless they wanted it to be a serious statement. In this case I would think a drone strike would do it, however the vehicle does not look like a soft drink can that had a serious fire cracker dropped inside it (no tearing of them metal in such a way as to suggest a serious explosive involved).
However, one thing that would be possible would be someone tailing him and, knowing his state of mind, making him aware of the tail. This would, given his state of mind, possibly result in him doing just as he did...driving recklessly at high speeds resulting in a fatal wreck. KISS works well with that scenario...simple yet effective.
Not saying that is what happened, but a definite possibility.
Questions one must ask:
1)Why was he out at 4 AM?
2)Why was he driving as he was?
2a)Was he trying to "lose" someone?
2b)Was he running from a perceived threat?
None of the above questions can be answered easily, and for those questions the photos are pretty useless. If I were investigating this, those would be my first questions, which would likely lead to other questions....you have to peel the onion to get to the truth.
Originally posted by bbracken677
...I went back and looked again...I think I am seeing what you are referring to and I believe what you see as photoshopping I would attribute to the use of different f-stop exposures which result in major differences in perspective and exposure. The difference between an f-stop of 1.4 used with, say a 28mm lense vs an f-stop of 22 used with a telephoto lens can be remarkable. One will result in a foreshortened background and the other will achieve the opposite.
If you notice, the pictures that are of the same direction were taken at markedly different times of the day and lighting.
Well - thanks for explaining your perspective.
The accident took place in the median in front of 632 North Highland Avenue (+/- one numerical address difference). Going south on North Highland', this is a very short distance past an alley, that is a very short distance past Melrose.
(from Google Maps)
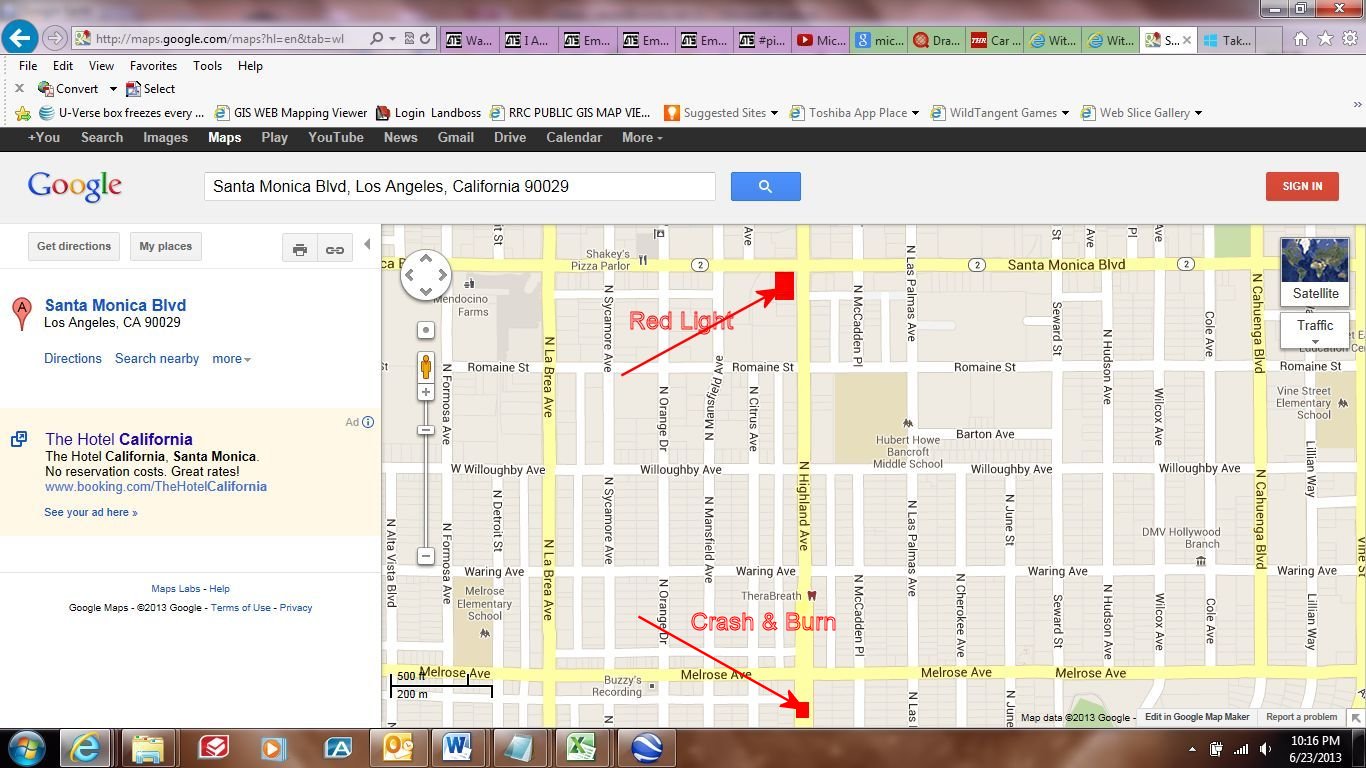
The next cross-street...going south (being about 4 more houses on both sides of the street) is Clinton Street. There is no traffic signal at Clinton... The next traffic signal is another city block south...being at Rosewood...
As you can see in this photo...apparently copyrighted by the Los Angeles Times...the first photo in question, shows the traffic signal at Rosewood, a short distance from the vehicle being inspected by three officers.

Obviously, there are three palm trees fairly closely grouped together, near the burned vehicle in the above photo.
Likewise, the median, for as far as the photo reveals, is FULL of mature palm trees.
Another matter to consider - the vehicle did not lodge (or settle) between trees, but rather collided head-on with one tree...as can be seen in this photo excerpted from the Loud Labs video...

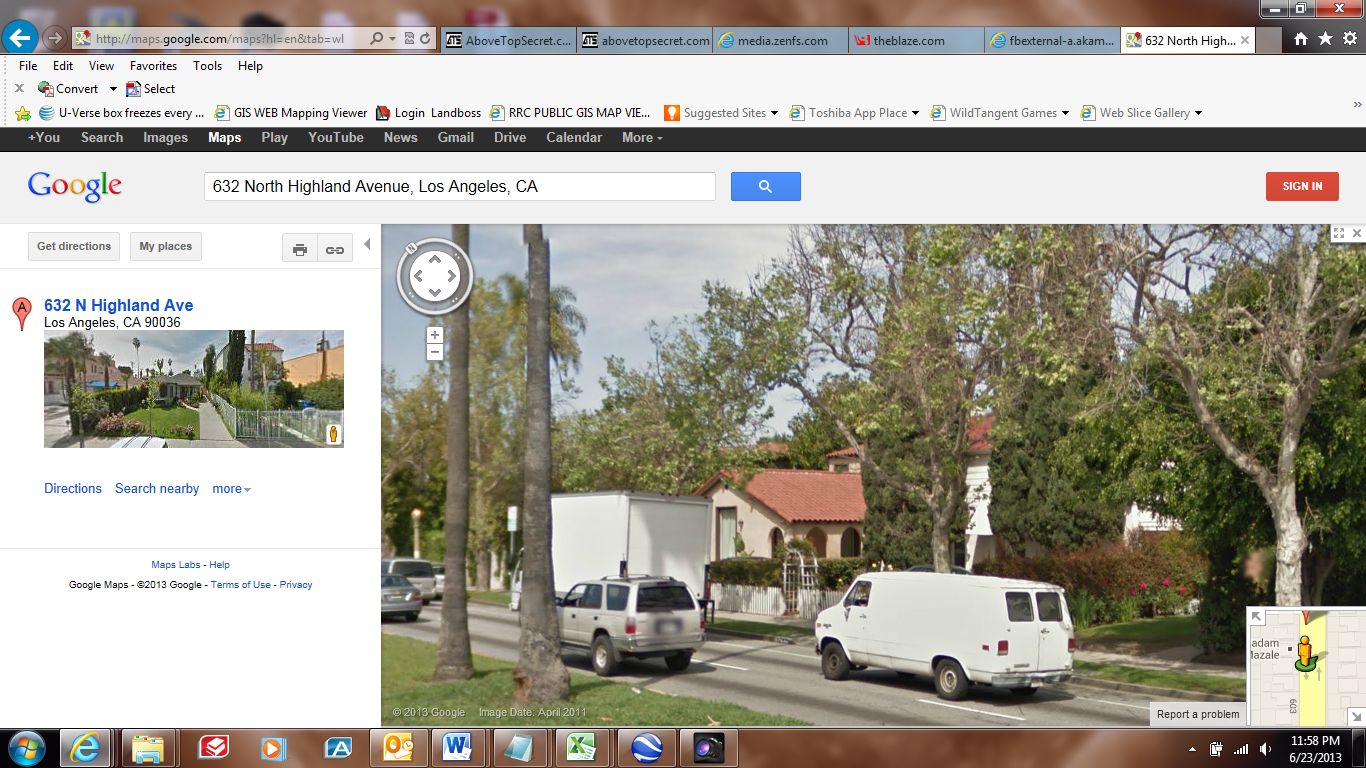
In this photo (also excerpted from the Loud Labs video), you can clearly identify a landmark...being the white picket fence with covered/rounded entry to the walkway...across the street.

In this photo taken from Google Maps (street view), you will see the only house on the entire east side of North Highland' with the white picket fence and ornamental entry to the walkway...
(the leftmost tree in the median is where the car burned)
If this doesn't answer your question, and you would like further explanation - I will be pleased to oblige.
If you remain stuck on the F-stop and/or other photographic perspective angle - Thanks for your consideration!
reply to post by WanDash
Here is your tree. The Fence and arch is blocked by the van. And you have the light pole. The trees seem to have more leafs and hides the double windows. They seem to have stretched the picture in some way to fit the wide screen format. I used the height above the light pole as a marker and the distance left and right from the arch as a marker. And tried to get as much of the street as I could.
The height of the camera could be a reason it seems off so much also. Google cars have the cameras pretty high. A person holding a camera would be a few feet shorter.
Notice I even found a California Google Car.
Here is your tree. The Fence and arch is blocked by the van. And you have the light pole. The trees seem to have more leafs and hides the double windows. They seem to have stretched the picture in some way to fit the wide screen format. I used the height above the light pole as a marker and the distance left and right from the arch as a marker. And tried to get as much of the street as I could.
The height of the camera could be a reason it seems off so much also. Google cars have the cameras pretty high. A person holding a camera would be a few feet shorter.
Notice I even found a California Google Car.
edit on 24-6-2013 by JBA2848 because: (no reason given)
Originally posted by JBA2848
...Here is your tree. The Fence and arch is blocked by the van. And you have the light pole. The trees seem to have more leafs and hides the double windows. They seem to have stretched the picture in some way to fit the wide screen format. I used the height above the light pole as a marker and the distance left and right from the arch as a marker. And tried to get as much of the street as I could.
...
Thanks JBA2848!
Yeah - I considered other angles, but was simply trying to establish, without contention, the proximity of the "arch". (Thanks for the word - For the life of me, I couldn't think of that word )
Also - from the other side (north-bound) of the street, you can view across to the houses on the south-bound side of the street, and confirm the house Water-hose Man was standing in front of...and the Psychic sign...
So Google drives Hyundai's...
Richard Clarke: Hastings Accident “Consistent with
a Car Cyber Attack”
This is consistent with many official remarks to the effect that 'they' are able and willing.
Former U.S. National Coordinator for Security, Infrastructure Protection, and Counter-terrorism Richard Clarketold The Huffington Post on Monday that the fatal crash of journalist Michael Hastings’ Mercedes C250 coupe last week is “consistent with a car cyber attack.”
“There is reason to believe that intelligence agencies for major powers” — including the United States — know how to remotely seize control of a car,” Clarke said.
This is consistent with many official remarks to the effect that 'they' are able and willing.
edit on 25-6-2013 by Guadeloupe because: (no reason given)
Witness [Jose Rubacalva] to Michael Hastings Car Crash Shares His Story (TYT Exclusive)
Telling interview with Ana Kasparian.....................
Telling interview with Ana Kasparian.....................
edit on 25-6-2013 by Guadeloupe because: (no reason given)
Originally posted by WanDash
Also - from the other side (north-bound) of the street, you can view across to the houses on the south-bound side of the street, and confirm the house Water-hose Man was standing in front of...and the Psychic sign...
So Google drives Hyundai's...
Water-hose Man belonged to this group...volunteer Hasidic community watch etc..........

The person (Jose Rubacalva) interviewed (above) is Mexican. He's most likely a worker not living in the neighborhood, an apparently Orthodox Jewish enclave.
NOTE: I have no opinion whatsoever on the merits of the video and on whatever bias it might contain. Its presented only as a research item inasmuch as it helps to clarify Hatzolah and the presence of Water-hose Man
edit on 25-6-2013 by Guadeloupe because: (no reason given)
reply to post by Guadeloupe
DARPA PM Kathleen Fisher, High Assurance Systems Published on Mar 14, 2012
Dr. Kathleen Fisher speaks on DARPA's High-Assurance Cyber Military Systems (HACMS) program. To learn more, please visit go.usa.gov...
TEXT: From a lecture by Dr. Kathleen Fisher, DARPA Program Manager, High Assurance Systems:
Comment: bm3racer - EASY TO MAKE HASTINGS CAR ACCELERATE AUTOMATICALLY TO KILL HIM IN “ACCIDENT”…
This post outlines a plausible scenario in which Michael Hastings might
have been murdered by the government altering the software in his car and auto accelerating his vehicle to his death (corroborated by computer scientists, hackers and a DARPA Program Manager).
Reddit Link: redd.it / 1grycy
Please share and up vote on reddit, otherwise this story will get buried.
DARPA PM Kathleen Fisher, High Assurance Systems Published on Mar 14, 2012
Dr. Kathleen Fisher speaks on DARPA's High-Assurance Cyber Military Systems (HACMS) program. To learn more, please visit go.usa.gov...
TEXT: From a lecture by Dr. Kathleen Fisher, DARPA Program Manager, High Assurance Systems:
Modern vehicles consist of between 30 and 100 embedded control units which are essentially small computers connected via CAN bus. [ CAN bus (for controller area network) is a vehicle bus standard designed to allow microcontrollers and devices to communicate with each other within a vehicle without a host computer. - donnafritz from Wikipedia] These cars were required by law to have a diagnostic port typically located under the steering wheel that allows mechanics to download diagnostic information and to perform software updates. In the first paper, the researchers from UCSD and the University of Washington showed that if they could touch the CAN bus to that diagnostic port, they could take over all of the functionality of the car that's controlled by software. And in an modern automobile, that's pretty much everything: the breaks are controlled by software because of anti-lock breaking,the acceleration is controlled by software because of cruise control, and those fancy cars that can park themselves, even the steering is under software control. The reaction to this first paper was somewhat muted, perhaps because the researchers had access to that diagnostic port, they were inside the car, and so already had physical access to the breaks, acceleration, and steering. They responded with a second paper, in which they showed a variety of ways of touching that CAN bus without physically touching the car. These attacks involved infecting the computers and repair shop, and then having that infection spread to the car through diagnostic port or hacking into the blue tooth system, or using the cell phone network to break into the telematics unit that's normally used to provide roadside assistance. The most ingenious attack, though used the stereo system in the car. The researchers were able to craft an electronic version of a song that played just fine in your household stereo system or on your personal computer. But when you put that on a CD and played it in the car CD player, it took over total control of your automobile. Yeah right – pretty scary, huh? These vulnerabilities arise because the cyber components of the interface of these cars are built from the same kinds of buddy components that are in your personal computers, and the control systems that are actually running the car have no notion that there can be an attacker sitting on the CAN bus. [...]
So commercial automobiles are not the only kind on non-traditional computer that are vulnerable to attack. We have to worry about all these other kinds of systems as well. Everything from SCADA systems that control the power grid and canal systems, to medical devices like the insulin pump shown on the slide, to computer peripherals, communication devices, and various kinds of vehicles. Researchers and/or attackers have shown that systems in each of these categories are vulnerable to attack. For example, for SCADA systems, the attacks on the Muruchi-Shire sewage plant in Australia -- say that ten times fast -- and the Ginot(sp?) canal system in France show that even supposedly air gap systems are vulnerable to remote attack, and that those attacks can cause physical damage while hiding the evidence of the attack from local monitoring.
Rest of lecture at
- See more at: www.tytnetwork.com...
Comment: bm3racer - EASY TO MAKE HASTINGS CAR ACCELERATE AUTOMATICALLY TO KILL HIM IN “ACCIDENT”…
This post outlines a plausible scenario in which Michael Hastings might
have been murdered by the government altering the software in his car and auto accelerating his vehicle to his death (corroborated by computer scientists, hackers and a DARPA Program Manager).
Reddit Link: redd.it / 1grycy
Please share and up vote on reddit, otherwise this story will get buried.
I'm a computer programmer, I'm no conspiracy theorist or anything, but I think no item should be left unturned when investigating this. If the investigators don't think of potential hypothetical scenarios, they will not be able to investigate for it. Here is a scenario…
All modern cars now days run on code, the code or "software" in his car could have been altered to ensure that once over a particular speed, it auto accelerates at full speed while the breaks are disabled and the car ends up crashing at some point. if you pull the handbrake, you'll end up going sideways and crashing, if you don't do that, you'll end up hitting something at very high speed. Notice how the car exploded? That is not normal, and only "normal" for it to happen in the movies.
They should look for signs of accessing the computer in the car (usually underneath the drivers seat) either using forced entry, cutting bits and pieces out from underneath the car to access it, or by getting a new key from the car distributor (sales outlet where he brought his car). Since the gov can print copies of passports without issue, and produce the necessary points of ID, it's easy to get a copy of the key from the car dealer (criminals even do this, that's how they steal new model cars now). If they did this, it would leave a trace, if they used forced entry by cutting underneath the car, that would leave a trace.
Also, the computer program may still be on the cars computer, but could also been auto deleted as soon as a crash was detected (since the car knows when it has entered a crash, it can trigger many things to occur before the car and its contents are destroyed, this information would be available to the central computer). Now, the investigator would need to check for deleted files as well as securely deleted files (files that are deleted in a way to prevent undeleting). If the investigator doesn't know to check for these items, they will NEVER know or be able to isolate this possibility.
Remember, the gov always has methods of killing people that it has not yet disclosed to the public, it is for this reason they can get away with it without it looking suspicious. To equalize the playing field, we have to think about these possibilities and ensure they are part of the investigation. Otherwise, we'll only know in 70 years when its too late and the items are declassified.
The last point I wanted to make was, they probably had access to his computer just like they had access to the women's computer at CNN I think it was. If they saw a story coming, or a story that he was working on or was about to break, then they may have killed him for that. There is a reason Glenn Greenwald lives in Brazil, to stay the hell away from US law enforcement and their ability to harm him in any way. I think we need to determine if he was working on a big story, but if they had access to his computer, it would have been irrecoverably deleted most likely.
Do I believe this happened? Unlikely, but even if there is a 1% possibility, its worth investigating for. What do you guys think?
I'm mainly worried that the investigator is not going to know to look for these types of things, because they probably know very little about computers.
Erx
- See more at: www.tytnetwork.com...
edit on 25-6-2013 by Guadeloupe because: added text
edit on 25-6-2013 by Guadeloupe because: (no reason given)
reply to post by Guadeloupe
That is interesting information. At this time, however, it is hard to imagine that most people wouldn't expect the government (and - just about anyone with the techno-savvy & desire) to have, not only the capability...but to also have tried, tested & proven methods (experience!!) of employing such covert tactics.
How can the official statement be - "No foul play" before the car even has time to cool down? How long does it take to investigate such an "incident"? He couldn't have left a suicide note in the car...that was readable (unless he scratched it into the metal.. ). Did he have a history of being ticketed for speeding around and about LA -?- at such hours -?- shortly after informing his co-horts that he was going off radar -?-
Everything about what we actually know of the accident looks like -
1. Someone who was trying to kill themself (and not caring if they killed others in the process), or
2. Someone who was not in control of the vehicle they were "driving".
Your point regarding the emergency brake... That could make sense (we don't know if that's what happened, but...) -
Had he engaged the Emergency Brakes along the stretch of North Highland from (at least) Santa Monica Blvd. to Melrose...the odds of hitting someone-else were significant... As soon as he passed Melrose, and was out of the business district/blocks...he pulled the brake... ?
Just exploring possibilities...
That is interesting information. At this time, however, it is hard to imagine that most people wouldn't expect the government (and - just about anyone with the techno-savvy & desire) to have, not only the capability...but to also have tried, tested & proven methods (experience!!) of employing such covert tactics.
How can the official statement be - "No foul play" before the car even has time to cool down? How long does it take to investigate such an "incident"? He couldn't have left a suicide note in the car...that was readable (unless he scratched it into the metal.. ). Did he have a history of being ticketed for speeding around and about LA -?- at such hours -?- shortly after informing his co-horts that he was going off radar -?-
Everything about what we actually know of the accident looks like -
1. Someone who was trying to kill themself (and not caring if they killed others in the process), or
2. Someone who was not in control of the vehicle they were "driving".
Your point regarding the emergency brake... That could make sense (we don't know if that's what happened, but...) -
Had he engaged the Emergency Brakes along the stretch of North Highland from (at least) Santa Monica Blvd. to Melrose...the odds of hitting someone-else were significant... As soon as he passed Melrose, and was out of the business district/blocks...he pulled the brake... ?
Just exploring possibilities...
edit on 6/25/2013 by WanDash because: Singular not Plural
reply to post by Guadeloupe
"crickets" ????????? Really!
Anyhow I was checking out the same thing and thought I would search ATS. Seems we are thinking the same thing.
Here is some info from RT:
rt.com...
"crickets" ????????? Really!
Anyhow I was checking out the same thing and thought I would search ATS. Seems we are thinking the same thing.
Here is some info from RT:
rt.com...
Hastings died last week when his 2013 Mercedes C250 coupe collided with a tree in Los Angeles, California on the morning of June 18. He was reportedly traveling at a high rate of speed and failed to stop at a red light moments before the single-car crash. He was only 33. Speaking to Huffington Post this week, Clarke said that a cyberattack waged at the vehicle could have caused the fatal collision. "What has been revealed as a result of some research at universities is that it's relatively easy to hack your way into the control system of a car, and to do such things as cause acceleration when the driver doesn't want acceleration, to throw on the brakes when the driver doesn't want the brakes on, to launch an air bag," Clarke told The Huffington Post. "You can do some really highly destructive things now, through hacking a car, and it's not that hard." "So if there were a cyberattack on the car — and I'm not saying there was," Clarke continued, "I think whoever did it would probably get away with it." The Los Angeles Police Department said they don’t expect foul play was involved in the crash, but an investigation has been opened nonetheless. In an email reportedly sent by Hastings hours before the crash, he told colleagues that he thought he was the target of a federal investigation. “Hey [redacted], the Feds are interviewing my ‘close friends and associates,’” Hastings wrote 15 hours before the crash. Michael Hastings (Paul Morigi / Getty Images for The Guardian / AFP) Michael Hastings (Paul Morigi / Getty Images for The Guardian / AFP) “Also: I’m onto a big story, and need to go off the rada[r] for a bit,” he added. “All the best, and hope to see you all soon.”
edit on 25-6-2013 by wevebeenassimilated because: added "Really!"
not to start an additional wave of conspiracy here but..
Intellectually most american accept the stretch of drones.. however they miss some things emo wise..
Nano Falcon..smallest in the world-just as big as your thumb!!
a thread on ATS you might find interesting
by cheesy
The reason I reference it
NO PARTICULAR REASON AT ALL!!!!
After all another thread here mentioned something about micro injectors..
its not like the body was burned..
And its not like some poisons burn through the body quickly
or that they survive fire..
Intellectually most american accept the stretch of drones.. however they miss some things emo wise..
Nano Falcon..smallest in the world-just as big as your thumb!!
a thread on ATS you might find interesting
by cheesy
The reason I reference it
NO PARTICULAR REASON AT ALL!!!!
After all another thread here mentioned something about micro injectors..
its not like the body was burned..
And its not like some poisons burn through the body quickly
or that they survive fire..
Originally posted by bbracken677
Originally posted by wulff
Absolutely, I have wondered for years why automakers are so supposedly working on safer cars but still allow 10 to 20 gallons of gasoline to be hung on a car with two straps and a tank thickness like a coffee can!
-Thanks
Thickness of a coffee can? Obviously you have never attempted to drill into one. I have and it is nothing like a coffee can.
I just love it when people make claims and then turn and look at their rear-ends to see what just came out. [/quote
I was exaggerating to make a point, as a matter of fact YES, I have drilled into one (I added a return line for converting to carb car to EFI )
They still are way to thin, I have a new one in my garage to replace one that was 'oil-canning' and developed a leak.
My hobby is building high performance cars and I grew up around them!
The fuel tank is one area (other than the stupid 70's GM scam the media tried) are not protected like they should be, a girlfriend of mine had a car that she bought back east and didn't know the 2 thin straps that held the tank was rusted, she filled it up (for a change) and hit a bump, it fell to the pavement and ruptured spewing fuel across the road, she had the brains to stop and shut it off and unbelievably there was no fire (the heavy rain probably helped).
No, this is one thing that never seems to get the attention it deserves. STOCK GAS TANKS ARE DANGEROUS! This is why my 10 second Camaro has a fuel cell!edit on 26-6-2013 by wulff because: (no reason given)
hmm maybe he was working on the story about obama not being legitimately on the ballot in 08 and had something huge..
hi, im calling from 2017 when WL leaks info on the CIA being able to remote control cars to assassinate and silence targets.
new topics
-
Only two Navy destroyers currently operational as fleet size hits record low
Military Projects: 4 hours ago -
George Stephanopoulos and ABC agree to pay $15 million to settle Trump defamation suit
Mainstream News: 9 hours ago
top topics
-
George Stephanopoulos and ABC agree to pay $15 million to settle Trump defamation suit
Mainstream News: 9 hours ago, 17 flags -
Light from Space Might Be Travelling Instantaneously
Space Exploration: 17 hours ago, 9 flags -
More Bad News for Labour and Rachel Reeves Stole Christmas from Working Families
Regional Politics: 16 hours ago, 8 flags -
Only two Navy destroyers currently operational as fleet size hits record low
Military Projects: 4 hours ago, 7 flags
active topics
-
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3687 • : angelchemuel -
The Mystery Drones and Government Lies
Political Conspiracies • 72 • : tarantulabite1 -
Only two Navy destroyers currently operational as fleet size hits record low
Military Projects • 1 • : alwaysbeenhere2 -
A priest who sexually assaulted a sleeping man on a train has been jailed for 16 months.
Social Issues and Civil Unrest • 30 • : alwaysbeenhere2 -
They Know
Aliens and UFOs • 86 • : ianmoone3 -
George Stephanopoulos and ABC agree to pay $15 million to settle Trump defamation suit
Mainstream News • 11 • : WeMustCare -
President-Elect DONALD TRUMP's 2nd-Term Administration Takes Shape.
Political Ideology • 331 • : WeMustCare -
Nov 2024 - Former President Barack Hussein Obama Has Lost His Aura.
US Political Madness • 15 • : WeMustCare -
Former DNI-Congressman John Ratcliffe says the U.S. Government is Intimidated by UFOs.
Aliens and UFOs • 41 • : WeMustCare -
One out of every 20 Canadians Dies by Euthanasia
Medical Issues & Conspiracies • 23 • : Daughter2v2
