It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
10
share:
Sorry in advance for the long thread but this seemed like important information!
Well first I want to start by saying, that while this cyber attack seems to be ongoing, the hackers haven't attacked...YET!
Microsoft warns that China Hackers Attacked US Infrastructure
Apparently Microsoft has somehow taken since "Mid-2021" to identify the threat but now they know who it is for sure.
At first I was thinking my usual, "this is MSM hype" but as I read I realized the potential for serious harm to be done. If this threat has been ongoing since Mid 2021 why has it taken our "intelligence agencies" so long to issue an alert
Well Good thing the NSA is doing their job, because today, they finally issued that alert, almost 2 years after the fact.
Joint CyberSecurity Advisory
The Advisory, issued by at least 7 Alphabet agencies from across the globe, Insists that affected parties have already been alerted.
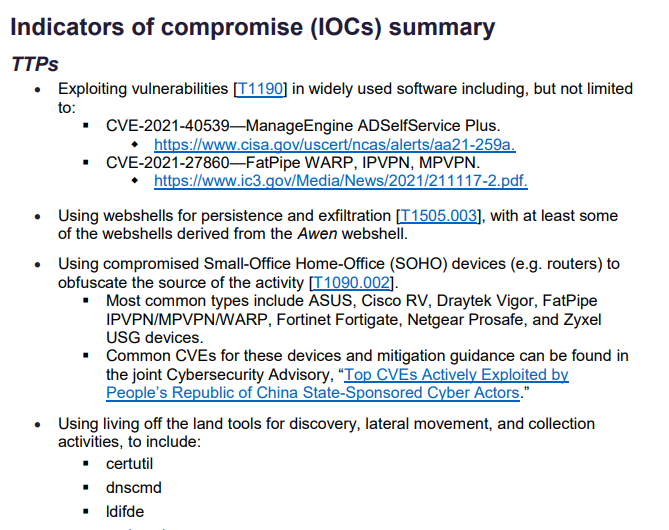
The Advisory includes steps and directives on how to spot and deal with the "Hack" and explains how this "VOLT TYPHOON" group is using specialized programs to lay undetected, utilizing normal software routines to disguise itself as it grow, spreads and prepares to take action.
There are pages of very specific, software coding, detection and mitigation protocols. I have added some screen shot of the PDF but the link is to webpage and does not automatically download.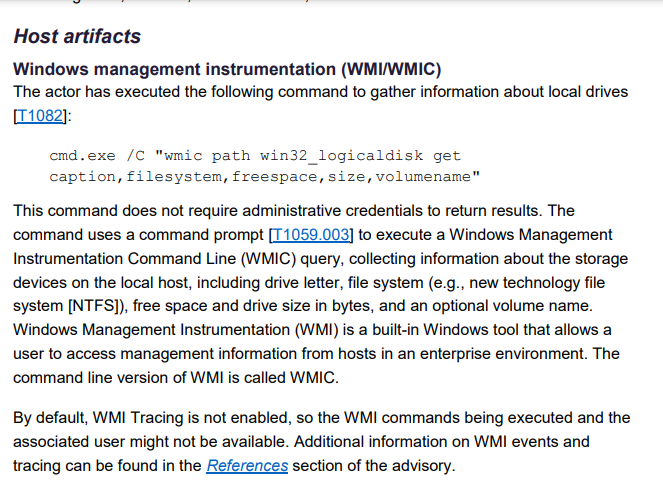
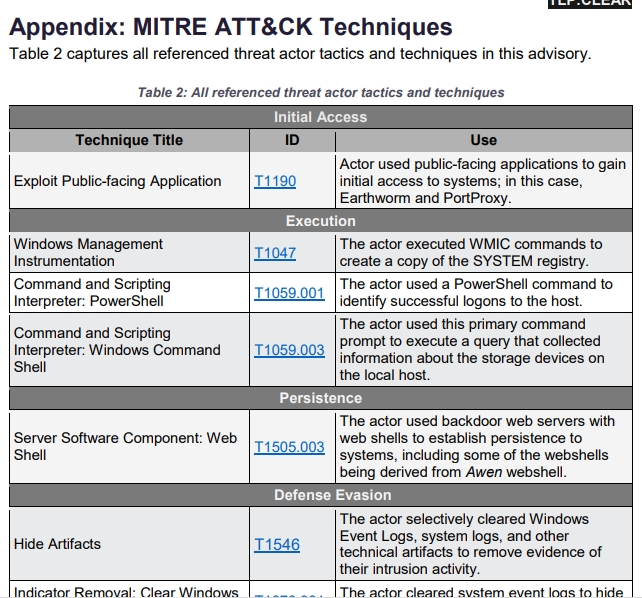

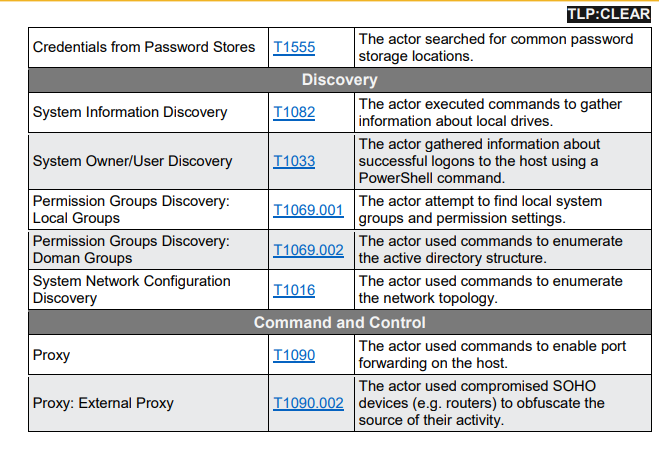
As you can see this has the potential to affect you and me at home as well not just as a repercussion of any potential attacks but your computer could be infected and helping to spread this, so being aware is always good.
I am sure there are those among us that understand the technicals far better than I do, i hope they are willing and able to share that understanding here with us as well.
There is also this article published today on the topic.
Vol t Typhoon targets US critical infrastructure
Beyond that this article goes deep into coding terminology and software specifics i do not fully understand.
With that said I DO understand one thing, this has the potential for some serious damage!
What have they acquired already?
How deeply rooted is this campaign, after two years, how many "slaves" have been created and what systems are they in?
These specifics are not mentioned but acknowledged, surely if this was serious enough it would be all over the news?
In any case, I'm going to keep diving here and there for a bit. I will update if/when I find anything new
Well first I want to start by saying, that while this cyber attack seems to be ongoing, the hackers haven't attacked...YET!
Microsoft warns that China Hackers Attacked US Infrastructure
Apparently Microsoft has somehow taken since "Mid-2021" to identify the threat but now they know who it is for sure.
Microsoft warned on Wednesday that Chinese state-sponsored hackers had compromised “critical” U.S. cyber infrastructure across numerous industries with a focus on gathering intelligence.
The Chinese hacking group, codenamed “Volt Typhoon,” has operated since mid-2021,
At first I was thinking my usual, "this is MSM hype" but as I read I realized the potential for serious harm to be done. If this threat has been ongoing since Mid 2021 why has it taken our "intelligence agencies" so long to issue an alert
U.S. intelligence agencies became aware of the incursion in February, around the same time that a Chinese spy balloon was downed
Well Good thing the NSA is doing their job, because today, they finally issued that alert, almost 2 years after the fact.
Joint CyberSecurity Advisory
The Advisory, issued by at least 7 Alphabet agencies from across the globe, Insists that affected parties have already been alerted.
The Advisory includes steps and directives on how to spot and deal with the "Hack" and explains how this "VOLT TYPHOON" group is using specialized programs to lay undetected, utilizing normal software routines to disguise itself as it grow, spreads and prepares to take action.
There are pages of very specific, software coding, detection and mitigation protocols. I have added some screen shot of the PDF but the link is to webpage and does not automatically download.








As you can see this has the potential to affect you and me at home as well not just as a repercussion of any potential attacks but your computer could be infected and helping to spread this, so being aware is always good.
I am sure there are those among us that understand the technicals far better than I do, i hope they are willing and able to share that understanding here with us as well.
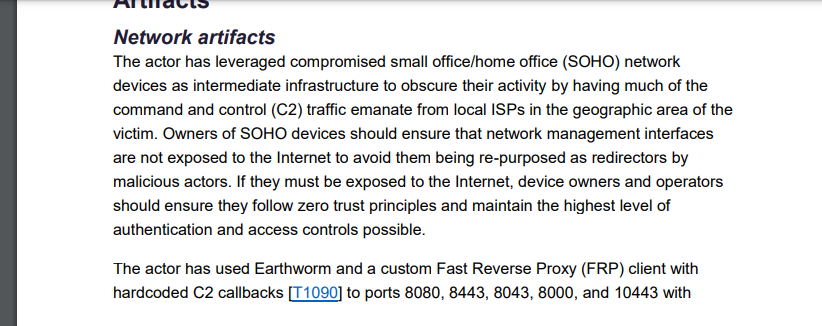
The actor has leveraged compromised small office/home office (SOHO) network
devices as intermediate infrastructure to obscure their activity by having much of the
command and control (C2) traffic emanate from local ISPs in the geographic area of the
victim. Owners of SOHO devices should ensure that network management interfaces
are not exposed to the Internet to avoid them being re-purposed as redirectors by
malicious actors. If they must be exposed to the Internet, device owners and operators
should ensure they follow zero trust principles and maintain the highest level of
authentication and access controls possible
There is also this article published today on the topic.
Vol t Typhoon targets US critical infrastructure
TextIn this campaign, the affected organizations span the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors. Observed behavior suggests that the threat actor intends to perform espionage and maintain access without being detected for as long as possible.
To achieve their objective, the threat actor puts strong emphasis on stealth in this campaign, relying almost exclusively on living-off-the-land techniques and hands-on-keyboard activity. They issue commands via the command line to (1) collect data, including credentials from local and network systems, (2) put the data into an archive file to stage it for exfiltration, and then (3) use the stolen valid credentials to maintain persistence. In addition, Volt Typhoon tries to blend into normal network activity by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware. They have also been observed using custom versions of open-source tools to establish a command and control (C2) channel over proxy to further stay under the radar.
As with any observed nation-state actor activity, Microsoft has directly notified targeted or compromised customers, providing them with important information needed to secure their environments.
Beyond that this article goes deep into coding terminology and software specifics i do not fully understand.
With that said I DO understand one thing, this has the potential for some serious damage!
What have they acquired already?
How deeply rooted is this campaign, after two years, how many "slaves" have been created and what systems are they in?
These specifics are not mentioned but acknowledged, surely if this was serious enough it would be all over the news?
In any case, I'm going to keep diving here and there for a bit. I will update if/when I find anything new
edit on 24pm31600000023 by datguy because: (no reason given)
edit on 24pm31600000023 by datguy because: (no reason
given)
It took 2 years of intel and military intel to see and analyze the finer details of it. The intel most likely has a program in place now to protect
any attacks on the infrastructure including the MIC data base.
As you can see this has the potential to affect you and me
First step : Turn off remote desktop and remote registry services, if possible .
Second step : Disable local network discovery , if possible .
The reason for the "if possible" is that if you have a small network at home , shared storage , etc. you may not want to do this . Also , if you use a "hotspot" , doing so may disable the connection ,etc.
a reply to: datguy
As someone in cybersecurity, we knew about this long before it was made public. The FBI and companies like Microsoft, Verizon, Mandiant, Crowdstrike, etc., do notifications without telling the public. My sector of choice is critical infrastructure, they get regular briefings, yet due to the nature of the processes they run, it takes a very long time to make changes.
I wouldn't worry about this one, the ones you have to worry about are way bigger, and you'll never hear anything about them unless they are required to disclose the incident. When the media gets ahold of it, it's all a big FUD fest for the average person.
As someone in cybersecurity, we knew about this long before it was made public. The FBI and companies like Microsoft, Verizon, Mandiant, Crowdstrike, etc., do notifications without telling the public. My sector of choice is critical infrastructure, they get regular briefings, yet due to the nature of the processes they run, it takes a very long time to make changes.
I wouldn't worry about this one, the ones you have to worry about are way bigger, and you'll never hear anything about them unless they are required to disclose the incident. When the media gets ahold of it, it's all a big FUD fest for the average person.
a reply to: Hypntick
Yeah , like Spectre and Meltdown in my opinion .
Big sh__ caused by Google's Team to make them appear relevant.
Those exploits had been known since the late 80s .
And I give you an
Very important , little known job .
From a retired "White Hat" .
When the media gets ahold of it, it's all a big FUD fest for the average person.
Yeah , like Spectre and Meltdown in my opinion .
Big sh__ caused by Google's Team to make them appear relevant.
Those exploits had been known since the late 80s .
And I give you an
Very important , little known job .
From a retired "White Hat" .
edit on 5/24/23 by Gothmog because: (no reason given)
a reply to: Hypntick
This does make sense but then I have to wonder. if this is under wraps so to speak, why the alert?
Are there concerns of some of the SOHO slaves becoming active? or are they trying to use this now as disinformation against the hacker group?
It seems they still have some very real concerns about systems over seas, specifically the ones mentions in Guam that they are concerned may be used in an attack on Taiwan
Chinese Malware hits systems in Guam
Are they really that slow to making changes?
This does make sense but then I have to wonder. if this is under wraps so to speak, why the alert?
Are there concerns of some of the SOHO slaves becoming active? or are they trying to use this now as disinformation against the hacker group?
It seems they still have some very real concerns about systems over seas, specifically the ones mentions in Guam that they are concerned may be used in an attack on Taiwan
Chinese Malware hits systems in Guam
Are they really that slow to making changes?
Going back to the Obama years when large transformers for our power grid were outsourced to China, people who thought this was a slippery slope were
ignored. Fast forward to 2018 and this report:
China is far deeper in our business than most people realize, and much of it is unknown to the general population-as are the dangers from multiple angles.
[www.lawfareblog.com...]
From two years ago:
[www.reuters.com... KBN28R31R]
Much of the decoupling involves these digital supply-chain issues, like with attempts to ban government employees and contractors from downloading the app TikTok, which is owned by a Chinese company, or the aforementioned inspections of foreign telecom suppliers whose operation in the U.S. may pose security risks.
China is far deeper in our business than most people realize, and much of it is unknown to the general population-as are the dangers from multiple angles.
[www.lawfareblog.com...]
From two years ago:
WASHINGTON (Reuters) - The U.S. energy secretary on Thursday signed an order prohibiting electric utilities that supply critical defense facilities from importing certain power system items from China, in an effort to protect U.S. security from cyber and other attacks.
The Department of Energy said in a release the order prohibits utilities that supply the defense facilities at a service voltage of 69kV or above from acquiring, importing, transferring, or installing bulk power system electric equipment. It was not immediately clear which defense sites were considered critical and the Energy Department did not immediately respond to a request for comment.
Bulk power equipment consists of items used in substations, control rooms, or power plants, including nuclear reactors, capacitors, transformers, large generators and backup generators and other equipment.
[www.reuters.com... KBN28R31R]
a reply to: datguy
So depending on the systems in operation and their age, it can take years to accomplish anything. Windows 7 has been end of life for a while, yet organizations still run it. Heck, I've been on an old IBM mainframe that was older than I am, all because it was so costly to move its operations to a more modern system.
When they do release these, it's either because there's a regulatory requirement to release, or in a case like this, they've already spoken with the most impacted parties and have given them time to remediate. The rest of the SOHO slave thing that's always going to be a thing due to the nature of SOHO equipment. Unless you've picked up a firewall with a subscription service for updates and have had it configured correctly, you will be running basic stuff. Most of that will get patches, but does the average home user know to check their router to see if there's a patch hanging out? That's why they would release this one to let the average home user know to check their equipment.
As I said, worry about the stuff you never hear about, those are the ones that have serious pucker factor to them.
So depending on the systems in operation and their age, it can take years to accomplish anything. Windows 7 has been end of life for a while, yet organizations still run it. Heck, I've been on an old IBM mainframe that was older than I am, all because it was so costly to move its operations to a more modern system.
When they do release these, it's either because there's a regulatory requirement to release, or in a case like this, they've already spoken with the most impacted parties and have given them time to remediate. The rest of the SOHO slave thing that's always going to be a thing due to the nature of SOHO equipment. Unless you've picked up a firewall with a subscription service for updates and have had it configured correctly, you will be running basic stuff. Most of that will get patches, but does the average home user know to check their router to see if there's a patch hanging out? That's why they would release this one to let the average home user know to check their equipment.
As I said, worry about the stuff you never hear about, those are the ones that have serious pucker factor to them.
a reply to: soundsofmadness
I have trouble believing that. While i have enough issues with Gates and his board members being tied to epstein amongst other things, I think this is the Prime reason China would have nothing to do with him.
Is he selling his US farmland to or buying it from the Chinese?
I have trouble believing that. While i have enough issues with Gates and his board members being tied to epstein amongst other things, I think this is the Prime reason China would have nothing to do with him.
Is he selling his US farmland to or buying it from the Chinese?
originally posted by: datguy
a reply to: soundsofmadness
I have trouble believing that. While i have enough issues with Gates and his board members being tied to epstein amongst other things, I think this is the Prime reason China would have nothing to do with him.
Is he selling his US farmland to or buying it from the Chinese?
A quick property profile by the Title company will answer your questions.
originally posted by: datguy
a reply to: soundsofmadness
I have trouble believing that. While i have enough issues with Gates and his board members being tied to epstein amongst other things, I think this is the Prime reason China would have nothing to do with him.
Is he selling his US farmland to or buying it from the Chinese?
Id bet if you asked Bill Gates if Microsoft was an American or Chinese company Like NIKE he would say Chinese.
Im adding some new information in regards to a current event that is also ongoing.
There is a thread about it already but ia m adding the link here.
Also a new threat was issues yesterday about an attack on European banks
Could they all be tied together?
www.abovetopsecret.com...
this was my addition to that thread
www.abovetopsecret.com...
There is a thread about it already but ia m adding the link here.
Also a new threat was issues yesterday about an attack on European banks
Could they all be tied together?
www.abovetopsecret.com...
this was my addition to that thread
www.abovetopsecret.com...
new topics
-
Fun with extreme paints
Interesting Websites: 20 minutes ago -
CIA is alleged to be operat social media troll frms in Kyiv
ATS Skunk Works: 1 hours ago -
Rainbow : Stargazer
Music: 2 hours ago -
I sleep no more.
Philosophy and Metaphysics: 4 hours ago -
Canada caught red-handed manipulating live weather data and make it warmer
Fragile Earth: 4 hours ago -
Why Files Our Alien Overlords | How We Secretly Serve The Tall Whites
Aliens and UFOs: 6 hours ago -
Curse of King Tuts Tomb Solved
Ancient & Lost Civilizations: 7 hours ago -
What allies does Trump have in the world?
ATS Skunk Works: 7 hours ago
top topics
-
Canada caught red-handed manipulating live weather data and make it warmer
Fragile Earth: 4 hours ago, 15 flags -
BIDEN Admin Begins Planning For January 2025 Transition to a New President - Today is 4.26.2024.
2024 Elections: 16 hours ago, 10 flags -
Big Storms
Fragile Earth: 17 hours ago, 9 flags -
Why Files Our Alien Overlords | How We Secretly Serve The Tall Whites
Aliens and UFOs: 6 hours ago, 9 flags -
Curse of King Tuts Tomb Solved
Ancient & Lost Civilizations: 7 hours ago, 7 flags -
What allies does Trump have in the world?
ATS Skunk Works: 7 hours ago, 3 flags -
CIA is alleged to be operat social media troll frms in Kyiv
ATS Skunk Works: 1 hours ago, 2 flags -
I sleep no more.
Philosophy and Metaphysics: 4 hours ago, 1 flags -
Fun with extreme paints
Interesting Websites: 20 minutes ago, 1 flags -
Rainbow : Stargazer
Music: 2 hours ago, 0 flags
active topics
-
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 348 • : Threadbarer -
Rainbow : Stargazer
Music • 2 • : Hakaiju -
Canada caught red-handed manipulating live weather data and make it warmer
Fragile Earth • 20 • : network dude -
Fun with extreme paints
Interesting Websites • 1 • : Encia22 -
Biden "Happy To Debate Trump"
2024 Elections • 53 • : SchrodingersRat -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics • 107 • : NoCorruptionAllowed -
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies • 42 • : SchrodingersRat -
CIA is alleged to be operat social media troll frms in Kyiv
ATS Skunk Works • 8 • : pianopraze -
Why Files Our Alien Overlords | How We Secretly Serve The Tall Whites
Aliens and UFOs • 7 • : Degradation33 -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology • 4 • : randomuser2034
10
