It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: kwakakev
None...
So just for the record..
What professional hitman that Hillary Clinton could afford is going to get in a street fight with his target??
None..
Half the things that “look shady” are literally the last thing ANY professional hit man would ever do..
As another example.. if you are faking a robbery YOU TAKE THE WALLET!
Obviously lol...
All rich’s Family, all rich’s Friends, all the police who actually investigated the case ..
EVERYONE with any personal or professional stake in the case agree that the conspiracy theory is ONLY an attempt to protect Donald trump after allegations of malfeasance against him came out..
Literally not one individual who is not a cartoon conservative hack believes the conspiracy theory..
None...
So just for the record..
What professional hitman that Hillary Clinton could afford is going to get in a street fight with his target??
None..
Half the things that “look shady” are literally the last thing ANY professional hit man would ever do..
As another example.. if you are faking a robbery YOU TAKE THE WALLET!
Obviously lol...
All rich’s Family, all rich’s Friends, all the police who actually investigated the case ..
EVERYONE with any personal or professional stake in the case agree that the conspiracy theory is ONLY an attempt to protect Donald trump after allegations of malfeasance against him came out..
Literally not one individual who is not a cartoon conservative hack believes the conspiracy theory..
a reply to: kwakakev
Except it is fake, so he won’t..
Just like every other accusation conservative media makes..
They claim felonies with no proof, then nothing happens..
They are never required to prove their case, yet all the sheeple believe then the next time..
Wash, rinse repeat
Except it is fake, so he won’t..
Just like every other accusation conservative media makes..
They claim felonies with no proof, then nothing happens..
They are never required to prove their case, yet all the sheeple believe then the next time..
Wash, rinse repeat
a reply to: kwakakev
So why isn’t trump prosecuting him assuming your opinion is correct????
If trump/ gop had ANY proof of their allegations, it only benefits them to prosecute the offenders..
THE ONLY WAY IT HURTS TRUMP TO PROSECUTE THOSE HE HAS ACCUSED OF WHATEVER, IS IF HE HAS ZERO EVIDENCE!!
Besides that it is only a win.
So why isn’t trump prosecuting him assuming your opinion is correct????
If trump/ gop had ANY proof of their allegations, it only benefits them to prosecute the offenders..
THE ONLY WAY IT HURTS TRUMP TO PROSECUTE THOSE HE HAS ACCUSED OF WHATEVER, IS IF HE HAS ZERO EVIDENCE!!
Besides that it is only a win.
few of the comments link this story to Scorcha Faal
Boomer1941 noname
3 days ago
The name Sorch Faal says it all...total BS.
SharpAsATack
3 days ago
YES!!!!! Sorcha Faal is the ORIGINATOR!!!!
if thats the case....
Boomer1941 noname
3 days ago
The name Sorch Faal says it all...total BS.
SharpAsATack
3 days ago
YES!!!!! Sorcha Faal is the ORIGINATOR!!!!
if thats the case....
Judge Jeanine Pirro Tackles The Left’s Plot To REMAKE America | Huckabee
Here Judge Jeanine Pirro talks about the operations of the deep state. The deep state is comprised of government workers who are essentially on the ground making the decisions. They do not care what the rules are, they know how to circumvent the rules.
Attempts to frame Donald Trump by James Comey and company is one example of this with two years of division. The FBI have been blocking a lot of requests with Christopher Wray complicate. More about protecting the agency than serving the people.
This interview also includes some of the Ukraine stuff kicking off.
Here Judge Jeanine Pirro talks about the operations of the deep state. The deep state is comprised of government workers who are essentially on the ground making the decisions. They do not care what the rules are, they know how to circumvent the rules.
Attempts to frame Donald Trump by James Comey and company is one example of this with two years of division. The FBI have been blocking a lot of requests with Christopher Wray complicate. More about protecting the agency than serving the people.
This interview also includes some of the Ukraine stuff kicking off.
Liz Crokin Update 2019 — THE DARK TAPE ON THE DARK WEB
This report by Liz Crokin details an article from True Pundit around Oct/Nov 2016, just before the election. It is about the contents recovered by Anthony Winers Laptop. Evidence of money laundering, child exploitation, sex crimes with minors, perjury, pay to play Clinton Foundation, obstruction of justice and other felony crimes.
General Flynn did tweet out this article and got targeted for exposing Pizzagate. Liz confirms through other sources that there is a video of Hillary Clinton and Huma Abedin involved in multiple crimes with a minor. Disturbing reports. Liz also talks about some of the recent Epstein case.

Some of this laptop stuff did hit the boards here on ATS at the time, along with many other scandals along the way. I do agree with what Liz has reported. There are a lot of similar themes with John's testimony of an over reaching and lawless control of government and private industry.
This report by Liz Crokin details an article from True Pundit around Oct/Nov 2016, just before the election. It is about the contents recovered by Anthony Winers Laptop. Evidence of money laundering, child exploitation, sex crimes with minors, perjury, pay to play Clinton Foundation, obstruction of justice and other felony crimes.
General Flynn did tweet out this article and got targeted for exposing Pizzagate. Liz confirms through other sources that there is a video of Hillary Clinton and Huma Abedin involved in multiple crimes with a minor. Disturbing reports. Liz also talks about some of the recent Epstein case.

Some of this laptop stuff did hit the boards here on ATS at the time, along with many other scandals along the way. I do agree with what Liz has reported. There are a lot of similar themes with John's testimony of an over reaching and lawless control of government and private industry.
Kevin Shipp – Former CIA Director Brennan Will Rat Out Trump Coup Criminals
Kevin Shipp is a former CIA agent after turning whistle blower against government corruption. Charges include abuse of the states secret act. Questioned the lack of security for CIA agents overseas. Has been poisoned, sections of this book 'Company of Shadows' censored and pension removed. Under went a common program to destroy and discredit whistle blowers.
The current whistle blower complaint in congress is like Russian Collusion 2.0. Cover up facts and impeach Trump. Jenna Hasbolt and CIA Director John Brennan are caught up in it. The evidence is a plant. Looks stupid, media is complicate in the corruption. John Brennan is on the board of MSNBC. CIA Director James Clapper is on the board of CNN. An operation against the American people.
John Brennan should of been indited a long time ago. It is up to William Barr now. Expects John Brennan to talk should it happen. Will expose the rest of the coup with James Clapper, James Comey, Barrack Obama. Obama approved through daily CIA presidential breifs. Connections to George Soros, Clinton Foundation and globalism.
People going nuts because they are afraid of prison. FISA fraud soon with Andrew McCabe, James Comey, Rod Rosienstien and the Intelligence Community Inspector General. Whistle blower aid provided by George Soros. Known and provable crimes have been committed. Up to William Barr to sort it out. Carl Bernstien has reported that William Barr is getting ready to drop the hammer on the deep state. Everyone should be upset by it.
Kevin Shipp is a former CIA agent after turning whistle blower against government corruption. Charges include abuse of the states secret act. Questioned the lack of security for CIA agents overseas. Has been poisoned, sections of this book 'Company of Shadows' censored and pension removed. Under went a common program to destroy and discredit whistle blowers.
The current whistle blower complaint in congress is like Russian Collusion 2.0. Cover up facts and impeach Trump. Jenna Hasbolt and CIA Director John Brennan are caught up in it. The evidence is a plant. Looks stupid, media is complicate in the corruption. John Brennan is on the board of MSNBC. CIA Director James Clapper is on the board of CNN. An operation against the American people.
John Brennan should of been indited a long time ago. It is up to William Barr now. Expects John Brennan to talk should it happen. Will expose the rest of the coup with James Clapper, James Comey, Barrack Obama. Obama approved through daily CIA presidential breifs. Connections to George Soros, Clinton Foundation and globalism.
People going nuts because they are afraid of prison. FISA fraud soon with Andrew McCabe, James Comey, Rod Rosienstien and the Intelligence Community Inspector General. Whistle blower aid provided by George Soros. Known and provable crimes have been committed. Up to William Barr to sort it out. Carl Bernstien has reported that William Barr is getting ready to drop the hammer on the deep state. Everyone should be upset by it.
a reply to: drewlander
John McAfee Wikipedia
There are some similarities between the witness statement and the legal issues of John McAfee.
It appears that Guatemala has some similarities to Guantanamo Bay.
John McAfee Wikipedia
There are some similarities between the witness statement and the legal issues of John McAfee.
On April 30, 2012, McAfee's property in Orange Walk Town, Belize, was raided by the Gang Suppression Unit of the Belize Police Department. At that time, McAfee was in bed with his girlfriend, who McAfee said was traumatized by the incident. A GSU press release stated that McAfee was arrested for unlicensed drug manufacturing and possession of an unlicensed weapon. He was released without charge. In 2012, Belize police spokesman Raphael Martinez confirmed that McAfee was neither convicted nor charged, only suspected.
On December 5, 2012, McAfee was arrested for illegally entering Guatemala. Shortly afterward, he was placed under arrest and a board to review McAfee's plea for asylum was formed. The committee denied his asylum, so he was taken from his holding facility to a detention center in order to await deportation to Belize.
On December 6, 2012, Reuters and ABC News reported that McAfee had two minor heart attacks in a Guatemalan detention center and was hospitalized. McAfee's lawyer stated that his client had not suffered heart attacks, but had instead suffered from high blood pressure and anxiety attacks.
It appears that Guatemala has some similarities to Guantanamo Bay.
Russia DID NOT Hack The DNC - John McAfee Lays It Out
This interview with John McAfee on RT news is from Jan 5, 2017. It does show John with a strong knowledge of the events and investigations with the DNC server hack.
JOHN MCAFEE TELLS ALL / RAW
This presentation by John McAfee is from Aug 27, 2013. It address a lot of the stories going around with John getting out of Guatemala. Done in a light hearted and comical way.
John McAfee does have a website at whoismcafee.com. In it he provides instructions on how to remove McAfee Antivirus. He was the founder for this product, strong reputation back then. Has not been involved with it for 15 years.
It is looking good that Johnheretohelp is John McAfee.
This interview with John McAfee on RT news is from Jan 5, 2017. It does show John with a strong knowledge of the events and investigations with the DNC server hack.
JOHN MCAFEE TELLS ALL / RAW
This presentation by John McAfee is from Aug 27, 2013. It address a lot of the stories going around with John getting out of Guatemala. Done in a light hearted and comical way.
John McAfee does have a website at whoismcafee.com. In it he provides instructions on how to remove McAfee Antivirus. He was the founder for this product, strong reputation back then. Has not been involved with it for 15 years.
It is looking good that Johnheretohelp is John McAfee.
a reply to: drewlander
I will have to say no. Below is a recent 2 hour Q&A interview with Johnheretohelp along with a recent 30min interview with John McAfee. There are a lot of similarities in both of their stories and the way they talk. The biggest clue that these are not the same people is how Johnheretohelp did not use the F bomb word once while John McAfee is regularly using this word. I could see John McAfee disguising his voice if he wanted, I cannot see John McAfee going two hours without swearing, especially with some of the topics discussed.
Another clue is at the 1:52:06 mark where Johnheretohelp does say 'that he does not have a household name'.
JohnHereToHelp Q&A
John McAfee Talks Anarchy, Crypto, and His DEX
To update JohnHereToHelp position, he is living with a low profile at this time. His has been cut off from access to his medication and is still looking for an official security detail. Has had some meetings with lawyers but still looking for someone to take on his case.
Is Johnheretohelp irl John McAfee?
I will have to say no. Below is a recent 2 hour Q&A interview with Johnheretohelp along with a recent 30min interview with John McAfee. There are a lot of similarities in both of their stories and the way they talk. The biggest clue that these are not the same people is how Johnheretohelp did not use the F bomb word once while John McAfee is regularly using this word. I could see John McAfee disguising his voice if he wanted, I cannot see John McAfee going two hours without swearing, especially with some of the topics discussed.
Another clue is at the 1:52:06 mark where Johnheretohelp does say 'that he does not have a household name'.
JohnHereToHelp Q&A
John McAfee Talks Anarchy, Crypto, and His DEX
To update JohnHereToHelp position, he is living with a low profile at this time. His has been cut off from access to his medication and is still looking for an official security detail. Has had some meetings with lawyers but still looking for someone to take on his case.
a reply to: kwakakev
It's been scrubbed from the net but there was a project called green lantern that had ties to software was stolen and developed on an Indian reservation in AZ.
www.sgtreport.com...
It's been scrubbed from the net but there was a project called green lantern that had ties to software was stolen and developed on an Indian reservation in AZ.
www.sgtreport.com...
a reply to: staple
The PROMIS software is a deep rabbit hole. Richard Andrew Grove brings it up with his 9/11 testimony. Sounds like the original developer of this software got ripped off as those that stole it put in back doors and spread it around the world to snoop on the worlds judiciary and other government branches. Big CIA / Mossad operation. Still hear the name popping up at times with ongoing court cases.
The Abernathy Murders, February 19, 1997
I have not hear of Green Lantern in relation to this before. Does continue the science fiction theme of deep space nine in project names. With the work outlined by John in another thread, having access to the data set from something like PROMIS will help give the super computers something to feed off with a Looking Glass type project. With how 5G is also being merged with this data can produce a powerful beast.
It is an interesting lead you bring up. Cheers, got any more on it?
The PROMIS software is a deep rabbit hole. Richard Andrew Grove brings it up with his 9/11 testimony. Sounds like the original developer of this software got ripped off as those that stole it put in back doors and spread it around the world to snoop on the worlds judiciary and other government branches. Big CIA / Mossad operation. Still hear the name popping up at times with ongoing court cases.
Promis itself is supposed to be this magical software program that allows operatives in the shadowy world of intelligence to track anyone and anything throughout the world - well, that's the claim at least. In reality, at the time it was written, Promis was a glorified computer-architecture-independent relational database program for tracking criminal case files, with the ability to juggle different data types and formats used by various law enforcement agencies
The Abernathy Murders, February 19, 1997
I have not hear of Green Lantern in relation to this before. Does continue the science fiction theme of deep space nine in project names. With the work outlined by John in another thread, having access to the data set from something like PROMIS will help give the super computers something to feed off with a Looking Glass type project. With how 5G is also being merged with this data can produce a powerful beast.
It is an interesting lead you bring up. Cheers, got any more on it?
@John let it slip that he has a very unusual name.
Hendricus G. Loos is a very unusual name.
patents.justia.com...
www.quora.com...
Hendricus G. Loos is a very unusual name.
patents.justia.com...
Who is Hendricus G. Loos?
The name Hendricus G. Loos does not belong to a person, its a fictitious name. Perhaps the person working behind this name is Professor Ross Adey , who qualified in Medicine from Australia, then came to Oxford University to study brain physiology . Then he joined University of California in 1954, later joined the Brain Research Institute in 1961. He mainly studied the effects of ELF & microwaves on human brain and nervous system. He developed several devices for remote mind control and manipulation of nervous system which were later patented in US. There could be a few other such professionals and scientists, who developed the Mind Control devices under a single fictitious name 'Dr Hendricus G. Loos', actually working for DARPA or CIA, so as not to attract the attention of the Media or investigators.
www.quora.com...
edit on 24-12-2019 by IAMTAT because: (no reason given)
edit on 24-12-2019 by IAMTAT because: (no reason given)
The Truth Fears no Questions
In this 19 min presentation it sounds like Santa Surfing and JohnHereToHelp have had a falling out. John has provided an interview with another person, in which there are inconsistencies in the story. With the part on the Seth Rich murder, the evidence is pointing at two MS-13 gang members that where later killed. Santa Surfing does go into other inconsistence with Johns story.
John has taken any money that was given, has refused any security and legal support that was offered. Is John just a con man or has a psychological operation been applied to murky the waters and discredit John?
With how twitter banned all reference to JohnHerToHelp when his story first came out, I do question just who exactly is using the current JohnHereToHelp twitter account. With John talking about trying to protect his online footprint while in hiding with the recent RedPill78 interview, the recent high use of this twitter account does not match someone trying to keep a low profile.
Has Santa Surfing taken on more than she could handle with this interview and its deep state repercussions? Either willingly or unwillingly been warned off the story?
I don't know. The deep state does have a poor track record in cleaning up its moral delimas. Things do look to be turning into a big convoluted mess. For now will just need to stay tuned as things develop.
In this 19 min presentation it sounds like Santa Surfing and JohnHereToHelp have had a falling out. John has provided an interview with another person, in which there are inconsistencies in the story. With the part on the Seth Rich murder, the evidence is pointing at two MS-13 gang members that where later killed. Santa Surfing does go into other inconsistence with Johns story.
John has taken any money that was given, has refused any security and legal support that was offered. Is John just a con man or has a psychological operation been applied to murky the waters and discredit John?
With how twitter banned all reference to JohnHerToHelp when his story first came out, I do question just who exactly is using the current JohnHereToHelp twitter account. With John talking about trying to protect his online footprint while in hiding with the recent RedPill78 interview, the recent high use of this twitter account does not match someone trying to keep a low profile.
Has Santa Surfing taken on more than she could handle with this interview and its deep state repercussions? Either willingly or unwillingly been warned off the story?
I don't know. The deep state does have a poor track record in cleaning up its moral delimas. Things do look to be turning into a big convoluted mess. For now will just need to stay tuned as things develop.
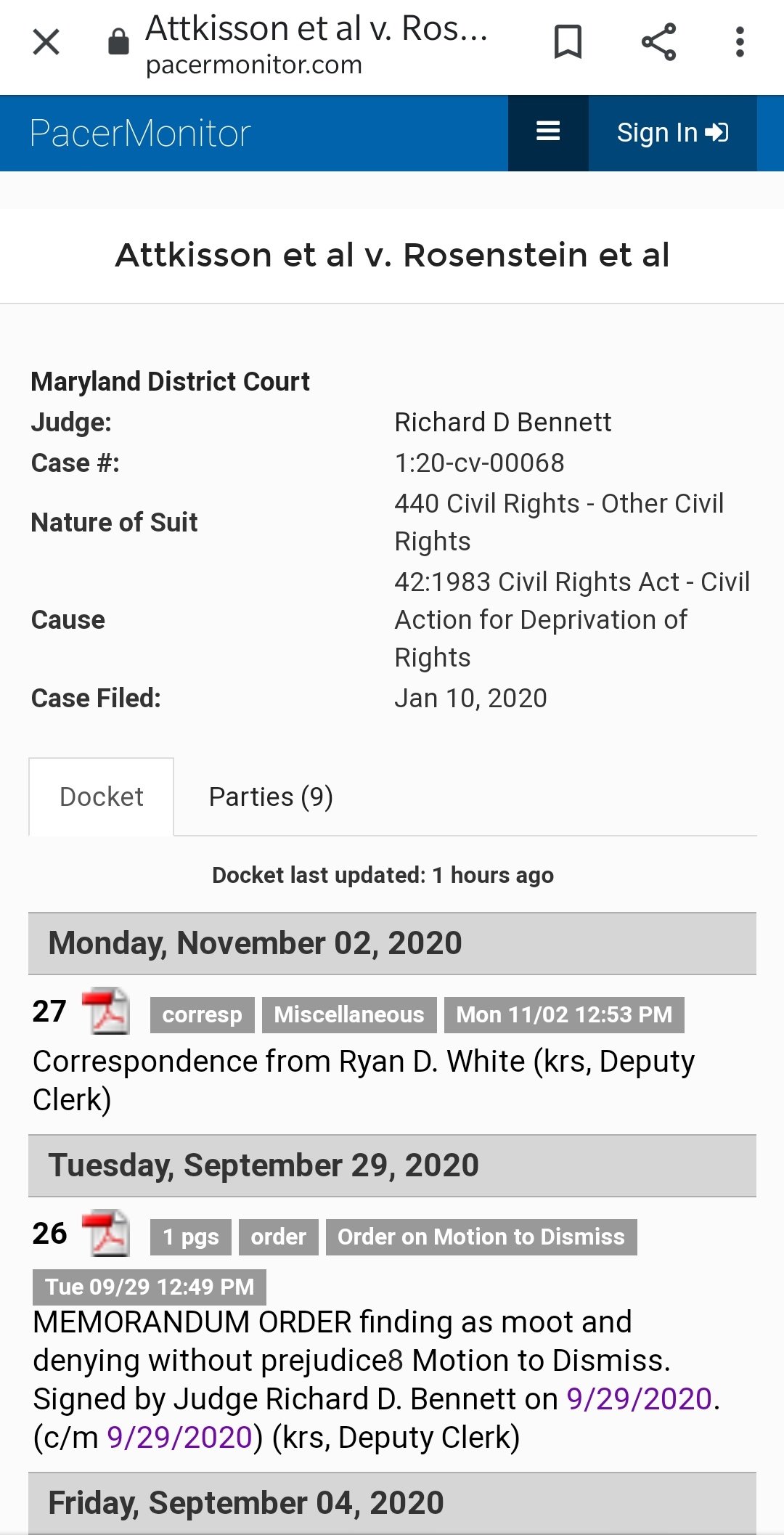
Looking into the court docket, it links back to James Howard Attkisson
Source
Sharyl Attkisson website is at sharylattkisson.com...
James Attkisson is a retired lawyer. He was also in law enforcement. He was the head of his SWAT team commander in Florida and he served in the Vietnam War as well.
Sharyl Attkisson is married to James Attkisson. Sharyl Attkisson is an Award-winning American writer and an investigative journalist. She hosted the show Full Measure with Sharyl Attkisson. She is known for her audacity of reporting on tough and controversial topics. She posts News Blogs independently on her own website.
Source
Sharyl Attkisson website is at sharylattkisson.com...
For the latest update in the case Attkisson v. DOJ and FBI
Sourc e
In March of 2019, an appellate panel of three judges determined the former Attorney General Eric Holder has immunity from Attkisson's claims.
Two of the three judges ruled Attkisson?s claims should be dismissed because she took too long, three years "and without success" to determine the names of the "John Doe" federal agents involved in the intrusions of her computers.
A third judge rightly dissented, understanding that Attkisson consistently attempted to identify the John Does but the Department of Justice continuously blocked discovery, filed protective orders and filed motions to dismiss in an attempt to obstruct. The government did not turn over a single piece of paper in response to more than a dozen subpoenas.
The dissenting judge called the government's actions "Kafkaesque" for obstructing Attkisson and then blaming her for "taking too long."
Attkisson continues to move forward with the lawsuit. The Department of Justice continues to spend tax money to fight her.
Sourc e
Just to help us out here. So, your saying that this word salad below isn't about you finding what you liked and you ran with it?
I think we all have to ask what is the reason for such a comment when you appear to be doing the same thing?
If it was one person saying things that seemed outlandish that even regardless of the corroborating facts, then I could agree we should proceed as if it wasn't true until we have more data and more witnesses. We see hundreds and hundreds of tidbits being corroborated that the left tries to say to us "now don't believe your lying eyes and ears".
From Seth Rich to the Clinton's being involved in the voting machines and calling up a Russia Russia Russia hoax, the dots are forming a BIG PICTURE that even those of you who think you are 'woke' can't ignore.
originally posted by: underwerks
What really happened:
Link
If all it takes is some guy saying what you want to believe on YouTube for you to believe, that pretty much says it all.
I think we all have to ask what is the reason for such a comment when you appear to be doing the same thing?
If it was one person saying things that seemed outlandish that even regardless of the corroborating facts, then I could agree we should proceed as if it wasn't true until we have more data and more witnesses. We see hundreds and hundreds of tidbits being corroborated that the left tries to say to us "now don't believe your lying eyes and ears".
From Seth Rich to the Clinton's being involved in the voting machines and calling up a Russia Russia Russia hoax, the dots are forming a BIG PICTURE that even those of you who think you are 'woke' can't ignore.
originally posted by: underwerks
What really happened:
At one point, the Russians used servers located in the U.S. to carry out the massive data exfiltration effort, the report confirms.
Much of the information was previously learned from the indictment of Viktor Borisovich Netyksho, the Russian officer in charge of Unit 26165. Netyksho is believed to be still at large in Russia.
But new details in the 488-page redacted report released by the Justice Department on Thursday offered new insight into how the GRU operatives hacked.
The operatives working for the Russian intelligence directorate, the GRU, sent dozens of targeted spearphishing emails in just five days to the work and personal accounts of Clinton Campaign employees and volunteers, as a way to break into the campaign’s computer systems.
The GRU hackers also gained access to the email account of John Podesta, Clinton’s campaign chairman, of which its contents were later published.
Using credentials they stole along the way, the hackers broke into the networks of the Democratic Congressional Campaign Committee days later. By stealing the login details of a system administrator who had “unrestricted access” to the network, the hackers broke into 29 computers in the ensuing weeks, and more than 30 computers on the DNC.
The operatives, known collectively as “Fancy Bear,” comprised several units tasked with specific operations. Mueller formally blamed Unit 26165, a division of the GRU specializing in targeting government and political organizations, for taking on the “primary responsibility for hacking the DCCC and DNC, as well as email accounts of individuals affiliated with the Clinton Campaign,” said the Mueller report.
The hackers used Mimikatz, a hacking tool used once an intruder is already in a target network, to collect credentials, and two other kinds of malware: X-Agent for taking screenshots and logging keystrokes, and X-Tunnel used to exfiltrate massive amounts of data from the network to servers controlled by the GRU. Mueller’s report found that Unit 26165 used several “middle servers” to act as a buffer between the hacked networks and the GRU’s main operations. Those servers, Mueller said, were hosted in Arizona — likely as a way to obfuscate where the attackers were located but also to avoid suspicion or detection.
In all, some 70 gigabytes of data were exfiltrated from Clinton’s campaign servers and some 300 gigabytes of data were obtained from the DNC’s network.
Meanwhile, another GRU hacking unit, Unit 74455, which helped disseminate and publish hacked and stolen documents, pushed the stolen data out through two fictitious personas. DCLeaks was a website that hosted the hacked material, while Guccifer 2.0 was a hacker-like figure who had a social presence and would engage with reporters.
Under pressure from the U.S. government, the two GRU-backed personas were shut down by the social media companies. Later, tens of thousands of hacked files were funneled to and distributed by WikiLeaks .
“I hope you’re able to find the 30,000 emails that are missing,” said then-candidate Trump at a press conference, referring to emails Clinton stored on a personal email server while she headed the State Department. Mueller’s report said “within approximately five hours” of those remarks, GRU officers began targeting for the first time Clinton’s personal office.
Link
If all it takes is some guy saying what you want to believe on YouTube for you to believe, that pretty much says it all.
edit on
11-11-2020 by Justoneman because: (no reason given)
edit on 11-11-2020 by Justoneman because: (no reason given)
With Youtube dropping this topic, here is one link on Bitchute:
JOHN HERE TO HELP_[THEIR] FINAL ATTEMPT AN INTERVIEW WITH "JOHNHERETOHELP" :CODED:
JOHN HERE TO HELP_[THEIR] FINAL ATTEMPT AN INTERVIEW WITH "JOHNHERETOHELP" :CODED:
He’s known on Twitter as @johnheretohelp , he’s been forced to use the name Ryan White, but his real name is Dr. Jonathan McGreevey. He’s been targeted, jailed, and tortured to ends you could never imagine..
Twitter Link
EXCLUSIVE! @Johnheretohelp | EXPOSED! Deep State - COVID, Jan 6, 'Vaccines', Stolen Election
Dr. Jonathan McGreevey joined Stew Peters for an exclusive 1-on-1, named high-ranking military officials, Nancy Pelosi, Anthony Fauci, Bill Gates, Deep State operatives responsible for the theft of the 2020 election, execution of Ashli Babbitt, January 6 set-up, COVID plans for mass murder and the 'vaccine' plot to commit genocide
new topics
-
America's Greatest Ally
General Chit Chat: 35 minutes ago -
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 5 hours ago -
Maestro Benedetto
Literature: 7 hours ago -
Is AI Better Than the Hollywood Elite?
Movies: 7 hours ago -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 10 hours ago -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 11 hours ago
top topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 5 hours ago, 26 flags -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 16 hours ago, 9 flags -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 12 hours ago, 8 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 16 hours ago, 8 flags -
Weinstein's conviction overturned
Mainstream News: 15 hours ago, 8 flags -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 13 hours ago, 7 flags -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 10 hours ago, 6 flags -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 13 hours ago, 5 flags -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 11 hours ago, 4 flags -
Is AI Better Than the Hollywood Elite?
Movies: 7 hours ago, 3 flags
active topics
-
America's Greatest Ally
General Chit Chat • 1 • : BingoMcGoof -
How ageing is" immune deficiency"
Medical Issues & Conspiracies • 35 • : annonentity -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three • 49 • : Freeborn -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues • 30 • : Asher47 -
Electrical tricks for saving money
Education and Media • 8 • : anned1 -
Is AI Better Than the Hollywood Elite?
Movies • 16 • : 5thHead -
Hate makes for strange bedfellows
US Political Madness • 48 • : Terpene -
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies • 17 • : BingoMcGoof -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics • 90 • : Lumenari -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs • 12 • : KrustyKrab