It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
NSA Quantum Program Leaked: Edward Snowden Reveals How US Government Spies On Offline Computers
page: 1share:
The latest leak from former National Security Agency contractor turned whistleblower Edward Snowden, published by the New York Times on Tuesday, revealed that the NSA has been using old-school technology to spy on offline computers. The NSA has used the secret program, codenamed Quantum, to monitor about 100,000 offline computers around the world.
NSA Quantum Program Leaked: Edward Snowden Reveals How US Government Spies On Offline Computers
They have been monitoring all of us and keeping the logs.
Quantum also targets iPhones and network servers. Over time, the NSA has updated the technology to make it easier to access the computer systems without needing physical access.
The reported indicated that the NSA has used this technology in attacks against Iran’s nuclear facilities and to monitor networks in China, Russia, the European Union, Saudi Arabia, India and Pakistan, and those of drug cartels.
Internationally, is this even legal?
President Obama is scheduled to announce changes to the NSA’s practices on Friday.
Is he going to announce what they are doing with all their logs, too?
Considering the hardware requirements, unless they had somehow managed to make ALL computers have the hardware installed, and ALL USB cables specially
created to meet their requirements as well, we wouldn't all be monitored this way.
Even in the section the OP quoted it states "about 100,000" modified in this manner. So, given the NSA is behind this....let's jack that number up to about 10 million...just to be safe
Considering there are over 300 million residents in the US alone....oh...that's what...about 3.1% ?
Even in the section the OP quoted it states "about 100,000" modified in this manner. So, given the NSA is behind this....let's jack that number up to about 10 million...just to be safe
Considering there are over 300 million residents in the US alone....oh...that's what...about 3.1% ?
zeroBelief
Considering the hardware requirements, unless they had somehow managed to make ALL computers have the hardware installed, and ALL USB cables specially created to meet their requirements as well, we wouldn't all be monitored this way.
Even in the section the OP quoted it states "about 100,000" modified in this manner. So, given the NSA is behind this....let's jack that number up to about 10 million...just to be safe
Considering there are over 300 million residents in the US alone....oh...that's what...about 3.1% ?
3.1? Jeez, that's nothing. But what about these Smart Meters being installed everywhere?
President Obama is scheduled to announce changes to the NSA’s practices on Friday.
More intrusive practices?
The spying has been proven to do absolutely nothing to prevent terrorism. It is extensively used to find people involved in the drug trade, more
specifically people who make money off the drug trade that are not backed by the DEA or CIA.
It also worked well to find dirt on people like David Petraeus. Do you really believe the official story on how he got caught having an affair? He was not on-board with team Obama and all they had to do was manufacture a story on how they legally were able to hack his computers.
Strange times we are living in.
It also worked well to find dirt on people like David Petraeus. Do you really believe the official story on how he got caught having an affair? He was not on-board with team Obama and all they had to do was manufacture a story on how they legally were able to hack his computers.
Strange times we are living in.
reply to post by zeroBelief
I wouldn't be so sure about that. Cottonmouth is only one of the methods they use to monitor data in an isolated (no network) environment. If you think about the sheer number of wireless networks out there, and the fact that they already said Nightstand can inject packets of data from 8 miles away, I'd bet money that they can pretty easily intercept data from pretty much any standard wireless network if they really wanted to. They also mentioned micro-circuitry that's used in a similar fashion to the Cottonmouth method.
Jesus, as I was writing this I just remembered the whole RSA scandal that was uncovered a few weeks back (Source). Talk about a perfect way to distribute Cottonmouth!? Who's to say that every one of the RSA key's sold and used with this flawed algorithm designed by the NSA, also doesn't double as a radio-transmitter like Cottonmouth? It'd be the perfect double whammy:
Step 1: If the user is online, they can use the backdoor built-in to the algorithm to gain real-time access, like a trojan virus. This would then allow further installation/distribution of software to keep the door "held open" too.
Step 2: In the event that the PC was offline yet still accessing a secure date source via the RSA key, they would simply need a little briefcase (Nightstand) located somewhere within their acceptable 8-mile radius to accomplish the exact same thing.
This is probably worthy of another thread, but directly related to the OP. S&F for the find, should be interesting come Friday.
I wouldn't be so sure about that. Cottonmouth is only one of the methods they use to monitor data in an isolated (no network) environment. If you think about the sheer number of wireless networks out there, and the fact that they already said Nightstand can inject packets of data from 8 miles away, I'd bet money that they can pretty easily intercept data from pretty much any standard wireless network if they really wanted to. They also mentioned micro-circuitry that's used in a similar fashion to the Cottonmouth method.
Jesus, as I was writing this I just remembered the whole RSA scandal that was uncovered a few weeks back (Source). Talk about a perfect way to distribute Cottonmouth!? Who's to say that every one of the RSA key's sold and used with this flawed algorithm designed by the NSA, also doesn't double as a radio-transmitter like Cottonmouth? It'd be the perfect double whammy:
Step 1: If the user is online, they can use the backdoor built-in to the algorithm to gain real-time access, like a trojan virus. This would then allow further installation/distribution of software to keep the door "held open" too.
Step 2: In the event that the PC was offline yet still accessing a secure date source via the RSA key, they would simply need a little briefcase (Nightstand) located somewhere within their acceptable 8-mile radius to accomplish the exact same thing.
This is probably worthy of another thread, but directly related to the OP. S&F for the find, should be interesting come Friday.
edit on 16-1-2014 by parad0x122 because: typo
AfterInfinity
zeroBelief
Considering the hardware requirements, unless they had somehow managed to make ALL computers have the hardware installed, and ALL USB cables specially created to meet their requirements as well, we wouldn't all be monitored this way.
Even in the section the OP quoted it states "about 100,000" modified in this manner. So, given the NSA is behind this....let's jack that number up to about 10 million...just to be safe
Considering there are over 300 million residents in the US alone....oh...that's what...about 3.1% ?
3.1? Jeez, that's nothing. But what about these Smart Meters being installed everywhere?
Yepp. Smart meters, not a fan of those either. But they're not as bad as them eyeballing your internet comings and goings though, IMHO.
parad0x122
reply to post by zeroBelief
I wouldn't be so sure about that. Cottonmouth is only one of the methods they use to monitor data in an isolated (no network) environment. If you think about the sheer number of wireless networks out there, and the fact that they already said Nightstand can inject packets of data from 8 miles away, I'd bet money that they can pretty easily intercept data from pretty much any standard wireless network if they really wanted to. They also mentioned micro-circuitry that's used in a similar fashion to the Cottonmouth method.
The discussion was about the Cottonmouth devices...Operation Quantum (or whatever the silly thing is called)....
Not about *all* the ways the NSA could possibly snoop on you.
The OP said this operation was keeping tabs on us all. I simply said that 100,000 implementations of it is far from all of us, let alone the more likely figure of 10million, as I proposed the real number of implementations would be closer to.
So, sure, let's talk other forms. Frankly, I'm starting to think that BadBIOS is simply a more up to to date version of Cottonmouth that slowly spreads itself and replicates via software alone....
Any thoughts on that ?
reply to post by zeroBelief
Very true, and I wholeheartedly agree on the figure not being anywhere near ALL of us, especially only using one method of surveillance/infection such as Cottonmouth. Definitely not trying to de-rail this thread either, so apologies to OP for any confusion my previous post may have caused. To be honest, I'm not up to snuff on BadBIOS, but if it's anything like it sounds, it seems absolutely feasible! It's scary, but the more and more I hear about theses NSA surveillance mechanisms, the more they resemble existing malware/spyware/trojan virii. Who would've thought that the very same department who is partially responsible for prevention/monitoring of cyber crime is using the same tools it's opponent s(hackers) have been using for decades.
Very true, and I wholeheartedly agree on the figure not being anywhere near ALL of us, especially only using one method of surveillance/infection such as Cottonmouth. Definitely not trying to de-rail this thread either, so apologies to OP for any confusion my previous post may have caused. To be honest, I'm not up to snuff on BadBIOS, but if it's anything like it sounds, it seems absolutely feasible! It's scary, but the more and more I hear about theses NSA surveillance mechanisms, the more they resemble existing malware/spyware/trojan virii. Who would've thought that the very same department who is partially responsible for prevention/monitoring of cyber crime is using the same tools it's opponent s(hackers) have been using for decades.
edit on 16-1-2014 by parad0x122 because: double reply
reply to post by ChefSlug
What's next on the list for the NSA to invade every living human being's privacy? Toilet cameras? Meh...they're probably already there.
What's next on the list for the NSA to invade every living human being's privacy? Toilet cameras? Meh...they're probably already there.
zeroBelief
Considering the hardware requirements, unless they had somehow managed to make ALL computers have the hardware installed, and ALL USB cables specially created to meet their requirements as well, we wouldn't all be monitored this way.
Even in the section the OP quoted it states "about 100,000" modified in this manner. So, given the NSA is behind this....let's jack that number up to about 10 million...just to be safe
Ha ha, I love your math there. Okay well it wouldn't be all, it's probably partially a targeted program used for field operations or something like that.
edit on 16pmThu, 16 Jan 2014 13:33:11 -0600kbpmkAmerica/Chicago by darkbake because: (no reason given)
parad0x122
reply to post by zeroBelief
Very true, and I wholeheartedly agree on the figure not being anywhere near ALL of us, especially only using one method of surveillance/infection such as Cottonmouth. Definitely not trying to de-rail this thread either, so apologies to OP for any confusion my previous post may have caused. To be honest, I'm not up to snuff on BadBIOS, but if it's anything like it sounds, it seems absolutely feasible! It's scary, but the more and more I hear about theses NSA surveillance mechanisms, the more they resemble existing malware/spyware/trojan virii. Who would've thought that the very same department who is partially responsible for prevention/monitoring of cyber crime is using the same tools it's opponent s(hackers) have been using for decades.edit on 16-1-2014 by parad0x122 because: double reply
Where do you think all the hackers who get caught end up? Work for us or rot in prison forevermore
Lil
I hate how the conservatives call him a terrorist. He has freed the people, no ifs, ands or buts about it.
doggoneit666
reply to post by ChefSlug
What's next on the list for the NSA to invade every living human being's privacy? Toilet cameras? Meh...they're probably already there.
They've already done smartphone cameras, there's always been suspicion about the Xbox Kinect, and cable-TV boxes that might have little cameras in them. If you look at a smartphone, a high-resolution camera isn't much bigger than a LED.
I have my suspicions of those hotel beds with the extension hose bedlights. Always thought they would be the perfect place to put a concealed camera.
The next goal would be fingerprint recognition on household appliances. Voice recognition has already been done.
When The first of the Snowden files was released, I was not surprised. Like many on ATS, I was in the I-told-you-so group.
At this point, I am genuinely apalled and terribly disconcerted. The United States of America, once an unassailable bastion of liberty unique to the Earth, is dangerously far down the path to irreversible loss of freedom. With this kind of power in the hands of Presidents, Congress, overzealous bureaucrats, self-serving LEO's...sooner or later it will be used against every one of us.
This particular article is much more alarming alongside the revelation from December that the federal government regularly intercepts electronics mid-shipment from UPS and FedEx. Gives them a chance to install one of these transmitter/receivers....
At this point, I am genuinely apalled and terribly disconcerted. The United States of America, once an unassailable bastion of liberty unique to the Earth, is dangerously far down the path to irreversible loss of freedom. With this kind of power in the hands of Presidents, Congress, overzealous bureaucrats, self-serving LEO's...sooner or later it will be used against every one of us.
This particular article is much more alarming alongside the revelation from December that the federal government regularly intercepts electronics mid-shipment from UPS and FedEx. Gives them a chance to install one of these transmitter/receivers....
reply to post by ChefSlug
"The report comes just days before President Obama is expected to announce new restrictions on surveillance programs that will curtail the NSA's activities."
New restrictions? Curtail their activities? LOL!!!
Now they'll just deny they do not do what they are restricted not to do, they are "in compliance with the law." Sorry folks, but you can't stop this beast.
"The report comes just days before President Obama is expected to announce new restrictions on surveillance programs that will curtail the NSA's activities."
New restrictions? Curtail their activities? LOL!!!
Now they'll just deny they do not do what they are restricted not to do, they are "in compliance with the law." Sorry folks, but you can't stop this beast.
reply to post by John_Rodger_Cornman
Err huh? He was talking about Virii and Trojans and stuff yeah?
I was responding that The hackers who have been caught are now working for the NSA, hope that clarifies it, guess I shouldn't try to be sarcastic lol
Lil
Err huh? He was talking about Virii and Trojans and stuff yeah?
To be honest, I'm not up to snuff on BadBIOS, but if it's anything like it sounds, it seems absolutely feasible! It's scary, but the more and more I hear about theses NSA surveillance mechanisms, the more they resemble existing malware/spyware/trojan virii. Who would've thought that the very same department who is partially responsible for prevention/monitoring of cyber crime is using the same tools it's opponent s(hackers) have been using for decades.
I was responding that The hackers who have been caught are now working for the NSA, hope that clarifies it, guess I shouldn't try to be sarcastic lol
Lil
edit on 1/18/2014 by Lilroanie because: fixed quote tag
edit on 1/18/2014 by Lilroanie because: again grrrr
reply to post by ChefSlug
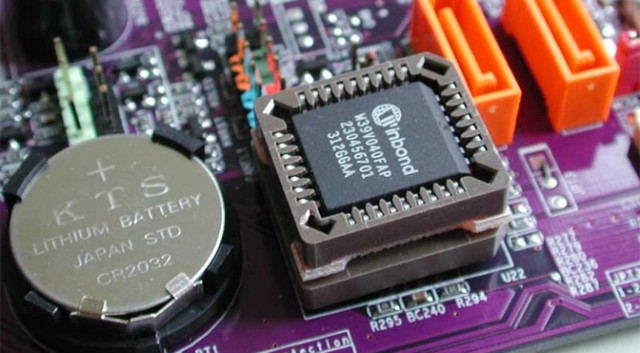 Bios Chip/Firmware (embedded software in the hardware)
Bios Chip/Firmware (embedded software in the hardware)
Malicious Firmware: How the NSA, and China, can hack into anything, and anyone, anywhere and at any time from any device.
Rakshasa: The hardware backdoor that China could embed in every computer
Check this out, from a hacker friend of mine re: technical capabilities - highly related and directly relevant to the OP, in particular as it related to the Iran nuclear hack.
I don't have the technical knowhow to explain it, but many of you will.
-------------------
This is in ref to the Proof of concept presented at BlackHat 2012 by Johnathan Brassard.
www.extremetech.com...
www.forbes.com...
This is Brossard’s actual talk at Def Con 12 in which he demonstrates the Proof of Concept.
LINK
We knew of our variant already extant in the wild some 12 -18 months before this presentation.
LINK
GOOGLE HEADLINES AND PAGES WHERE OUR SPECIFIC VARIANT IS DISCUSSED AT LENGTH W/ VARYING DEGREES OF INCREDULITY:
LINK
This is the FaceBook Group that the core of us who first observed and described it created:
LINK
THIS IS THE ORIGINAL THREAD…
LINK
THESE ARE HEADLINES ABOUT THE DARPA PROJECT TO ADDRESS THIS ISSUE ON THE SUPPLY CHAIN SIDE
LINK
THIS MAY OR MAY NOT BE THE PARTY WHO FIRST INTRODUCED THIS TYPE OF TECHNOLOGY IN THE WILD FOR TARGETED STATE LEVEL ESPIONAGE…
en.wikipedia.org...
AND THE BROADER CLASS OF MALWARE THAT IT BELONGS TO:
en.wikipedia.org...
THIS ATTACK WAS ITS EARLY PRECURSOR
en.wikipedia.org...

Malicious Firmware: How the NSA, and China, can hack into anything, and anyone, anywhere and at any time from any device.
Rakshasa: The hardware backdoor that China could embed in every computer
Check this out, from a hacker friend of mine re: technical capabilities - highly related and directly relevant to the OP, in particular as it related to the Iran nuclear hack.
I don't have the technical knowhow to explain it, but many of you will.
-------------------
This is in ref to the Proof of concept presented at BlackHat 2012 by Johnathan Brassard.
www.extremetech.com...
www.forbes.com...
This is Brossard’s actual talk at Def Con 12 in which he demonstrates the Proof of Concept.
LINK
We knew of our variant already extant in the wild some 12 -18 months before this presentation.
LINK
GOOGLE HEADLINES AND PAGES WHERE OUR SPECIFIC VARIANT IS DISCUSSED AT LENGTH W/ VARYING DEGREES OF INCREDULITY:
LINK
This is the FaceBook Group that the core of us who first observed and described it created:
LINK
THIS IS THE ORIGINAL THREAD…
LINK
THESE ARE HEADLINES ABOUT THE DARPA PROJECT TO ADDRESS THIS ISSUE ON THE SUPPLY CHAIN SIDE
LINK
THIS MAY OR MAY NOT BE THE PARTY WHO FIRST INTRODUCED THIS TYPE OF TECHNOLOGY IN THE WILD FOR TARGETED STATE LEVEL ESPIONAGE…
en.wikipedia.org...
AND THE BROADER CLASS OF MALWARE THAT IT BELONGS TO:
en.wikipedia.org...
THIS ATTACK WAS ITS EARLY PRECURSOR
en.wikipedia.org...
edit on 19-1-2014 by NewAgeMan because: (no reason given)
edit on 19-1-2014 by NewAgeMan because: (no reason given)
new topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 2 hours ago -
Maestro Benedetto
Literature: 4 hours ago -
Is AI Better Than the Hollywood Elite?
Movies: 4 hours ago -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 7 hours ago -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 8 hours ago -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 8 hours ago -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum: 10 hours ago -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 10 hours ago -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 10 hours ago
top topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies: 2 hours ago, 23 flags -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 13 hours ago, 9 flags -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 16 hours ago, 8 flags -
Weinstein's conviction overturned
Mainstream News: 12 hours ago, 8 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 13 hours ago, 8 flags -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 10 hours ago, 7 flags -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 8 hours ago, 7 flags -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs: 7 hours ago, 6 flags -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 10 hours ago, 5 flags -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 8 hours ago, 4 flags
active topics
-
President BIDEN's FBI Raided Donald Trump's Florida Home for OBAMA-NORTH KOREA Documents.
Political Conspiracies • 8 • : WeMustCare -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 685 • : RelSciHistItSufi -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 74 • : Justoneman -
Starburst galaxy M82 - Webb Vs Hubble
Space Exploration • 6 • : Arbitrageur -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 264 • : stelth2 -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People • 22 • : stelth2 -
VirginOfGrand says hello
Introductions • 9 • : TheMichiganSwampBuck -
Las Vegas UFO Spotting Teen Traumatized by Demon Creature in Backyard
Aliens and UFOs • 10 • : pianopraze -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics • 84 • : Daughter2v2 -
Is AI Better Than the Hollywood Elite?
Movies • 12 • : rickymouse
