It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: Eilasvaleleyn
Also, does your experience involve working on the specific software involved in the case, or do you have its exact specifications that make the claimed story impossible? If not, your opinion is as worthless as mine from a technological perspective. If I know all about one type of piano... Well, not all pianos are exactly the same.
Actually, I don't even know why I'm responding to this... It's obviously some sort of bait.
Well actually, while I was not a member of the development team, as a software architect I DO have very good idea of what was/is involved. Did you know that the provider (NGP VAN) has a "developer's" program? A support area, and feedback system for those who wish to use their API (application program interface)...the API tells me just about everything I need...to connect to their services, and to analyze their services...
Seems to me that insisting on an "audit" would be a good first obfuscation...
No...sorry, not bait...just my opinion as a professional software developer.
edit on 25-12-2015 by tanka418 because: (no reason given)
Oh give me a break...... Quickpickneakk University in Connecti-cut.... Yea what is that, some stripmall leased building with surplus government
computers and a back room made into a cafeteria with cheese sandwiches and Tang (the drink of astronauts) for lunch..... ?
Friggen media.......
The Earth is Flat, news flash....... sources at World renouned Quinnipiac University have polled the campus and announce their poll findings......... 'the earth is flat' ... and life was brought here by "Q" from the 'Continuum.
Wait.......... !!!!! are we not here to 'deny ignorance' ? 11 more months and we will have our 'real' statistics.
Friggen media.......
The Earth is Flat, news flash....... sources at World renouned Quinnipiac University have polled the campus and announce their poll findings......... 'the earth is flat' ... and life was brought here by "Q" from the 'Continuum.
Wait.......... !!!!! are we not here to 'deny ignorance' ? 11 more months and we will have our 'real' statistics.
a reply to: tanka418
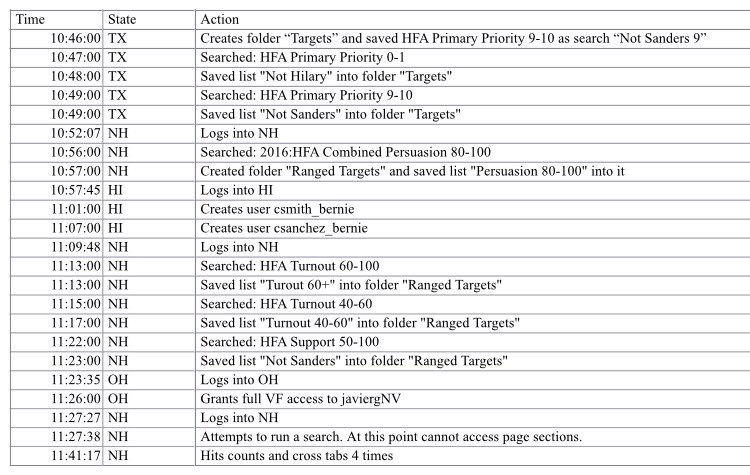
Have you seen the logs in question?
It seems they no one outside NGP VAN has, what was show in court seems to be spreadsheets rather than server logs:
source
Have you seen the logs in question?
It seems they no one outside NGP VAN has, what was show in court seems to be spreadsheets rather than server logs:

The above screenshot is, at first glance, an audit trail of actions taken by a particular user within the NGP-VAN system. To a layman, this appears very much as one might think a system produced audit trail would. It has all the features we associate with technical mumbo-jumbo, including highly specific timestamps (down to the second), consistency among description (searches preceded with “Searched:”), etc.
This sample alone, however, gives us pretty clear indications that this is not an actual log. What you’re seeing in Exhibit A is, at best, a human interpretation of a more technical log, at worst, a complete fabrication. As with most things, the reality probably lies somewhere in the middle. That is to say, I’m not claiming that these are complete fabrications, but rather, likely a reduction of information contained in multiple logs which are not necessarily as clear about what is going on as are the descriptions we see here.
source
edit on 25-12-2015 by AlaskanDad because: added source and fixed typo's
originally posted by: AlaskanDad
.
The above screenshot is, at first glance, an audit trail of actions taken by a particular user within the NGP-VAN system
No, I've not seen any logs, it would not be typical of the provider to provide that data. Logs typically contain a great deal of, shall we say; "esoteric data" which is nearly impossible for a lay person to understand. much of it being specific to the software being run. And, then of course; it depends on what kind of "log" you're talking about.
What you have shown; is an absolute joke! I don't know how anybody could mistake that for a log fragment!
edit on 25-12-2015 by tanka418 because: (no reason given)
new topics
-
More Bad News for Labour and Rachel Reeves Stole Christmas from Working Families
Regional Politics: 5 hours ago -
Light from Space Might Be Travelling Instantaneously
Space Exploration: 6 hours ago -
The MSM has the United Healthcare assassin all wrong.
General Conspiracies: 7 hours ago -
2025 Bingo Card
The Gray Area: 7 hours ago -
The Mystery Drones and Government Lies
Political Conspiracies: 9 hours ago
top topics
-
Pelosi injured in Luxembourg
Other Current Events: 16 hours ago, 21 flags -
The Mystery Drones and Government Lies
Political Conspiracies: 9 hours ago, 11 flags -
2025 Bingo Card
The Gray Area: 7 hours ago, 7 flags -
The MSM has the United Healthcare assassin all wrong.
General Conspiracies: 7 hours ago, 7 flags -
Light from Space Might Be Travelling Instantaneously
Space Exploration: 6 hours ago, 7 flags -
More Bad News for Labour and Rachel Reeves Stole Christmas from Working Families
Regional Politics: 5 hours ago, 6 flags
