It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
I don't really know too much about this subject, but having had some education in computer programming, particularly COBOL, I'm well aware that any
system can be hacked into and I have always had an adversion to internet banking as a result.
So perhaps my paranoia is unfounded, but this article makes me think twice
"The stakes are potentially enormous, since once data is hijacked, the perpetrator can copy and then comb through any unencrypted data freely — reading email and spreadsheets, extracting credit card numbers, and capturing vast amounts of sensitive information."
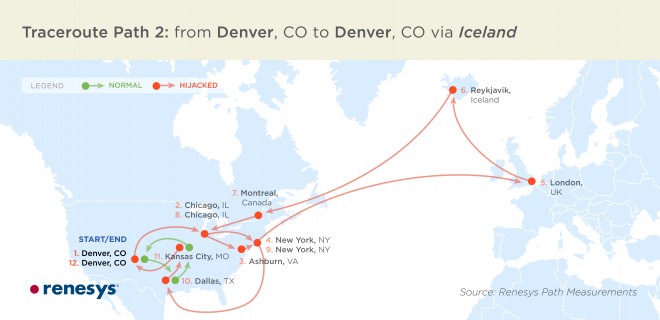
Hijacked traffic went all the way to Iceland, where it may have been copied before being released to its intended destination. The green arrows show the path the traffic should have traveled; the red arrows show the path it took.
Full story:
www.wired.com...
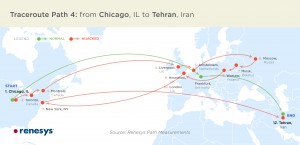
Map showing the long and winding path taken by traffic headed from Chicago to Iran. The green route represents the normal route the traffic takes; the red route is the hijacked route it took through Belarus.
So perhaps my paranoia is unfounded, but this article makes me think twice
In 2008, two security researchers at the DefCon hacker conference demonstrated a massive security vulnerability in the worldwide internet traffic-routing system — a vulnerability so severe that it could allow intelligence agencies, corporate spies or criminals to intercept massive amounts of data, or even tamper with it on the fly. The traffic hijack, they showed, could be done in such a way that no one would notice because the attackers could simply re-route the traffic to a router they controlled, then forward it to its intended destination once they were done with it, leaving no one the wiser about what had occurred. Now, five years later, this is exactly what has happened.
"The stakes are potentially enormous, since once data is hijacked, the perpetrator can copy and then comb through any unencrypted data freely — reading email and spreadsheets, extracting credit card numbers, and capturing vast amounts of sensitive information."

Hijacked traffic went all the way to Iceland, where it may have been copied before being released to its intended destination. The green arrows show the path the traffic should have traveled; the red arrows show the path it took.
Full story:
www.wired.com...

Map showing the long and winding path taken by traffic headed from Chicago to Iran. The green route represents the normal route the traffic takes; the red route is the hijacked route it took through Belarus.
Classic man in the middle attack. The only way around it would be to have known routes and not to accept packets from unknown origin/ routes.
Any data that's sent over the internet can be intercepted and relayed to its intended origin.
Save a copy of the packets intercepted and decode at your will.
Anything made by man can be re engineered.
The internet will never be 100% secure.
Vpn is the only way to secure your traffic, and then your sill at the mercy of the endpoints security.
Also, Defcon is not a hacker conference per say. Its a network analysis and security conference.
Any data that's sent over the internet can be intercepted and relayed to its intended origin.
Save a copy of the packets intercepted and decode at your will.
Anything made by man can be re engineered.
The internet will never be 100% secure.
Vpn is the only way to secure your traffic, and then your sill at the mercy of the endpoints security.
Also, Defcon is not a hacker conference per say. Its a network analysis and security conference.
edit on 12/7/2013 by shaneslaughta because:
(no reason given)
reply to post by pandersway
I saw this on Digg the other day. Without any knowledge.. I am thinking it was China, Russia or Isreal. Clearly America just steals data without the complex run a round. If I had to bet money.. I bet it was Russia. Followed by China. I don't believe it was someone. It was somebody. It was a state security apparatus.
I saw this on Digg the other day. Without any knowledge.. I am thinking it was China, Russia or Isreal. Clearly America just steals data without the complex run a round. If I had to bet money.. I bet it was Russia. Followed by China. I don't believe it was someone. It was somebody. It was a state security apparatus.
edit on 7-12-2013 by GArnold because: (no reason given)
As soon as i read it i knew it was a BGP (Border Gateway Protocol) exploit, a lot of internet protocols are not designed with any form of security by
default which is why IP V6 is designed with some basic security more from the ground up than the traditions V4 and changes in BGP propegate to other
core routers with no checking by default IIRC so its one of those things that could very easily be abused to cause a real internet clusterf---
One of the things about the internet is the fact the packets could some from anywhere as its designed to be a resilient network , obviously for secure communications you would want to do more checking but generally thats going to be at the higher levels
I do remember where the Chinese mucked up the BGP settings on one of their routers and loads of stuff including US DOD stuff went through their routers for about 30 mins or so and that caused a right stink at the time
One of the things about the internet is the fact the packets could some from anywhere as its designed to be a resilient network , obviously for secure communications you would want to do more checking but generally thats going to be at the higher levels
I do remember where the Chinese mucked up the BGP settings on one of their routers and loads of stuff including US DOD stuff went through their routers for about 30 mins or so and that caused a right stink at the time
reply to post by GArnold
It could be anyone, anywhere. Thus is the downfall of the internet. The inter-connectivity of the net, and how it routes data through nodes. Its also how the net is so stable, routing the data through endpoint nodes that respond fastest.
The whole system is flawed from a security standpoint.
It could be anyone, anywhere. Thus is the downfall of the internet. The inter-connectivity of the net, and how it routes data through nodes. Its also how the net is so stable, routing the data through endpoint nodes that respond fastest.
The whole system is flawed from a security standpoint.
Maxatoria
I do remember where the Chinese mucked up the BGP settings on one of their routers and loads of stuff including US DOD stuff went through their routers for about 30 mins or so and that caused a right stink at the time
Do you know why the DOD and other agencies use the public internet? Why dont they use a network controlled wholly by them? Maybe one that's isolated from the WEB?
shaneslaughta
reply to post by GArnold
It could be anyone, anywhere. Thus is the downfall of the internet. The inter-connectivity of the net, and how it routes data through nodes. Its also how the net is so stable, routing the data through endpoint nodes that respond fastest.
The whole system is flawed from a security standpoint.
I tend to disagree. It had to be someone with vast resources as well as the ability to do it. It almost had to be a state actor in my opinion..I could be wrong about who it was but I would as I said bet money on Russia or China.
For that matter it could have been any of the five eyes partners. I tend to rule out the US they were acting with impunity and never for a second thought a Snowden would appear. It could have been GCHQ. Austrailia. New Zealand of even Canada. I would not rule out Isreal either. They were an important part of Stuxnet and Olympic Games.
edit on 7-12-2013 by GArnold because: (no reason given)
reply to post by GArnold
It can be anyone with a good broadband internet connection that can throughput enormous amounts of data.
Anytime data is routed through nodes its subject to being misused. The internet is only as secure as the nodes and endpoints that pass the data lets say from Facebook to yourself.
You may have a dozen route hops or more before you receive your page.
Every hop to a different node is another chance someone can DATA LOG you.
It can be anyone with a good broadband internet connection that can throughput enormous amounts of data.
Anytime data is routed through nodes its subject to being misused. The internet is only as secure as the nodes and endpoints that pass the data lets say from Facebook to yourself.
You may have a dozen route hops or more before you receive your page.
Every hop to a different node is another chance someone can DATA LOG you.
For those curious about routes your data takes between sites and yourself please check this link out.
TracRoute
Feel free to run a trace on any site url or ip you use.
You can see how your data is routed through nodes.
You can take the nodes ip and check out who owns it.
TracRoute
Feel free to run a trace on any site url or ip you use.
You can see how your data is routed through nodes.
You can take the nodes ip and check out who owns it.
reply to post by shaneslaughta
found the article here
it affected .gov and .mil domains and basically all emails/webtraffic to the sites would of been routed through China so while it would not have had any traffic for classified stuff any and all emails into the us goverment would of been read by china before the intended recipient and who knows what could of been read in those 18 mins? and theres always a chance of some idiot sending themselves an email of a classified document after working on it from home
found the article here
it affected .gov and .mil domains and basically all emails/webtraffic to the sites would of been routed through China so while it would not have had any traffic for classified stuff any and all emails into the us goverment would of been read by china before the intended recipient and who knows what could of been read in those 18 mins? and theres always a chance of some idiot sending themselves an email of a classified document after working on it from home
read the wired story...this was around the 2008 collapse...seems more than coincidental....remember that most of the 2008 problem came from the
entirely unregulated derivative market, with untold trillions of dollars in deals coursing around the globe...someone made money, or someone covered
their ass.
jimmyx
2nd post wrong
edit on 7-12-2013 by jimmyx because: (no reason given)
shaneslaughta
reply to post by GArnold
It could be anyone, anywhere. Thus is the downfall of the internet. The inter-connectivity of the net, and how it routes data through nodes. Its also how the net is so stable, routing the data through endpoint nodes that respond fastest.
The whole system is flawed from a security standpoint.
Sort of exactly..
It is designed this way so that there would always be a connection between point A and point B. It's designed to find a stable route, not necessarily the fastest.
It was very good back in the 60's & 70's.
What is more worrying to me is the amount of unencrypted stuff people are sending willy nilly over the net thinking they have an iota of privacy and wondering why there are people snaffling up terabytes of it..
reply to post by winofiend
By fastest i mean the lowest latency, not speed of the host.
The truly scary part is that the packets that hold even secure data have a hash that holds the decryption key.
While the packet can not be tampered with in route, it can be copied and then unencrypted.
The quieter you are, the more your able to hear.
By fastest i mean the lowest latency, not speed of the host.
The truly scary part is that the packets that hold even secure data have a hash that holds the decryption key.
While the packet can not be tampered with in route, it can be copied and then unencrypted.
The quieter you are, the more your able to hear.
reply to post by shaneslaughta
I still tend to think evidence will end up proving it was a state actor. I cannot believe this is joe blow anonymous or a similar group behind this. In my opinion it had to be someone with funds behind them and the actual ability to do this for so long without being caught.
The US has been tapping data since 2001 at leeast. Other countries with or without Snowden had to suspect we could do it. They have to had plans to deal with it and apparatus in place to make it happen.
The Chinese have been breaking into American systems for a long time. I suspect if they can do it... So can Russia. China has 1.4 Billion People. They have the highest percentage of people born who turn out with Genius IQs on the planet. When you combine the population and the rate of genius in my mind that makes for a very dynamic opponent who most likely has a vastly superior number of IT types than the US has at its disposal.
I still tend to think evidence will end up proving it was a state actor. I cannot believe this is joe blow anonymous or a similar group behind this. In my opinion it had to be someone with funds behind them and the actual ability to do this for so long without being caught.
The US has been tapping data since 2001 at leeast. Other countries with or without Snowden had to suspect we could do it. They have to had plans to deal with it and apparatus in place to make it happen.
The Chinese have been breaking into American systems for a long time. I suspect if they can do it... So can Russia. China has 1.4 Billion People. They have the highest percentage of people born who turn out with Genius IQs on the planet. When you combine the population and the rate of genius in my mind that makes for a very dynamic opponent who most likely has a vastly superior number of IT types than the US has at its disposal.
edit on 7-12-2013 by GArnold because: (no reason given)
edit on 7-12-2013 by GArnold because: (no reason given)
reply to post by shaneslaughta
When I did network maintenance at a small non-profit 10 years ago, I always received secure packets through FTP methods, but maybe that was then. And isn't it FTP that is being used by global members of the nuclear community to exchange information and questions about nuclear power plants? At any rate, the global nuclear community does seem to have a secure internet communication protocol, whatever it is.
Such "gaping holes" in the internet may be how security problems have arisen with the ownership of bitcoins. Some say that bitcoins are a DARPA scheme, tht every large holder of bitcoins has been robbed. The idea is to get people to use bitcoins then take them from so many people that the people demand a chip implant to facilitate safe bitcoins transactions. Etc. etc., you can see where that theory is going.
When I did network maintenance at a small non-profit 10 years ago, I always received secure packets through FTP methods, but maybe that was then. And isn't it FTP that is being used by global members of the nuclear community to exchange information and questions about nuclear power plants? At any rate, the global nuclear community does seem to have a secure internet communication protocol, whatever it is.
Such "gaping holes" in the internet may be how security problems have arisen with the ownership of bitcoins. Some say that bitcoins are a DARPA scheme, tht every large holder of bitcoins has been robbed. The idea is to get people to use bitcoins then take them from so many people that the people demand a chip implant to facilitate safe bitcoins transactions. Etc. etc., you can see where that theory is going.
edit on 12/7/2013 by Uphill because: (no reason given)
reply to post by pandersway
These are all thought-provoking comments and they have given me quite an insight into the workings of the net I wasn't completely aware of.
These are all thought-provoking comments and they have given me quite an insight into the workings of the net I wasn't completely aware of.
reply to post by pandersway
No it isn't... Your computer is very vulnerable especially if you aren't using an open source OS you have no clue or control of what it going on in your machine. In any case I share your distrust and it seems to be the only rational outcome. I also do not do banking from my computer and even if I take steps to secure it I think of it as being fully accessible to external access and so act accordingly.
I have always had an adversion to internet banking as a result. So perhaps my paranoia is unfounded
No it isn't... Your computer is very vulnerable especially if you aren't using an open source OS you have no clue or control of what it going on in your machine. In any case I share your distrust and it seems to be the only rational outcome. I also do not do banking from my computer and even if I take steps to secure it I think of it as being fully accessible to external access and so act accordingly.
reply to post by Panic2k11
Just about everyone I know does internet banking and uses their credit cards over the net....I've been the odd ball because I just know that if the security pgms, encryption coding etc is man-made, it can be hacked into. It's good to read others who share my concerns.
Just about everyone I know does internet banking and uses their credit cards over the net....I've been the odd ball because I just know that if the security pgms, encryption coding etc is man-made, it can be hacked into. It's good to read others who share my concerns.
new topics
-
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 12 minutes ago -
Don't take advantage of people just because it seems easy it will backfire
Rant: 26 minutes ago -
VirginOfGrand says hello
Introductions: 1 hours ago -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 1 hours ago -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 4 hours ago -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 5 hours ago -
God lived as a Devil Dog.
Short Stories: 5 hours ago -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 7 hours ago -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 8 hours ago -
Hate makes for strange bedfellows
US Political Madness: 10 hours ago
top topics
-
Hate makes for strange bedfellows
US Political Madness: 10 hours ago, 18 flags -
Who guards the guards
US Political Madness: 13 hours ago, 13 flags -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 7 hours ago, 8 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 8 hours ago, 7 flags -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 4 hours ago, 7 flags -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 1 hours ago, 4 flags -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 14 hours ago, 2 flags -
Don't take advantage of people just because it seems easy it will backfire
Rant: 26 minutes ago, 2 flags -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 5 hours ago, 2 flags -
God lived as a Devil Dog.
Short Stories: 5 hours ago, 2 flags
active topics
-
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 22 • : VirginOfGrand -
Don't take advantage of people just because it seems easy it will backfire
Rant • 1 • : worldstarcountry -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 121 • : NorthOS -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry • 0 • : worldstarcountry -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 17 • : DBCowboy -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 632 • : daskakik -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs • 43 • : DaydreamerX -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 261 • : YourFaceAgain -
Why did Phizer team with nanobot maker
Medical Issues & Conspiracies • 18 • : annonentity -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People • 4 • : underpass61
