It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
I would suggest an AT@T business class gateway router with built in firewall if available in your area. Only 75 bucks, well worth the clams.
reply to post by Hope_for_reason
Looks to me as though your linksys router assigned an ip to your pc which is the origin pc ip 192.168.1.15 : 1636 port being used to the destination ip 194.126.213.68:5000. port 5000 is a yahoo messenger port. The ip 194.126.213.68 points to Ministry of Defense of Republic of Croatia.
I don't think you have incoming problems, rather outgoing traffic.
Just my nickles worth........
Looks to me as though your linksys router assigned an ip to your pc which is the origin pc ip 192.168.1.15 : 1636 port being used to the destination ip 194.126.213.68:5000. port 5000 is a yahoo messenger port. The ip 194.126.213.68 points to Ministry of Defense of Republic of Croatia.
I don't think you have incoming problems, rather outgoing traffic.
Just my nickles worth........
Originally posted by Flyer
Its nothing special, Ive had all those hits too. The best one was the President of Lithuanias office trying to get something off me.
[edit on 24-9-2007 by Flyer]
Hey! I had President of Lithuania too!
Maybe he has a son who's into some hardcore tech music?
Or euro super car cruising videos going 150+ MPH.
Everyone in this thread, if you do not have it, download PeerGuardian2 from Phoenix Labs. Do a web search it'll pop right up. Update it daily.
Protect your privacy with a list of BILLIONS of IP addresses.. constantly updated..
The program is a God send. I plan on donating to those fools when I get my money up.
The program is a God send. I plan on donating to those fools when I get my money up.
I think if the government or any other high ranking community tried to hack into your laptop, they would have done it by now and not be blocked off by
some basic defenses
[edit on 25-9-2007 by AncientVoid]
[edit on 25-9-2007 by AncientVoid]
Edit: Edited by the government...
[edit on 25-9-2007 by AncientVoid]
[edit on 25-9-2007 by AncientVoid]
[edit on 25-9-2007 by AncientVoid]
Edit: Edited by the government...
[edit on 25-9-2007 by AncientVoid]
Especially as windows has a backdoor that they can get in through at will.
reply to post by Flyer
Windows 2000 had 5,000,000 million lines of code. I wonder what XP/Vista has. In case no one heard or remembers, MS secretively updated XP/Vista files when auto update was turned off. I recall that backdoor thing MS had in the operating systems called _NSAKEY which microsoft has a (2) crypto key(S) and some unnanmed other has the other key (NSA) supposedly.
Windows 2000 had 5,000,000 million lines of code. I wonder what XP/Vista has. In case no one heard or remembers, MS secretively updated XP/Vista files when auto update was turned off. I recall that backdoor thing MS had in the operating systems called _NSAKEY which microsoft has a (2) crypto key(S) and some unnanmed other has the other key (NSA) supposedly.
reply to post by WorldShadow
So basically the NSA as access to anyone with Windows!!!! Oddly enough I dont find that to hard to believe. Crazy!!!!
So basically the NSA as access to anyone with Windows!!!! Oddly enough I dont find that to hard to believe. Crazy!!!!
there's a way you can check which programs and ports are currently listening or connected to a server. go to start > run type cmd. that launches
the command prompt, type in "netstat -b" without the quotes. that lists the connections to/from your computer and what programs are using them.
if you find something that might look weird you can always disabled them.
Use "netstat -h" to see what other options you can use with the netstat command.
sorry if this has already been posted...
if you find something that might look weird you can always disabled them.
Use "netstat -h" to see what other options you can use with the netstat command.
sorry if this has already been posted...
reply to post by jaden_x
Thanks good advice will look into that, Its stuff I never think about really just assume the software i run should do all this form me!
Cheers
Paul
Thanks good advice will look into that, Its stuff I never think about really just assume the software i run should do all this form me!
Cheers
Paul
Originally posted by WorldShadow
reply to post by Flyer
Windows 2000 had 5,000,000 million lines of code. I wonder what XP/Vista has. In case no one heard or remembers, MS secretively updated XP/Vista files when auto update was turned off. I recall that backdoor thing MS had in the operating systems called _NSAKEY which microsoft has a (2) crypto key(S) and some unnanmed other has the other key (NSA) supposedly.
Exactly, my brothers friend has a job that includes secretly accessing peoples systems, its against the law but hes employed but two very big and multinational companies.
Im not even sure if thats the way in or if theres another way.
DoD is hitting up my comp.
Here are the ARIN info
OrgName: DoD Network Information Center
OrgID: DNIC
Address: 3990 E. Broad Street
City: Columbus
StateProv: OH
PostalCode: 43218
Country: US
NetRange: 7.0.0.0 - 7.255.255.255
CIDR: 7.0.0.0/8
NetName: DISANET7
NetHandle: NET-7-0-0-0-1
Parent:
NetType: Direct Allocation
Comment:
RegDate: 1997-11-24
Updated: 2006-04-28
OrgTechHandle: MIL-HSTMST-ARIN
OrgTechName: Network DoD
OrgTechPhone: +1-800-365-3642
OrgTechEmail: [email protected]
Here are the ARIN info
OrgName: DoD Network Information Center
OrgID: DNIC
Address: 3990 E. Broad Street
City: Columbus
StateProv: OH
PostalCode: 43218
Country: US
NetRange: 7.0.0.0 - 7.255.255.255
CIDR: 7.0.0.0/8
NetName: DISANET7
NetHandle: NET-7-0-0-0-1
Parent:
NetType: Direct Allocation
Comment:
RegDate: 1997-11-24
Updated: 2006-04-28
OrgTechHandle: MIL-HSTMST-ARIN
OrgTechName: Network DoD
OrgTechPhone: +1-800-365-3642
OrgTechEmail: [email protected]
First, 192.168.***.*** is an internal IP, along with several others.
Second, anyone running a P2P is an idiot, imho. Do you know how many *very* illegal files are you are serving up, or allowing to pass though your box? Do you know your machines name and addy are served up for all to see, as well as every packet transferred? Do you not think that every government, criminal orginization, or police agency, including interpol, has figured out how exceedingly simple it is to spoof or anonimize an IP so it doesn't show up as theirs? ( Thus defeating any blocklist )
Even the most secure connection scheme, the TOR network, has had servers arrested, even though they are just a passthrough, for distributing child porn? If you wish to be very afraid, install a packet sniffer and see exactly what is going in and out of your connection when you are on a P2P network.
There is no way to be invisible on the net, even if you use a supposedly secure system, like TOR, at the minimum, the exit traffic is sent in the clear and can be read, and who knows how many TOR routers are run by agencies just for that purpose. It is not even the least bit paranoid to imagine that every P2P network has thousands of machines monitoring traffic, making a list, checking it twice---finding out who is naughty, as there are none nice. (According to RIAA and INTERPOL)
Second, anyone running a P2P is an idiot, imho. Do you know how many *very* illegal files are you are serving up, or allowing to pass though your box? Do you know your machines name and addy are served up for all to see, as well as every packet transferred? Do you not think that every government, criminal orginization, or police agency, including interpol, has figured out how exceedingly simple it is to spoof or anonimize an IP so it doesn't show up as theirs? ( Thus defeating any blocklist )
Even the most secure connection scheme, the TOR network, has had servers arrested, even though they are just a passthrough, for distributing child porn? If you wish to be very afraid, install a packet sniffer and see exactly what is going in and out of your connection when you are on a P2P network.
There is no way to be invisible on the net, even if you use a supposedly secure system, like TOR, at the minimum, the exit traffic is sent in the clear and can be read, and who knows how many TOR routers are run by agencies just for that purpose. It is not even the least bit paranoid to imagine that every P2P network has thousands of machines monitoring traffic, making a list, checking it twice---finding out who is naughty, as there are none nice. (According to RIAA and INTERPOL)
Secure is a Knoppix Linux Boot DVD. With the Hard Drive disabled, and in read only access to the OS and running out of a RAM drive.
Flyer, they don't need that fancy crud for decrypting MS anymore, the password is two 16 bit chunks that can be broken independantly in less than 30
seconds using rainbow tables and brute force guessing. You're probably sharing your entire OS automatically being in a workgroup anyway.
Rainbow tables are precomputed crypto for every possibility, its just an index lookup of your hashcode which your system will surrender willingly.
Welcome to the future, they cracked your password last year, they just haven't bothered to look it up yet! Besides, most passwords are the same 500 words over and over anyway.
Rainbow tables are precomputed crypto for every possibility, its just an index lookup of your hashcode which your system will surrender willingly.
Welcome to the future, they cracked your password last year, they just haven't bothered to look it up yet! Besides, most passwords are the same 500 words over and over anyway.
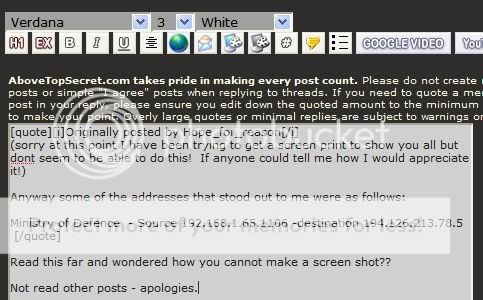
Wondered how you could copy paste IP's and not copy paste screen shots?
Well thanks for all the input. In conclusion I feel I may have to remove my P2P software as I had no idea how many people and files were passing
though my laptop. I may also disconneect from the net completely and lock my self in a dark cave and barricade the entrance with cement.
But thats for another reason all together!
Thanks everyone
Paul
But thats for another reason all together!
Thanks everyone
Paul
I'm glad at least a few people caught the whole source-destination thing.
That screenshot is YOU hitting all those places, not them hitting you. For it to be a response means you have an app up and a port responding (like a P2P client) or you have a trojan pounding away using your box....
I would check what you have running and scan away for spy/malware ASAP....
That screenshot is YOU hitting all those places, not them hitting you. For it to be a response means you have an app up and a port responding (like a P2P client) or you have a trojan pounding away using your box....
I would check what you have running and scan away for spy/malware ASAP....
oh, there ARE ways to safely run a P2P-----not on your own machine or your own network.
But I digress.
But I digress.
new topics
-
George Knapp AMA on DI
Area 51 and other Facilities: 4 hours ago -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 4 hours ago -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 6 hours ago -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 8 hours ago -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 10 hours ago -
Do we live in a simulation similar to The Matrix 1999?
ATS Skunk Works: 11 hours ago -
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 11 hours ago
top topics
-
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 11 hours ago, 23 flags -
George Knapp AMA on DI
Area 51 and other Facilities: 4 hours ago, 19 flags -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 12 hours ago, 18 flags -
African "Newcomers" Tell NYC They Don't Like the Free Food or Shelter They've Been Given
Social Issues and Civil Unrest: 17 hours ago, 12 flags -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 12 hours ago, 7 flags -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 6 hours ago, 7 flags -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry: 16 hours ago, 6 flags -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 10 hours ago, 5 flags -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 8 hours ago, 3 flags -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 4 hours ago, 3 flags
active topics
-
Truth Social goes public, be careful not to lose your money
Mainstream News • 119 • : Kaiju666 -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness • 44 • : JadedGhost -
George Knapp AMA on DI
Area 51 and other Facilities • 14 • : Brotherman -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 383 • : xuenchen -
OUT OF THE BLUE Chilling moment pulsating blue cigar-shaped UFO is filmed hovering over PHX AZ
Aliens and UFOs • 42 • : Ophiuchus1 -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 531 • : cherokeetroy -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs • 20 • : Halfswede -
MULTIPLE SKYMASTER MESSAGES GOING OUT
World War Three • 33 • : Halfswede -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs • 7 • : JonnyC555 -
Mood Music Part VI
Music • 3057 • : BatCaveJoe
