It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: Xcalibur254
a reply to: Gryphon66
It's funny how all the people complaining about voting machine integrity had no issues in 2000 and 2004 when the majority of machines were owned by Diebold whose owner was a major Bush contributor.
Was that before Dominion bought them out? Asking for all those politicians who own stock in Dominion voting systems.
originally posted by: LookingAtMars
originally posted by: Gryphon66
a reply to: lordcomac
It's been well known for some time that most of the voting systems in use in the US have the ability to connect to the internet under certain circumstances. I've linked MSM articles from 2019 and earlier that make it clear.
It's not a new issue.
That is an issue because it was claimed many times in 2020 that the machines are not connected to the internet.
Here's what the Dominion CEO said in the Michigan "hearing" (under oath if that matters):
Dominion tabulators are not connected to the Internet. In some jurisdictions, though not in Antrim, cellular modems are used for very brief periods, after the polls are closed, to transmit unofficial results from the precincts to the county headquarters. In Antrim, the tabulator memory cards are sealed and delivered to the county clerk by hand and there is no Internet connectivity, which could pose a potential risk of hacking, he said.
USA Today
Here's one of the articles I mentioned earlier ... it's low-hanging fruit from NBC:
NBC News Jan 10, 2020
The three largest voting manufacturing companies — Election Systems &Software, Dominion Voting Systems and Hart InterCivic — have acknowledged they all put modems in some of their tabulators and scanners. The reason? So that unofficial election results can more quickly be relayed to the public. Those modems connect to cell phone networks, which, in turn, are connected to the internet.
So that squares with the Dominion CEO's statement at least. Again, it's not a new problem, and it's not just with Dominion systems.
originally posted by: LookingAtMars
GA’s SoS Raffensperger Gave Hackers Roadmap To Infiltrate Machines A Year Before Election
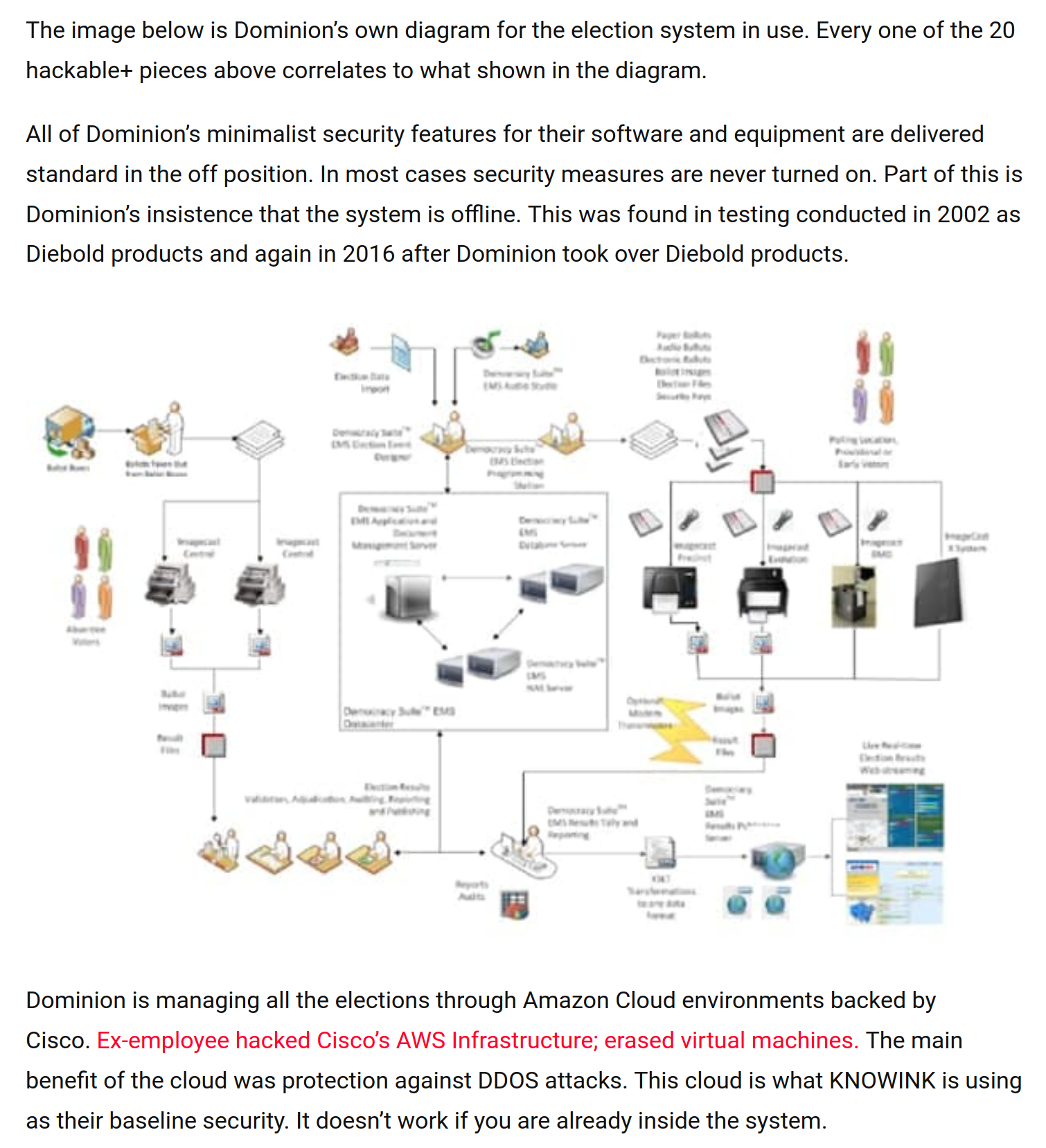
GA SoS Brad Raffensperger posted what is essentially a guide to hack Dominion, ES&S, and Smartmatic voting systems during the summer of 2019, one year ahead of the 2020 elections. This made every aspect of the Dominion Voting Systems Democracy Suite open for business to anyone in the business of skewing elections. Raffensperger gave them a year to prepare with the actual components Dominion uses and perfect the methodologies used to hack the GA election.
This link is to the redacted GA Master Technical Evaluation. Although redacted, the report left every route needed to hack and control each technical component Dominion uses as well as adding an actual vulnerability to get hackers started.
The GA evaluation also lists the scanners needed to find the source code and all possible routes into all three systems. I’ll be getting back to this later but it even identifies Dominion’s source code.
Voters in any state using electronic voting systems during the 2020 election should be angry at the government of GA about this.
Right now the exact same people in GA are telling voters to use these exact same voting machines and to go out and vote in a run off that will determine the fate of the nation.
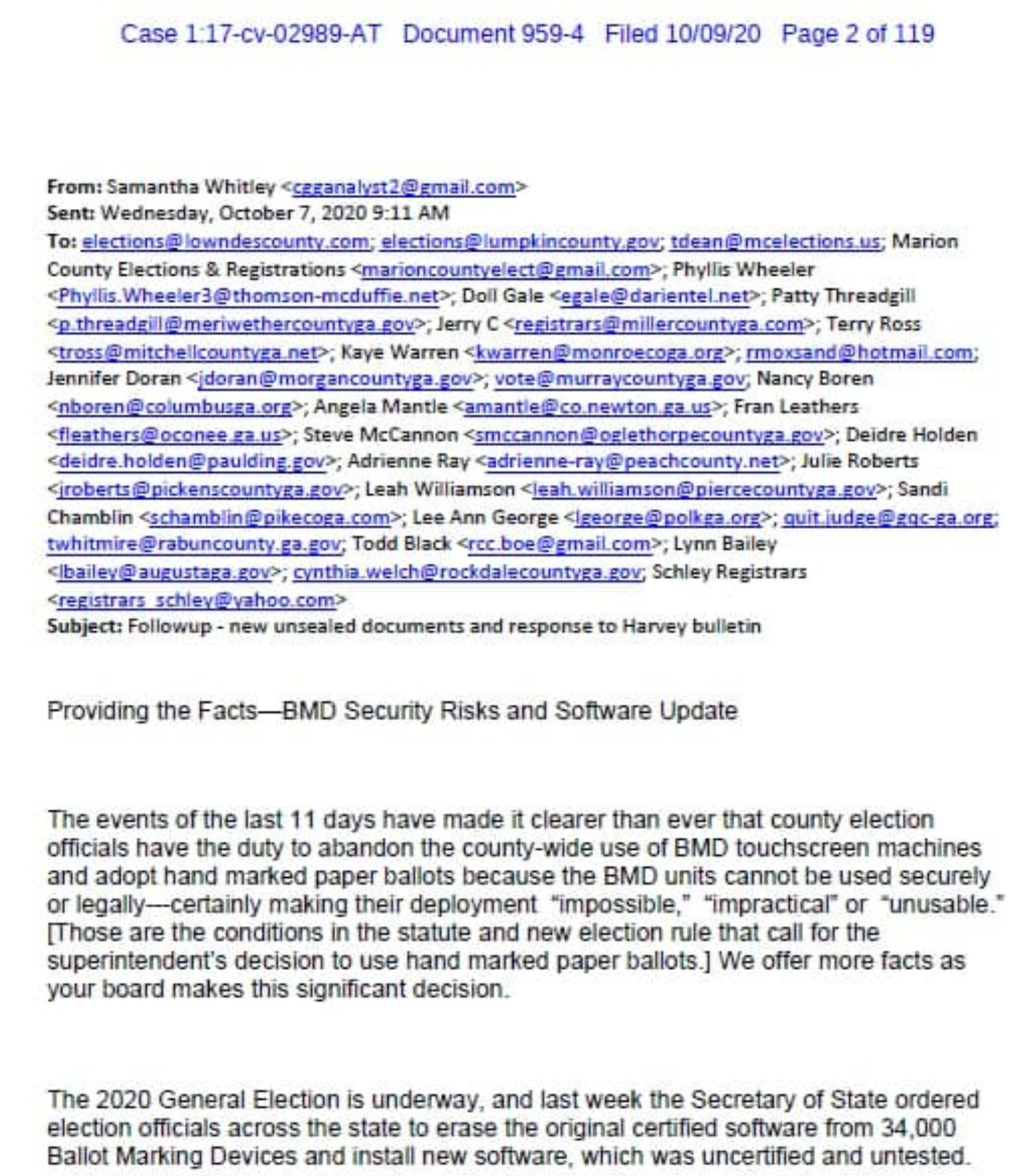
It also looks like our SoS "ordered county election officials to do a complete software wipe of the BMDs and install brand new software that never went through the certification process" before the Nov. election. See the email below.
All of this and more is in the link above that I found on twitter at Patrick Byrne. Even more evidence there for anyone looking.
The Democrats DO NOT want the election being audited/investigated...That tell us every thing we need to know to throw out the election...
originally posted by: NoCorruptionAllowed
Have you noticed that the folks who believe the election was fair have decided their best strategy is personal attacks on people who want an audit? What’s that tell you?
That plus those who attempt to downplay things like this in the OP also tell us everything we need to know about them personally..
Indeed.
Notice the replies to the OP.
They ask if they OP can hack the election using the schematic provided, as if no one possibly could do it if the OP can’t.
originally posted by: butcherguy
originally posted by: NoCorruptionAllowed
Have you noticed that the folks who believe the election was fair have decided their best strategy is personal attacks on people who want an audit? What’s that tell you?
That plus those who attempt to downplay things like this in the OP also tell us everything we need to know about them personally..
Indeed.
Notice the replies to the OP.
They ask if they OP can hack the election using the schematic provided, as if no one possibly could do it if the OP can’t.
The funny thing is after looking at the info in the contract, I think I could. With that info I could learn all I need to know in a year.
originally posted by: Gryphon66
a reply to: rickymouse
How would you gain access to the systems that are on a closed network?
There seems to be a lot of evidence that it was not on a closed network....can't you grasp that. I used to know people who could hack things, getting in through e-mails or just because someone hooked into the network and someone got access. I knew people who worked at different government systems where someone connected their phone to the closed protected network system and viruses got in. He got kind of frustrated when people did that, using the password to gain access to the network so they could go online at work. Lots of people were doing that once one person got away with it.
They can hack power plants which are on a closed system that way. Evidently you know little about this kind of stuff, all a hacker needs is some information on how to find an opening. My daughter goes to a big hacking convention in Vegas or whereever some years to learn things, she works with high level medical records and is in management and tries to teach people how to not let doors open so hackers can get in. She is a contracted management person for two companies.
She learns how hacking works to learn to protect from hacking and is part of a local cyber security group of people who train people to identify hacking....a cyber security company that teaches people how to make their businesses and agencies secure. Not all those who know how to hack are bad people, they use their skills to help people to protect their companies from cyber attacks more often than they use their abilities to hack into places.
I chose to pursue researching food chemistry, pharmacology, and the agencies that govern those and agriculture to try to identify problems in the food chain instead of continuing with technology. They use the same basic techniques in hacking they used to use, but it requires continued upgrading of your knowledge of how to bypass security features, things change too fast, I would rather research things that will be relevant for many years than keep up with computers now. Seems like I wasted so much time now because if you stop keeping up with technology for even a year, it has changed so much. This planned obsolete crap is frustrating, but the basics of how to get access are still there, if you got some information to work with.
The argument is that these public records enable a hacker to hack the Georgia Election System.
That is a claim that is not substantiated in any way. Also the fact is that the OP suggests that the public disclosure of the information some how implicates Raffensperger in "the Steal."
I pointed out that these are matters of public record (by law) and are available freely on the SoS website.
Several posters in the discussion who have systems experience have weighed in.
Every one of the claims supporting "the Steal" are a series of "what if" statements when they are not simply statements of belief (Trump won in a landslide, everybody else cheated.)
There's really no where to go from here. The core "evidence" of the discussion is publicly available information required by law. There is no evidence offered here that anyone used any of this to compromise any computer system, merely a chorus claiming "of course they did it."
That is a claim that is not substantiated in any way. Also the fact is that the OP suggests that the public disclosure of the information some how implicates Raffensperger in "the Steal."
I pointed out that these are matters of public record (by law) and are available freely on the SoS website.
Several posters in the discussion who have systems experience have weighed in.
Every one of the claims supporting "the Steal" are a series of "what if" statements when they are not simply statements of belief (Trump won in a landslide, everybody else cheated.)
There's really no where to go from here. The core "evidence" of the discussion is publicly available information required by law. There is no evidence offered here that anyone used any of this to compromise any computer system, merely a chorus claiming "of course they did it."
a reply to: rickymouse
I can grasp that claims are made by one side that the systems are not closed networks. I have yet to see any proof of that. The only thing you've said is "all a hacker needs is information on how to get in." Yes, I'll accept that surely. Is it your claim that this publicly available document does that?
Your argument would make a bit of sense if you weren't peppering with attempts to portray my exceptions with the claims as due to a lack of knowledge on my part. That's fallacious reasoning.
All you're saying here is that hackers exist, and hacking exists, so therefore the election systems could have been hacked.
You said yourself that there are individuals who protect against hacking.
Do you think there are none of those individuals associated with elections in Georgia? Do you think that Dominion Voting Systems doesn't employ security?
I can grasp that claims are made by one side that the systems are not closed networks. I have yet to see any proof of that. The only thing you've said is "all a hacker needs is information on how to get in." Yes, I'll accept that surely. Is it your claim that this publicly available document does that?
Your argument would make a bit of sense if you weren't peppering with attempts to portray my exceptions with the claims as due to a lack of knowledge on my part. That's fallacious reasoning.
All you're saying here is that hackers exist, and hacking exists, so therefore the election systems could have been hacked.
You said yourself that there are individuals who protect against hacking.
Do you think there are none of those individuals associated with elections in Georgia? Do you think that Dominion Voting Systems doesn't employ security?
originally posted by: Gryphon66
The argument is that these public records enable a hacker to hack the Georgia Election System.
That is a claim that is not substantiated in any way. Also the fact is that the OP suggests that the public disclosure of the information some how implicates Raffensperger in "the Steal."
I pointed out that these are matters of public record (by law) and are available freely on the SoS website.
Several posters in the discussion who have systems experience have weighed in.
Every one of the claims supporting "the Steal" are a series of "what if" statements when they are not simply statements of belief (Trump won in a landslide, everybody else cheated.)
There's really no where to go from here. The core "evidence" of the discussion is publicly available information required by law. There is no evidence offered here that anyone used any of this to compromise any computer system, merely a chorus claiming "of course they did it."
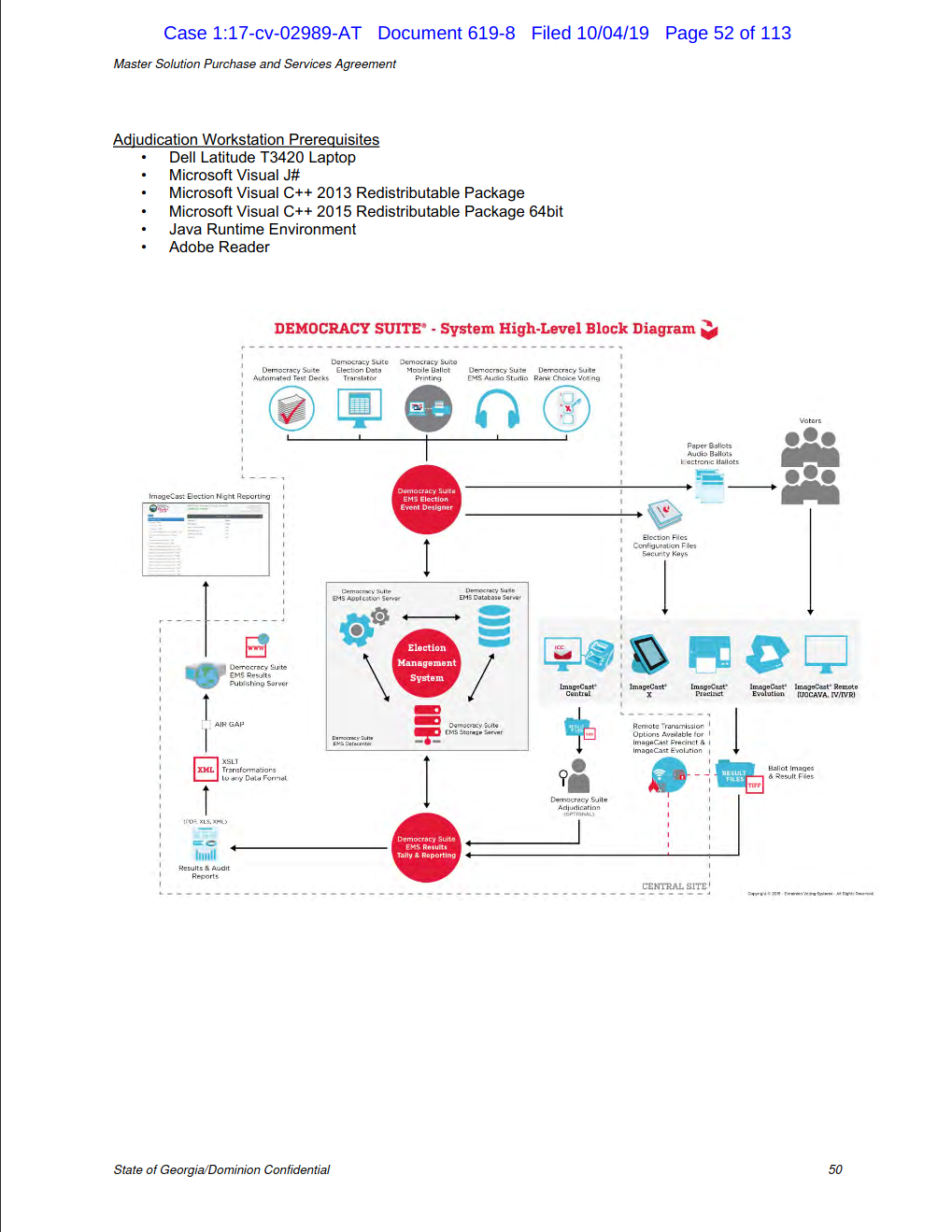
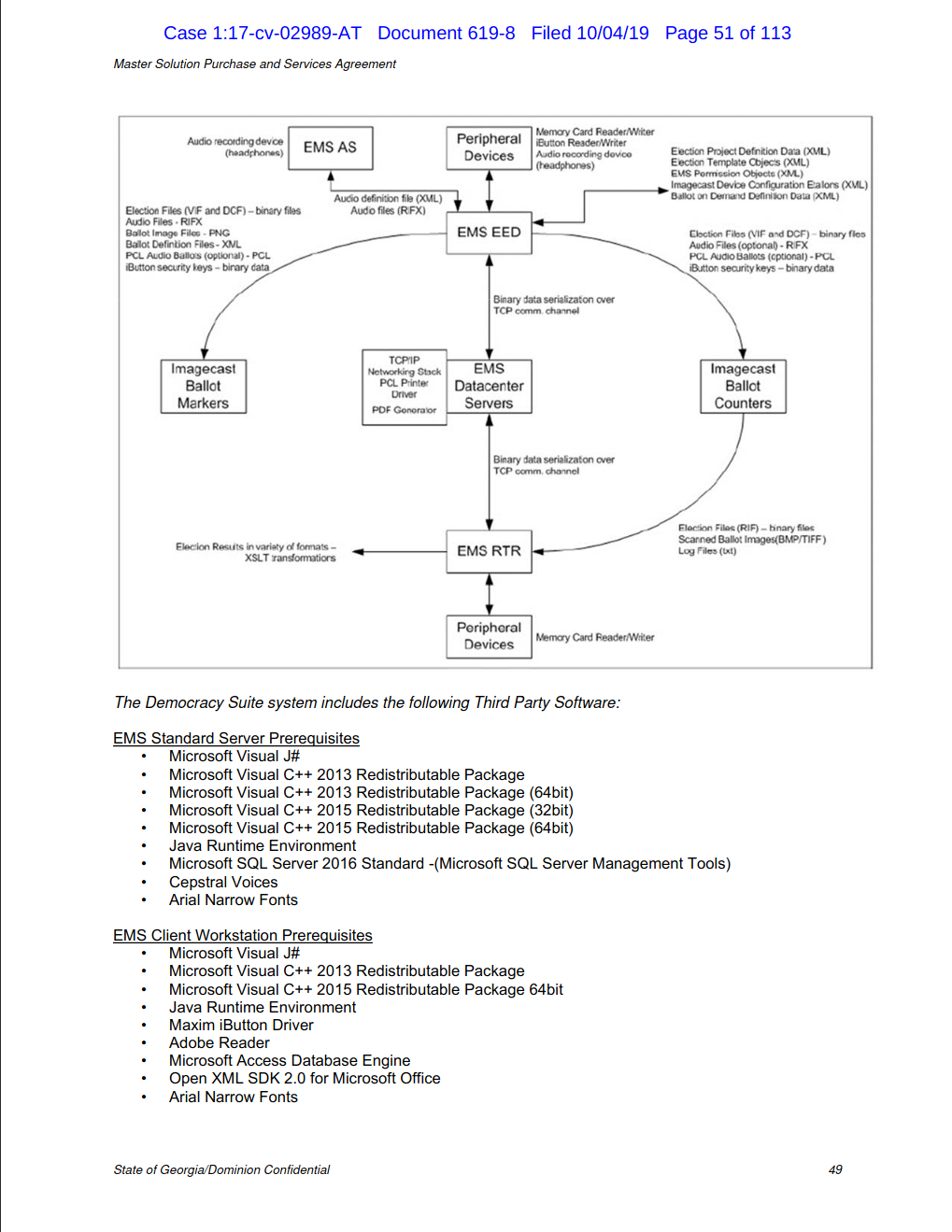
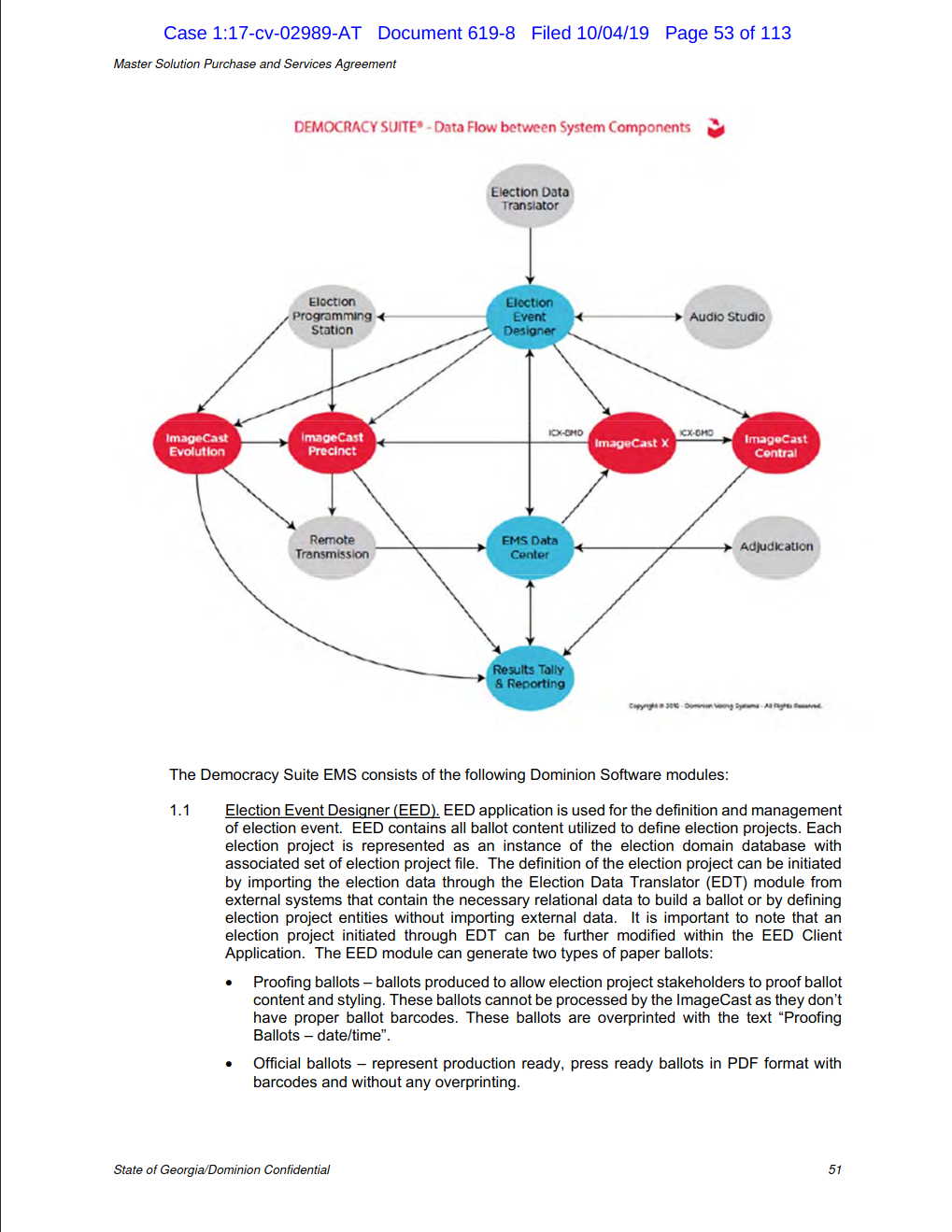
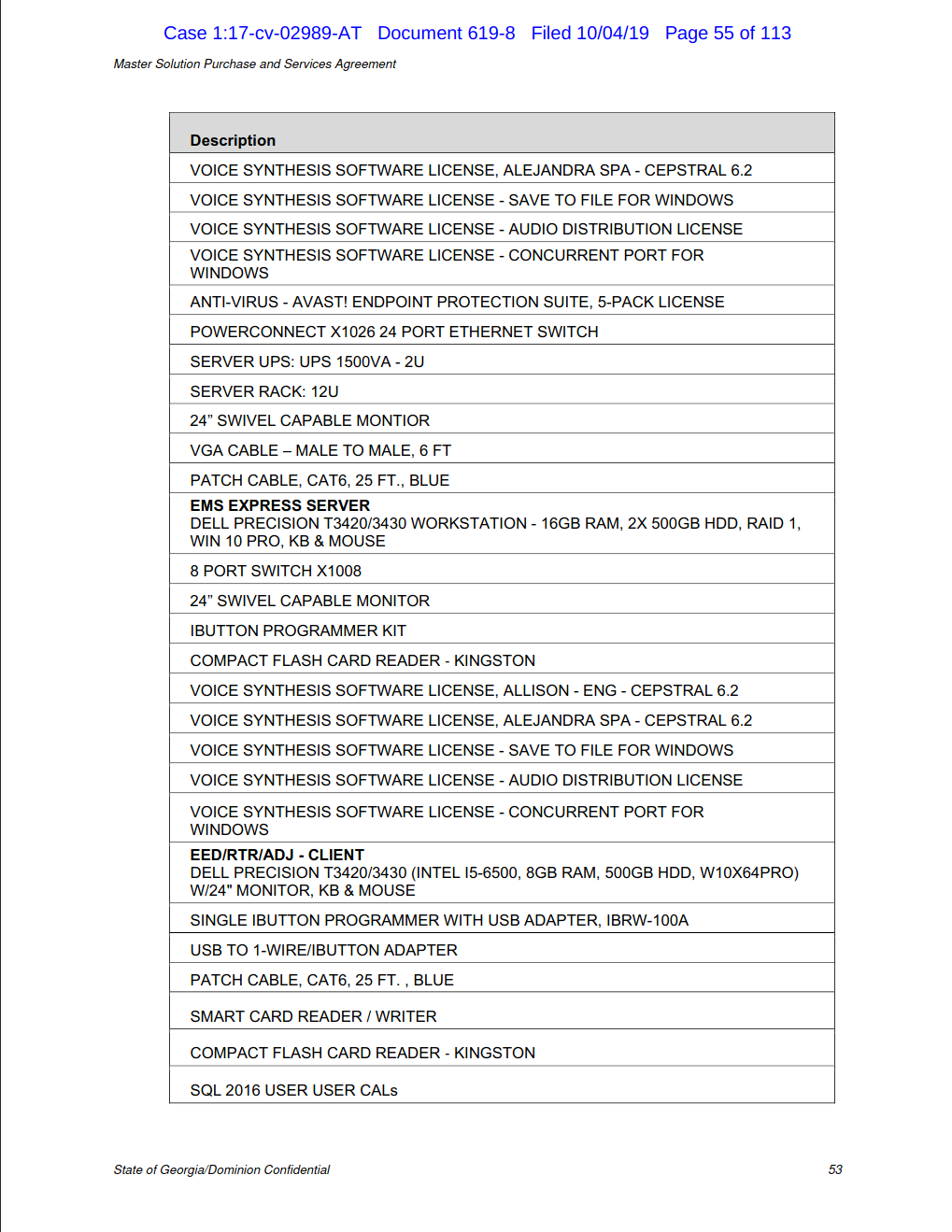
The information in the contract is marked confidential at the bottom of each page.
I hope some of our experts have time to look at it. It gives away a lot more than the spreadsheet does.
a reply to: LookingAtMars
The Contract you're so excited about is in the list of public documents on our Sec. of State's website.
Contract
Thanks for the chat.
The Contract you're so excited about is in the list of public documents on our Sec. of State's website.
Contract
Thanks for the chat.
a reply to: Gryphon66
I know that, the source says that. That is what the OP is about.
I missed the contract link as stated. It has a lot more info in it.
The Contract you're so excited about is in the list of public documents on our Sec. of State's website.
I know that, the source says that. That is what the OP is about.
I missed the contract link as stated. It has a lot more info in it.
edit on 3-1-2021 by LookingAtMars because: (no reason given)
originally posted by: Gryphon66
What would it take to hack the Dominion system based on what you know?
Wouldn't the hack leave "footprints" throughout the systems?
Are we talking an outside hack or an inside hack? It seems when we talk "hack" people are suggesting an outside party doing it and in this case I would think it would be a planned inside job. So should we talk about how to get through a steel locked door, or what to do if someone left the door unlocked?
If there was fraud with the software it wouldn't come from some outside jailbreaking as much as the software with the hack already imbedded and people already in place to change the votes...This could look like a software update before and then again after the election to put in the hack and then remove it replacing it with the good software.
If it can be hacked it has been hacked
If its on the internet it can be hacked
Simple rules we can all agree on
If its on the internet it can be hacked
Simple rules we can all agree on
originally posted by: Gryphon66
a reply to: rickymouse
I can grasp that claims are made by one side that the systems are not closed networks. I have yet to see any proof of that. The only thing you've said is "all a hacker needs is information on how to get in." Yes, I'll accept that surely. Is it your claim that this publicly available document does that?
So how do they transfer the data from a closed network, or independent machines to the main hub for collection? It seems they used flash drives? The ones my company doesn't allow ever due to security reasons... pretty f'ed up way if that is what they did. At some point that data from the machines needs to be transferred, so how many steps is that and what was the security at each step?
I'm actually asking for real and not Trolling... Seems we focus on the machines and not the process to get the votes actually counted for real. If they used flash drives would there be away to take one and change votes on the drive before sending the information? Are the flash drives physically delivered or plugged in to send the information on an open network?
Are each machine totals recorded per machine and then verifiable along the whole process? So lets say one machine A00002X3 has a manual count verified by poll watcher 12,000 votes Trump and 9000 votes Biden. Can I go back at from the total vote counts in the end and still see a break down of each machine and verify machine A00002X3 votes are still that same?
It just seems to me there are a number of risk areas in the whole process.
edit on 3-1-2021 by Xtrozero because: (no reason given)
a reply to: Xtrozero
That is almost exactly what happened in GA and the email in the OP is some evidence of that.
But it looks like others actually did hack into the system over the internet. From what I have seen in print, multiple countries hacked into the 2020 election.
I hope some info gets declassed next week as proof.
This could look like a software update before and then again after the election to put in the hack and then remove it replacing it with the good software.
That is almost exactly what happened in GA and the email in the OP is some evidence of that.
But it looks like others actually did hack into the system over the internet. From what I have seen in print, multiple countries hacked into the 2020 election.
I hope some info gets declassed next week as proof.
a reply to: Xtrozero
However it was done I am sure it was not secure in GA.
Nearly Two-Thirds of Georgia Counties Fail to Produce Chain of Custody Documents for 460,000 Absentee Ballots
ETA - I think they were using smart cards to transfer votes. I know they used them for something.
The contract lays out the whole process. Just skimmed it so far.
However it was done I am sure it was not secure in GA.
Nearly Two-Thirds of Georgia Counties Fail to Produce Chain of Custody Documents for 460,000 Absentee Ballots
ETA - I think they were using smart cards to transfer votes. I know they used them for something.
The contract lays out the whole process. Just skimmed it so far.
edit on 3-1-2021 by LookingAtMars because: (no reason given)
originally posted by: Gryphon66
a reply to: rickymouse
I can grasp that claims are made by one side that the systems are not closed networks. I have yet to see any proof of that. The only thing you've said is "all a hacker needs is information on how to get in." Yes, I'll accept that surely. Is it your claim that this publicly available document does that?
Your argument would make a bit of sense if you weren't peppering with attempts to portray my exceptions with the claims as due to a lack of knowledge on my part. That's fallacious reasoning.
All you're saying here is that hackers exist, and hacking exists, so therefore the election systems could have been hacked.
You said yourself that there are individuals who protect against hacking.
Do you think there are none of those individuals associated with elections in Georgia? Do you think that Dominion Voting Systems doesn't employ security?
I know little compared to my daughter and my old worker who now owns a computer shop. Their businesses deal with cyber security. They both work in trying to fix or prevent it from happening and teaching others how to lower risk. The big hospital servers have excellent security, yet people hack them at increasing rates these days. My daughter is required to have high dollar liability insurance, plus the companies that she work for also have insurance policies that do cover losses or expenses from someone hacking the system when they are online... My daughter's insurance covers her employees that work on medical records too.
I am not attacking your lack of knowledge, I even admit I do not know enough about this, but with the help of some people I know, I could probably figure out how to hack a machine like that if I had enough time and knew when they were upgrading the software to get access. Those machines are connected to the network at times.
I cannot say for sure they were hacked, but for a cyber secure company to allow that kind of info to be leaked out, that is criminal. That information we are discussing should never have been let out, it is a challenge for people who like hacking to break into it.
new topics
-
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 13 minutes ago -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 39 minutes ago -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum: 1 hours ago -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 2 hours ago -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 2 hours ago -
Weinstein's conviction overturned
Mainstream News: 3 hours ago -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 5 hours ago -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 5 hours ago -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 6 hours ago -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 8 hours ago
top topics
-
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 5 hours ago, 8 flags -
Weinstein's conviction overturned
Mainstream News: 3 hours ago, 6 flags -
Electrical tricks for saving money
Education and Media: 17 hours ago, 5 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 5 hours ago, 5 flags -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 8 hours ago, 5 flags -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 2 hours ago, 4 flags -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 2 hours ago, 3 flags -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 6 hours ago, 2 flags -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 10 hours ago, 2 flags -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 14 hours ago, 1 flags
active topics
-
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 177 • : theatreboy -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum • 8 • : grey580 -
Breaking Baltimore, ship brings down bridge, mass casualties
Other Current Events • 487 • : Threadbarer -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion • 1 • : chiefsmom -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues • 9 • : Asher47 -
Fossils in Greece Suggest Human Ancestors Evolved in Europe, Not Africa
Origins and Creationism • 84 • : whereislogic -
Ditching physical money
History • 21 • : SprocketUK -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News • 4 • : ElitePlebeian2 -
Is there a hole at the North Pole?
ATS Skunk Works • 38 • : Therealbeverage -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry • 10 • : ATruGod