It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Lots of ransomware tools are shared / sold in the underground web. Also there are many cyber investigators which exposes the code behind such a virus
so strong defences can be built.
One of the first things such a virus does is check if the user is browsing from Internet Explorer, and there is a reason for that.
When Macromedia Flash started to die because of Apple not allowing it to run on IOs devices, Microsoft wanted so badly to to be the new tool to build interactive content for the web, crating SilverLIght.
I know this because once I was using a memory driven database library called LexDB which was able to make data persistent through a browser. Since LexDB is open source I was interested in see how this can be done. Looking through the code it was evident the library was using C Sharp's File System Object allowed by Microsoft.
The ransomware tools when purchased also includes an admin panel from which the attacker can apart from following the spreading of the virus, the affected systems, location..he can even interact with the victims via chat provided in the admin panel.
An example u such a tool can be found here :
Karmen Ransomware Variant
I think one of the most common ways such virus spread is through fake articles on celebrities/way to make money/etc.
One of the first things such a virus does is check if the user is browsing from Internet Explorer, and there is a reason for that.
When Macromedia Flash started to die because of Apple not allowing it to run on IOs devices, Microsoft wanted so badly to to be the new tool to build interactive content for the web, crating SilverLIght.
I know this because once I was using a memory driven database library called LexDB which was able to make data persistent through a browser. Since LexDB is open source I was interested in see how this can be done. Looking through the code it was evident the library was using C Sharp's File System Object allowed by Microsoft.
The ransomware tools when purchased also includes an admin panel from which the attacker can apart from following the spreading of the virus, the affected systems, location..he can even interact with the victims via chat provided in the admin panel.
An example u such a tool can be found here :
Karmen Ransomware Variant
I think one of the most common ways such virus spread is through fake articles on celebrities/way to make money/etc.
A massive cyber-attack using tools believed to have been developed by the US National Security Agency has struck organisations around the world. Computers in thousands of locations have been locked by a programme that demands $300 (£230) in Bitcoin. In April hackers known as The Shadow Brokers claimed to have stolen the tools and released them online. Microsoft released a patch for the vulnerability in March, but many systems may not have been updated. How big is the attack? There have been reports of infections in 99 countries, including the UK, US, China, Russia, Spain, Italy and Taiwan. Cyber-security firm Avast said it had seen 75,000 cases of the ransomware - known as WannaCry and variants of that name - around the world. "This is huge," said Jakub Kroustek at Avast.
OP article evolving ..
Microsoft built in the hole for the vulnerability , and then goes to patch it .
Microsoft released a patch for the vulnerability in March, but many systems may not have been updated.
i still don't know why they want to blame the NSA when such tools are so easily obtained from the underground..of course for a price..there are
thousands of variants
Some experts say the attack may be have been built to exploit a weakness in Microsoft systems that was identified by the NSA and given the name EternalBlue. The NSA tools were then stolen by a group of hackers known as The Shadow Brokers, who then attempted to sell the encrypted cache in an online auction. However they subsequently made the tools freely available, releasing a password for the encryption on 8 April.
The hackers said they had published the password as a "protest" about US President Donald Trump. At the time, some cyber-security experts said some of the malware was real, but old. A patch for the vulnerability was released by Microsoft in March, but many systems may not have had the update installed. Microsoft said on Friday its engineers had added detection and protection against WnaCryt. The company was providing assistance to customers, it added. How does the malware work? Some security researchers have pointed out that the infections seem to be deployed via a worm - a program that spreads by itself between computers. Unlike many other malicious programs, this one has the ability to move around a network by itself. Most others rely on humans to spread by tricking them into clicking on an attachment harbouring the attack code. By contrast, once WanCry is inside an organisation it will hunt down vulnerable machines and infect them too. This perhaps explains why its impact is so public - because large numbers of machines at each victim organisation are being compromised.
editthat
originally posted by: heineken
i still don't know why they want to blame the NSA when such tools are so easily obtained from the underground..of course for a price..there are thousands of variants
Not only that, they are presenting this as if the ransomware was created by the NSA, not the exploit used to spread it.
a reply to: ArMaP
So the nsa got microsoft to build in a hole which allows remote access and control , which was put in all chips for all computers made from 2010 in secret , and now the nsa has been hacked and stolen from , allowing remote access through the hole they put there together , to presumably anyone with hacking knowledge because the tools were available (dumped) on line , in a an apparent protest about trump by a group called the shadow brokers .
lol out loud ! its a proper story already , its nothing to do with me , except my good old dad is hospital right now , that's no so amusable
And..... where's the Americans ? Isn't this thread veeery quiet ?
So the nsa got microsoft to build in a hole which allows remote access and control , which was put in all chips for all computers made from 2010 in secret , and now the nsa has been hacked and stolen from , allowing remote access through the hole they put there together , to presumably anyone with hacking knowledge because the tools were available (dumped) on line , in a an apparent protest about trump by a group called the shadow brokers .
lol out loud ! its a proper story already , its nothing to do with me , except my good old dad is hospital right now , that's no so amusable
And..... where's the Americans ? Isn't this thread veeery quiet ?
originally posted by: ZIPMATT
a reply to: ArMaP
So the nsa got microsoft to build in a hole which allows remote access and control , which was put in all chips for all computers made from 2010 in secret , and now the nsa has been hacked and stolen from , allowing remote access through the hole they put there together , to presumably anyone with hacking knowledge because the tools were available (dumped) on line , in a an apparent protest about trump by a group called the shadow brokers .
lol out loud ! its a proper story already , its nothing to do with me , except my good old dad is hospital right now , that's no so amusable
And..... where's the Americans ? Isn't this thread veeery quiet ?
microsoft dont build chips, intel though does
a reply to: Misterlondon
My guess is it's someone who got a hold of the NSA package that was dropped a few months ago and is now taking some of it out for a spin.
My guess is it's someone who got a hold of the NSA package that was dropped a few months ago and is now taking some of it out for a spin.
Jakub Kroustek of the security firm Avast said in a blog post update around 2000 GMT, "We are now seeing more than 75,000 detections... in 99 countries."
Kaspersky researcher Costin Raiu cited 45,000 attacks in 74 countries, saying that the malware, a self-replicating "worm," was spreading quickly.
phys.org -Fast-moving cyberattacks wreak havoc worldwide (Update 3)
A self-replicating worm exploiting a known windows flaw that has already been patched! I know it is a PITA but you need keep your computers up-to-date.
Anyway, figures are in the article I had to share.
a reply to: TEOTWAWKIAIFF
so I'd thought about it and he probably wants his records back
because large numbers of machines at each victim organisation are being compromised.
so I'd thought about it and he probably wants his records back
edit on 12-5-2017 by ZIPMATT because: (no reason given)
One can follow the money coming in which I assume will increase in the coming hours getting closer to zero time
here are some link of the wallets used by the attacking party
Wallet 1
Wallet 2
Wallet 3
Wallet 4
These wallets so far generated += 8.676 thus 14,916.21 US Dollar
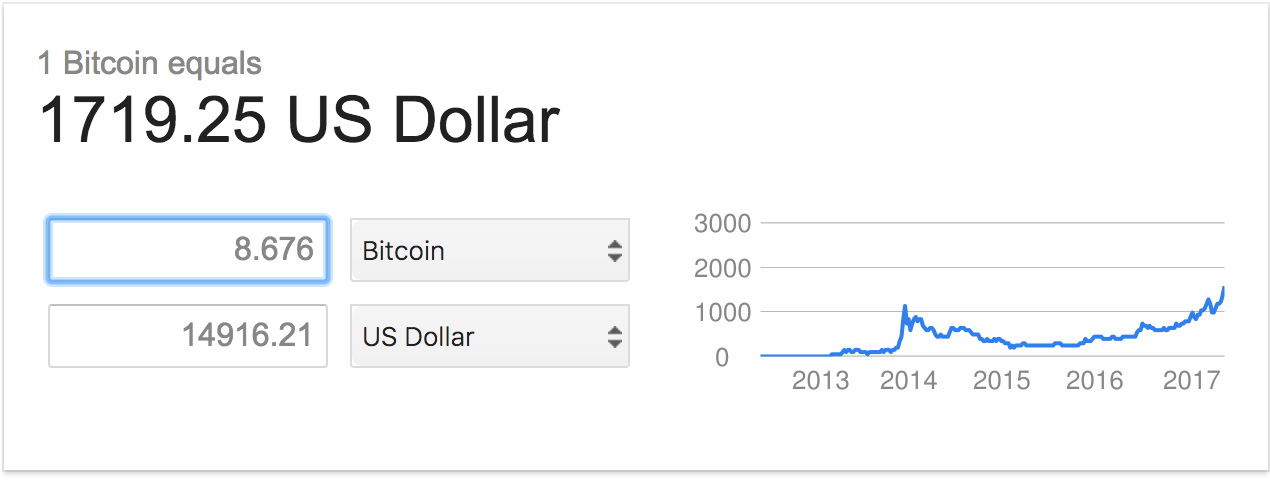
here are some link of the wallets used by the attacking party
Wallet 1
Wallet 2
Wallet 3
Wallet 4
These wallets so far generated += 8.676 thus 14,916.21 US Dollar

edit on 12-5-2017 by heineken because: corrected total amount
a reply to: jadedANDcynical
what else could they do then
what else could they do then
edit on 12-5-2017 by ZIPMATT because: (no reason given)
originally posted by: heineken
One can follow the money coming in which I assume will increase in the coming hours getting closer to zero time
here are some link of the wallets used by the attacking party
Wallet 1
Wallet 2
Wallet 3
Wallet 4
These wallets so far generated += 8.676 thus 1,719.25 US Dollar
Maybe anonymous money transfer companies should be held liable for the damage caused by their users demanding ransoms. Either they provide the ability to trace the money transfers or they are consider accomplices. Their choice.
Attention to Windows User :
This is the patch you need to have in order to fix the vulnerability exploited by the virus
MIcrosoft Official Patch
There is no need to say one is suggested to install.
For MacOs / Linux users just another day at the office
This is the patch you need to have in order to fix the vulnerability exploited by the virus
MIcrosoft Official Patch
There is no need to say one is suggested to install.
For MacOs / Linux users just another day at the office
new topics
-
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 2 hours ago -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 4 hours ago -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 8 hours ago -
Electrical tricks for saving money
Education and Media: 11 hours ago
top topics
-
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 13 hours ago, 10 flags -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 17 hours ago, 8 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 13 hours ago, 4 flags -
Sunak spinning the sickness figures
Other Current Events: 13 hours ago, 4 flags -
Electrical tricks for saving money
Education and Media: 11 hours ago, 4 flags -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 15 hours ago, 2 flags -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 4 hours ago, 2 flags -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 2 hours ago, 1 flags -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 8 hours ago, 0 flags
active topics
-
Sunak spinning the sickness figures
Other Current Events • 16 • : Freeborn -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 139 • : xuenchen -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues • 47 • : andy06shake -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 9 • : Vermilion -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 50 • : YourFaceAgain -
New whistleblower Jason Sands speaks on Twitter Spaces last night.
Aliens and UFOs • 57 • : baablacksheep1 -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three • 39 • : crayzeed -
British TV Presenter Refuses To Use Guest's Preferred Pronouns
Education and Media • 147 • : Annee -
So this is what Hamas considers 'freedom fighting' ...
War On Terrorism • 260 • : network dude -
Hate makes for strange bedfellows
US Political Madness • 43 • : network dude
