It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
A sophisticated piece of malware known as “Regin” has been spying on government organizations, infrastructure operators, businesses, researchers and private individuals since at least 2008. The backdoor-type Trojan is said to display a degree of technical competence rarely seen and would have required a significant investment of time and resources to create according to Symantec.
The design of the malware makes it suitable for long-term surveillance operations against a range of international targets and can even be customized with a range of capabilities depending on the target. The customization uses a modular approach similar to what has been seen in other sophisticated malware including Flamer and Weevil (The Mask).
Top-tier espionage malware 'Regin' has been spying on targets since 2008
www.symantec.com...

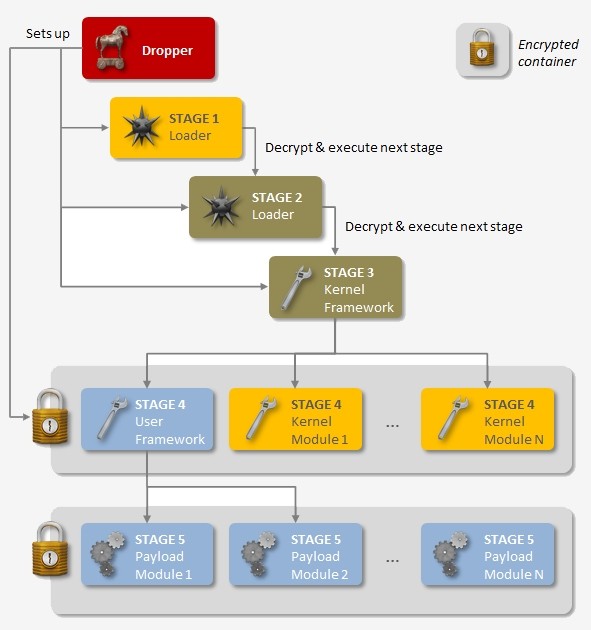
Thought this article(articles) may be of some interest to my fellow members. This “Regin” seems to have been doing the rounds for sometime now. One has to wonder as to which alphabet agency is responsible for this particularly sophisticated backdoor type Trojan. As you can see the malware comes in stages and is rather hard to detect.
edit on 24-11-2014 by andy06shake because: (no reason given)
Privacy is long dead on the net....(if it ever existed in the first place) the US military brought you the internet...did you think it was a FREE
GIFT?
edit on 24-11-2014 by stirling because: (no reason given)
Just saying...its sooo convenient to have the world using the system to which you undoubtedly have the backdoor keys.....
The use of Trojans is so widespread by government agencies and private corporations that I sincerely doubt there is any uninfected computer on the planet....
The use of Trojans is so widespread by government agencies and private corporations that I sincerely doubt there is any uninfected computer on the planet....
Its probably not any individual government group who did it by a collection as with the 5 eyes theres a lot of very good people all with different
skills and get them together and job done, they'd also be able to manipulate the AV companies etc so it would last as long as possible
originally posted by: Yeahkeepwatchingme
a reply to: stirling
This is why I think it was a surveillance device from day one.
You may be right. I worked for a company who maintained their own copy of the TCP/IP stack for their products (a large block of software going all the way from the device drivers to NIC's (network cards + connectors) to the actual sockets library used for applications development. Many of the source code modules, even senior engineers and architects were just not allowed to touch or even to try and understand, especially routing and encryption. Fixing memory leaks and faulty inter-process synchronisation that was OK.
Any new ideas to TCP/IP were/are introduced through RFC's (Request for Comments) and only universities like Berkeley and Stanford, who did all the research in conjunction with the NSA.
Then time and time again, we find some fundamental obvious bug that should have been fixed ages ago, still lurking there.
originally posted by: stirling
Privacy is long dead on the net....(if it ever existed in the first place) the US military brought you the internet...did you think it was a FREE GIFT?
Well, I was never under any illusions about the nature of the people who own us. Though I guess it is pretty easy to forget sometimes that your friendly computer and it's associated software is really basically a doorway into your mind. More than any other piece of technology ever invented, the internet basically is the telescreen. If for no other reason than a network is always going to involve other people in some way or another.
Anyway, I can remember sitting down at a computer for the first time in my life and wondering how much of what I was doing was being monitored somehow.
a reply to: stirling
Considering the amount of garbage that most people unwillingly or unknowingly download to there systems on a daily basis I have to agree. Short of having an air-gap rig that's essentially useless for all intents and purposes regarding communication I highly doubt there is an uninfected computer or network on the planet without some form of malware present.
Considering the amount of garbage that most people unwillingly or unknowingly download to there systems on a daily basis I have to agree. Short of having an air-gap rig that's essentially useless for all intents and purposes regarding communication I highly doubt there is an uninfected computer or network on the planet without some form of malware present.
originally posted by: andy06shake
a reply to: stirling
Apparently everything has its price, even freedom, or so it seems.
Freedom has always had a price, that price has always been blood, sweat and tears.
That will NEVER change.
a reply to: OneManArmy
Cant argue with that considering the supporting evidence. However the basic human paradigm has to change if we are ever to be anything other than predatory animals. We have such potential for evil yet also for good given the correct circumstances. Simple fact is there are far to many of us for this planet to accommodate. So we ether devise a means to remove ourselves to greener pastures or keep on killing one another until there are no people left to fight over the dwindling resources that remain. I know what scenario i would choose. And it's certainly not the Orwellian nightmare we currently experience should we happen to gaze out the window.
Cant argue with that considering the supporting evidence. However the basic human paradigm has to change if we are ever to be anything other than predatory animals. We have such potential for evil yet also for good given the correct circumstances. Simple fact is there are far to many of us for this planet to accommodate. So we ether devise a means to remove ourselves to greener pastures or keep on killing one another until there are no people left to fight over the dwindling resources that remain. I know what scenario i would choose. And it's certainly not the Orwellian nightmare we currently experience should we happen to gaze out the window.
edit on 25-11-2014 by andy06shake because: (no reason given)
originally posted by: andy06shake
A sophisticated piece of malware known as “Regin” has been spying on government organizations, infrastructure operators, businesses, researchers and private individuals since at least 2008.
So what's the point? Is anyone more enlightened because of the information supposedly gathered? Who gets the juicy info? Has anything been exposed? Nope. Spying on government organizations??? Yah okay. It's taken years to get backup tapes of the IRS emails.
I'm having a hard time believing this story.
originally posted by: StoutBroux
So what's the point? Is anyone more enlightened because of the information supposedly gathered? Who gets the juicy info? Has anything been exposed? Nope. Spying on government organizations??? Yah okay. It's taken years to get backup tapes of the IRS emails.
I'm having a hard time believing this story.
Military and industrial espionage. To say nothing of the ability to spy on governments and find out what they're doing which is an important part of diplomacy.
a reply to: StoutBroux
Well they do say that forewarned is forearmed, there is some enlightenment in that at least. As to who profits from the information, if Symantec know they certainly are not saying.
Well they do say that forewarned is forearmed, there is some enlightenment in that at least. As to who profits from the information, if Symantec know they certainly are not saying.
a reply to: andy06shake
It's unlikely that Symantec knows. Virus definitions are shared openly between anti virus vendors because it allows for everyone to have an effective product rather than each company have only a partially effective one. If any antivirus maker knew it would result in everyone knowing more than likely.
The more likely scenario in my opinion is that whoever made this virus has detailed knowledge of the coding behind the anti virus software and they wrote it to use loopholes in their code so that it would be less likely to be noticed.
It's unlikely that Symantec knows. Virus definitions are shared openly between anti virus vendors because it allows for everyone to have an effective product rather than each company have only a partially effective one. If any antivirus maker knew it would result in everyone knowing more than likely.
The more likely scenario in my opinion is that whoever made this virus has detailed knowledge of the coding behind the anti virus software and they wrote it to use loopholes in their code so that it would be less likely to be noticed.
a reply to: andy06shake
What concerns me is so many people going out
and buying video cameras to watch their homes,
etc... And that they may be setting themselves up
for strangers to be able to access those cameras
and spy on people if they can be accessed via The
Internet. I have refused to buy such cameras
because of this, but the masses seem completely
clueless.
Rebel 5
What concerns me is so many people going out
and buying video cameras to watch their homes,
etc... And that they may be setting themselves up
for strangers to be able to access those cameras
and spy on people if they can be accessed via The
Internet. I have refused to buy such cameras
because of this, but the masses seem completely
clueless.
Rebel 5
a reply to: rebelv
Buddy given the security issues we face in today's society and the unwillingness and or lack of aptitude Police show regarding crimes like petty theft, vandalism, burglary, and even assault i have to say im considering purchasing an outside IP cam for my residence.
www.lightinthebox.com...
A couple of the above to be more precise. There dirt cheap and will offer endless peace of mind to both myself and family members.
Buddy given the security issues we face in today's society and the unwillingness and or lack of aptitude Police show regarding crimes like petty theft, vandalism, burglary, and even assault i have to say im considering purchasing an outside IP cam for my residence.
www.lightinthebox.com...
A couple of the above to be more precise. There dirt cheap and will offer endless peace of mind to both myself and family members.
edit on
25-11-2014 by andy06shake because: (no reason given)
originally posted by: rebelv
a reply to: andy06shake
What concerns me is so many people going out
and buying video cameras to watch their homes,
etc... And that they may be setting themselves up
for strangers to be able to access those cameras
and spy on people if they can be accessed via The
Internet. I have refused to buy such cameras
because of this, but the masses seem completely
clueless.
Rebel 5
Everything is a tradeoff and that goes double for technology. A network camera can provide real time remote surveillance while storing the data offsite, but that same network access can allow someone to hijack it and spy on you. It all comes down to where you place the camera. For example, I would be perfectly comfortable with some perimeter cameras on my home being on a network and them potentially being hijacked but the camera on my laptop gets covered with tape.
edit on 25-11-2014 by Aazadan because: (no reason given)
new topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 1 hours ago -
Ode to Artemis
General Chit Chat: 2 hours ago -
Ditching physical money
History: 5 hours ago -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 5 hours ago -
Don't take advantage of people just because it seems easy it will backfire
Rant: 6 hours ago -
VirginOfGrand says hello
Introductions: 7 hours ago -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 7 hours ago -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 10 hours ago -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 11 hours ago -
God lived as a Devil Dog.
Short Stories: 11 hours ago
top topics
-
Hate makes for strange bedfellows
US Political Madness: 16 hours ago, 20 flags -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 10 hours ago, 12 flags -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 13 hours ago, 9 flags -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 1 hours ago, 7 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 14 hours ago, 7 flags -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 7 hours ago, 6 flags -
Don't take advantage of people just because it seems easy it will backfire
Rant: 6 hours ago, 4 flags -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 5 hours ago, 4 flags -
God lived as a Devil Dog.
Short Stories: 11 hours ago, 3 flags -
Ditching physical money
History: 5 hours ago, 3 flags
active topics
-
Why to avoid TikTok
Education and Media • 17 • : mooncake -
The Superstition of Full Moons Filling Hospitals Turns Out To Be True!
Medical Issues & Conspiracies • 22 • : mooncake -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 23 • : BigDuckEnergy -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 3 • : BingoMcGoof -
Russia Ukraine Update Thread - part 3
World War Three • 5717 • : Arbitrageur -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 44 • : budzprime69 -
Hundreds of teenagers flood into downtown Chicago, smashing car windows
Other Current Events • 111 • : 777Vader -
British TV Presenter Refuses To Use Guest's Preferred Pronouns
Education and Media • 125 • : Annee -
Who guards the guards
US Political Madness • 4 • : kwaka -
New whistleblower Jason Sands speaks on Twitter Spaces last night.
Aliens and UFOs • 44 • : pianopraze
