It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: Maxmars
I have to disagree about this, and kind of take it offensively being that I work in security myself.
There are those out there that actually do wish to protect those they are tasked to protect. That includes protection from an over-reaching gov't, as well as hackers.
I have to disagree about this, and kind of take it offensively being that I work in security myself.
There are those out there that actually do wish to protect those they are tasked to protect. That includes protection from an over-reaching gov't, as well as hackers.
originally posted by: theantediluvian
a reply to: Maxmars
...
They're really not as expensive as the author leads on (or particularly new). Here's an article about the demonstration of an IMSI-catcher at DefCon in 2010 that cost about $1500 to put together:
Wired - Hacker Spoofs Cell Phone Tower to Intercept Calls
There's some interesting information at the Android IMSI-Catcher Detector project site including a list of links to even more information.
Thanks! It does seem that people are not general aware that the Internet is not rocket science. The entire point was to communicate. It's those who have discovered the unheralded well-spring of access who are now corporatized and well-funded... telling us that this product or that is "unhackable" or "virus-proof," or their security "uncrackable."
If you want it so... you have to invent it. But somehow those who can are considered a threat by our government, or so I've heard... I wonder why that might be?
originally posted by: eriktheawful
Just another reason why I'm glad I do not own a cell phone.
There are quite a number of benefits either way.... I opted out too....
I remember when phones could simply call another phone.... and the law provided that the reliability-performance of land-lines was well in excess of 90%.
originally posted by: douglas5
I wonder what Steve jobs was thinking now
I suppose he may have thought he was a knight in shining armor. That's what his empire's marketing folks want us to believe. I'm not much for celebrity perspectives... most of them live in a white tower to begin with, and most of their opinions are given as a function of "commerce."
originally posted by: ANNED
NSA or a hacker looking for credit card numbers, passwords ect ect ect.
I might be looking at this differently.
The first key point I focused on was that these particular "cell towers points" weren't supposed to even be noticed.
No one has accepted the "ownership" of these devices.
Some of them are on restricted properties (government land.)
Then there's the fact that they bumped any connecting device down to a more primitive security protocol.
Then add the fact that this material may be reported in a "bad light"... trying to "sell" something.
But most hear are not prone to fall for such things... the information is open to all.
I would think that this might even be part of a foreign intelligence operation; after all our security services are all about keeping us in check... and not much else.
You know what's really funny? You get dinged by one of these petty hackers via a vulnerability... and they end up investigating you.
originally posted by: Bone75
What better way to squash any kind of opposition to our fascist dictators, before it even gets started, than this?
It doesn't necessarily have to be that... it could be about money. Unless we know who put them there, we can only speculate.
originally posted by: MystikMushroom
It's called "Stingray" and the ACLU is aware of it:
ACLU - "Stingray"
If you have something important to tell someone, and you don't want anyone but the intended recipient to hear it -- discuss it in person, in an interior room without windows and very loud white noise.
Knowing this, would you feel better that it is deployed without oversight? I doubt they would deploy equipment with no designator that says something foreboding like; "Prop of XXXXX ..." and then include some drivel about prosecution and penalties.
Knowing they have this tool is one thing, but this is another, I think.
Once again a thread that p*sses the hell out of me showing how controlling a flock is such big business that they cant handle it all by themselves so
privatise it. We can discuss the reasoning behind these measures of being a necessity if we want to be safe or a threat on our freedoms. But the fact
is that the only people to blame are ourselves. We will discuss this to the point that we may or may not come to agreement, then go back to our daily
life of struggling to get by to be allowed to survive on basic rights of food, water and being with your family.
All I see now is discussion after discussion on "big" issues what are lost and quickly forgotten when we are dragged back to reality of watching some crap on tv or a new more important "big" issue comes up and this will be buried with the rest of the abuses on our rights as humans to live and progress in a way with no greed or being herded like f*cking sheep for our milk, shave our asses and butcher our children for their sick appetites.
This should of been in a rant section but im away back to work for enough money to be allowed to retire in peace and allowed to sit in my own piss.
All I see now is discussion after discussion on "big" issues what are lost and quickly forgotten when we are dragged back to reality of watching some crap on tv or a new more important "big" issue comes up and this will be buried with the rest of the abuses on our rights as humans to live and progress in a way with no greed or being herded like f*cking sheep for our milk, shave our asses and butcher our children for their sick appetites.
This should of been in a rant section but im away back to work for enough money to be allowed to retire in peace and allowed to sit in my own piss.
originally posted by: thinline
I could be reading this post wrong. What we are talking about is that some people who are making a product that creates privacy just came out and said that there is less privacy then we all thought. Therefore, creating a bigger need and giving their start up company more press then they could pay for.
Not saying they are lying, just saying clarification/verification would be nice before we go all ranty
I see that angle as well.
The most important part of this story however, in my mind, is the potential for a massively criminal organized effort to access millions of users' information. If we discover that this product developer manufactured anything about these observations, you will be vindicated in your principle point. I wouldn't mind that, although the story is as of yet unresolved.
originally posted by: AgentSmith
1) The headline is misleading (not your fault OP) - it implies they are only spying on Android devices - not so...
A more accurate headline would be "Dozens of fake cell phone towers discovered eavesdropping on phones" - but the person who wrote it probably didn't think about the possibility of wrong interpretation of the original sentence or is just an Apple fanboi.
Thank you, I agree. Frankly, I should have thought to change the title for this thread... (I tend not to that), but in this case it might have served us better.
2) These 'towers' which are more likely to be small femtocell sized homebrew devices can be easily constructed by someone who can read, understands Linux, has some mediocre programming skills and any amount of money ranging from about $50 to many thousands.
This is speculation considering we have no physical proof to examine. But it is not lost on me that in our society, there are many who opt not to use their knowledge and skill to construct, deploy, and use such a tool. But obviously, someone did it. And we know nothing about who put it there, what they did with it, and what they did with the information they simply 'overheard.'
So much disinformation as usual and the usual 'Government are doing it' crowd are out in force I see....
So sorry to burst the 'government did it' crowds bubble...
Well, that's clear... evidently you propose that because it can be done easily; it can't have been the government. That assertion is as wrong as saying it was them. My point is that we should be concerned if this was an organized effort... especially since who put them there is an open question.
originally posted by: Leonidas
There are nineteen (19) towers identified in this article I just read. The conclusion in the article discount the NSA as the culprit because they have easier and more complete ways to do this and dont need these towers.
....
Is this part of the same Android story being reported, or is it something else?
I suspect this is related to it. Perhaps a piggy-back story made by the 'reporters' citing NSA is usually good to make people paranoid... which makes them read more.
Or maybe it is just another social engineering exercise, I am powerless to speculate about a infinity of possibilities.
originally posted by: Dragoon01
Very similar to a thread I saw last week.
A lot of implications that are not entirely supported by the facts.
This talks about fake “towers” and implies that the NSA is the operator of those towers.
I apologize for missing that thread; I have no intention of interfering with another members contribution.
What you believe is my intent... to imply something... is actually backwards, I want you to infer something. I won't say this is a government thing, because I don't have information about the equipment, nor who put it there.
Everyone concedes that there are over a dozen agencies with access to this kind of equipment. Perhaps they don't want to claim the device... perhaps it wasn't them at all; it could be part of the new cyber-mafia that traffics in stolen personal data. Perhaps it's (as I speculated before) a foreign intelligence gathering operation... who knows. I would like to.
Well that’s not the only possibility. Setting up a local cell is not that hard and not that costly.
There are companies that do it to improve connectivity in their campus for their employees.
They set up the tower and route the traffic over their corporate PBX. Their employees devices are authorized on the networks but all others are not.
So to your phone it looks like a fake tower.
Another way to look at that is that for the convenience of their own organization they are setting up a "weak point" in the communications security of anyone in range. I know hospitals, universities, and such use this method to avoid paying for enterprise solutions for connectivity.
What they did not do is do some locating of one of these “towers” and then cross reference that location with the FCC’s transmitter database.
If the tower was fake or not legit it would not show up in that data. If it’s a business operating it then it would be there and be identified.
If they did that however they would not have a marketing angle for their special super secret cryptophone.
I choose to infer an excellent suggestion... but I haven't the data; ... if you did, would you check?
originally posted by: Assassin82
I'm not suggesting that some people aren't out for some evil or sinister use for this technolgy or information. But I did want to suggest something in regards to the ones being on military installations.
Imagine a scenario where somehow, somway, someone takes truck full of explosives onto a miltary base and kills hundres of our troops. Imagine the outcry for better security and intelligence gathering. Now imagine if that base didn't have the ability to monitor cell phone track around the base. They had no early intelligence warnings that someone was planning something. That would be a terrible day for America.
Now imagine if they did, and the sole purpose was to listen for possible warnings or attacks. Some tracking algorythm picked up on a few key words, an alert goes out to SP's or MP's to either increase security protocol or shut down the base completely. They find and detain the bad guys or at the very least scare them off.
No dead soldiers, and you'd likely hear very little about it because it's not shocking enough to be carried on MSM. My point is, not everything and everyone is sinister in nature. Not everyone is out to get your nude photos stored on your phone or your password/credit card numbers/etc. Sometimes this technology is used to save lives.
But there certainly is no reason for it to be in a Casino or anything like that.
The difficulty in your scenario presents itself to me differently.
First off, I have to presume you agree that you cannot expect to have total security unless you are a prisoner, in a cell, all alone.
Second, if there is even ONE way to communicate (between people) the plans for doing evil; we cannot expect the "big brother" total security (no privacy) to provide safety. It is impossible. The kind of safety those eavesdroppers promise us is a huge lie.
That's why they so often fabricate events to call 'anti-terrorism' success stories... because this only works in a very few kinds of cases.
originally posted by: wmd_2008
a reply to: Maxmars
Had a quick look at the link doesn't really say what's claimed in the title.
So we have a guy PUSHING his OWN product claiming dozens of towers with NO real proof of the fake claim and in the link a road trip of possibly up to 650 miles they find 8 of these claimed fake towers.
Now since his phone is $3500 dollars what better way to push sales than make claims WE can't really check!!!
Yup, he is.
Now, what is your opinion about those incognito, unowned, unaccounted for, fake cell phone towers that are apparently all over the place? Are you saying you know they are "not fake"? Please share.
originally posted by: parad0x122
a reply to: Maxmars
I have to disagree about this, and kind of take it offensively being that I work in security myself.
There are those out there that actually do wish to protect those they are tasked to protect. That includes protection from an over-reaching gov't, as well as hackers.
I apologize if the tone of my generalization gave you offense. I am most concerned with the possibility that the most sweeping and intrusive of capabilities of technologies is being used by someone without any real accountability. But I grant that I may be wrong.
Even if this was not deployed to a malevolent end, it compromises the thing most people prize most - the details of their own lives.
a reply to: liteonit6969
Rant on, my friend.
So many of us will select an aspect of this to discuss, from the commercialism tainting the reporters source, to the disquieting notion that you must not be free if you wish to be 'safe,' (and how, accepting that, no one can be free - if we are to be 'safe.')
Your voice, like all, are welcome.
Rant on, my friend.
So many of us will select an aspect of this to discuss, from the commercialism tainting the reporters source, to the disquieting notion that you must not be free if you wish to be 'safe,' (and how, accepting that, no one can be free - if we are to be 'safe.')
Your voice, like all, are welcome.
Tech 1 - Hey we got the information on those private searches we have been doing.
Tech 2 - OK, what have we got? The NSA and the other agencies may want to buy the information.
Tech 1 - Well, 97.7% of all activity was related to porn, the other 2.2% were for ordering from Amazon....
Tech 2 - (crickets)
Tech 2 - OK, what have we got? The NSA and the other agencies may want to buy the information.
Tech 1 - Well, 97.7% of all activity was related to porn, the other 2.2% were for ordering from Amazon....
Tech 2 - (crickets)
I've personally designed thousands of these cell phone facilities for pretty much all the major carriers, from fake boulders, fake barns and trees,
church crosses, towers, pretty much everywhere you can imagine. It's easy to slip something like this by because there are so many of these
facilities to even notice.
Can you spy on a phone when it is turned
off?
They might use invisible spying apps uploaded through these towers. They have their own proprietary line and frequency for pulling all sorts of nasty tricks. The funny part is, millions of Android users consent to giving up private information daily, including there whereabouts. Even when people found out the dark side of social media, they usually try and block it out of their heads and still people's lives get ruined. I don't wish this to happen but if people had to fend for themselves, they would be the first sheep to the pen. Less competition for resources when everything goes bat ship crazy.
This is why I root all my phones and tablets, remove 100% crap and start with a rom that can modify permissions. For anybody that didn't know...
Location Reporting
Android 4.3 Includes Hidden App Permissions Manager That Could Bolster Privacy & Security
Android 4.3 has a hidden feature called "App Ops" and it lets you selectively disable some permissions for your apps. Not too many people know about this and if you are rooted, there are better alternatives over privacy control.
Someone has made a handy app that launches the permission manager.
Whether you consider Edward Snowden a traitor or a patriot, before he hit the news most people didn’t give much thought to government spying on everyday citizens. During a recent interview, he said that the NSA has the ability to spy on your smartphone, even if it's turned off.
They might use invisible spying apps uploaded through these towers. They have their own proprietary line and frequency for pulling all sorts of nasty tricks. The funny part is, millions of Android users consent to giving up private information daily, including there whereabouts. Even when people found out the dark side of social media, they usually try and block it out of their heads and still people's lives get ruined. I don't wish this to happen but if people had to fend for themselves, they would be the first sheep to the pen. Less competition for resources when everything goes bat ship crazy.
The worst part is that even if you turned the phone off to be safe, it wouldn't really be off. The app makes your phone pretend to be off — it turns off the screen, ignores incoming calls and doesn't respond to button presses — but the spying will still be going on.
This is why I root all my phones and tablets, remove 100% crap and start with a rom that can modify permissions. For anybody that didn't know...
Location Reporting
Location Reporting in Google Settings is available on devices running Android 2.3 or higher and have Google Maps for mobile 6.14.5 or higher installed.
Location Reporting allows Google to periodically store and use your device's most recent location data, as well as activities like driving, walking, and biking, in connection with your Google Account.
Location Reporting is a per-device setting and can potentially use a lot of data. We recommend that you review your data plan before using this feature. If Location Reporting is not available in your region, it’s automatically turned off for that device.
How often Location Reporting updates your location data isn't fixed. Frequency is determined by factors like how much battery life your device has, if you’re moving, or how fast you’re moving. Location Reporting will only use cell ID or Wi-Fi location detection depending on your device.
Android 4.3 Includes Hidden App Permissions Manager That Could Bolster Privacy & Security
Android 4.3 has a hidden feature called "App Ops" and it lets you selectively disable some permissions for your apps. Not too many people know about this and if you are rooted, there are better alternatives over privacy control.
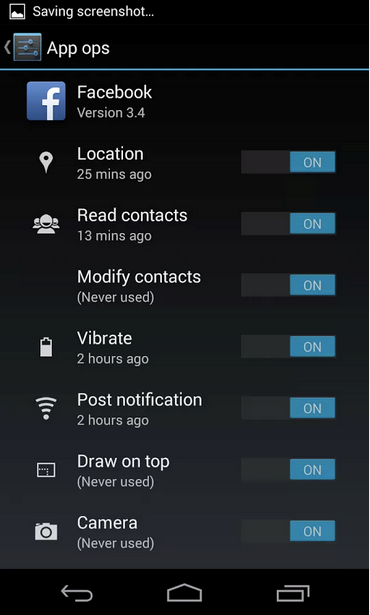
Android Police has unearthed a hidden app permissions manager that allows users to selectively disable certain permissions for apps.
The feature is apparently called App Ops, and lets users toggle app permissions — such as location and the ability to post notifications — on and off for individual apps. Android Police notes that a developer has already created an app (available here on Google Play if you have Android 4.3 installed) that foregrounds App Ops, and has been having a play around with it.

Someone has made a handy app that launches the permission manager.

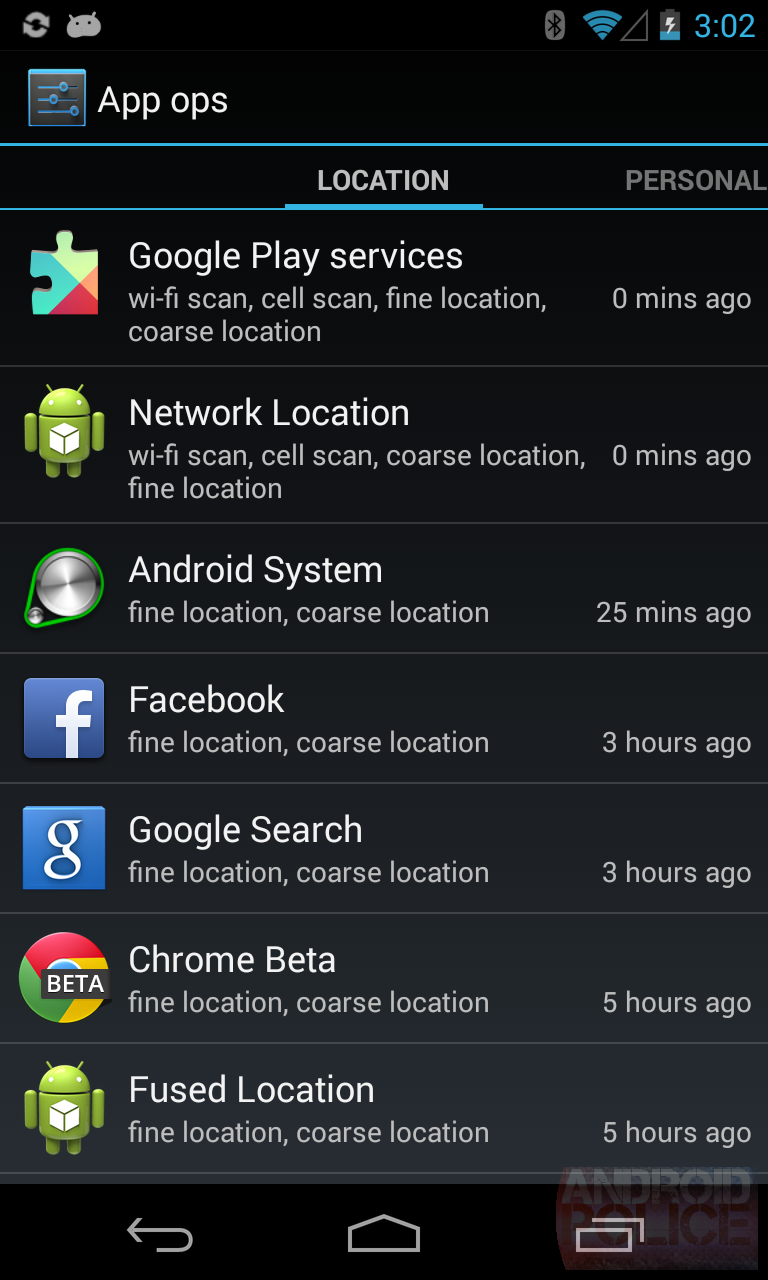
Tap the icon and you'll see something like this. There's list of all your apps and the permissions they use, categorized into 4 handy tabs. The tabs are broken down into "location," "personal," "messaging," and "device," so it's easy to see what app uses the permissions you're concerned about. On the right is a timestamp for when the app last used a permission.
edit on 4-9-2014 by eisegesis because: (no reason given)
Since THE very first phone call was recorded......Watson, come here. I need you.....what would make any rational person think that the recording would
stop? People were being recorded before telephones came out! Duh!
new topics
-
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 33 minutes ago -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 2 hours ago -
Bobiverse
Fantasy & Science Fiction: 5 hours ago -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 5 hours ago -
Former Labour minister Frank Field dies aged 81
People: 7 hours ago -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 9 hours ago
top topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 14 hours ago, 16 flags -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 5 hours ago, 7 flags -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 9 hours ago, 6 flags -
Former Labour minister Frank Field dies aged 81
People: 7 hours ago, 4 flags -
Ode to Artemis
General Chit Chat: 15 hours ago, 3 flags -
This is our Story
General Entertainment: 12 hours ago, 3 flags -
Bobiverse
Fantasy & Science Fiction: 5 hours ago, 3 flags -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 2 hours ago, 1 flags -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 33 minutes ago, 0 flags
active topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 70 • : grey580 -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 276 • : marg6043 -
So this is what Hamas considers 'freedom fighting' ...
War On Terrorism • 258 • : FlyersFan -
CIA botched its handling of sexual assault allegations, House intel report says
Breaking Alternative News • 8 • : lilzazz -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest • 44 • : xWorldxGonexMadx -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 48 • : marg6043 -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three • 11 • : JooTunnels -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology • 0 • : randomuser2034 -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest • 11 • : pianopraze -
Who are the Russians?
New World Order • 202 • : twistedpuppy
