It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
There's a new computer virus out there to warn you about and it bullies you into taking the bait.
Some computer experts are saying this is one of the worst viruses they have ever seen. It only affects windows PCs but it essentially holds your computer hostage.
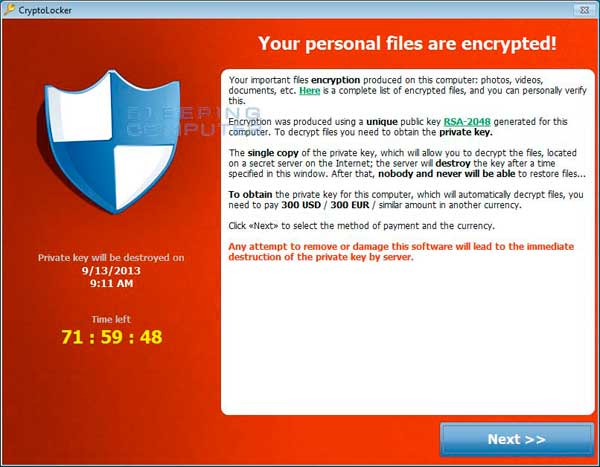
It's called Crypto Locker, a virus that's infecting computers across the country. It's delivered in the form of an email and users are tricked into opening it because it looks like it's from a legitimate company such as FedEx or UPS.
"Ransomware causes your computer files to be non-accessible and when that happens you have two choices. You can recover if you have a backup which I hope you do or pay the ransom within 100 hours. If you do not pay the ransom you lose all of your data," Computer Expert Anthony Mongeluzo said.
Source
It looks like this is a nasty one folks. Keep your important files backed up. Although it is preferable to back up your entire OS drive by creating a system image with Windows backup, or another good backup program. Right now, if you get this virus, your data is inaccessible. There is also no guarantee you will get it back if you pay the ransom, either.
I find it interesting the NSA has time to spy on its own citizens, as well as 35 other countries, but they can't track down a group of thugs who create "ransomware". That should tell us all something.
The following is a good link for reading about this new threat. Bleepingcomputer.com is a safe and trustworthy site. CryptoLocker
Here's a video that explains how it works.
ETA: Note at around 5:45 in the video, that if your anti-virus deletes part of the virus, you have to put it back in order for the decryption process to work, after you have paid the ransom.
ETA2: I almost forgot to add. Any drives that are connected to your computer at the time of infection, including network drives, USB drives of any kind, CAN be encrypted as well by this malware. If you use an external hard drive to do backups(You should), disconnect that drive when you aren't using it.
As a last note. I should make it clear, this infection is not actually a "virus". It is malware, or ransomware. Nevertheless, that doesn't make it any less of a threat.
edit on 10/28/2013 by Klassified because: ETA's - Add text - Corrections.
reply to post by Klassified
Thank you for the heads up. It's nice to know someone is looking out for the rest of us. Much appreciated info.
Thank you for the heads up. It's nice to know someone is looking out for the rest of us. Much appreciated info.
liveandlearn
reply to post by Klassified
Thank you. Just did my first ever backup.
*Thumbs up*
Make sure you keep that data separate from the computer, on an external hard drive. I added some info to the bottom of the OP.
reply to post by Klassified
It is very nasty!
Warning to all!
This malware will encrypt your files on your pc and will ransom you $300 dollars to un encrypt them.
All files on your pc and network drives are at risk.
I've already had to deal with this one. pdf's, word docs, excel files and images were encrypted on the users pc. along with several gigs of important pdf files on our shared drive.
Luckily enough we backup daily. So restoring the files was a snap. However 2 hours worth of work was lost.
For everyone with a business backup your files. Either you use it or lose it.
If you're not backing up to two different types of media you're going to wish you were.
For home users Carbonite is a good service to use.
Don't lose years of images to this ransomeware.
It is very nasty!
Warning to all!
This malware will encrypt your files on your pc and will ransom you $300 dollars to un encrypt them.
All files on your pc and network drives are at risk.
I've already had to deal with this one. pdf's, word docs, excel files and images were encrypted on the users pc. along with several gigs of important pdf files on our shared drive.
Luckily enough we backup daily. So restoring the files was a snap. However 2 hours worth of work was lost.
For everyone with a business backup your files. Either you use it or lose it.
If you're not backing up to two different types of media you're going to wish you were.
For home users Carbonite is a good service to use.
Don't lose years of images to this ransomeware.
edit on 28-10-2013 by grey580 because: (no reason given)
reply to post by grey580
Thanks for the input grey. I tried to cover all the bases in the OP, regarding what you're saying. It's good to have verification from someone who has experienced this firsthand.
Thanks for the input grey. I tried to cover all the bases in the OP, regarding what you're saying. It's good to have verification from someone who has experienced this firsthand.
reply to post by Klassified
I dont really understand how people will just open things up like that.
I mean it could happen. I have had infections before....but still. Once you learn to have common sense you dont even need an anti virus. I dont even use one anymore. I just dont open up ANYTHING I am not expecting.
If this is like one of those UPS scams, I would still run a scan even if I was in a business where UPS email was something normal for me.
I also like old fashioned everything...so I never NEEDED email for something I could just call about or go in person for.
I always say...NEVER buy anything online, NEVER use online banking, and dont give out ANY information.
I have in the past, and thats why I was a victim of identity theft. NEVER again. Just do things the way we have for years before the advent of the information age.
I dont really understand how people will just open things up like that.
I mean it could happen. I have had infections before....but still. Once you learn to have common sense you dont even need an anti virus. I dont even use one anymore. I just dont open up ANYTHING I am not expecting.
If this is like one of those UPS scams, I would still run a scan even if I was in a business where UPS email was something normal for me.
I also like old fashioned everything...so I never NEEDED email for something I could just call about or go in person for.
I always say...NEVER buy anything online, NEVER use online banking, and dont give out ANY information.
I have in the past, and thats why I was a victim of identity theft. NEVER again. Just do things the way we have for years before the advent of the information age.
Thanks for the insight, Klassified.
Luckily, I run Linux and never check my email. No one wants to talk to me.
Luckily, I run Linux and never check my email. No one wants to talk to me.
tadaman
reply to post by Klassified
I dont really understand how people will just open things up like that.
We have to clean up my mother-in-law's computer quite often because she CONSTANTLY opens stuff like that. She's gotten some really bad viruses in the past, and it wouldn't surprise me if she gets this, because stuff comes up on the screen that she doesn't understand (she's in her late 70s) and she just clicks "OK".
I've long held that computers should have a "Grandma mode", that locks the drive down and doesn't allow any changes to be made, no matter what "permission" is given, and you can restore the thing with a single click when something does sneak through.
I was actually going to start a thread about this late last night but I was too tired by the time I finished restoring from backups tens of thousands
of encrypted documents. It is exactly as bad as it sounds. I got an email about a corrupted spreadsheet around 5pm Friday, didn't give it another
thought for the next 48 hours. Then yesterday I decided to take a look and to my surprise, multiple files in the same directory are similarly FUBAR. I
ended up RDP'ing into the workstation of the user who was now owner of all these files that I knew she wouldn't normally access only to be greeted
with a ransom demand, complete with nerve wrecking countdown timer.
We do nightly backups from inside the VMs to a NAS and everything is copied to a USB drive and taken off site daily, so I was able to recover everything from the Thursday backup and only lost a day's worth of files and revisions.
I read that the most common way people are becoming infected is from spoofed emails appearing to come from UPS, FedEx, and others with an attached executable masquerading as a .PDF file. If that's how my user picked it up, it made it through our 3rd party spam/virus filtering service before not being picked up by NAV (though the definitions were out of date).
There's a lot of good information on the link to bleeping computer from the OP but here's my own short list of what I thought were the most relevant details:
- Affects Windows XP - Windows 8, local documents and anything accesible on a mapped drive
- Files are encrypted with RSA 2048, the private key used is stored on a server or servers
- Encrypts all MS Office documents, PDFs, and basically all common image formats including those used by Adobe applications like Photoshop's PSD.
- Victims are given 100 hours from when the encryption process ends (and the ransom demand pops up) to submit payment. After that, it uninstalls itself and you're left uninfected (allegedly) but with your data irrecoverably encrypted.
- Payment can be made with Green Dot MoneyPak and Bitcoin.
- People are apparently paying (estimates I saw are 3%) and the keys are sent though in some cases it was well over a week before receipt. Once the software receives the key, it decrypts everything and removes itself (allegedly).
I formatted and reinstalled the workstation but apparently MalwareBytes will remove it. We of course did not pay--if we didn't have backups, we would have been forced to but that's what backups are for, keeping you out of situations like that
We do nightly backups from inside the VMs to a NAS and everything is copied to a USB drive and taken off site daily, so I was able to recover everything from the Thursday backup and only lost a day's worth of files and revisions.
I read that the most common way people are becoming infected is from spoofed emails appearing to come from UPS, FedEx, and others with an attached executable masquerading as a .PDF file. If that's how my user picked it up, it made it through our 3rd party spam/virus filtering service before not being picked up by NAV (though the definitions were out of date).
There's a lot of good information on the link to bleeping computer from the OP but here's my own short list of what I thought were the most relevant details:
- Affects Windows XP - Windows 8, local documents and anything accesible on a mapped drive
- Files are encrypted with RSA 2048, the private key used is stored on a server or servers
- Encrypts all MS Office documents, PDFs, and basically all common image formats including those used by Adobe applications like Photoshop's PSD.
- Victims are given 100 hours from when the encryption process ends (and the ransom demand pops up) to submit payment. After that, it uninstalls itself and you're left uninfected (allegedly) but with your data irrecoverably encrypted.
- Payment can be made with Green Dot MoneyPak and Bitcoin.
- People are apparently paying (estimates I saw are 3%) and the keys are sent though in some cases it was well over a week before receipt. Once the software receives the key, it decrypts everything and removes itself (allegedly).
I formatted and reinstalled the workstation but apparently MalwareBytes will remove it. We of course did not pay--if we didn't have backups, we would have been forced to but that's what backups are for, keeping you out of situations like that
sheepslayer247
Thanks for the insight, Klassified.
Luckily, I run Linux and never check my email. No one wants to talk to me.
Yep. Only affects Windoze...For now. I won't be surprised if an Apple version of it hits the intertubez though.
That's because they know you never check your e-mail.
edit on 10/28/2013 by Klassified because: duh grammar
reply to post by adjensen
LOL! I second the Grandma Mode. I have lots of those little old ladies, and they can get into more trouble...
I've long held that computers should have a "Grandma mode", that locks the drive down and doesn't allow any changes to be made, no matter what "permission" is given, and you can restore the thing with a single click when something does sneak through.
LOL! I second the Grandma Mode. I have lots of those little old ladies, and they can get into more trouble...
reply to post by Klassified
In my personal opinion, the way society handles and punishes the people behind these needs to be elevated to a significant degree. There isn't near the deterrent 'it isn't worth it' factor now that there needs to be.
Thanks for the heads up on this. I get a bit lax at times about backing up and this is a good reminder to keep on it like it really matters. It sure would if this little sucker came calling. Ouch... Nasty one there.
In my personal opinion, the way society handles and punishes the people behind these needs to be elevated to a significant degree. There isn't near the deterrent 'it isn't worth it' factor now that there needs to be.
Thanks for the heads up on this. I get a bit lax at times about backing up and this is a good reminder to keep on it like it really matters. It sure would if this little sucker came calling. Ouch... Nasty one there.
reply to post by Wrabbit2000
Absolutely. It should be a serious offense, internationally. Not that I really think that's going to happen.
Yeah, it sobered me up too.
In my personal opinion, the way society handles and punishes the people behind these needs to be elevated to a significant degree. There isn't near the deterrent 'it isn't worth it' factor now that there needs to be.
Absolutely. It should be a serious offense, internationally. Not that I really think that's going to happen.
Thanks for the heads up on this. I get a bit lax at times about backing up and this is a good reminder to keep on it like it really matters. It sure would if this little sucker came calling. Ouch... Nasty one there.
Yeah, it sobered me up too.
Of course the video is showing XP which wont tell you when you run an exe.
In windows 7 if you double click a PDF that is really an exe file you system will inform you that the program is about to make changes to your computer and ask you for permission first. This should be enough warning that something is wrong.
In windows 7 if you double click a PDF that is really an exe file you system will inform you that the program is about to make changes to your computer and ask you for permission first. This should be enough warning that something is wrong.
edit on 28-10-2013 by PhoenixOD because: (no reason given)
reply to post by Klassified
no problem.
also let me add that the malware package also installs several Trojans onto your pc as well.
the Trojans are designed to steal your passwords.
malware bytes anti malware will remove the Trojans if you get hit with this.
no problem.
also let me add that the malware package also installs several Trojans onto your pc as well.
the Trojans are designed to steal your passwords.
malware bytes anti malware will remove the Trojans if you get hit with this.
PhoenixOD
Of course the video is showing XP which wont tell you when you run an exe.
In windows 7 if you double click an exe that is really an exe file you system will inform you that the program is about to make changes to your computer and ask you for permission first. This should be enough warning that something is wrong.
True enough, for you, me, and the more savvy computer users. But many will click yes, because in their mind, "make changes to your computer" doesn't always register. Just as file extensions don't. Because most people have nothing to truly relate those things to. So they don't really understand what it all means. They just know what they want the machine to do at the moment.
That said. I agree with you. It should be their first warning sign to look again at what they just clicked on, before they click the second time.
grey580
reply to post by Klassified
no problem.
also let me add that the malware package also installs several Trojans onto your pc as well.
the Trojans are designed to steal your passwords.
malware bytes anti malware will remove the Trojans if you get hit with this.
Isn't that a kick in the seat of the pants? So even if a person pays the ransom, and they're files are actually decrypted, they still have a passel of password stealing trojans, and probably keyloggers to deal with.
adjensen
We have to clean up my mother-in-law's computer quite often...
Get Granny on Linux ASAP! I recommend Linux Mint.
The article i just read about it mentions bitcoins specifically,
time to put on my tinfoil hat, what if its a false flag to take
what little credibility bitcoin has left and flush it?
Get rid of something that was becoming a thorn in their side.
A big thank you the OP, i haven't run across this one yet and
hopefully can get my customers to avoid it as well.
time to put on my tinfoil hat, what if its a false flag to take
what little credibility bitcoin has left and flush it?
Get rid of something that was becoming a thorn in their side.
A big thank you the OP, i haven't run across this one yet and
hopefully can get my customers to avoid it as well.
new topics
-
12 jurors selected in Trump criminal trial
US Political Madness: 2 hours ago -
Iran launches Retalliation Strike 4.18.24
World War Three: 2 hours ago -
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three: 2 hours ago -
George Knapp AMA on DI
Area 51 and other Facilities: 8 hours ago -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 8 hours ago -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 10 hours ago
top topics
-
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 15 hours ago, 25 flags -
George Knapp AMA on DI
Area 51 and other Facilities: 8 hours ago, 23 flags -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 16 hours ago, 18 flags -
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three: 2 hours ago, 12 flags -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 16 hours ago, 7 flags -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 10 hours ago, 7 flags -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 14 hours ago, 5 flags -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 8 hours ago, 4 flags -
Iran launches Retalliation Strike 4.18.24
World War Three: 2 hours ago, 4 flags -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 12 hours ago, 3 flags
active topics
-
MULTIPLE SKYMASTER MESSAGES GOING OUT
World War Three • 44 • : SchrodingersRat -
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness • 15 • : BingoMcGoof -
Running Through Idiot Protestors Who Block The Road
Rant • 109 • : Astyanax -
Iran launches Retalliation Strike 4.18.24
World War Three • 10 • : VoiceofReality -
12 jurors selected in Trump criminal trial
US Political Madness • 20 • : Lumenari -
Pfizer is 'deeply sorry'
Diseases and Pandemics • 23 • : VoiceofReality -
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three • 47 • : YourFaceAgain -
It has begun... Iran begins attack on Israel, launches tons of drones towards the country
World War Three • 887 • : 5thHead -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics • 20 • : ScarletDarkness -
Terrifying Encounters With The Black Eyed Kids
Paranormal Studies • 44 • : Consvoli
