It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Originally posted by sean
Originally posted by tetra50
Microsoft/Apple, whatever....they all have backdoors for remote control. Take a look at the current patents on all things computing......
Everyone seems to think that computer networks are security conscious, more than paper or anything. Nothing could be further from the truth. It was why this computational universal connection was created, after all.
The government created the internet as a spy highway and so here we are being spied upon.
and perhaps even to superimpose, if you will, it over the current universe, as we use that energy in other ways.....
Not quite sure how to put what I mean into words, but this is as close as I can come. Sort of a holographic universe, to replace the real one..
reply to post by StargateSG7
Not sure if you are talking to me or the other guy you quoted. Anyways, there are favorable benefits to static over dynamic. If you are running a server you wouldn't want it's IP constantly changing every time the lease runs out. Then all your IP's that is stored in your software will be incorrect and you will have to constantly change it. Changing mac address on the router constantly will cause more problems than it's worth. Typically you are going to probably pull a new IP down from your internet provider which will probably knock your network down for a while till everything is back up. I only do that if it's absolutely necessary and you are being DDOS or something nasty going on. Most internet providers are pretty good at keeping you set to your same WAN IP regardless of what your mac is. It sometimes can be hard to push it back to the IP pool. As an example I have had my so called DHCP IP from my provider now for about 5 years. I have gone through 3 routers as well as 3 Modems and done lots of mac cloning in between that time I am sure.
Yes, scan mapping a network is possible, but the buck stops at the NAT router. I don't enable port forwarding on some servers until I am actually going to use them and most are just VM's and are shut down completely until used. Most hackers scanning a network are looking for known default ports that are opened such as 21, 22, etc. You don't have to run a server on those default ports and if you are then enjoy all the knocking on your back door constantly. It's best to change them. Also turning off replies in the router as well as UPNP. Turn off WPS (wifi protected setup) Or get a router that doesn't even have it. Sometimes turning it off it really doesn't turn off. Majority of routers out there are exploitable because of WPS even if you have WPA/WPA2. Most can be hacked in under 2 hours. Best to get a router capable of handling 3rd party firmware such as DDWRT or Tomato. A lot of routers cannot use DDWRT and cannot be updated to fix the exploit and basically you need to junk it and buy a new one.
If some noob is scanning your network on all ports then alerts are going to be popping up left and right and everything is going to be logged either in the router or on the soft firewall. Someone doing a deep scan on all ports is more than likely going find himself being scanned and his internet provider notified.
Furthermore, put a server on a double NAT network for extra security especially something like a Web Server you are hosting yourself. Put it on a subnet of it's own or in a DMZ. So if the one network is ever compromised no traffic can be traversed back through to the network that is hosting file shares etc. let the public server fend for itself.
That sums it up for me.
Not sure if you are talking to me or the other guy you quoted. Anyways, there are favorable benefits to static over dynamic. If you are running a server you wouldn't want it's IP constantly changing every time the lease runs out. Then all your IP's that is stored in your software will be incorrect and you will have to constantly change it. Changing mac address on the router constantly will cause more problems than it's worth. Typically you are going to probably pull a new IP down from your internet provider which will probably knock your network down for a while till everything is back up. I only do that if it's absolutely necessary and you are being DDOS or something nasty going on. Most internet providers are pretty good at keeping you set to your same WAN IP regardless of what your mac is. It sometimes can be hard to push it back to the IP pool. As an example I have had my so called DHCP IP from my provider now for about 5 years. I have gone through 3 routers as well as 3 Modems and done lots of mac cloning in between that time I am sure.
Yes, scan mapping a network is possible, but the buck stops at the NAT router. I don't enable port forwarding on some servers until I am actually going to use them and most are just VM's and are shut down completely until used. Most hackers scanning a network are looking for known default ports that are opened such as 21, 22, etc. You don't have to run a server on those default ports and if you are then enjoy all the knocking on your back door constantly. It's best to change them. Also turning off replies in the router as well as UPNP. Turn off WPS (wifi protected setup) Or get a router that doesn't even have it. Sometimes turning it off it really doesn't turn off. Majority of routers out there are exploitable because of WPS even if you have WPA/WPA2. Most can be hacked in under 2 hours. Best to get a router capable of handling 3rd party firmware such as DDWRT or Tomato. A lot of routers cannot use DDWRT and cannot be updated to fix the exploit and basically you need to junk it and buy a new one.
If some noob is scanning your network on all ports then alerts are going to be popping up left and right and everything is going to be logged either in the router or on the soft firewall. Someone doing a deep scan on all ports is more than likely going find himself being scanned and his internet provider notified.
Furthermore, put a server on a double NAT network for extra security especially something like a Web Server you are hosting yourself. Put it on a subnet of it's own or in a DMZ. So if the one network is ever compromised no traffic can be traversed back through to the network that is hosting file shares etc. let the public server fend for itself.
That sums it up for me.
edit on 17-7-2013 by sean because: (no reason given)
What about the plug in the wall where you plug your computer up? I figure the gov can access your computer through there somehow regardless if you
have an internet connection. BPL exists. (Broadband over Power Line).
reply to post by Voyager1
Or... what? You could just take direct connection with a device. Maybe even a satellite, though there might be more lag.
BPL was OLD technology, heck, even satellites have been around since forever.
Or... what? You could just take direct connection with a device. Maybe even a satellite, though there might be more lag.
BPL was OLD technology, heck, even satellites have been around since forever.
Originally posted by sean
reply to post by StargateSG7
...Anyways, there are favorable benefits to static over dynamic. If you are running a server you wouldn't want it's IP constantly changing every time the lease runs out. Then all your IP's that is stored in your software will be incorrect and you will have to constantly change it. Changing mac address on the router constantly will cause more problems than it's worth. Typically you are going to probably pull a new IP down from your internet provider which will probably knock your network down for a while till everything is back up. I only do that if it's absolutely necessary and you are being DDOS or something nasty going on. Most internet providers are pretty good at keeping you set to your same WAN IP regardless of what your mac is. It sometimes can be hard to push it back to the IP pool. As an example I have had my so called DHCP IP from my provider now for about 5 years. I have gone through 3 routers as well as 3 Modems and done lots of mac cloning in between that time I am sure.
Yes, scan mapping a network is possible, but the buck stops at the NAT router. I don't enable port forwarding on some servers until I am actually going to use them and most are just VM's and are shut down completely until used. Most hackers scanning a network are looking for known default ports that are opened such as 21, 22, etc. You don't have to run a server on those default ports and if you are then enjoy all the knocking on your back door constantly. It's best to change them. Also turning off replies in the router as well as UPNP. Turn off WPS (wifi protected setup) Or get a router that doesn't even have it. Sometimes turning it off it really doesn't turn off. Majority of routers out there are exploitable because of WPS even if you have WPA/WPA2. Most can be hacked in under 2 hours. Best to get a router capable of handling 3rd party firmware such as DDWRT or Tomato. A lot of routers cannot use DDWRT and cannot be updated to fix the exploit and basically you need to junk it and buy a new one.
If some noob is scanning your network on all ports then alerts are going to be popping up left and right and everything is going to be logged either in the router or on the soft firewall. Someone doing a deep scan on all ports is more than likely going find himself being scanned and his internet provider notified.
Furthermore, put a server on a double NAT network for extra security especially something like a Web Server you are hosting yourself. Put it on a subnet of it's own or in a DMZ. So if the one network is ever compromised no traffic can be traversed back through to the network that is hosting file shares etc. let the public server fend for itself.
That sums it up for me.edit on 17-7-2013 by sean because: (no reason given)
---
On our side we let a 3rd party service provider CONSTANTLY update every minute our current
IP address which we can FORCE an IP address change on. and then also we FORCE a MAC
address change. it's called DDNS (or Dynamic Domain Name Service) our NEW MAC address
and NEW Gateway/Router IP address gets sent to the 3rd party DNS provider which updates
its records every minute or so. This prevents scanners from associating our hardware with
any specific IP address.
I probably shouldn't be saying this in a public forum, but to give you a taste of how paranoid
our IT department is (that would be ME!) we have FIVE LAYERS OF ROUTERS EACH
separated by a high-end firewall from different manufacturers that have widely
disparate internal IP addresses. Any attacker has to go through 10 layers of security
to get to our final internal fully encrypted network system. We've modified the firmware
ON ALL those routers to open source code and have NO remote management services.
We have NOTHING that is wireless...all high end fibre LAN connections NOT using AES-256
but rather our custom long-bit-length MULTI-ALGORITHM encrypt/decrypt system embedded
into standard TCP/IP packets (i.e. nested packets). ALL TRUSTED-COMPUTING
environment versions of Linux with all our drivers vetted and embedded into the Kernel
and the ENTIRE OS LOCKED to the motherboards and CPU's to prevent replacement!
Servers are all alarmed and secured in 2 inch thick solid steel cabinets (weighs MANY TONNES!)
with specialty locks with security-vetted open-source biometric entry software and hardware which are
ALWAYS LOGGED! We also have FARADAY CAGED, EMP SHIELDED and TEMPEST-rated
alarms, cameras, monitors, workstations and SECURED FULLY STEEL-PIPED comm fibre links
with pressurized nitrogen gas to prevent physical taps. WE ARE FAR WORSE THAN THE NSA
when it comes to information security paranoia !!!
I should that we do this to protect something really BIG...something that the rest of the world
will soon want!
edit on 2013/7/18 by StargateSG7 because: sp.
edit on 2013/7/18 by StargateSG7 because: sp
reply to post by StargateSG7
I was mainly talking about a typical home private network. All the things you mentioned is nice and comes with a hefty price tag. All that security is great, but the NSA forces themselves on MA BELL down the the street controls the root of all connections so there is no stopping them from placing a tap. You could always launch your own satellite up into space and create your own internet lol.
A friend of mine used to be a electrician till the jobs went sour so he got into IT bought out a small computer repair shop etc and done a little work for some large networks in the area. We got a great deal on renting some game servers etc, but eventually he got FTTH and hosted himself. He's on east coast in NY I am on west coast. The latency was yuck. Often we would get something in between like a Colorado server. You can see trace roots going to the same points for no reason other than the GOV spying on everything.
Some of them was blatantly obvious It would be something like Colorado, Washington DC, Seattle Washington, down to California, back through Seattle, Back through Washington DC and back to Colorado. LOL The DC connection is obvious but whats in Seattle? Well Microsoft, FBI main HQ, NSA main HQ god knows what else. so there is no stopping the gov tapping main trunks. So just make darn sure your stuff is wrapped up tight with hella encrpytion.
I was mainly talking about a typical home private network. All the things you mentioned is nice and comes with a hefty price tag. All that security is great, but the NSA forces themselves on MA BELL down the the street controls the root of all connections so there is no stopping them from placing a tap. You could always launch your own satellite up into space and create your own internet lol.
A friend of mine used to be a electrician till the jobs went sour so he got into IT bought out a small computer repair shop etc and done a little work for some large networks in the area. We got a great deal on renting some game servers etc, but eventually he got FTTH and hosted himself. He's on east coast in NY I am on west coast. The latency was yuck. Often we would get something in between like a Colorado server. You can see trace roots going to the same points for no reason other than the GOV spying on everything.
Some of them was blatantly obvious It would be something like Colorado, Washington DC, Seattle Washington, down to California, back through Seattle, Back through Washington DC and back to Colorado. LOL The DC connection is obvious but whats in Seattle? Well Microsoft, FBI main HQ, NSA main HQ god knows what else. so there is no stopping the gov tapping main trunks. So just make darn sure your stuff is wrapped up tight with hella encrpytion.
Originally posted by tigershark1988
An uninformed question: What is a security hole?
It's what you get after a TSA search after refusing to go through a scanner at the airport.
This is your hole normally, this is your security hole after a TSA strip search
Originally posted by sean
reply to post by StargateSG7
I was mainly talking about a typical home private network. All the things you mentioned is nice and comes with a hefty price tag. All that security is great, but the NSA forces themselves on MA BELL down the the street controls the root of all connections so there is no stopping them from placing a tap. You could always launch your own satellite up into space and create your own internet lol.
A friend of mine used to be a electrician till the jobs went sour so he got into IT bought out a small computer repair shop etc and done a little work for some large networks in the area. We got a great deal on renting some game servers etc, but eventually he got FTTH and hosted himself. He's on east coast in NY I am on west coast. The latency was yuck. Often we would get something in between like a Colorado server. You can see trace roots going to the same points for no reason other than the GOV spying on everything.
Some of them was blatantly obvious It would be something like Colorado, Washington DC, Seattle Washington, down to California, back through Seattle, Back through Washington DC and back to Colorado. LOL The DC connection is obvious but whats in Seattle? Well Microsoft, FBI main HQ, NSA main HQ god knows what else. so there is no stopping the gov tapping main trunks. So just make darn sure your stuff is wrapped up tight with hella encrpytion.
---
ATT and Verizon are the worst for having Man-In-The-Middle taps
NSA does have a Seattle office but that's not IT oriented.
I suspect it's that GIANT data server farm that has been alluded to in the past
somewhere on the Olympic Peninsula, probably near Bremerton my guess
because of the large Navy base.
From what I understand, the NSA has regional data centres that are
HOT BACKUP sites for their current main Ft. Meade centre.
i.e. SouthWest, Northwest, NorthEast and Southeast data centres
These centres are the size of a typical Walmart and I think
TWO are fully underground. The near-Los Angeles one is from
what I understand close to a large mountain water reservoir
and is fully underground!
The North East one is in Upper New York,
The southeast one in Georgia and the main one at Ft Meade, MD
That's the information that has been "whispered to me" but I have
no absolute confirmation that this is actually true.
I SUSPECT that specialty data centres used for number crunching
on special projects rather than data-gathering are also located
in illinois, Ohio, Texas, Colorado and Nevada.
There is also an NRO data centre office in the Blue Ridge mountains
(close to the Virginia's or Carolinas) used by the NSA for image
analysis but that's been known for decades now.
---
Yup we have spent a pretty penny on drives, computing servers and workstations
not to mention security for the last 15 years! I know we are into the many-many-Petabyte
if not multi-EXABYTE range on video data alone! I've got over a petabyte just under my desk!
That's a 1000+ Terabytes of video data! YIKES!!!! No wonder our backups take so long!
edit on 2013/7/18 by StargateSG7 because: sp.
These days there shouldn't be any need to route stuff just to tap into it...routers have port mirroring so whatever goes up/down one cable will be
sent down another (to the boys at the NSA to have a look over) and you can even do the same with fibre optics but will be just as easy to mirror it
down a copper cable than have to start work on the actual fibre optics and it'll be very noticeable to anyone looking into the cabinet compared with
just another network cable running away somewhere
Originally posted by Maxatoria
These days there shouldn't be any need to route stuff just to tap into it...routers have port mirroring so whatever goes up/down one cable will be sent down another (to the boys at the NSA to have a look over) and you can even do the same with fibre optics but will be just as easy to mirror it down a copper cable than have to start work on the actual fibre optics and it'll be very noticeable to anyone looking into the cabinet compared with just another network cable running away somewhere
---
The NSA boys would have to do a "Black Bag Job" on our site in order to install a physical tap
on our internal fibre network lines but the pressure differential on a tap into the Nitrogen gas-infused
comm lines would sound the alarm and let us know something is up. Not to mention that a mild
electrical current is put on the pipes and measured on a continuous basis to get average resistance
and noise floor so we can tell if a tap is being installed at all! Ah what the heck! I'll let them know
that we've got BOTH optical and MULTI-SPECTRAL Hidden and Visible Cameras (IR, UV,
Acoustic Imaging and Soft XRAY and multi-band RF detectors) and a high-end CUSTOM-BUILT
TEMPEST-RATED software/hardware machine vision system that scans for the HUMAN SIZED
and SHAPED DISTORTED EDGES that accompany advanced optical and multi-spectral
camouflage systems. It can HUNT, TRACK and LOCK onto tens of thousands of objects
per second...so good luck! Not to mention there's 24hr security!
SERIOUSLY! We are TEN THOUSAND TIMES MORE PARANOID
than the NSA is about Data Security!
edit on 2013/7/19 by StargateSG7 because: sp.
Originally posted by iwilliam
Originally posted by andy06shake
That svchost.exe can be a real resource hog sometimes, guess now we know why!
Seriously. I've wondered about that, myself. Sometimes this process takes up quite a large % of my CPU.
At different periods I have also seen more than one svchost.exe process running.
Are we sure, if this is indeed connecting to microsoft, that it doesn't just have to do with "Windows Update" or whatnot? IME Windows update can be pretty intrusive / aggressive sometimes.
Anyway, back to the process... speaking of multiple processes, a couple of the times I've seen multiple instances of svchost.exe running, I was under the impression / belief that my system was infected, and that this process might have been part of that infection. Actually, I think I recalled reading somewhere that sometimes a virus will disguise its running process as "svchost.exe." But don't quote me on that one....
SCVHOST is the Windows NT equivalent of RUNDLL from Windows 9x. A DLL can't be run as a program, it has to be run under either SVCHOST or RUNDLL. As one faulting DLL could take down the entire SVCHOST/RUNDLL process, each DLL is run under its own process. Malware can hide itself by either injecting a DLL into the SVCHOST/RUNDLL process, or calling itself SVCHOST.exe or RUNDLL.exe. However, it is quite normal to see multiple entries, as you can see in the image I'm linking I have ten right now.
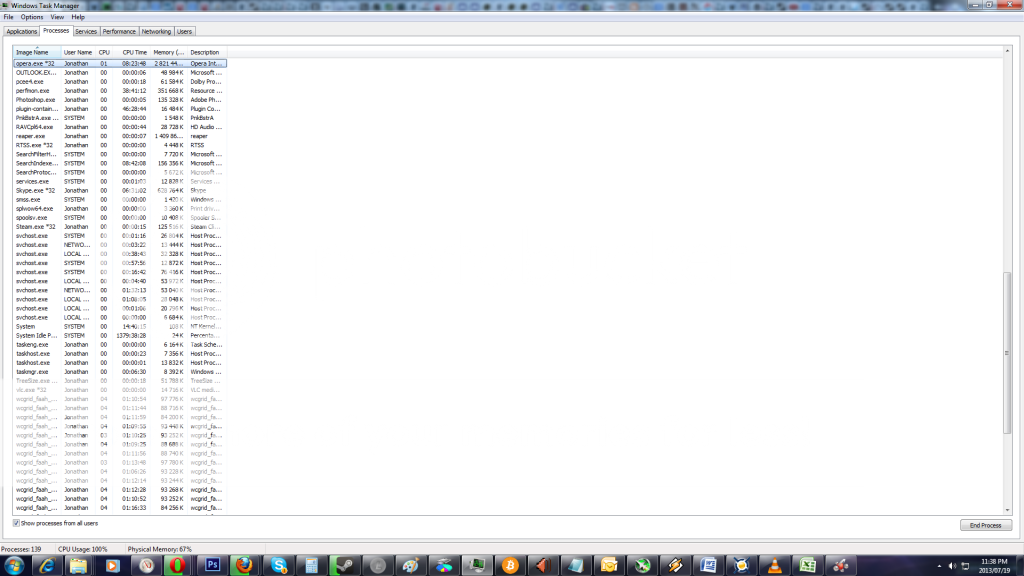
edit on 19-7-2013 by Oj101 because: added larger, readable
image
Ok I have never used a router & I run Win 8, have a printer, & a not so smart
cell phone. I download movies & music so what would be the best router for me?
I want to be wireless which me laptop has....
I am not savoy in computer world...however I do want protection & read about the
DD-WRT in OP's post so i would be so grateful for your input.
Cheers
Ektar
cell phone. I download movies & music so what would be the best router for me?
I want to be wireless which me laptop has....
I am not savoy in computer world...however I do want protection & read about the
DD-WRT in OP's post so i would be so grateful for your input.
Cheers
Ektar
reply to post by Ektar
Shopping for a router you really have to do some homework. It's sad and pathetic really as the average person wouldn't even know. Some of these lemon routers are still being sold in stores. Here's a link to a spreadsheet of all the known routers it's not complete as many routers out there are unknowns.
WPS Vulnerability Router Spreadsheet
US CERT (Computer Emergency Response Team) Good info on everything related to internet security recent threats etc.
US Cert
DDWRT website. They have a router search engine link there for which routers can be flashed with DDWRT
DDWRT
Essentially DDWRT has lots more options you typically would find on a more expensive router; If the router has enough ram and cpu power etc that can handle a much larger flash file. Faster better routers are constantly coming out, but some oldies but goodies are still out there and can be picked up at places like Amazon.com the well sought after Cisco-Linksys WRT54G or GL It's not wireless N, but this router still kicks butt. It can handle the DDWRT and has twice the CPU power than most routers in it's class. On Amazon.com you can just do a search for DDWRT and lots of routers pop up. Others are really good too like Maybe the Asus or Netgear N600's that has all the bells and whistles like sharing a USB drive over the network.
Shopping for a router you really have to do some homework. It's sad and pathetic really as the average person wouldn't even know. Some of these lemon routers are still being sold in stores. Here's a link to a spreadsheet of all the known routers it's not complete as many routers out there are unknowns.
WPS Vulnerability Router Spreadsheet
US CERT (Computer Emergency Response Team) Good info on everything related to internet security recent threats etc.
US Cert
DDWRT website. They have a router search engine link there for which routers can be flashed with DDWRT
DDWRT
Essentially DDWRT has lots more options you typically would find on a more expensive router; If the router has enough ram and cpu power etc that can handle a much larger flash file. Faster better routers are constantly coming out, but some oldies but goodies are still out there and can be picked up at places like Amazon.com the well sought after Cisco-Linksys WRT54G or GL It's not wireless N, but this router still kicks butt. It can handle the DDWRT and has twice the CPU power than most routers in it's class. On Amazon.com you can just do a search for DDWRT and lots of routers pop up. Others are really good too like Maybe the Asus or Netgear N600's that has all the bells and whistles like sharing a USB drive over the network.
reply to post by sean
Thank you for your response. I am finding this thread to be very educational
although some of it is way over me head at least it provides enough information
to look into things in more depth. I have been looking into different routers & info
for the past week. I'm thinking of getting Netgear WNDR4300-100NAS N750.
There is a good rebate & offer ends today. I can't tell if it supports DD-WRT or not.
Cheers
Ektar
Thank you for your response. I am finding this thread to be very educational
although some of it is way over me head at least it provides enough information
to look into things in more depth. I have been looking into different routers & info
for the past week. I'm thinking of getting Netgear WNDR4300-100NAS N750.
There is a good rebate & offer ends today. I can't tell if it supports DD-WRT or not.
Cheers
Ektar
as an old computer guy from the DOS 3.11 and WIN95 days, ALL, and I mean ALL software system platforms have "backdoors", even Linux......I keep
saying this, "what can be written, can be read"
reply to post by jimmyx
Everythings about the value of your data as to how much effort someone will expend to get at it, commercial operating systems by default will always have ways to bypass security features as the last thing you'd want to hear is sorry we can't do the payroll due to jeff in HR has forgotten his password so it'll be 2-3 weeks before you can get paid at the earliest, with linux the source is out there if you can be bothered to read a metric crap-ton of source code and understand it
These days with most data being held centrally for organisations it makes very little value to be able to control the workstation when you can just turn up with a court order and collect everything you want from the servers and now thats being put into the cloud you don't even know that they've sucked up all your data as its a warrant presented 300 miles away from your office with orders of not to tell you compared to the fact they'd of had to of carted off your servers from your offices years ago
Everythings about the value of your data as to how much effort someone will expend to get at it, commercial operating systems by default will always have ways to bypass security features as the last thing you'd want to hear is sorry we can't do the payroll due to jeff in HR has forgotten his password so it'll be 2-3 weeks before you can get paid at the earliest, with linux the source is out there if you can be bothered to read a metric crap-ton of source code and understand it
These days with most data being held centrally for organisations it makes very little value to be able to control the workstation when you can just turn up with a court order and collect everything you want from the servers and now thats being put into the cloud you don't even know that they've sucked up all your data as its a warrant presented 300 miles away from your office with orders of not to tell you compared to the fact they'd of had to of carted off your servers from your offices years ago
reply to post by Ektar
DDWRT website says it supports Netgear WNDR4300 revison or V4. You really don't know the revision of the router till you buy it and see. As an example some routers will sell and may say v1, v1.5, v2 and DDWRT may say it supports 1 and 1.5 but not 2 yet. They are always updating and developing so if the revision or type or router doesn't show up on the list doesn't mean that later on something might be developed for it. Things like this takes time. Even if you couldn't put DDWT on the Netgear WNDR4300-100NAS N750 it still is a monster of a router, with good features and will serve you well. Good Luck.
By the way it looks free in the clear as far as WPS vulnerability goes.
DDWRT website says it supports Netgear WNDR4300 revison or V4. You really don't know the revision of the router till you buy it and see. As an example some routers will sell and may say v1, v1.5, v2 and DDWRT may say it supports 1 and 1.5 but not 2 yet. They are always updating and developing so if the revision or type or router doesn't show up on the list doesn't mean that later on something might be developed for it. Things like this takes time. Even if you couldn't put DDWT on the Netgear WNDR4300-100NAS N750 it still is a monster of a router, with good features and will serve you well. Good Luck.
By the way it looks free in the clear as far as WPS vulnerability goes.
edit on 22-7-2013 by sean because: (no reason given)
reply to post by Maxatoria
Reminds me the other day I was watching the Trayvon & Zimmerman case of how they pulled data off of Trayvon's cell phone using Cellebrite software/hardware. Talking about an android app he used to supposedly secure pictures with a password pin lockout on the cell phone. Those apps are absolutely useless. It's easy to root phone or using something like cellebrite that can access or copy the dat image of the phone and pick it apart. Files that was deleted can still be retrieved too. It is never truly deleted till something is overwritten with more data. To truly hide something you need to encrypt it. Also, it is wise to have a app that can secure delete files or wipe recently deleted and blank space with junk 1's/0's.
Reminds me the other day I was watching the Trayvon & Zimmerman case of how they pulled data off of Trayvon's cell phone using Cellebrite software/hardware. Talking about an android app he used to supposedly secure pictures with a password pin lockout on the cell phone. Those apps are absolutely useless. It's easy to root phone or using something like cellebrite that can access or copy the dat image of the phone and pick it apart. Files that was deleted can still be retrieved too. It is never truly deleted till something is overwritten with more data. To truly hide something you need to encrypt it. Also, it is wise to have a app that can secure delete files or wipe recently deleted and blank space with junk 1's/0's.
Just want to post back to this. All I can say is I told you so. Since the thread died we had MSFT Windows 10 come out with built in spyware and
recently MSFT government back doors into your system according to Wikileaks vault 7 information.
I will give you an example...When you install Windows a unique ID is generated. So when you update or windows dials home (automatically) with the data they collect, they also log the date/time, geo location, IP address. This is one way they can track even through a VPN and the IP address has changed. They just look up the current IP address and reverse lookup the unique ID associate with it. They now know your previous IP and current IP. Your previous IP is linked to your ISP, thus revealing your identity. Now they just strong arm threaten the ISP for that information. See how that works?
This is just one part of this rabbit hole. The real threat to national security is the CIA. So anyone running Windows can be spied on. So not just everyday Joe, but that's in corporate world, stock market, Medical, government branches not apart of CIA, They know EVERYTHING and Control EVERYTHING. This reminds me of the movie Sneakers. The little black box that can take control of anything.
You want to crash a few planes? Want to write yourself a billion dollar check? SWAT team your mayor? Kill your neighbor? Start a war? Nuke a small country?
I will give you an example...When you install Windows a unique ID is generated. So when you update or windows dials home (automatically) with the data they collect, they also log the date/time, geo location, IP address. This is one way they can track even through a VPN and the IP address has changed. They just look up the current IP address and reverse lookup the unique ID associate with it. They now know your previous IP and current IP. Your previous IP is linked to your ISP, thus revealing your identity. Now they just strong arm threaten the ISP for that information. See how that works?
This is just one part of this rabbit hole. The real threat to national security is the CIA. So anyone running Windows can be spied on. So not just everyday Joe, but that's in corporate world, stock market, Medical, government branches not apart of CIA, They know EVERYTHING and Control EVERYTHING. This reminds me of the movie Sneakers. The little black box that can take control of anything.
You want to crash a few planes? Want to write yourself a billion dollar check? SWAT team your mayor? Kill your neighbor? Start a war? Nuke a small country?
new topics
-
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion: 17 minutes ago -
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues: 43 minutes ago -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum: 1 hours ago -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 2 hours ago -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 2 hours ago -
Weinstein's conviction overturned
Mainstream News: 3 hours ago -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 5 hours ago -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 5 hours ago -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 6 hours ago -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 8 hours ago
top topics
-
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 5 hours ago, 8 flags -
Weinstein's conviction overturned
Mainstream News: 3 hours ago, 6 flags -
Electrical tricks for saving money
Education and Media: 17 hours ago, 5 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 5 hours ago, 5 flags -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 8 hours ago, 5 flags -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News: 2 hours ago, 4 flags -
Massachusetts Drag Queen Leads Young Kids in Free Palestine Chant
Social Issues and Civil Unrest: 2 hours ago, 3 flags -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 6 hours ago, 2 flags -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 10 hours ago, 2 flags -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 14 hours ago, 1 flags
active topics
-
Gaza Terrorists Attack US Humanitarian Pier During Construction
Middle East Issues • 10 • : CarlLaFong -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 770 • : xuenchen -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 177 • : theatreboy -
The functionality of boldening and italics is clunky and no post char limit warning?
ATS Freshman's Forum • 8 • : grey580 -
Breaking Baltimore, ship brings down bridge, mass casualties
Other Current Events • 487 • : Threadbarer -
2024 Pigeon Forge Rod Run - On the Strip (Video made for you)
Automotive Discussion • 1 • : chiefsmom -
Fossils in Greece Suggest Human Ancestors Evolved in Europe, Not Africa
Origins and Creationism • 84 • : whereislogic -
Ditching physical money
History • 21 • : SprocketUK -
Meadows, Giuliani Among 11 Indicted in Arizona in Latest 2020 Election Subversion Case
Mainstream News • 4 • : ElitePlebeian2 -
Is there a hole at the North Pole?
ATS Skunk Works • 38 • : Therealbeverage
