It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
reply to post by PhoenixOD
Logically and Properly ...Yes.
But there are major "Piggybacks" occurring.
The Source Download is Not Sterile.
NSA provided the hardware in the middle of the night to Bill from the get go.
There is a solid allegiance there.
It is O.K. with me. But I would be careful with my Patents and Ideas. SAVVY?
Logically and Properly ...Yes.
But there are major "Piggybacks" occurring.
The Source Download is Not Sterile.
NSA provided the hardware in the middle of the night to Bill from the get go.
There is a solid allegiance there.
It is O.K. with me. But I would be careful with my Patents and Ideas. SAVVY?
reply to post by sean
Interesting read. I did follow the steps myself to verify this and it looks pretty legit. I do agree with the guy that is saying that this is rather in your face, but I guess that is the best way to do it.
Interesting read. I did follow the steps myself to verify this and it looks pretty legit. I do agree with the guy that is saying that this is rather in your face, but I guess that is the best way to do it.
ITT: A bunch of nerds waring it out over their programming/computer knowledge.
I use MacOSX, isn't that UNIX-based?
I use MacOSX, isn't that UNIX-based?
edit on 16-7-2013 by MystikMushroom because: (no reason given)
Originally posted by andy06shake
That svchost.exe can be a real resource hog sometimes, guess now we know why!
When I seen your title with the word RELOADED in it I thought it had something to do with the scene group. LoL
Actually, svchost.exe is sort of like a shell that is used by windows to run MANY different services.
That is why , on any given machine, you have can have 1-10+ instances of svchost.exe running at any given time.
To be more specific, specific host processes that windows uses, are run within svchost.exe. So basically, each different svchost.exe that is loaded, is a different process. You can consider svchost.exe the vehicle which the windows service/process uses to run.
edit on 7/16/2013 by
supermarket2012 because: added more info
reply to post by sean
This is so bizarre, that you seem to know a bit about computers with your CLI abilities, but don't know that the network service is a built-in windows account.
Really really weird. What's your angle?
This is so bizarre, that you seem to know a bit about computers with your CLI abilities, but don't know that the network service is a built-in windows account.
Really really weird. What's your angle?
reply to post by sean
The Only problem with dealing with stuff like this is the fact that you don't own that operating system at all. They, Microsoft went to a leased based operating system years ago...I do not know when they started this and cant remember if the DOS based systems were considered leased operating systems either .But I do know you don't own any current Microsoft operating system at all
The Only problem with dealing with stuff like this is the fact that you don't own that operating system at all. They, Microsoft went to a leased based operating system years ago...I do not know when they started this and cant remember if the DOS based systems were considered leased operating systems either .But I do know you don't own any current Microsoft operating system at all
Sadly, you have to trust MS to some extent.
If the cryptsvc essentially validates something as good or bad then
in the event that MS wanted to compromise your PC they could do it
easily by sending you an updated system file of their choosing.
If you had automatic updates ON then it would just install automatically.
The other hand the OS is being patched over and over constantly to
fix exploits and bugs. Turning these updates OFF would open your PC
to more proven malicious exploits.
As an example would you like some 15 year old kid enjoying a spanking
new xbox/pc ought using your stolen credit card details? I've seen things like this happen.
In one game I used to play the company were so bad that hackers
shared users credit card details by patching one of the game updates
on the game server and infecting thousands of machines with a key logger...
I remember one smart 15 year old kid was making thousands of $ from
his little hacking endeavors. The company running the game
were letting him dominate other players by giving him free godlike
items just to keep him happy so they could find out how he was doing it.
I don't see how you can win either way..
if you don't update you're _surely_ screwed, and if you do you give up liberties.
Limbo
www.bbc.co.uk...
If the cryptsvc essentially validates something as good or bad then
in the event that MS wanted to compromise your PC they could do it
easily by sending you an updated system file of their choosing.
If you had automatic updates ON then it would just install automatically.
The other hand the OS is being patched over and over constantly to
fix exploits and bugs. Turning these updates OFF would open your PC
to more proven malicious exploits.
As an example would you like some 15 year old kid enjoying a spanking
new xbox/pc ought using your stolen credit card details? I've seen things like this happen.
In one game I used to play the company were so bad that hackers
shared users credit card details by patching one of the game updates
on the game server and infecting thousands of machines with a key logger...
I remember one smart 15 year old kid was making thousands of $ from
his little hacking endeavors. The company running the game
were letting him dominate other players by giving him free godlike
items just to keep him happy so they could find out how he was doing it.
I don't see how you can win either way..
if you don't update you're _surely_ screwed, and if you do you give up liberties.
Limbo
www.bbc.co.uk...
reply to post by StumpDrummer
Different countries, different law. In Germany You do own the OS. Even if You have a notebook with Win7 preinstalled, You can extract the OS and sell it to someone else (and keep the notebook).
But anyway - the problem with the (possible) backdoor is a bit more complicated and even Wireshark (WinPcap) might not be able to show you the "real thing" behind the scenes.
Try to install Win7 into a virtual machine (under Linux), fire up EtherApe (as root) and watch the traffic comming from the virtual network card. It will be slightly diffrent from what Wireshark is showing you under Windows 7.
The problem is - with Windows Vista/Win7/Win8.x, Microsoft has introduced a new "user" (it is rather a security layer than a user) called "Trusted installer". This User (not to be seen under Users & Groups) is the REAL owner of the system. This user won't let you delete some files or folders, because even being the Administrator of the system, the trusted installer is some kind of Super-Admin or Root-Admin.
Of course, it is possible to take the rights away (some rights) from the trusted installer, but you can not fully clean the System and get really rid of it.
With Vista/Win7/Win8 MS has changed the kernel architecture, so you can not really use a reliable third-party firewall, because the OS will not let you go to really "deep". And the Windows Firewall is rather a joke.Something like the famous Sygate personal Firewall (Windows XP) will not work with Vista and above, most other FW-solutions can not go deep below the driver-level (which is what a real FW shoud do!). So Windows Vista and above can not be secured by the USER in the same way like it was possible with Windows XP.
Fast forward to Windows 8 & Windows 8.1.
Here you have even less freedom. Try to open a PDF-File if you are NOT logged in with a MS-live account. Not possible. Actualle NO App will work, if you are logged in with a LOCAL account. Why?
Why do you need a MS-Account (and a internet connection) if you want to read LOCALY stored PDF-Files? Why can I find the NAME of the PDF-File (if I open it with an MS-Account) in my network-log? Why does MS cares about what I am reading? Of course, you can install another PDF-Reader and stop using the PDF-App, but how many people are going to do this?
And even if you do it - welcome to Windows 8.1. You are looking for some files on your hard drive or on your local personal home-network? OK let BING help you searching. So, you are using a internet-based search enginge to scan and create an index of ALL of your files you have stored localy at home. And this index is connected to your personal MS-Profile. Part of this profile is kept local onto your harddrive and a full copy ist kept in the MS-Cloud.
So, by this, every 3-letter agency will instanly KNOW what you have stored onto your PC and what is on your network. Of course, I don't call this a "backdoor", but it is close enough :-)
Different countries, different law. In Germany You do own the OS. Even if You have a notebook with Win7 preinstalled, You can extract the OS and sell it to someone else (and keep the notebook).
But anyway - the problem with the (possible) backdoor is a bit more complicated and even Wireshark (WinPcap) might not be able to show you the "real thing" behind the scenes.
Try to install Win7 into a virtual machine (under Linux), fire up EtherApe (as root) and watch the traffic comming from the virtual network card. It will be slightly diffrent from what Wireshark is showing you under Windows 7.
The problem is - with Windows Vista/Win7/Win8.x, Microsoft has introduced a new "user" (it is rather a security layer than a user) called "Trusted installer". This User (not to be seen under Users & Groups) is the REAL owner of the system. This user won't let you delete some files or folders, because even being the Administrator of the system, the trusted installer is some kind of Super-Admin or Root-Admin.
Of course, it is possible to take the rights away (some rights) from the trusted installer, but you can not fully clean the System and get really rid of it.
With Vista/Win7/Win8 MS has changed the kernel architecture, so you can not really use a reliable third-party firewall, because the OS will not let you go to really "deep". And the Windows Firewall is rather a joke.Something like the famous Sygate personal Firewall (Windows XP) will not work with Vista and above, most other FW-solutions can not go deep below the driver-level (which is what a real FW shoud do!). So Windows Vista and above can not be secured by the USER in the same way like it was possible with Windows XP.
Fast forward to Windows 8 & Windows 8.1.
Here you have even less freedom. Try to open a PDF-File if you are NOT logged in with a MS-live account. Not possible. Actualle NO App will work, if you are logged in with a LOCAL account. Why?
Why do you need a MS-Account (and a internet connection) if you want to read LOCALY stored PDF-Files? Why can I find the NAME of the PDF-File (if I open it with an MS-Account) in my network-log? Why does MS cares about what I am reading? Of course, you can install another PDF-Reader and stop using the PDF-App, but how many people are going to do this?
And even if you do it - welcome to Windows 8.1. You are looking for some files on your hard drive or on your local personal home-network? OK let BING help you searching. So, you are using a internet-based search enginge to scan and create an index of ALL of your files you have stored localy at home. And this index is connected to your personal MS-Profile. Part of this profile is kept local onto your harddrive and a full copy ist kept in the MS-Cloud.
So, by this, every 3-letter agency will instanly KNOW what you have stored onto your PC and what is on your network. Of course, I don't call this a "backdoor", but it is close enough :-)
Originally posted by DAVID64
reply to post by SLAYER69
Just tried it. Everything is running fine so far. Restarted and when it came back up, I opened a browser and bounced around to a few sites. If anything, it seems a bit faster.
I've been going to ShieldsUP for about a year or so to check my computer and I always get this: THE EQUIPMENT AT THE TARGET IP ADDRESS
DID NOT RESPOND TO OUR UPnP PROBES!
(That's good news!)
edit on 15-7-2013 by DAVID64 because: (no reason given)
i love shields up dave gibons is the man, did you run the file sharing ports and common ports of the test.
see if you really have true stealth.
this is mine.
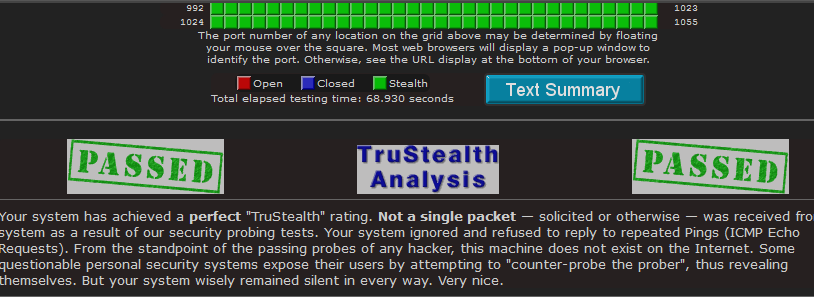
edit on 16-7-2013 by hounddoghowlie because: (no reason given)
I read an article recently (though can not find *sigh*) which talks about remote desktop software and the clever code that lets extremely small and
fast data packets to basically duplicate your PC screen over the internet and allow remote control. This is not news to any one, VNC has been around
for many many years and the are many many alternatives, all which work great.
The news that caught my eye was the part about moving to on chip, hardware RDC (remote desktop control) to be included on the motherboard of the computer. This means an RDC which works with any operating system, that you cannot remove or disable easily and that you wont actually know if its sending or receiving without watching your network traffic very very closely.
In the article it was more aimed at company's like HP to have an always available way to connect to a machine to fix it for the customer - I couldnt help but leap to the next step of forcing manufacturers to add this function to every computer sold.
Now prism has come to light, perhaps the chips are already there - the manufacturers sworn to secrecy like M$, google, yahoo etc with their forced compliance in regards to opening access up, against privacy agreements, not to with the user base.
Big Brother has never been more interested in watching you.
The news that caught my eye was the part about moving to on chip, hardware RDC (remote desktop control) to be included on the motherboard of the computer. This means an RDC which works with any operating system, that you cannot remove or disable easily and that you wont actually know if its sending or receiving without watching your network traffic very very closely.
In the article it was more aimed at company's like HP to have an always available way to connect to a machine to fix it for the customer - I couldnt help but leap to the next step of forcing manufacturers to add this function to every computer sold.
Now prism has come to light, perhaps the chips are already there - the manufacturers sworn to secrecy like M$, google, yahoo etc with their forced compliance in regards to opening access up, against privacy agreements, not to with the user base.
Big Brother has never been more interested in watching you.
edit on 16-7-2013 by Biigs because: (no reason given)
Originally posted by SonOfTheLawOfOne
Originally posted by sean
How is it way off base? I am just showing people that connections happen all the time with or without their knowledge. I am not saying this is a backdoor in this case, however and many viruses that do gain remote access use such ways. I know exactly what the service does, just like you said and what it's used for. You're preaching to the choir. You don't even find it odd in the slightest that a crypto service is connecting to a unencrypted server to send/receive data??? Not saying it's a back door but this connection should in the least be investigated for security risks. Who's to say I can't intercept and inject my own nefarious code??edit on 15-7-2013 by sean because: (no reason given)
There is no way to inject nefarious code into the crypto service call that goes out to Microsoft. You can see this by disassembling the DLL in Visual Studio or the Windows Debugger (Win Debug).
The service that is called is on a Microsoft secure server that only stores hashes of the assemblies that the crypto service checks. The stream being sent over the wire is a simple call that involves a callback to the DLL on your computer with a strongly typed interface between the two servers so that only hash keys can be returned for comparison, not code or SQL queries or injectable code. There is nothing that can be injected into this code because it only understands and accepts one type of reply, which is usually an MD5 one-way hash.
Like I said, if it could be hacked, it would have been, and if there was anyway whatsoever that a hacker could expose it and brag about it, it would have been done. If you want to know more about it, look at the code yourself in a decomposition tool like Win Dbg.
~Namaste
Yeah but what about the login itself and the password to the account you have no control over?? To me it just doesn't make sense to have an account for the service with a password and then login and send data through a normal http connection. A packet capture would reveal this password as plain text would it not? MD5 or no MD5 It still doesn't stop middle man packet capture for later use. Then we have the aging MD5 versus ever growing technology of super computer cpu/gpu clustering. One day these hashes and algorithms will be easily broken if not already.
It's the backdoors we can't find that worry me. Unless you do a hex dump of everything.
I would not be surprised at all if Microsoft works with law enforcement and alphabet agencies to hack into your computers. Sometimes they may have a good reason, like looking for child porn. But of course this technology can also be abused.
Big Brother is watching.
I would not be surprised at all if Microsoft works with law enforcement and alphabet agencies to hack into your computers. Sometimes they may have a good reason, like looking for child porn. But of course this technology can also be abused.
Big Brother is watching.
Originally posted by Evil_Santa
reply to post by sean
This is so bizarre, that you seem to know a bit about computers with your CLI abilities, but don't know that the network service is a built-in windows account.
Really really weird. What's your angle?
Heh when did I say this? Of course I know it's a built in service. I don't know maybe I said something that sounded like it. Some of these posts are really late and I am tired as hell. I was just posting my results of running a log against these types of services some as I stop/start them etc. Maybe I will check out the packets. Apparently no one else finds it odd for a service account that has a 15 character salted password connecting to a normal http web server.
Already had port 49175 blocked threw router along with # ton of others.
yup and if you want to see what process are running in your svchosts just use program called ProcessExplorer
Originally posted by supermarket2012
Originally posted by andy06shake
That svchost.exe can be a real resource hog sometimes, guess now we know why!
When I seen your title with the word RELOADED in it I thought it had something to do with the scene group. LoL
Actually, svchost.exe is sort of like a shell that is used by windows to run MANY different services.
That is why , on any given machine, you have can have 1-10+ instances of svchost.exe running at any given time.
To be more specific, specific host processes that windows uses, are run within svchost.exe. So basically, each different svchost.exe that is loaded, is a different process. You can consider svchost.exe the vehicle which the windows service/process uses to run.edit on 7/16/2013 by supermarket2012 because: added more info
edit on 16-7-2013 by 3xil3 because: (no reason given)
reply to post by Lysistrata
you can download "liveCDs" which let you burn a linux distro to a cd or dvd, or even make it into a bootable flash key. You boot to that (might have to go into your bios to select a boot device) and you can test out different linux distros without installing them. They boot from the media and run live, never touching your harddrive unless you specifically ask it to install itself, which only a few of them offer from the liveOS. This is about 1000% simpler than trying to run a virtual machine instance.
Some to try, for ease of migration from windows, are fedora core and ubuntu. There are subtle and not so subtle differences between linux and windows, but most of them now are fairly easy to migrate to.
don't disable that windows service, if you continue with windows, as you will end up crippling your system when it comes to ssl certificates as well as your windows file won't update leaving potential REAL security holes.
you can download "liveCDs" which let you burn a linux distro to a cd or dvd, or even make it into a bootable flash key. You boot to that (might have to go into your bios to select a boot device) and you can test out different linux distros without installing them. They boot from the media and run live, never touching your harddrive unless you specifically ask it to install itself, which only a few of them offer from the liveOS. This is about 1000% simpler than trying to run a virtual machine instance.
Some to try, for ease of migration from windows, are fedora core and ubuntu. There are subtle and not so subtle differences between linux and windows, but most of them now are fairly easy to migrate to.
don't disable that windows service, if you continue with windows, as you will end up crippling your system when it comes to ssl certificates as well as your windows file won't update leaving potential REAL security holes.
edit on 16-7-2013 by phishyblankwaters because: (no reason
given)
reply to post by sean
Well, you wouldn't want that account open, as a hacker could modify the system files / ssl certificates and have you pulling updates from a compromised source.
As well, I'd have to assume, and probably be right, that any files that do get pulled down are hashchecked in some manner, removing the need for a secure SSL connection.
And lastly, if there is an issue with your SSL store, this would be the means of fixing it, how exactly are you going to pull down updates if your ssl is fried?
Apparently no one else finds it odd for a service account that has a 15 character salted password connecting to a normal http web server.
Well, you wouldn't want that account open, as a hacker could modify the system files / ssl certificates and have you pulling updates from a compromised source.
As well, I'd have to assume, and probably be right, that any files that do get pulled down are hashchecked in some manner, removing the need for a secure SSL connection.
And lastly, if there is an issue with your SSL store, this would be the means of fixing it, how exactly are you going to pull down updates if your ssl is fried?
reply to post by MystikMushroom
Yup, but don't fool yourself thinking it's safe, because of iOS and it's market penetration over various devices, and the similarities between the versions, it's a target as of late, you aren't anymore secure with mac than you are windows, in fact, most windows users operate under the assumption their system is inherently insecure and take measures to secure it. A good portion of MAC users smile and repeat the mantra, we're safe on mac, and do nothing.
Linux isn't really anymore safe for bugs and possible exploits, but because of it's inability to really penetrate the market outside of android, which is basically linux, and the various differences in the versions and flavors, it's not a big target. It's built differently forcing a separation of the user from the ability to mess up the system, similar to what windows vista and 7 started doing. Many of the builds are open source and free, community supported, with tons and tons of code geeks inspecting code, changing it, fixing it, berating others for their sloppy work. Bugs are found faster, and patched faster, because a lot of the users as well as the people building it, are actively looking, not to exploit, but to fix.
I use MacOSX, isn't that UNIX-based?
Yup, but don't fool yourself thinking it's safe, because of iOS and it's market penetration over various devices, and the similarities between the versions, it's a target as of late, you aren't anymore secure with mac than you are windows, in fact, most windows users operate under the assumption their system is inherently insecure and take measures to secure it. A good portion of MAC users smile and repeat the mantra, we're safe on mac, and do nothing.
Linux isn't really anymore safe for bugs and possible exploits, but because of it's inability to really penetrate the market outside of android, which is basically linux, and the various differences in the versions and flavors, it's not a big target. It's built differently forcing a separation of the user from the ability to mess up the system, similar to what windows vista and 7 started doing. Many of the builds are open source and free, community supported, with tons and tons of code geeks inspecting code, changing it, fixing it, berating others for their sloppy work. Bugs are found faster, and patched faster, because a lot of the users as well as the people building it, are actively looking, not to exploit, but to fix.
reply to post by SLAYER69
Exactly Unix is the way to go. Unfortunately Ubuntu may or may not have been compromised.
Exactly Unix is the way to go. Unfortunately Ubuntu may or may not have been compromised.
So you found a Microsoft service on a Microsoft box that connects to the Microsoft website.
You've got to be kidding me !!
You've got to be kidding me !!
The only safe, unhackable, PC is one that isn't connected to the internet or a network in the 1st place.
There is no secure browsing of the internet, You cannot block yourself from being hacked unless you remove yourself from the loop. We have to keep remembering this, so if you think of your computer that is connected to the internet as a public whiteboard, then you cannot be taken by surprise.
Use a pc that isn't on a network if you don't want info to be seen or hacked.
Yes have two PCs, one connected to the internet that you use as your window to the world and another pc that isn't connected that you can be yourself on and never worry about. How does windows connect to their server if the PC isn't connected to the internet?
edit on 16-7-2013 by
Tranceopticalinclined because: (no reason given)
new topics
-
Weinstein's conviction overturned
Mainstream News: 21 minutes ago -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 1 hours ago -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 1 hours ago -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 2 hours ago -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 4 hours ago -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 6 hours ago -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 11 hours ago
top topics
-
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 15 hours ago, 11 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 16 hours ago, 6 flags -
Sunak spinning the sickness figures
Other Current Events: 16 hours ago, 5 flags -
Krystalnacht on today's most elite Universities?
Social Issues and Civil Unrest: 1 hours ago, 5 flags -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics: 1 hours ago, 4 flags -
Weinstein's conviction overturned
Mainstream News: 21 minutes ago, 4 flags -
Electrical tricks for saving money
Education and Media: 14 hours ago, 4 flags -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media: 4 hours ago, 2 flags -
Any one suspicious of fever promotions events, major investor Goldman Sachs card only.
The Gray Area: 6 hours ago, 2 flags -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People: 2 hours ago, 1 flags
active topics
-
British TV Presenter Refuses To Use Guest's Preferred Pronouns
Education and Media • 157 • : Annee -
University of Texas Instantly Shuts Down Anti Israel Protests
Education and Media • 97 • : marg6043 -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 667 • : daskakik -
Supreme Court Oral Arguments 4.25.2024 - Are PRESIDENTS IMMUNE From Later Being Prosecuted.
Above Politics • 11 • : network dude -
Weinstein's conviction overturned
Mainstream News • 7 • : underpass61 -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 144 • : underpass61 -
Sunak spinning the sickness figures
Other Current Events • 19 • : Freeborn -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 746 • : matafuchs -
Chris Christie Wishes Death Upon Trump and Ramaswamy
Politicians & People • 7 • : underpass61 -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 65 • : andy06shake
