It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
reply to post by MischeviousElf
I was not trying to give off an air of arrogance on my part. Like you said, Tor and deep web browsing is just the beginning of the true "deep web". And you are correct in saying that you need a laptop that was bought with cash in a no CCTV environment as well as net access with no ties or links to you. A laptop in which you have never logged into anything personal. All this is needed to be 100% safe on the internet.
But, face it. The guys on Menwith hill are humans just like we are. The Government is not the only band of engineers on the planet designing new software and cutting edge technologies. I have personally known some REAL computer Geniuses that could obliterate any of the known codes out there. You might say "So can the CIA or any other Govt agency". I say "Well, so can John doe".
Wherever there are oppressors or Tyrants that seek to control the web, there is someone smarter who goes around it all. I bet you anything that most of the guys and girls and Menwith hill were once "deep web" hackers that got caught and employed instead of incarcerated.
I was not trying to give off an air of arrogance on my part. Like you said, Tor and deep web browsing is just the beginning of the true "deep web". And you are correct in saying that you need a laptop that was bought with cash in a no CCTV environment as well as net access with no ties or links to you. A laptop in which you have never logged into anything personal. All this is needed to be 100% safe on the internet.
But, face it. The guys on Menwith hill are humans just like we are. The Government is not the only band of engineers on the planet designing new software and cutting edge technologies. I have personally known some REAL computer Geniuses that could obliterate any of the known codes out there. You might say "So can the CIA or any other Govt agency". I say "Well, so can John doe".
Wherever there are oppressors or Tyrants that seek to control the web, there is someone smarter who goes around it all. I bet you anything that most of the guys and girls and Menwith hill were once "deep web" hackers that got caught and employed instead of incarcerated.
I see last reply is a bit old and I don't like necroposting but I'll make an ecception beacause this is some really interesting stuff.
So, I don't have anything to contribute with that hasn't been already said here but I'd like to know if someone's got any "new" information about the topic...
So, I don't have anything to contribute with that hasn't been already said here but I'd like to know if someone's got any "new" information about the topic...
if someone want to hire a hacker, it's a possibility...
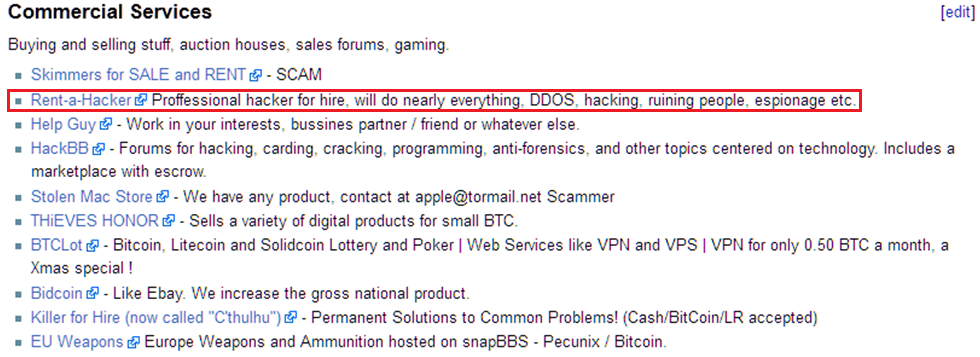
source 'the hidden wiki... bump or not...

source 'the hidden wiki... bump or not...
Okay here we go. What you have read in the past posts are both the truth and not the truth! It is not, and I repeat, not harm full in any way to enter
Tor or " the deep wep" if you want to call it that. 95% of you would not even know where to look in the first place for the gore or sick porn you
have run out of on the "normal" web.
And in the case that you do find some weird ass # DONT DOWNLOAD ANYTHING! The Tor Library is find to download from( just do it in the browser), but if you dont want your ass in trouble and stay save just dont download...!
I have seen it all in here but I also know my limits and so should you! Have fun and stay out of the freaky #..because what you will see in there would be enough to changes your view on humans
And in the case that you do find some weird ass # DONT DOWNLOAD ANYTHING! The Tor Library is find to download from( just do it in the browser), but if you dont want your ass in trouble and stay save just dont download...!
I have seen it all in here but I also know my limits and so should you! Have fun and stay out of the freaky #..because what you will see in there would be enough to changes your view on humans
reply to post by carlitomoore
this is full of child porn. Theres some good stuff to read but all the child porn on the onion. its best that people use w3m with this because it blocks images if in public places even know its a pain.
this is full of child porn. Theres some good stuff to read but all the child porn on the onion. its best that people use w3m with this because it blocks images if in public places even know its a pain.
I've skimmed though a good bit of this thread, to be honest I didn't even read half of it.
Let me first start by saying I'm not an "expert" or "authority" on anything, I basis everything on research or first hand experience.
I've spent a considerable amount of the "Deep Web", via Tor mostly. I've dabbled with I2P and did extensive research on FreeNet.
All of the above of are Anonymity Programs/Networks and Hidden Services. Technically the Deep Web is anything not in the DNS/Seach Engines.
Tor itself (as do many of the others) uses "Onion Routing", a concept developed and created by the US Naval Research Labs for citizens of Authoritarian States that restrict access control to the internet. By definition Tor is a "proxy".
Every system that is inside the Tor network has to "route" encrypted traffic, your IP and traffic is mixed in, layered and it is exactly as implied an "onion" of traffic. If you are probing around on the Tor and happen across CP you will NOT have anyone kicking down you door or arresting you, your IP is not logged.
Your IP is one of MILLIONS on the Tor Network, the traffic is encrypted and they're not going to go after a person who "accidentally" ran across some CP when there are entire rings of real pedophiles committing actual crimes.
As mentioned above Tor offers access to Hidden Services and a plethora of other places by using pseudo- Top Level Domain, non-mnemonic, 16-character alpha-semi-numeric hashes from a public key that is generated automatically when a Hidden Service is created.
That means the address is generated with the use of a public key for the pseudo-Top Level Domain, the hash is a 16 character set made up of any letter in the alphabet and with decimal digits beginning with 2 and ending with 7 (base32). Non-mnemonic means it isn't easy to remember.
Every time a page is shutdown and recreated (or mirrored) the address is changed to a new pseudo-Top Level Domain, non-mnemonic, 16-character alpha-semi-numeric hash.
I've been to a good many sites in Onionland, I've run into some Cheese Pizza (CP), but if you're not actively looking for it your chances of running isn't too big. As far as what's out there? Anything and everything, illegal arms, hit-men, CP, prostitutes, political dissidents, UFO groups, university science group projects, government and military web-space, information sites, hackers/crackers, software both legal and illegal, ect...
I've heard rumors and stories that after the Navy, the NSA and CIA used Tor to pass different types of data and information to Field Officers and each other. I've also heard that the Military has used some space for various projects and communications. I can not speak to the validity of any of theses rumors or stories, but it does entice the curious.
In regards to security. Running Tor in the open without additional security measures is dangerous, not because of government spooks or the CIA, but because of Crackers and Hackers looking to use your system as part of a Botnet, acquire Banking information, play pranks and all the other general thing one with nefarious intent on the internet would do.
Tor itself isn't a 'security" program, it is merely a supporting program to help hide and anonymize you and your traffic. Security requires an active part on the user.
The use of proxies such as Popilo, Privoxy, Squid, JonDoFox, ect... are encouraged. Firefox is probably the safest browser to partake this endeavor on, solely because of the plethora of security related add-ons at a users disposal.
In particular the Tor Button, FlagFox, Cookie Monster, AdBlock Plus, BetterPrivacy, HTTPS-Everywhere, PrivacyChoice TrackerBlocker, RefControl, User Agent Switcher, and others.
DO NOT access any private or personal information while using Tor, I2P, Freenet or any similar program. DO NOT access Facebook, Twitter, or any social media websites that contain personal information.
While these programs aren't illegal, it isn't a wise decision to openly take about them to others. It makes you a mark for anyone who's really nosy or works for a government agency that has nothing better to do than track US citizens.
There is no finite way to ensure complete anonymity on the internet, but a user can make it a behemoth of a task to tracked and or find any useable information.
I hope I've brought some insight and answered some questions.
Let me first start by saying I'm not an "expert" or "authority" on anything, I basis everything on research or first hand experience.
I've spent a considerable amount of the "Deep Web", via Tor mostly. I've dabbled with I2P and did extensive research on FreeNet.
All of the above of are Anonymity Programs/Networks and Hidden Services. Technically the Deep Web is anything not in the DNS/Seach Engines.
Tor itself (as do many of the others) uses "Onion Routing", a concept developed and created by the US Naval Research Labs for citizens of Authoritarian States that restrict access control to the internet. By definition Tor is a "proxy".
Every system that is inside the Tor network has to "route" encrypted traffic, your IP and traffic is mixed in, layered and it is exactly as implied an "onion" of traffic. If you are probing around on the Tor and happen across CP you will NOT have anyone kicking down you door or arresting you, your IP is not logged.
Your IP is one of MILLIONS on the Tor Network, the traffic is encrypted and they're not going to go after a person who "accidentally" ran across some CP when there are entire rings of real pedophiles committing actual crimes.
As mentioned above Tor offers access to Hidden Services and a plethora of other places by using pseudo- Top Level Domain, non-mnemonic, 16-character alpha-semi-numeric hashes from a public key that is generated automatically when a Hidden Service is created.
That means the address is generated with the use of a public key for the pseudo-Top Level Domain, the hash is a 16 character set made up of any letter in the alphabet and with decimal digits beginning with 2 and ending with 7 (base32). Non-mnemonic means it isn't easy to remember.
Every time a page is shutdown and recreated (or mirrored) the address is changed to a new pseudo-Top Level Domain, non-mnemonic, 16-character alpha-semi-numeric hash.
I've been to a good many sites in Onionland, I've run into some Cheese Pizza (CP), but if you're not actively looking for it your chances of running isn't too big. As far as what's out there? Anything and everything, illegal arms, hit-men, CP, prostitutes, political dissidents, UFO groups, university science group projects, government and military web-space, information sites, hackers/crackers, software both legal and illegal, ect...
I've heard rumors and stories that after the Navy, the NSA and CIA used Tor to pass different types of data and information to Field Officers and each other. I've also heard that the Military has used some space for various projects and communications. I can not speak to the validity of any of theses rumors or stories, but it does entice the curious.
In regards to security. Running Tor in the open without additional security measures is dangerous, not because of government spooks or the CIA, but because of Crackers and Hackers looking to use your system as part of a Botnet, acquire Banking information, play pranks and all the other general thing one with nefarious intent on the internet would do.
Tor itself isn't a 'security" program, it is merely a supporting program to help hide and anonymize you and your traffic. Security requires an active part on the user.
The use of proxies such as Popilo, Privoxy, Squid, JonDoFox, ect... are encouraged. Firefox is probably the safest browser to partake this endeavor on, solely because of the plethora of security related add-ons at a users disposal.
In particular the Tor Button, FlagFox, Cookie Monster, AdBlock Plus, BetterPrivacy, HTTPS-Everywhere, PrivacyChoice TrackerBlocker, RefControl, User Agent Switcher, and others.
DO NOT access any private or personal information while using Tor, I2P, Freenet or any similar program. DO NOT access Facebook, Twitter, or any social media websites that contain personal information.
While these programs aren't illegal, it isn't a wise decision to openly take about them to others. It makes you a mark for anyone who's really nosy or works for a government agency that has nothing better to do than track US citizens.
There is no finite way to ensure complete anonymity on the internet, but a user can make it a behemoth of a task to tracked and or find any useable information.
I hope I've brought some insight and answered some questions.
edit on 28-7-2012 by Weps21 because: (no reason given)
"in regards to security. Running Tor in the open without additional security measures is dangerous"
Coud you be more specific about that ? thanks for the insightful post .
Coud you be more specific about that ? thanks for the insightful post .
Let's just say they call it the "dark" web for a reason...keep your distance if you value your sanity and full-night's rests
Really.
Really.
reply to post by reassor
That is rubbish, tor is not like that. You have to set up the node part to become a "bouncer". It can be used for browsing purposes only. I have run a node for years now, back in NY I even ran an exit node, because I had good internet there. Canada internet sucks, so I just run a middle node.
That is rubbish, tor is not like that. You have to set up the node part to become a "bouncer". It can be used for browsing purposes only. I have run a node for years now, back in NY I even ran an exit node, because I had good internet there. Canada internet sucks, so I just run a middle node.
The deepweb is not all child porn.
Of course if you go looking, youll find it.
I have found contract killers/assassins, militia groupa, crime organizations, drug vendors, weapon vendors, images of murder, beheadings, rape, assault, gunshot wounds, and the list continues.
You really must be careful in the deep web. However it could be used to our benefit, but i suggest you leave it be. Its not something you toy with.
The governments can ban internet through DNS anyway.
Might as well use indexed web while we can.
Let me reitterate, do not tread lighty with the deep web. Many people grow interested, start searching, and then are horrified.
Of course if you go looking, youll find it.
I have found contract killers/assassins, militia groupa, crime organizations, drug vendors, weapon vendors, images of murder, beheadings, rape, assault, gunshot wounds, and the list continues.
You really must be careful in the deep web. However it could be used to our benefit, but i suggest you leave it be. Its not something you toy with.
The governments can ban internet through DNS anyway.
Might as well use indexed web while we can.
Let me reitterate, do not tread lighty with the deep web. Many people grow interested, start searching, and then are horrified.
edit on 19-11-2012 by Drazyhaze because: Spelling, additional info
reply to post by carlitomoore
You just discovered that. You never used Tor? Tor is huge and the deep web is nothing to be excited about.
You just discovered that. You never used Tor? Tor is huge and the deep web is nothing to be excited about.
There's Tor, I2p is pretty cool too. You can have your own site. The best thing I've been using for anonymity is TorBox. You should check it out.
And yes, there's child porn in the deep web. But if you don't look for it, you wont see it. So, just do your thing.
If you look for #ed up stuff there's no better place to find it, but if you don't, go ahead and give it a try, some interesting information lies in
the deepweb.
Just stay away from the blackhat forums, their watch-dogs are scum-bags and will give you head aches...
Just stay away from the blackhat forums, their watch-dogs are scum-bags and will give you head aches...
Nothing to add to this except great thread and I enjoyed reading all the replies.
Cheers
Cheers
new topics
-
God lived as a Devil Dog.
Short Stories: 2 minutes ago -
Happy St George's day you bigots!
Breaking Alternative News: 1 hours ago -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 2 hours ago -
Hate makes for strange bedfellows
US Political Madness: 4 hours ago -
Who guards the guards
US Political Madness: 7 hours ago -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 9 hours ago
top topics
-
Hate makes for strange bedfellows
US Political Madness: 4 hours ago, 14 flags -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs: 14 hours ago, 11 flags -
Who guards the guards
US Political Madness: 7 hours ago, 10 flags -
1980s Arcade
General Chit Chat: 16 hours ago, 7 flags -
Deadpool and Wolverine
Movies: 17 hours ago, 4 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 2 hours ago, 3 flags -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 9 hours ago, 2 flags -
Happy St George's day you bigots!
Breaking Alternative News: 1 hours ago, 2 flags -
God lived as a Devil Dog.
Short Stories: 2 minutes ago, 0 flags
active topics
-
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 719 • : xuenchen -
Happy St George's day you bigots!
Breaking Alternative News • 10 • : BedevereTheWise -
God lived as a Devil Dog.
Short Stories • 0 • : BrotherKinsMan -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 240 • : TzarChasm -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 615 • : daskakik -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs • 16 • : pianopraze -
1980s Arcade
General Chit Chat • 21 • : chris_stibrany -
Hate makes for strange bedfellows
US Political Madness • 30 • : nugget1 -
Who guards the guards
US Political Madness • 3 • : theatreboy -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat • 5 • : TzarChasm
