It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
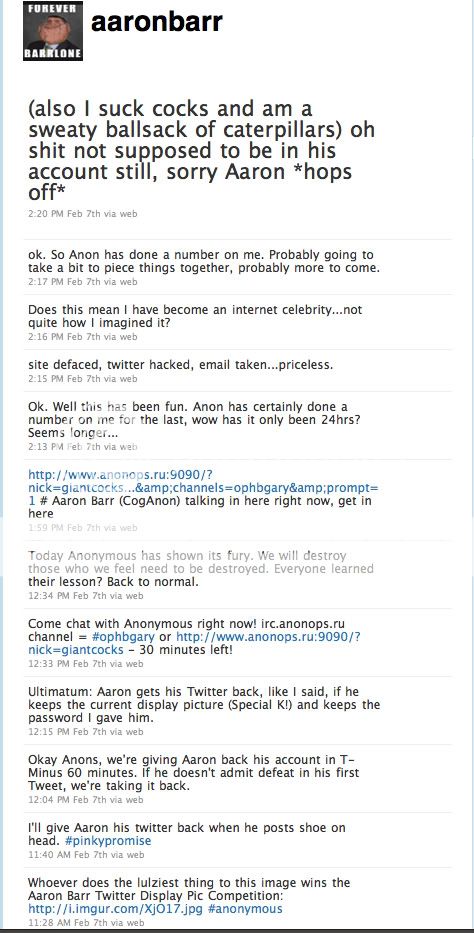
Anonymous speaks: the inside story of the HBGary hack
arstechnica.com
(visit the link for the full news article)
It has been an embarrassing week for security firm HBGary and its HBGary Federal offshoot. HBGary Federal CEO Aaron Barr thought he had unmasked the hacker hordes of Anonymous and was preparing to name and shame those responsible for co-ordinating the group's actions, including the denial-of-service attacks that hit MasterCard, Visa, and other perceived enemies of WikiLeaks late last year.
Interesting inside story how Anonymous hacked HBGary and how they got the passwords.
So there are clearly two lessons to be learned here. The first is that the standard advice is good advice. If all best practices had been followed then none of this would have happened. Even if the SQL injection error was still present, it wouldn't have caused the cascade of failures that followed.
The second lesson, however, is that the standard advice isn't good enough. Even recognized security experts who should know better won't follow it. What hope does that leave for the rest of us?
arstechnica.com
(visit the link for the full news article)
So there are clearly two lessons to be learned here. The first is that the standard advice is good advice. If all best practices had been followed then none of this would have happened. Even if the SQL injection error was still present, it wouldn't have caused the cascade of failures that followed.
The second lesson, however, is that the standard advice isn't good enough. Even recognized security experts who should know better won't follow it. What hope does that leave for the rest of us?
arstechnica.com
(visit the link for the full news article)
Originally posted by ckno1What hope does that leave for the rest of us?
In the capable hands of our brothers and sisters who care for us in ways we can't imagine and protect us from things we don't ever wish to imagine.
-m0r
The third lesson is; Karma is a bitch.
If they hadn't been engaged in some pretty unscrupulous shady business themselves (to wit; launching cyber-attacks to cover up for BoA potentially embarrassing corporate malfeasance by Wikileaks), then they wouldn't be in this mess now.
You can add HBGary to the number of evil corporate entities out there that exist to enrich the elitists and cover-up for their crimes.
If they hadn't been engaged in some pretty unscrupulous shady business themselves (to wit; launching cyber-attacks to cover up for BoA potentially embarrassing corporate malfeasance by Wikileaks), then they wouldn't be in this mess now.
You can add HBGary to the number of evil corporate entities out there that exist to enrich the elitists and cover-up for their crimes.
Originally posted by ckno1
So there are clearly two lessons to be learned here
You forgot the most important lesson you don't mess the Anonymous, you don't attack a beehive and expect no results. Leave them alone and they won't bother you indulge with them and you always loose.
This reminds me of the Tom Clancy book called Net Force.
However, a few things are different.
1) We have no true Net Policing Force yet.
2) So called computer security firms have been proven ineffective.
Maybe they are trying to spin this stuff to use as a legitimization or justification for forming a highly funded, wide jurisdiction Internet police force of some type. Who knows what plans they have.
Remember, "Never let a good crisis go to waste".
It is set in 2010 and charts the actions of Net Force: a special division of the FBI set up to combat increasing crime on the internet.
However, a few things are different.
1) We have no true Net Policing Force yet.
2) So called computer security firms have been proven ineffective.
Maybe they are trying to spin this stuff to use as a legitimization or justification for forming a highly funded, wide jurisdiction Internet police force of some type. Who knows what plans they have.
Remember, "Never let a good crisis go to waste".
Haha I had wanted to see what Kayla had said to Jussi.
Oh man, what a gimp
Oh man, what a gimp
Originally posted by Prince Of Darkness
Originally posted by ckno1
So there are clearly two lessons to be learned here
You forgot the most important lesson you don't mess the Anonymous, you don't attack a beehive and expect no results. Leave them alone and they won't bother you indulge with them and you always loose.
Oh that's not true... Give them a cause, people rally for them
Leave them alone, lulz are found wherever they like.. raids on facebook accounts just for pretty girls with dumb attitudes are lame.
And this is the bulk of anon. Sadly..
reply to post by muzzleflash
They did start a war on Wikileaks and created many military units with a soul purpose of attacking Wikileaks on all fronts. They attacked Wikileaks hard drives froze there bank accounts and planted moles. You know they will come up with a good name when there ready like the war on drugs, war on terror.... CERT teams doesn't have a ring to it. Although CERT stands for Computer Emergency Response Team.
www.au.af.mil...
They did start a war on Wikileaks and created many military units with a soul purpose of attacking Wikileaks on all fronts. They attacked Wikileaks hard drives froze there bank accounts and planted moles. You know they will come up with a good name when there ready like the war on drugs, war on terror.... CERT teams doesn't have a ring to it. Although CERT stands for Computer Emergency Response Team.
www.au.af.mil...
And this is the bulk of anon. Sadly..
They don't call it a cancer for nothing, lol. But keep in mind anon and 4chan are two different things, even if they overlap in many ways.
Originally posted by Blackmarketeer
And this is the bulk of anon. Sadly..
They don't call it a cancer for nothing, lol. But keep in mind anon and 4chan are two different things, even if they overlap in many ways.
I wonder how all those nihilistic channers like being lumped in with whoever these self-appointed "representatives" of Anon are. Anon is inherently chaotic and something tells me a sizable portion will not like marching behind whoever happens to jump to the front of the parade. What happens when the foot soldiers are told to aim the cannons somewhere they don't wish to? It's only a matter of time before Anon turns on itself in a paroxyism of autocannibalism. The consequences will never be the same.
article seems like a lie. i thought someone only had to call the system admin named jussi or something like that and ask for the password.
Originally posted by Blackmarketeer
And this is the bulk of anon. Sadly..
They don't call it a cancer for nothing, lol. But keep in mind anon and 4chan are two different things, even if they overlap in many ways.
True, I've always distinguished between the two, but I think publicity stabilises one over the other..
anon was 4chan before the media grabbed onto it... the name is derived from the boards ethos afterall..
edit on 16/2/2011 by badw0lf because: (no reason given)
Originally posted by silent thunder
Originally posted by Blackmarketeer
And this is the bulk of anon. Sadly..
They don't call it a cancer for nothing, lol. But keep in mind anon and 4chan are two different things, even if they overlap in many ways.
I wonder how all those nihilistic channers like being lumped in with whoever these self-appointed "representatives" of Anon are. Anon is inherently chaotic and something tells me a sizable portion will not like marching behind whoever happens to jump to the front of the parade. What happens when the foot soldiers are told to aim the cannons somewhere they don't wish to?
Simple. They'll sit back and do nothing. There is no directive. No reason for 99% of anon to do anything. No reason to even call them anon in the same regard that is being bandied about in the media.
you can have a million anon, all doing different things at opposition to each other, and it's still anon.
1 person is anon.
That so many rally for a cause, does not define anon.. it merely gives the media a spotlight area.
The guys in IRC are more or less a small group of people smothered in a barrage of fanbois.
Much like torrent sites, a core group, yet plenty of people who stick around for the aura.
If anyone has ever been on the EZTV irc channel, you know what I mean.. a channel with over 500 people, yet only a few dedicated to the distribution of torrents, who stay hard in good and bad times. Flies come and go.
It's only a matter of time before Anon turns on itself in a paroxyism of autocannibalism. The consequences will never be the same.
I doubt it, thats like saying people will disagree with each other, and it's already done...
The people who are educated enough in the technologies they desire to perform serious attacks, are rare and few. The rest are merely hanging on - following suit. Some are smart enough to not get caught, the rest just attack facebook. youtube channels, with comments and abuse.
Anon is the new in thing, you know... Everyone is doing it... /sarcasm
edit on 16/2/2011 by badw0lf because: (no reason given)
All I can say is "wow", they pretty-much f'd themselves ... I wouldn't be suprised for somebody to be able to do this to my hobby web-site, but I'm
not an "expert" security consulting firm doing work for the Fed's! Here's a few tid-bits ...
Why is it always the "Exec's"?
SSH open to the Internet? WTF? This ain't no hobby web-site!
The "social engineering" e-mail thread is a must read!
"two HBGary Federal employees, CEO Aaron Barr and COO Ted Vera, used passwords that were very simple; each was just six lower case letters and two numbers."
Why is it always the "Exec's"?
"Neither Aaron nor Ted followed best practices. Instead, they used the same password in a whole bunch of different places, including e-mail, Twitter accounts, and LinkedIn. For both men, the passwords allowed retrieval of e-mail. However, that was not all they revealed. Let's start with Ted's password first."
"Their system did not fall prey to some subtle, complex issue: it was broken into with basic, well-known techniques"
"One of these employees was Ted Vera, and his ssh password was identical to the cracked password he used in the CMS. This gave the hackers immediate access to the support machine."
SSH open to the Internet? WTF? This ain't no hobby web-site!
"Aaron's password yielded even more fruit. HBGary used Google Apps for its e-mail services, and for both Aaron and Ted, the password cracking provided access to their mail. But Aaron was no mere user of Google Apps: his account was also the administrator of the company's mail. With his higher access, he could reset the passwords of any mailbox and hence gain access to all the company's mail—not just his own. It's this capability that yielded access to Greg Hoglund's mail."
"And what was done with Greg's mail? A little bit of social engineering, that's what."
The "social engineering" e-mail thread is a must read!
edit on 2011-2-16 by EnhancedInterrogator because: Fixed some bad BBcode, etc.
Originally posted by EnhancedInterrogator
All I can say is "wow", they pretty-much f'd themselves ... I wouldn't be suprised for somebody to be able to do this to my hobby web-site, but I'm not a security consulting firm doing work for the Fed's! Here's a few tid-bits ...
"two HBGary Federal employees, CEO Aaron Barr and COO Ted Vera, used passwords that were very simple; each was just six lower case letters and two numbers."
Why is it always the "Exec's"?
Read the Emails, those two are new to the entire company, hired together from another firm in 09. They are chums.
I think they thought of themselves as holier than thou, when it comes to the company they joined.
They were NEW talent, touted as gods really, and look what they did rofl..
Just in case you missed it guys the emails are leaked through anonleaks.ru. My topic
www.abovetopsecret.com.... Unfortunately I haven't had
time to go over them yet.
reply to post by PsykoOps
Actually, I was just there looking at that too!
Damn, if my web-server weren't "on-shore", I'd be tempted to mirror.
...uh, I mean ... down with these anti-NWO Hooligans!
Actually, I was just there looking at that too!
Damn, if my web-server weren't "on-shore", I'd be tempted to mirror.
...uh, I mean ... down with these anti-NWO Hooligans!
I really hope they do not fire that "Jussi" guy as a scape-goat.
I can only say, that for the companies I've worked for, when you get a contact from an "Exec", all the so-called "rules" go out the f-ing door! You do pretty-darn-much whatever he ask's for!
From: Jussi
To: Greg
Subject: Re: need to ssh into rootkit
did you open something running on high port?
I can only say, that for the companies I've worked for, when you get a contact from an "Exec", all the so-called "rules" go out the f-ing door! You do pretty-darn-much whatever he ask's for!
edit on 2011-2-16 by EnhancedInterrogator because: Fixed formatting.
new topics
-
George Knapp AMA on DI
Area 51 and other Facilities: 2 hours ago -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 2 hours ago -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 4 hours ago -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 5 hours ago -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 7 hours ago -
Do we live in a simulation similar to The Matrix 1999?
ATS Skunk Works: 8 hours ago -
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 9 hours ago -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 10 hours ago -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 10 hours ago -
The good, the Bad and the Ugly!
Diseases and Pandemics: 11 hours ago
top topics
-
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 9 hours ago, 22 flags -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 10 hours ago, 18 flags -
George Knapp AMA on DI
Area 51 and other Facilities: 2 hours ago, 16 flags -
African "Newcomers" Tell NYC They Don't Like the Free Food or Shelter They've Been Given
Social Issues and Civil Unrest: 15 hours ago, 12 flags -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 10 hours ago, 7 flags -
Russia Flooding
Fragile Earth: 16 hours ago, 7 flags -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry: 14 hours ago, 6 flags -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 4 hours ago, 6 flags -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 7 hours ago, 5 flags -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 2 hours ago, 3 flags
active topics
-
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 117 • : KrustyKrab -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry • 164 • : Enduro -
George Knapp AMA on DI
Area 51 and other Facilities • 9 • : nerbot -
MULTIPLE SKYMASTER MESSAGES GOING OUT
World War Three • 28 • : Astrocometus -
Russia Flooding
Fragile Earth • 14 • : andy06shake -
Alabama Man Detonated Explosive Device Outside of the State Attorney General’s Office
Social Issues and Civil Unrest • 55 • : Vermilion -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs • 4 • : BernnieJGato -
911 emergency lines are DOWN across multiple states
Breaking Alternative News • 5 • : mysterioustranger -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 363 • : Annee -
The US Supreme Court Appears to Side With the January 6th 2021 Capitol Protestors.
Political Conspiracies • 47 • : EyeoftheHurricane