It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Originally posted by korean1818
I got the no-error password!
The password is very easy and normal...
The hint is in your discussions and wikidoc's movie.
I used below command-line.
[ openssl enc -d -aes256 -in insurance.aes256 > output.bin ]
The most passwords had occurred the error & error...
But one-password is passed!
So,I belive this word is correct passowrd.
But I can't analyse the below result file.
Who know the format of this file?
If your advice is correct, I'll open my password.
[Result File Header for WinXP]
E4 3F 17 CE 36 96 81 D9 D2 00 55 23 D8 D7 E5 62
C4 65 83 08 66 68 17 2D 41 65 40 59 96 BB 40 FC
EC A4 50 D7 3C 1E 2A AB C7 75 CC 66 60 E9 1F 68
4D 95 2D 4A 43 F1 74 1A 87 FB BB F6 18 20 E8 D8
C8 6B 6A 09 03 D8 E8 18 4B 43 08 47 DD 0F 58 2A
3E B9 FC 43 49 31 C4 C4 EE 12 4E AB A0 04 6E E9
97 15 BD A8 56 6C DF 97 65 EC B8 18 C1 42 AC BF
37 DA D0 91 5E 0F 6F EF DA 01 AC D1 B0 05 C3 11
A5 FA 38 A0 D6 6E 89 D7 21 C4 B5 45 14 9B C7 CA
35 16 9F F8 35 35 C1 D0 39 DB CA BC FC 77 B4 09
80 8F 12 10 2D 7C B8 33 43 1D 00 D9 A6 59 4E 9C
A6 CD FE B6 47 FE 1B 99 43 A4 91 FD 77 03 C6 9F
26 90 AD A8 5D D6 EB AC A6 A6 91 FB B6 66 DD 56
72 C8 F4 71 BF 19 35 A8 E8 C1 29 8C 76 8D 7C 8C
47 AE ED 62 A0 3B 23 9D 38 F4 29 BC E8 28 92 1C
E5 80 4F 2A 4A 04 17 A3 84 A7 CA CC 38 F0 4A 05
[Reversed File]
27 FC E8 73 6C 69 81 9B 4B 00 AA C4 1B EB A7 46
23 A6 C1 10 66 16 E8 B4 82 A6 02 9A 69 DD 02 3F
37 25 0A EB 3C 78 54 D5 E3 AE 33 66 06 97 F8 16
B2 A9 B4 52 C2 8F 2E 58 E1 DF DD 6F 18 04 17 1B
13 D6 56 90 C0 1B 17 18 D2 C2 10 E2 BB F0 1A 54
7C 9D 3F C2 92 8C 23 23 77 48 72 D5 05 20 76 97
E9 A8 BD 15 6A 36 FB E9 A6 37 1D 18 83 42 35 FD
EC 5B 0B 89 7A F0 F6 F7 5B 80 35 8B 0D A0 C3 88
A5 5F 1C 05 6B 76 91 EB 84 23 AD A2 28 D9 E3 53
AC 68 F9 1F AC AC 83 0B 9C DB 53 3D 3F EE 2D 90
01 F1 48 08 B4 3E 1D CC C2 B8 00 9B 65 9A 72 39
65 B3 7F 6D E2 7F D8 99 C2 25 89 BF EE C0 63 F9
64 09 B5 15 BA 6B D7 35 65 65 89 DF 6D 66 BB 6A
4E 13 2F 8E FD 98 AC 15 17 83 94 31 6E B1 3E 31
E2 75 B7 46 05 DC C4 B9 1C 2F 94 3D 17 14 49 38
A7 01 F2 54 52 20 E8 C5 21 E5 53 33 1C 0F 52 A0
But I can't analyse the below result file
OK....
One is an Old Testament Prayer (One Time Pad, in computer language it might be called a "decryption key").
The other block of data is the actual message (Password).
Typically you might
Subtract the one time pad data, from the decryption key data one digit at a time then convert the resultant value to a letter of the alphabet based on A=1, B =2, C = 3, etc.
Thats how we didi it back in the cold war days.
You could try that I guess.
Cheers!
I downloaded the insurance file from TPB, the genuine one, with over 2k seeders.
Then I Installed ESCrypt_v308_win32, right clicked the insurance file and opened. The window with the
Enter password:
Confirm password:
appears. In each one I inserted the following: B221399942apophis
I hit ok and a window appears saying Encrypting C:UsersxxxDestopinsurance.aes256.
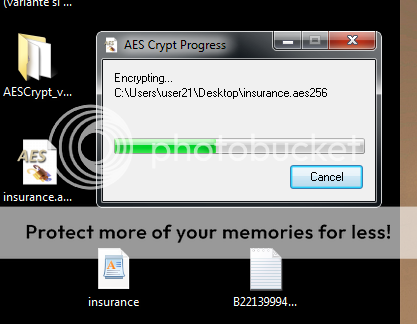
I get a new file called insurance.aes256, which if I try to open a new window appears this time with only a single space to be filled Enter password.
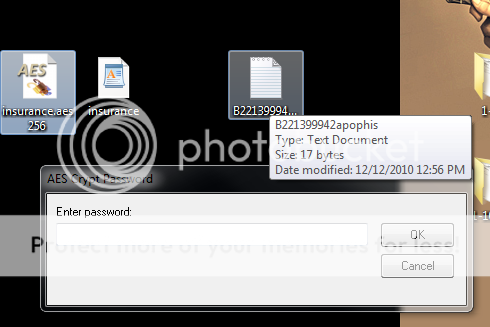
What I'm trying to point out is, has anyone tried tiping B221399942apophis instead of ß²²¹³99942apophis ?
Then I Installed ESCrypt_v308_win32, right clicked the insurance file and opened. The window with the
Enter password:
Confirm password:
appears. In each one I inserted the following: B221399942apophis
I hit ok and a window appears saying Encrypting C:UsersxxxDestopinsurance.aes256.

I get a new file called insurance.aes256, which if I try to open a new window appears this time with only a single space to be filled Enter password.

What I'm trying to point out is, has anyone tried tiping B221399942apophis instead of ß²²¹³99942apophis ?
edit on 12-12-2010 by ailailou
because: (no reason given)
edit on 12-12-2010 by ailailou because: (no reason given)
edit on 12-12-2010 by ailailou
because: (no reason given)
edit on 12-12-2010 by ailailou because: (no reason given)
edit on 12-12-2010 by ailailou
because: (no reason given)
reply to post by ailailou
I'm not to sure but i think you just put a password on the file. to decrypt you can change the extension of the file from '.aes256' to '.aes' and then right click and click on AES decrypt. then enter any password you want to try. if you happen to get the right one a new window should appear that says 'decrypting'. again i'm not 100% sure about this method.
Good luck
I'm not to sure but i think you just put a password on the file. to decrypt you can change the extension of the file from '.aes256' to '.aes' and then right click and click on AES decrypt. then enter any password you want to try. if you happen to get the right one a new window should appear that says 'decrypting'. again i'm not 100% sure about this method.
Good luck
Has anyone tried to find out what Assange's mother's maiden name is yet? or what his favourite pet was? When I forget my password these clues help
me. Perhaps Assange has done the same
LOving this thread S&F for all...
LOving this thread S&F for all...
reply to post by strangleholder1
i doubt it would be somthing so obvious but you never know.
Does anyone know if that password B221399942apophis from that youtube video was the real thing or not.
i doubt it would be somthing so obvious but you never know.
Does anyone know if that password B221399942apophis from that youtube video was the real thing or not.
reply to post by WalkinBlues
Not the real thing.
Video was a hoax.
It's somewhere in this thread.
Peace
Not the real thing.
Video was a hoax.
It's somewhere in this thread.
Peace
Originally posted by ianmoone1
One is an Old Testament Prayer (One Time Pad, in computer language it might be called a "decryption key").
....
You could try that I guess.
You're kidding, right? A OTP is nothing you can "try." If implemented correctly it is unbreakable. That being said, there's no way he used a OTP to encrypt this data; the pad would have to be at least as large as this file.
AES256 encryption is effective enough and is much simpler to work with.
Originally posted by ailailou
I downloaded the insurance file from TPB, the genuine one, with over 2k seeders.
Then I Installed ESCrypt_v308_win32, right clicked the insurance file and opened. The window with the
Enter password:
Confirm password:
appears. In each one I inserted the following: B221399942apophis
I hit ok and a window appears saying Encrypting C:UsersxxxDestopinsurance.aes256.
You realize it was encrypting the file again, right?
Guys, this file was NOT encrypted by the "AES Crypt" program. That utility produces a different header. That's why when some of you tried to decrypt it with "AES Crypt" you received errors about bad headers, etc.
The file was encrypted using "openssl enc". Stop wasting your time with "AES Crypt".
If Assange and WL are smart and I presume they are each separate doc in the insurance file will have separate encryptionM that way they can fire a
warning shot and give the insurance incrementally and still have some cards hidden. But equally distributed.
This has 129 flags? seriously?
And people are still discussing it, many of whom just joined today.
Come on everyone...
And people are still discussing it, many of whom just joined today.
Come on everyone...
allready posted in Introduction sorry mods !
but perhaps its related to this topic ?
Found a file inside the official wikileaks torrents at www.wikileaks.ch...
xyz.magnets.txt.torrent
contains :
xyz.magnets.txt
contains :
xyz.torrent: urn:btih:6FMVV3DRJGJ5AA2FZOJBNOYIDUYXVTGQ
xyz/x.gpg.torrent: urn:btih:WHSLRV6WMLV5JD22RFSIW63TEC5QAVWT
xyz/y-docs.gpg.torrent: urn:btih:EG563OLUKFG6FAHZQGMYKWNQUJUIOPWD
xyz/y.gpg.torrent: urn:btih:WT2DAKLWYNS6RMEXJAKI3V2ECIBEMHI6
xyz/z.gpg.torrent: urn:btih:7ZZA5QQ7WAGCVEPGPQH52UZ2KBZKPBIT
downloaded:
xyz/z.gpg.torrent: urn:btih:7ZZA5QQ7WAGCVEPGPQH52UZ2KBZKPBIT contains file : z.gpg
the file is something about mail crypto GnuPG and allows to encrypt and sign data and communication, features a versatile key.
I dont get all the torrents and i'm not able to open the z.gpg file with evolution....
what the heck is this ? and whats in the doc file ?
Anyone ?
but perhaps its related to this topic ?
Found a file inside the official wikileaks torrents at www.wikileaks.ch...
xyz.magnets.txt.torrent
contains :
xyz.magnets.txt
contains :
xyz.torrent: urn:btih:6FMVV3DRJGJ5AA2FZOJBNOYIDUYXVTGQ
xyz/x.gpg.torrent: urn:btih:WHSLRV6WMLV5JD22RFSIW63TEC5QAVWT
xyz/y-docs.gpg.torrent: urn:btih:EG563OLUKFG6FAHZQGMYKWNQUJUIOPWD
xyz/y.gpg.torrent: urn:btih:WT2DAKLWYNS6RMEXJAKI3V2ECIBEMHI6
xyz/z.gpg.torrent: urn:btih:7ZZA5QQ7WAGCVEPGPQH52UZ2KBZKPBIT
downloaded:
xyz/z.gpg.torrent: urn:btih:7ZZA5QQ7WAGCVEPGPQH52UZ2KBZKPBIT contains file : z.gpg
the file is something about mail crypto GnuPG and allows to encrypt and sign data and communication, features a versatile key.
I dont get all the torrents and i'm not able to open the z.gpg file with evolution....
what the heck is this ? and whats in the doc file ?
Anyone ?
Originally posted by ailailou
I downloaded the insurance file from TPB, the genuine one, with over 2k seeders.
Then I Installed ESCrypt_v308_win32, right clicked the insurance file and opened. The window with the
Enter password:
Confirm password:
appears. In each one I inserted the following: B221399942apophis
I hit ok and a window appears saying Encrypting C:UsersxxxDestopinsurance.aes256.
I get a new file called insurance.aes256, which if I try to open a new window appears this time with only a single space to be filled Enter password.
What I'm trying to point out is, has anyone tried tiping B221399942apophis instead of ß²²¹³99942apophis ?edit on 12-12-2010 by ailailou because: (no reason given)edit on 12-12-2010 by ailailou because: (no reason given)edit on 12-12-2010 by ailailou because: (no reason given)edit on 12-12-2010 by ailailou because: (no reason given)edit on 12-12-2010 by ailailou because: (no reason given)
Ya i;m using a HP Pavillion i7 x64 6Gb Ram and two 500 Mb HD
but download and install file AESCrypt_v308_x64
and i get the same thing as you
reply to post by Trillium
If I'm not mistaken, all you guys are doing is encrypting the file again, not decrypting the file.
On another note...:
I am new to ATS (past year or so lurker) and I can not believe this is still being discussed...its a damn hoax.
If I'm not mistaken, all you guys are doing is encrypting the file again, not decrypting the file.
On another note...:
I am new to ATS (past year or so lurker) and I can not believe this is still being discussed...its a damn hoax.
Originally posted by ianmoone1
One is an Old Testament Prayer (One Time Pad, in computer language it might be called a "decryption key").
The other block of data is the actual message (Password).
Typically you might
Subtract the one time pad data, from the decryption key data one digit at a time then convert the resultant value to a letter of the alphabet based on A=1, B =2, C = 3, etc.
Thanks for your advice..
I w'll try to analyse by your method(different ASCII table) and other methods..
And i'm mind the wikidos's comment on his youtube video(Password).
1) "This is for the people who already have the encryped docs" => we belive it's the [insurance.ase256]
2) "and a legand was sent out to use with password" => another keyword or description key ???
3) "This is only one part of the password." => ???
I'm not a native english speaker, So I didn't understand his last(third) comment.
what's means his comment?
1) Is the final password more long?
2) Is the total password is consist of two layer or step?
Anyway, It's interesting topic and I'll try...
edit on 12-12-2010 by korean1818 because: (no reason given)
Originally posted by korean1818
Originally posted by ianmoone1
One is an Old Testament Prayer (One Time Pad, in computer language it might be called a "decryption key").
The other block of data is the actual message (Password).
Typically you might
Subtract the one time pad data, from the decryption key data one digit at a time then convert the resultant value to a letter of the alphabet based on A=1, B =2, C = 3, etc.
Thanks for your advice..
I w'll try to analyse by your method(different ASCII table) and other methods..
And i'm mind the wikidos's comment on his youtube video(Password).
1) "This is for the people who already have the encryped docs" => we belive it's the [insurance.ase256]
2) "and a legand was sent out to use with password" => another keyword or description key ???
3) "This is only one part of the password." => ???
I'm not a native english speaker, So I didn't understand his last(third) comment.
what's means his comment?
1) Is the final password more long?
2) Is the total password is consist of two layer or step?
Anyway, It's interesting topic and I'll try...
edit on 12-12-2010 by korean1818 because: (no reason given)
Hope this helps a bit, basically, to decrypt this file, there are three routes:
1. Find a flaw in the encryption algorithm that allows you to decrypt the file without knowing the password (highly unlikely, almost 100% unlikely at this stage, even for people with highly advanced knowledge of encryption algorithms)
2. Find the password by try and fail method (it could be from found at first try to 200 years later or more, probably the later since the password won't be short and simple, there are unlimited number of combinations you can make right?)
3. Obtain the original password from the creator of the file (that is, wait for it to be released from an official source, steal it from them, etc)
Anything else is just a dead end, there are so much different possibilities that it is basically impossible for a single person to crack the encryption on this file. Also, by trying to manipulate the file itself nothing will be gained, you can't extract any information related to the password from the file, there is a need for external data not contained on that file (the password, key whatever), so trying to look into the file and manipulate it with standard encryption tools is just another dead end.
That's where we are, anything else beyond this comes from someone trying to show off so don't mind them.
Kai
Originally posted by IDKWTB
reply to post by Trillium
If I'm not mistaken, all you guys are doing is encrypting the file again, not decrypting the file.
On another note...:
I am new to ATS (past year or so lurker) and I can not believe this is still being discussed...its a damn hoax.
Yes most of us 99.99 % think that B2213999??????????????? is a Hoax
We would just like to firgure out why it trying to encrypte it not decryting it
would just like to firgure were we when wrong before the real password come out that
reply to post by gandhi
A thermonuclear bomb would be capable of destroying the asteroid. Although it is nearly impossible to make.
The page is set to say 0 views. The work of Julian, no doubt. Wonder why one of the tags is "Thermonuclear"? Any thoughts?
A thermonuclear bomb would be capable of destroying the asteroid. Although it is nearly impossible to make.
Hypothetically, if you cracked the password would you post it here.
Seriously, consider the implications involved....
First and foremost you would have killed a man electronically.
Can you live with that, i couldn't.
All of Julians leverage would have been removed.
Thus making him a matar, they would need to teach us that no one can stand up to them and live.
Second - You'll probably get a knock on the door......End Game.
Seriously, consider the implications involved....
First and foremost you would have killed a man electronically.
Can you live with that, i couldn't.
All of Julians leverage would have been removed.
Thus making him a matar, they would need to teach us that no one can stand up to them and live.
Second - You'll probably get a knock on the door......End Game.
reply to post by AGRESSION
Drive around find an access point post away.
Oh yeah and spoof your details.
Drive around find an access point post away.
Oh yeah and spoof your details.
edit on 13-12-2010 by aivlas because: (no reason given)
new topics
-
Electrical tricks for saving money
Education and Media: 2 hours ago -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 3 hours ago -
Sunak spinning the sickness figures
Other Current Events: 4 hours ago -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 4 hours ago -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 6 hours ago -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 7 hours ago -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 9 hours ago -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 11 hours ago
top topics
-
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 7 hours ago, 8 flags -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 14 hours ago, 8 flags -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 3 hours ago, 8 flags -
Former Labour minister Frank Field dies aged 81
People: 16 hours ago, 4 flags -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 11 hours ago, 3 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 4 hours ago, 3 flags -
Sunak spinning the sickness figures
Other Current Events: 4 hours ago, 3 flags -
Bobiverse
Fantasy & Science Fiction: 14 hours ago, 3 flags -
Electrical tricks for saving money
Education and Media: 2 hours ago, 3 flags -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 6 hours ago, 2 flags
active topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 127 • : RazorV66 -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest • 17 • : Xtrozero -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News • 29 • : WeMustCare -
VirginOfGrand says hello
Introductions • 6 • : TheMichiganSwampBuck -
How ageing is" immune deficiency"
Medical Issues & Conspiracies • 31 • : rickymouse -
Electrical tricks for saving money
Education and Media • 1 • : BeyondKnowledge3 -
Why to avoid TikTok
Education and Media • 18 • : burritocat -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 654 • : 777Vader -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 138 • : Xtrozero -
IDF Intel Chief Resigns Over Hamas attack
Middle East Issues • 44 • : BrotherKinsMan
