It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: CriticalStinker
They have chat logs of Manning asking Assange if he could crack a password, and Assange told him yes, they have rainbow tables to hack that type of password.
They have chat logs of Manning asking Assange if he could crack a password, and Assange told him yes, they have rainbow tables to hack that type of password.
a reply to: Xtrozero
From what I've read, Assange didn't do as much breaching as we are lead to believe.... We'll have to let the facts come out and I could be wrong.
As it stands I'm operating off of the assumption he did provide some assistance to Manning just like journalists have in the past as far as protecting them from being discovered.
Greenwald and Scahill still stand as an acceptable analogy in this scenario as they have done that with sources before.
When it comes to Government vs (real) journalists, I'm going to side with journalists 99% of the time.
Were they involved in gathering the information or did Snowden just provide it to them. As example, if they went to Snowden and asked him to gather for them then yes they are part of the crime. If Snowden came to them with the information then they are not part of the crime.
From what I've read, Assange didn't do as much breaching as we are lead to believe.... We'll have to let the facts come out and I could be wrong.
As it stands I'm operating off of the assumption he did provide some assistance to Manning just like journalists have in the past as far as protecting them from being discovered.
Greenwald and Scahill still stand as an acceptable analogy in this scenario as they have done that with sources before.
When it comes to Government vs (real) journalists, I'm going to side with journalists 99% of the time.
originally posted by: PokeyJoe
a reply to: CriticalStinker
They have chat logs of Manning asking Assange if he could crack a password, and Assange told him yes, they have rainbow tables to hack that type of password.
Could you provide me with that source? Not questioning you, I'm just curious.
And if that's the case, I'll certainly have to re-evaluate my position... Though more from how I approach the subject and not how I feel about it all....
I'm bias but at least I'm honest about that, and I always try to be
originally posted by: PokeyJoe
a reply to: CriticalStinker
They have chat logs of Manning asking Assange if he could crack a password, and Assange told him yes, they have rainbow tables to hack that type of password.
Makes it seem as though he had the password hashes since he mentioned rainbow table.
originally posted by: roadgravel
originally posted by: PokeyJoe
a reply to: CriticalStinker
They have chat logs of Manning asking Assange if he could crack a password, and Assange told him yes, they have rainbow tables to hack that type of password.
Makes it seem as though he had the password hashes since he mentioned rainbow table.
Quick question, I'm not as fluent in this realm of computing as I'd like to be, so I'll ask you....
The hashes they spoke of could have been to verify the file rather than a password, correct?
a reply to: roadgravel
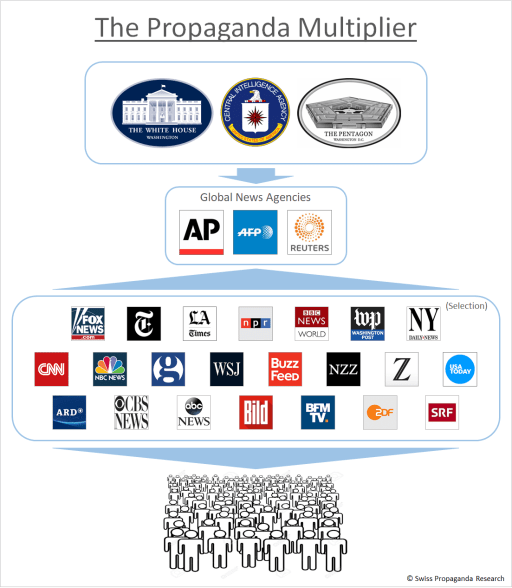
Most journalists today never leave their desks. They go to sources in the pic and create their narratives from there.

Most journalists today never leave their desks. They go to sources in the pic and create their narratives from there.
a reply to: CriticalStinker
If they are talking about the data Manning is to supply then I would believe the database he has access to has the user id and password hashes in them. This would explain the talk about help to login as a different user.
It a common method for finding passwords.
Manning wouldn't have anything to do with JA's insurance files, would he.
If they are talking about the data Manning is to supply then I would believe the database he has access to has the user id and password hashes in them. This would explain the talk about help to login as a different user.
It a common method for finding passwords.
Manning wouldn't have anything to do with JA's insurance files, would he.
edit on 4/12/2019 by roadgravel because: (no reason given)
a reply to: roadgravel
Gotchya.
I wasn't eluding to the insurance files, rather I was wondering if manning was giving hashes to files prior to sending them so JA could verify them.
To be honest though I didn't quite understand all their jargon in the conversation.
Gotchya.
I wasn't eluding to the insurance files, rather I was wondering if manning was giving hashes to files prior to sending them so JA could verify them.
To be honest though I didn't quite understand all their jargon in the conversation.
a reply to: CriticalStinker
A rainbow table is a list of hashes of words or phrases using a certain hash algorithm. If the hash for a password is known then if that hash value can be found in the table, the text for the hash is then known. reverse lookup.
Password verification normally uses an algorithm that takes the plain text the user enter and hashes it. That hash is compared to a stored hash and a match indicates the correct text (password) was entered. This method stores a hash instead of the password text. Often the hash is the output of the password and an extra bit of text to make it more unique and to help protect against rainbow tables use.
A rainbow table is a list of hashes of words or phrases using a certain hash algorithm. If the hash for a password is known then if that hash value can be found in the table, the text for the hash is then known. reverse lookup.
Password verification normally uses an algorithm that takes the plain text the user enter and hashes it. That hash is compared to a stored hash and a match indicates the correct text (password) was entered. This method stores a hash instead of the password text. Often the hash is the output of the password and an extra bit of text to make it more unique and to help protect against rainbow tables use.
originally posted by: CriticalStinker
a reply to: roadgravel
Gotchya.
I wasn't eluding to the insurance files, rather I was wondering if manning was giving hashes to files prior to sending them so JA could verify them.
To be honest though I didn't quite understand all their jargon in the conversation.
OK, I see what you meant. That may have been done also.
a reply to: roadgravel
Ahhhhh.
So this was why Facebook was under scrutiny recently for storing passwords plain text, they should have done hashes.
So the symbols equate a value? If you knew one password would you be able to see the hash equivalents so that you could figure other ones out?
Ahhhhh.
So this was why Facebook was under scrutiny recently for storing passwords plain text, they should have done hashes.
So the symbols equate a value? If you knew one password would you be able to see the hash equivalents so that you could figure other ones out?
a reply to: CriticalStinker
Good hashing is designed so the output is not predictable or reversible. The way to find the text is to use the same hashing algorithm and look at the output. The text cannot be known by inspecting the hash.
edit:
It would only identify the hash algorithm. It would not help with the other words other than knowing which hash algorithm to use.
Good hashing is designed so the output is not predictable or reversible. The way to find the text is to use the same hashing algorithm and look at the output. The text cannot be known by inspecting the hash.
edit:
If you knew one password would you be able to see the hash equivalents so that you could figure other ones out?
It would only identify the hash algorithm. It would not help with the other words other than knowing which hash algorithm to use.
edit on
4/12/2019 by roadgravel because: (no reason given)
a reply to: roadgravel
No. At least not necessarily. Withholding information for a timely disclosure is not lying. Using connotation and compliments is not lying. Calling Kim Jong Un "Little Rocket Man" was not a lie, and calling him his best buddy is not a lie. Both were simply comments designed to elicit the desired response from Kim.
I can say "I don't hang around person A much" or "I wouldn't go around someone as mean as person A" and say the exact same thing. The connotation is completely different, though, even though both statements may be true. That's what Trump and every other successful person does: they use words to elicit desired responses. How on earth is that considered lying?
This "Trump lies!" crap is really getting out of hand. As far as I have seen every single poster who tries to start with that nonsense ends up caught in more out and out lies than Trump ever has... so as soon as someone says it, I just figure they admitted to being a compulsive liar. It saves time.
TheRedneck
Yep, they do a lot of lying and less than ethical things.
No. At least not necessarily. Withholding information for a timely disclosure is not lying. Using connotation and compliments is not lying. Calling Kim Jong Un "Little Rocket Man" was not a lie, and calling him his best buddy is not a lie. Both were simply comments designed to elicit the desired response from Kim.
I can say "I don't hang around person A much" or "I wouldn't go around someone as mean as person A" and say the exact same thing. The connotation is completely different, though, even though both statements may be true. That's what Trump and every other successful person does: they use words to elicit desired responses. How on earth is that considered lying?
This "Trump lies!" crap is really getting out of hand. As far as I have seen every single poster who tries to start with that nonsense ends up caught in more out and out lies than Trump ever has... so as soon as someone says it, I just figure they admitted to being a compulsive liar. It saves time.
TheRedneck
a reply to: TheRedneck
How can anyone not see Trump saying something and then saying he didn't say it and saying something else later many times. Sometimes it might be he doesn't remember what he said and then just says something else and believe he didn't say anything before.
Either way, something is screwy.
My beef is that it make our president look poorly.
Believe what you want but so many people wouldn't bring it up if it wasn't happening.
Could be he just doens't understand the office.
How can anyone not see Trump saying something and then saying he didn't say it and saying something else later many times. Sometimes it might be he doesn't remember what he said and then just says something else and believe he didn't say anything before.
Either way, something is screwy.
My beef is that it make our president look poorly.
Believe what you want but so many people wouldn't bring it up if it wasn't happening.
Could be he just doens't understand the office.
a reply to: roadgravel
Or maybe he changed his mind? Sometimes people do that based on new information, you know.
Anyway, I would rather have a President who actually negotiates decent deals with other nations than someone who cares more about appearances than about the people.
In any case, what I referred to is simply not included in any reasonable person's definition of lying. If you want to cal it such and appear to be ignorant over it, that's your business.
TheRedneck
Or maybe he changed his mind? Sometimes people do that based on new information, you know.
Anyway, I would rather have a President who actually negotiates decent deals with other nations than someone who cares more about appearances than about the people.
In any case, what I referred to is simply not included in any reasonable person's definition of lying. If you want to cal it such and appear to be ignorant over it, that's your business.
TheRedneck
a reply to: roadgravel
5d4c62e20076bf374b2f2d0d9cbf847f
Might be interesting to see what resources people find?
Hashing goes way back to the 50's when we were more concerned about fixed field lengths.
It used to make short passwords a little less vulnerable to "dictionary" attacks.
There is a lot of redundancy, the MD5 hash of JulianAssange starts out dcdc20..
5d4c62e20076bf374b2f2d0d9cbf847f
Might be interesting to see what resources people find?
Hashing goes way back to the 50's when we were more concerned about fixed field lengths.
It used to make short passwords a little less vulnerable to "dictionary" attacks.
There is a lot of redundancy, the MD5 hash of JulianAssange starts out dcdc20..
edit on 12-4-2019 by Slichter because: (no reason given)
It used to make short passwords a little less vulnerable to "dictionary" attacks.
A hash doesn't change that. More unique character groups do.
edit on 4/12/2019 by roadgravel because: (no reason given)
new topics
-
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 3 hours ago -
Electrical tricks for saving money
Education and Media: 6 hours ago -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 7 hours ago -
Sunak spinning the sickness figures
Other Current Events: 8 hours ago -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 8 hours ago -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 10 hours ago -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 11 hours ago
top topics
-
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 7 hours ago, 9 flags -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 11 hours ago, 8 flags -
Electrical tricks for saving money
Education and Media: 6 hours ago, 4 flags -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 15 hours ago, 3 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 8 hours ago, 3 flags -
Sunak spinning the sickness figures
Other Current Events: 8 hours ago, 3 flags -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 10 hours ago, 2 flags -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 13 hours ago, 1 flags -
God's Righteousness is Greater than Our Wrath
Religion, Faith, And Theology: 3 hours ago, 0 flags
active topics
-
Mood Music Part VI
Music • 3101 • : ThatSmellsStrange -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News • 41 • : ThatSmellsStrange -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three • 32 • : DaRAGE -
New whistleblower Jason Sands speaks on Twitter Spaces last night.
Aliens and UFOs • 55 • : baablacksheep1 -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest • 20 • : Asher47 -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues • 12 • : Asher47 -
Electrical tricks for saving money
Education and Media • 4 • : Lumenari -
DONALD J. TRUMP - 2024 Candidate for President - His Communications to Americans and the World.
2024 Elections • 514 • : WeMustCare -
The Acronym Game .. Pt.3
General Chit Chat • 7744 • : bally001 -
Truth Social goes public, be careful not to lose your money
Mainstream News • 128 • : Astyanax
