It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: efabian
a reply to: Vasa Croe
A valve within the appliance will blow so the pipes and the appliance it-self would not get damaged.
When these valves blow, all the gas would freely disperse through the house. (Imagine a pressure cooker valve)
There isn't enough pressure in a nat-gas line to blow a gas valve in a household appliance.
a reply to: Vasa Croe
Typical operating pressure on gas lines is very low. Running into a household the pressure should be around .25psi, and at a main, depending on how much it is supplying you might see 30-60 psi. Very low pressure.
Any gas lines guys know the pressures for all the pipes and the valves used and if a high pressure pop could feasibly burst any of these things?
Typical operating pressure on gas lines is very low. Running into a household the pressure should be around .25psi, and at a main, depending on how much it is supplying you might see 30-60 psi. Very low pressure.
I use SCADA at work. We can activate overrides if we need to manually control something but there are interlocks built in at the local level with
mechanical protection built in that require physical intervention to adjust. Sure you could mess with a process if you were able to break in but most
systems are constantly monitored. Just my view as a SCADA user.
originally posted by: Vasa Croe
originally posted by: Guyfriday
originally posted by: DBCowboy
Now I'm no smart guy. . . but could those "smart meters" be hackable?
There's a joke in there I know it.
Here is a quick looking loo on google:
IoT agenda
Computer World
Sorry for the fear of it all, but it's a reality we live in.
I'm not sure if they could regulate flow from the smart meter and also no sure if they could hack multiple at the same time.
I am wondering though....these explosions all seem to have happened in homes/businesses. That would make me think more that this was a hack to push gas into the open valves, or opening the valves themselves. Wouldn't a leak have blown somewhere on the ground as well? Not just the homes?
There should be manual overpressure popoff valves on the gas lines to prevent something like this. I would think mains would be more prone to failure from overpressure than past the gas meter at a home or business. As far as smart meters getting hacked yeah you could use it to monitor the power but you wouldn’t be able to throttle or increase the voltage worst case scenario they could turn off your power and that’s it. I suppose if you were using IP over power networking they could develop an algorithm to spy on network activity and gain acsess that way but that’s not common these days.
a reply to: Vasa CroeIt may be that the Russians have finally got around to seaking retribution for this
www.zdnet.com... Seriously though the ability to increase pressure and cause devastation by
hacking or hidden software command is very real
originally posted by: astra001uk
a reply to: Vasa CroeIt may be that the Russians have finally got around to seaking retribution for this www.zdnet.com... Seriously though the ability to increase pressure and cause devastation by hacking or hidden software command is very real
I was actually thinking about that incident....
Were this a few years ago, I wouldn't think an intentional hack was on the table.
I wouldn't point the finger elsewhere though. We might be Tony Starking.
If we made these types of software flaws, I could just as easily believe we are being bitten by our own dog.
I wouldn't point the finger elsewhere though. We might be Tony Starking.
If we made these types of software flaws, I could just as easily believe we are being bitten by our own dog.
edit on 14-9-2018 by Archivalist
because: Grammatical tactical sabbatical
originally posted by: RexKramerPRT
I use SCADA at work. We can activate overrides if we need to manually control something but there are interlocks built in at the local level with mechanical protection built in that require physical intervention to adjust. Sure you could mess with a process if you were able to break in but most systems are constantly monitored. Just my view as a SCADA user.
But, wouldn't it be impossible to install physical interlocks on a distributed system. The distributed system would have to rely on software to prevent improper configuration.
Once bad actors have access to overall system control, they can probably disguise error signals and provide erroneous data display in order to hide their nefarious activities.
In those cases where direct worker intervention is necessary to reconfigure a device, perhaps a bad actor could create a set of fake work orders. A series of well planned misconfigurations, implemented by the workers themselves, could put the distributed system in an unsafe state.
Thanks for your insights.
-dex
a reply to: DexterRiley
That's the mechanical protection comes in. Think burst disk on a pressurised vessel or a valve that needs someone to get to tools out to alter to prevent it operating beyond a certain range.
Possible I guess but implies they have an intimate knowledge of current operations.
I can only talk about my own experience but our SCADA does the overall big picture stuff but individual components are all designed and built to operate independently, each with its own PLC/controller and fail safe, that don't require SCADA. I'm only a user but have had instances of SCADA crashing or needing to be taken offline for one reason or another. It just means more physical, eyes on checks.
But, wouldn't it be impossible to install physical interlocks on a distributed system. The distributed system would have to rely on software to prevent improper configuration.
That's the mechanical protection comes in. Think burst disk on a pressurised vessel or a valve that needs someone to get to tools out to alter to prevent it operating beyond a certain range.
Once bad actors have access to overall system control, they can probably disguise error signals and provide erroneous data display in order to hide their nefarious activities.
Possible I guess but implies they have an intimate knowledge of current operations.
I can only talk about my own experience but our SCADA does the overall big picture stuff but individual components are all designed and built to operate independently, each with its own PLC/controller and fail safe, that don't require SCADA. I'm only a user but have had instances of SCADA crashing or needing to be taken offline for one reason or another. It just means more physical, eyes on checks.
edit on 14/9/2018 by
RexKramerPRT because: (no reason given)
Some interesting information about Natural Gas Delivery System.
Click the following image for a full size version.
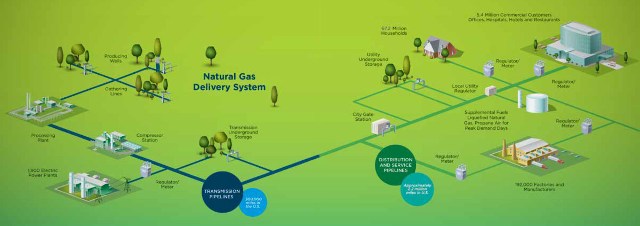
The American Gas Association also provides some additional descriptions about the various components used: How Does the Natural Gas Delivery System Work?
This PDF provides some interesting engineering specs for gas distributions systems. One thing to notice is the requirement for pressure regulation and relief devices throughout the delivery system.
This PDF from the Pipeline Safety Trust provides a lively and colorful presentation of the components of a Natural Gas delivery system.
A few interesting factoids that I recall from memory:
1. Gas meters do have internal regulators. The distribution line side may be up to 20 PSI. But the house side of the meter is generally on the order of 1/2 PSI.
2. Current NG delivery system regulations require pressure regulation and relief devices throughout the delivery system, limiting the various segments to their maximum designed operating pressure.
3. There are quite a few remotely controlled and/or remotely monitored components in the system. Pumping stations are almost completely automated.
4. In modern delivery systems the SCADA infrastructure is used to monitor flow rates and pressures in the various segments of the system. Pressures and flow rates can be controlled automatically in order to quickly respond to changes in customer demand.
5. If a high level of customer demand is expected, the pressure in the main distribution system can be increased. Essentially this allows the gas company to use their piping system for temporary local NG storage.
6. The customer distribution grid is fed as a loop. This allows the gas company to work on part of their distribution infrastructure without turning off the gas to the customer. The loop also helps to maintain gas pressure in the grid by feeding it from both ends.[Unfortunately this means that it's more difficult to isolate segments due to the need to shut off multiple valves.]
7. When the NG is extracted from the ground, processing plants remove impurities such as water, carbon dioxide and sulfur. These impurities may corrode the pipeline.[I wonder what are the consequences of having these impurities reintroduced in the downstream delivery segments? How quickly can these contaminants induce dangerous pipeline failure?]
8. While the pressure to the customer is on the order of 1/2 PSI, the major segments of the pipeline may be as high as 1500 PSI.
****************************
I would guess that this suburban Boston gas delivery system is quite dated. And that this aging infrastructure probably doesn't have all of the safety features in place that are required by modern building codes. And, if the extant safety systems are not periodically tested, it's possible they may not work as intended. Such conditions could easily lead to the catastrophic failure we witnessed.
-dex
Click the following image for a full size version.

The American Gas Association also provides some additional descriptions about the various components used: How Does the Natural Gas Delivery System Work?
This PDF provides some interesting engineering specs for gas distributions systems. One thing to notice is the requirement for pressure regulation and relief devices throughout the delivery system.
This PDF from the Pipeline Safety Trust provides a lively and colorful presentation of the components of a Natural Gas delivery system.
A few interesting factoids that I recall from memory:
1. Gas meters do have internal regulators. The distribution line side may be up to 20 PSI. But the house side of the meter is generally on the order of 1/2 PSI.
2. Current NG delivery system regulations require pressure regulation and relief devices throughout the delivery system, limiting the various segments to their maximum designed operating pressure.
3. There are quite a few remotely controlled and/or remotely monitored components in the system. Pumping stations are almost completely automated.
4. In modern delivery systems the SCADA infrastructure is used to monitor flow rates and pressures in the various segments of the system. Pressures and flow rates can be controlled automatically in order to quickly respond to changes in customer demand.
5. If a high level of customer demand is expected, the pressure in the main distribution system can be increased. Essentially this allows the gas company to use their piping system for temporary local NG storage.
6. The customer distribution grid is fed as a loop. This allows the gas company to work on part of their distribution infrastructure without turning off the gas to the customer. The loop also helps to maintain gas pressure in the grid by feeding it from both ends.[Unfortunately this means that it's more difficult to isolate segments due to the need to shut off multiple valves.]
7. When the NG is extracted from the ground, processing plants remove impurities such as water, carbon dioxide and sulfur. These impurities may corrode the pipeline.[I wonder what are the consequences of having these impurities reintroduced in the downstream delivery segments? How quickly can these contaminants induce dangerous pipeline failure?]
8. While the pressure to the customer is on the order of 1/2 PSI, the major segments of the pipeline may be as high as 1500 PSI.
****************************
I would guess that this suburban Boston gas delivery system is quite dated. And that this aging infrastructure probably doesn't have all of the safety features in place that are required by modern building codes. And, if the extant safety systems are not periodically tested, it's possible they may not work as intended. Such conditions could easily lead to the catastrophic failure we witnessed.
-dex
a reply to: RexKramerPRT
Thanks for the reply.
If memory serves, the Israelis were able to hack the Iranian SCADA systems because they had access to the software product they were using. Which was a commercial product used worldwide. Using that knowledge, the Israelis were able to reprogram the Iranian centrifuges to damage themselves.
I believe that a nation-state supported hacker could have in-depth knowledge of the products in use by the vendor. And, depending on the level of system access gained, could infer implementation details from examination of configuration artifacts.
I don't know... It certainly would not be a trivial effort to attempt to hack and control a system like this. However, some have criticized the US government of not thinking far enough outside of the box in relationship to the uniqueness of the 911 attacks. I think it's always beneficial to examine these events from multiple angles.
Regards,
-dex
Thanks for the reply.
Possible I guess but implies they have an intimate knowledge of current operations.
If memory serves, the Israelis were able to hack the Iranian SCADA systems because they had access to the software product they were using. Which was a commercial product used worldwide. Using that knowledge, the Israelis were able to reprogram the Iranian centrifuges to damage themselves.
I believe that a nation-state supported hacker could have in-depth knowledge of the products in use by the vendor. And, depending on the level of system access gained, could infer implementation details from examination of configuration artifacts.
I don't know... It certainly would not be a trivial effort to attempt to hack and control a system like this. However, some have criticized the US government of not thinking far enough outside of the box in relationship to the uniqueness of the 911 attacks. I think it's always beneficial to examine these events from multiple angles.
Regards,
-dex
a reply to: DexterRiley
I agree that nothing is impossible but there are skilled and motivated people on both sides.
I agree that nothing is impossible but there are skilled and motivated people on both sides.
a reply to: toysforadults
File exchanges, software updates, OS patches, USB drives, insider threat, and user error are all much more likely causes than real time "hacking" that compromises a system. Once you air gap the system all of these file transfers and updates still need to be done, only now you rely on a human delivering them on some sort of media, contractors have to login, users need data and configuration files.
The air gap gives a false sense of security and leads to the degradation in that network over time as it most likely won't be maintained properly, as I said before if you air gap your system you are contributing to the problem. the DCS should sit behind it's own firewall within the corporate network to explicitly control both inbound and outbound traffic to the network and also be maintained with proper patching and antivirus.
Just to be clear having the DCS or SCADA system connected to the corporate network does not mean the operator has access the internet from the HMI, in fact that is strictly prohibited on our systems although some companies do allow it.
The next most likely entry point is removable media, the USB stick that johnny operator brought from home with pictures of his kids and dog on it that was already infected before it showed up at the facility.
Third most likely is email clients, again we don't permit outlook on the HMI systems nor access to the internet from within the DCS control network.
The remainder of likely methods to exploit are largely blocked with proper patching and up to date anti-virus.
File exchanges, software updates, OS patches, USB drives, insider threat, and user error are all much more likely causes than real time "hacking" that compromises a system. Once you air gap the system all of these file transfers and updates still need to be done, only now you rely on a human delivering them on some sort of media, contractors have to login, users need data and configuration files.
The air gap gives a false sense of security and leads to the degradation in that network over time as it most likely won't be maintained properly, as I said before if you air gap your system you are contributing to the problem. the DCS should sit behind it's own firewall within the corporate network to explicitly control both inbound and outbound traffic to the network and also be maintained with proper patching and antivirus.
Just to be clear having the DCS or SCADA system connected to the corporate network does not mean the operator has access the internet from the HMI, in fact that is strictly prohibited on our systems although some companies do allow it.
The next most likely entry point is removable media, the USB stick that johnny operator brought from home with pictures of his kids and dog on it that was already infected before it showed up at the facility.
Third most likely is email clients, again we don't permit outlook on the HMI systems nor access to the internet from within the DCS control network.
The remainder of likely methods to exploit are largely blocked with proper patching and up to date anti-virus.
originally posted by: RexKramerPRT
a reply to: DexterRiley
I agree that nothing is impossible but there are skilled and motivated people on both sides.
Hopefully the corporate IT security practices are up to the challenge. Unfortunately, we see that many large companies are ignoring sound security practices. And they have had millions of records of sensitive user data stolen.
While I would hope that crucial public utilities providers are being extra vigilant in their IT security practices, I have little reason to believe that is the case.
In the end I believe that the cause of this tragedy will be much more mundane than this speculation about hacking. At least that's what we'll be told.
-dex
a reply to: Vasa Croe
Very doubtful. If the pressure was jacked up and regulators and blow off valves disabled, things like water heaters and furnaces with a pilot light on all the time would burn the gas as if the appliance was turned on. Explosions come from a whole room or house being filled with gas and then hit by an ignition source.
a reply to: toysforadults
I have heard of an attack over an air gap. Essentially two machines were sending data back and forth using a type of 'Morse code' using their speakers and microphones on a frequency inaudible to humans. It is possible.
Very doubtful. If the pressure was jacked up and regulators and blow off valves disabled, things like water heaters and furnaces with a pilot light on all the time would burn the gas as if the appliance was turned on. Explosions come from a whole room or house being filled with gas and then hit by an ignition source.
a reply to: toysforadults
I have heard of an attack over an air gap. Essentially two machines were sending data back and forth using a type of 'Morse code' using their speakers and microphones on a frequency inaudible to humans. It is possible.
originally posted by: SouthernForkway26
a reply to: Vasa Croe
Very doubtful. If the pressure was jacked up and regulators and blow off valves disabled, things like water heaters and furnaces with a pilot light on all the time would burn the gas as if the appliance was turned on. Explosions come from a whole room or house being filled with gas and then hit by an ignition source.
a reply to: toysforadults
I have heard of an attack over an air gap. Essentially two machines were sending data back and forth using a type of 'Morse code' using their speakers and microphones on a frequency inaudible to humans. It is possible.
A lot of it also comes from things like thumb drives being plugged across the air gap, but there are fancier methods.
new topics
-
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 58 minutes ago -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 2 hours ago -
God lived as a Devil Dog.
Short Stories: 2 hours ago -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 3 hours ago -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 4 hours ago -
Hate makes for strange bedfellows
US Political Madness: 6 hours ago -
Who guards the guards
US Political Madness: 9 hours ago -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 11 hours ago
top topics
-
Hate makes for strange bedfellows
US Political Madness: 6 hours ago, 14 flags -
Who guards the guards
US Political Madness: 9 hours ago, 13 flags -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs: 16 hours ago, 11 flags -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 3 hours ago, 7 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 4 hours ago, 5 flags -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 58 minutes ago, 3 flags -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 11 hours ago, 2 flags -
God lived as a Devil Dog.
Short Stories: 2 hours ago, 2 flags -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 2 hours ago, 2 flags
active topics
-
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest • 35 • : BedevereTheWise -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 119 • : FlyersFan -
Europe declares war on Russia?
World War Three • 65 • : Freeborn -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 731 • : Threadbarer -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 248 • : FlyersFan -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 4 • : chiefsmom -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 626 • : cherokeetroy -
The Superstition of Full Moons Filling Hospitals Turns Out To Be True!
Medical Issues & Conspiracies • 19 • : FloridaManMatty -
Iranian Regime Escalates Hiijab Mandate Through Sexual Violence and Beatings of Women
Mainstream News • 166 • : purplemer -
They Killed Dr. Who for Good
Rant • 67 • : grey580
