It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: Mandroid7
a reply to: Wardaddy454
Christ, I can do that in 2 min by running my proxy through Russia, then trash talk from there, like a basement dwelling fat kid from 4chan.
All completely traceable . Instantly .
There is one major thing you cannot hide....
And , this was about the malware used. Not going through a proxy .
a reply to: Gothmog
With the help of the ISP yes it is traceable even with a proxy you still have to go through the ISP
Thats why I'm saying it would be more likely accessed from a stolen laptop in another country
With the help of the ISP yes it is traceable even with a proxy you still have to go through the ISP
Thats why I'm saying it would be more likely accessed from a stolen laptop in another country
edit on 13-7-2018 by toysforadults because: (no
reason given)
a reply to: toysforadults
Didn't Secretary of State Clinton forget and leave her laptop and classified documents a Russian hotel room about 4 years ago?
Didn't Secretary of State Clinton forget and leave her laptop and classified documents a Russian hotel room about 4 years ago?
edit on
7/13/2018 by carewemust because: (no reason given)
originally posted by: network dude
originally posted by: theantediluvian
a reply to: network dude
Your handle is literally "network dude" so I assume you've got access to a network. Let's assume gigabit ethernet with normal-low utilization and two run-of-the-mill Windows desktops with 5400 rpm drives. That seems like a safe bet for approximating the DCCC office's network.
Fire up robocopy, xcopy or whatever you favor and do a large batch copy. I'll bet you'll get a sustained transfer rate of about 20-25 MB/s.
And like I said earlier, I get ~20 MB/s regularly between VPSes in Houston, TX and Windsor, Ontario (at different ISPs).
The idea that the only thing that could explain an apparent 22 MB/s transfer speed, assuming the gap in the mod times results from a batch file copy, is copying to a thumb drive, is rather silly. And even if the files were at some point copied to a thumb drive, that could have been done basically anywhere. They could have been put on a thumb drive by the hackers and handed off to a different department for them to deploy.
And what would explain the multiple independent lines of publicly available evidence for the spearphishing campaign? I've posted stuff from Dell SecureWorks, FireEye, etc with the data from passive DNS monitoring, the timestamped (link tracking not allowed) shortened URL data pulled from their API, etc that all strongly and independently evidence the spearphishing campaign. We also know 100% that Podesta's Gmail account was phished. We also know that the FBI had detected an attack against the DNC and tried (somewhat half-heartedly imo) to get them to move on it. I haven't seen any reporting about it but I assume they stumbled on it from something like passive DNS monitoring.
And that's without getting into the logs that the FBI would have obtained from involved ISPs, anything coming directly from the DNC/DCCC networks and whatever scary # the NSA is snooping with. I'm just talking about the publicly available information.
It's ridiculous to believe that the DNC/DCCC wasn't hacked. It's literally known what shortened URL Podesta clicked on, when it was created, when he received the email, when he clicked on the link, what the link translated to, where that host was located and who else was targeted in the same campaign.
It's ridiculous to assert that there was no hacking. So the thumb drive meme is pretty lame on its face. Attribution is something else altogether but even then, publicly available analysis of the targets, the infrastructure and the MO all point to the Russians.
It was pretty conclusive that either the Russians did it or somebody trying hard to look like the Russians and going after targets that would most fit the Kremlin's interests.
internet upload speed. When you get your new 100mb internet, it's usually displayed like this 100/50. The 50 is your upload speed. Symmetrical vs, Asymmetrical. Now I don't know what the speed at the DNC was at the time, and perhaps they had some amazing fiber link that wasn't available to the rest of the country at the time, but it does matter and unless they had the holy grail of ISPs, they likely had what the rest of us could get.
I don't know a lot about a lot, but this, I know, and if you really want to get into it, I can explain it to you. But before you go telling me my business, get your facts straight.
Now, if you are interested in the truth, and not just your political nose up the left side of someones ass, you can dig into that aspect of things. It's the key to knowing if the hack was possible or not. If you are just the partisan hack I assume you to be, ignore that, and go tell everyone how much you know about internet upload transfer speeds.
What are you disagreeing with with what he said? I'm trying to piece that together. You explained how up and down speeds work, which we all already know, and then you asked him not to tell you how things work because you are the networkdude.
But what did he state wrong? What are you disagreeing with?
I got stuck on your post trying to find meaning. Help out please.
a reply to: Kharron
He's talking about the amount of time it takes to upload gigs of data and that the transfer rate released by crowdstrike excess known upload rates via internet
The port for a USB can transfer higher amounts of data in less time
www.pcworld.com...
Read that article
L
He's talking about the amount of time it takes to upload gigs of data and that the transfer rate released by crowdstrike excess known upload rates via internet
The port for a USB can transfer higher amounts of data in less time
www.pcworld.com...
Read that article
L
Lol, Mueller playing politics with some phantom Russians again that he (or us) will never see.
Timed for the meeting with Putin on Monday. Pretty obvious stuff.
Current count of indictments relating to Russian collusion, 2 years since the FBI investigation was opened and a year since Mueller was appointed : 0
Timed for the meeting with Putin on Monday. Pretty obvious stuff.
Current count of indictments relating to Russian collusion, 2 years since the FBI investigation was opened and a year since Mueller was appointed : 0
edit on 13/7/2018 by UKTruth because: (no reason given)
We should remember that there were reports that Obama told the DOJ to stand down when he heard about Russia IPs found on servers.
The theory was that although they expected Hillary to win they needed an insurance policy. So they planned to use Russia as an excuse, and as a way to take down Trump.
The Obama admin used the DOJ the same way that he used the IRS to take down political opponents.
Obama stand-down on Russia probe looks completely partisan: Varney
Months before the 2016 presidential election, the Obama team knew that the Russians were meddling. Our National Security Council had a cybersecurity team in place, looking into it. Trying to figure out, what were the Russians up to?
Then, as the election campaign was in full swing, the national security adviser, Susan Rice, told the team to "stand down" ... stop working on options to counter the Russian attack. The man in charge of our response confirms the "stand down" order. Another member of the team told the Senate this week that he was "incredulous, and in disbelief." He asked: "Why the hell are we standing down."
The theory was that although they expected Hillary to win they needed an insurance policy. So they planned to use Russia as an excuse, and as a way to take down Trump.
The Obama admin used the DOJ the same way that he used the IRS to take down political opponents.
Obama stand-down on Russia probe looks completely partisan: Varney
edit on 7/13/18 by BlueAjah because: oops, forgot the source link
originally posted by: toysforadults
a reply to: Gothmog
With the help of the ISP yes it is traceable even with a proxy you still have to go through the ISP
Thats why I'm saying it would be more likely accessed from a stolen laptop in another country
Dont need the ISP
A stolen laptop is just about as easily traceable the moment it goes online.
Again , there is one thing that cannot be hidden nor ever changed.
a reply to: toysforadults
You're asking the wrong person.
Attribution is something of a two-part process here. The first thing to know is how specific threat actors are identified in the security community.
Often it's by the implants they leave behind when they are discovered. "Implants" is the en vogue term for a variety of malicious software used for remote access, remote execution, data collection, etc. These tools are highly specialized, often developed by multiple people over the course of years, tweaked and adapted and improved upon.
Then there's the MO, just like with non-cyber crime. What tactics do they use to infiltrate, what do they use for command and control, etc. And related to that is their preference in targets. I think a good analogy in the non-cyber world would be how law enforcement identifies serial killers.
They can look at a victim who fits a profile, who was murdered in a specific way, possibly with the use of specific weapons/gear and ascertain reasonably that a dead person is the victim of a serial killer known to law enforcement who hadn't been apprehended. They might not know the killer's identity but they know that the same person is responsible for multiple homicides.
Discovering the identity of the killer or at least, naming a suspect, would be akin to the second part of attribution. That gets a little hairier. They can look at the MO, specifically at aspects of the infrastructure to make some inferences just like with the first part. They can look at the tools for things like languages used in text strings, locale-related environment stuff from the development, etc. Importantly, the targets are considered. State-sponsored threat actors are of course advancing their government's goals. That means they're going after targets that are of interest to the government.
Okay so to CrowdStrike:
First there was the implants that were removed from the servers. In this case, the implants included X-Agent and X-Tunnel. These are known to have been used by suspected-Russian groups in past hacks and not by anyone else. Specifically, these versions show definite signs of ongoing development. That is, if you plot implants found in other hacks, there's progression which can be observed. This would tend to indicate that these weren't for instance, implants that were obtained from known copies floating around the security research community.
Within the binaries, there are some traces that point back to the same, including a C&C address (for a defunct C&C server) that had been used previously in the TV5 Monde hack which was attributed to to APT28/Fancy Bear.
They actually identified not one, but two threat actors, the second being APT29/Cozy Bear/The Dukes/CozyDuke who are known from the use of SeaDaddy and related implants. (It's perhaps better to think of these implants as "families" of implants) Cozy Bear was implicated in the 2015 hacks of non-secure WH and Pentagon networks.
So that's where *CrowdStrike* first came up with the identification of APT28 and APT29 as the threat actors who had infiltrated the DNC. But as I've detailed exhaustively, others have uncovered things like the SecureWorks with the Bitly URLs and ThreatConnect using passive DNS (and a lot more than I just don't have the energy to type out for the 5000th time) to tie the attacks against the DNC/DCCC/HRC campaign/etc to other hacks attributed to these groups and also, show the attacks in the greater context of the larger campaign. That's important when you find out that the campaign targeted you know, 5,000 entities or something (I'm not looking back for this right now) and maybe a few hundred of them were related to the DNC/Hillary and others are government contractors (of interest to foreign governments) and yet others are people that would *only* be of interest to the Russian government like Russian journalists.
Somewhere there is a really good breakdown of targets by FireEye as part of an analysis from a few years back (like 2013-14) that makes a very compelling case for Russian attribution for APT28. APT by the way is their nomenclature (APT = Advance Persistent Threat), everyone has different names from them.
I'm not hunting that down now but you can get other information about these and others from the FireEye site.
That's the last I'm explaining of this.
You're asking the wrong person.
Attribution is something of a two-part process here. The first thing to know is how specific threat actors are identified in the security community.
Often it's by the implants they leave behind when they are discovered. "Implants" is the en vogue term for a variety of malicious software used for remote access, remote execution, data collection, etc. These tools are highly specialized, often developed by multiple people over the course of years, tweaked and adapted and improved upon.
Then there's the MO, just like with non-cyber crime. What tactics do they use to infiltrate, what do they use for command and control, etc. And related to that is their preference in targets. I think a good analogy in the non-cyber world would be how law enforcement identifies serial killers.
They can look at a victim who fits a profile, who was murdered in a specific way, possibly with the use of specific weapons/gear and ascertain reasonably that a dead person is the victim of a serial killer known to law enforcement who hadn't been apprehended. They might not know the killer's identity but they know that the same person is responsible for multiple homicides.
Discovering the identity of the killer or at least, naming a suspect, would be akin to the second part of attribution. That gets a little hairier. They can look at the MO, specifically at aspects of the infrastructure to make some inferences just like with the first part. They can look at the tools for things like languages used in text strings, locale-related environment stuff from the development, etc. Importantly, the targets are considered. State-sponsored threat actors are of course advancing their government's goals. That means they're going after targets that are of interest to the government.
Okay so to CrowdStrike:
First there was the implants that were removed from the servers. In this case, the implants included X-Agent and X-Tunnel. These are known to have been used by suspected-Russian groups in past hacks and not by anyone else. Specifically, these versions show definite signs of ongoing development. That is, if you plot implants found in other hacks, there's progression which can be observed. This would tend to indicate that these weren't for instance, implants that were obtained from known copies floating around the security research community.
Within the binaries, there are some traces that point back to the same, including a C&C address (for a defunct C&C server) that had been used previously in the TV5 Monde hack which was attributed to to APT28/Fancy Bear.
They actually identified not one, but two threat actors, the second being APT29/Cozy Bear/The Dukes/CozyDuke who are known from the use of SeaDaddy and related implants. (It's perhaps better to think of these implants as "families" of implants) Cozy Bear was implicated in the 2015 hacks of non-secure WH and Pentagon networks.
So that's where *CrowdStrike* first came up with the identification of APT28 and APT29 as the threat actors who had infiltrated the DNC. But as I've detailed exhaustively, others have uncovered things like the SecureWorks with the Bitly URLs and ThreatConnect using passive DNS (and a lot more than I just don't have the energy to type out for the 5000th time) to tie the attacks against the DNC/DCCC/HRC campaign/etc to other hacks attributed to these groups and also, show the attacks in the greater context of the larger campaign. That's important when you find out that the campaign targeted you know, 5,000 entities or something (I'm not looking back for this right now) and maybe a few hundred of them were related to the DNC/Hillary and others are government contractors (of interest to foreign governments) and yet others are people that would *only* be of interest to the Russian government like Russian journalists.
Somewhere there is a really good breakdown of targets by FireEye as part of an analysis from a few years back (like 2013-14) that makes a very compelling case for Russian attribution for APT28. APT by the way is their nomenclature (APT = Advance Persistent Threat), everyone has different names from them.
I'm not hunting that down now but you can get other information about these and others from the FireEye site.
That's the last I'm explaining of this.
a reply to: Kharron
He was trying to explain that it's entirely possible for the hack to have occurred. I disagree, UNLESS the DNC way back then, had an amazing (the most awesome evah) ISP. I don't think they did, but if they did, then all the people explaining how this can't happen were and are wrong. I don't know how to find the information of who the ISP was, and what their network speeds were, but I would think that an investigator could.
My anger stems from the insinuation that I don't know or understand this. I don't know about most of the topics here, and there is plenty about computers and networking I don't know, but this, I do know and understand, and also know what's possible and what highly unlikely.
If Anti is a real news person (he writes OP Eds elsewhere I think) then perhaps he is interested in finding a key bit of info that would blow the lid off of this, or at the very least, shut up folks like me. maybe I'm wrong and DC had super fiber when the rest of us were cursing at our copper links. But rather than tell me over and over again how it just couldn't be, I want to know the facts. If they point to me being wrong, I am a big boy and can deal with that. I was wrong once before.
ETA: and never once did I deny that hacking occurred. Podesta was fished, not hacked. But to think that at the time there wasn't a guy in Russia, a guy in China, and a girl in NK all accessing files on that server and others that day, and likely today would be wrong. Sadly, by the same token, to think that there isn't a senior airman, or a petty officer behind a screen in Langley doing the same thing to Russia, China and North Korea right now, and back then, is equally as unrealistic.
Your network is only as good as it's security, and hackers have the knowledge and tools to overcome most of what we know.
I just don't believe that those speeds were available back then, and would like to know for certain.
He was trying to explain that it's entirely possible for the hack to have occurred. I disagree, UNLESS the DNC way back then, had an amazing (the most awesome evah) ISP. I don't think they did, but if they did, then all the people explaining how this can't happen were and are wrong. I don't know how to find the information of who the ISP was, and what their network speeds were, but I would think that an investigator could.
My anger stems from the insinuation that I don't know or understand this. I don't know about most of the topics here, and there is plenty about computers and networking I don't know, but this, I do know and understand, and also know what's possible and what highly unlikely.
If Anti is a real news person (he writes OP Eds elsewhere I think) then perhaps he is interested in finding a key bit of info that would blow the lid off of this, or at the very least, shut up folks like me. maybe I'm wrong and DC had super fiber when the rest of us were cursing at our copper links. But rather than tell me over and over again how it just couldn't be, I want to know the facts. If they point to me being wrong, I am a big boy and can deal with that. I was wrong once before.
ETA: and never once did I deny that hacking occurred. Podesta was fished, not hacked. But to think that at the time there wasn't a guy in Russia, a guy in China, and a girl in NK all accessing files on that server and others that day, and likely today would be wrong. Sadly, by the same token, to think that there isn't a senior airman, or a petty officer behind a screen in Langley doing the same thing to Russia, China and North Korea right now, and back then, is equally as unrealistic.
Your network is only as good as it's security, and hackers have the knowledge and tools to overcome most of what we know.
I just don't believe that those speeds were available back then, and would like to know for certain.
edit on 13-7-2018 by network dude because:
added thought
a reply to: theantediluvian
I still don't see how this is relevant to Trumps legitimate win in the 2016 Federal election. I see no way that 12 Russians could in any way shape or form influence anything remotely related to legitimate US federal election outcomes using 'hacking the DNC server' as a base for their shenanigans.
It actually appears that Rosenstein, like Obamas 'stop whining' comment, has just proved that Russian hacking didn't change votes in the 2016 federal election.
How many millions of taxpayer dollars, per Russian, does this amount to?
NB: Here are the names of the 12 hackers (may as well be innit??)........
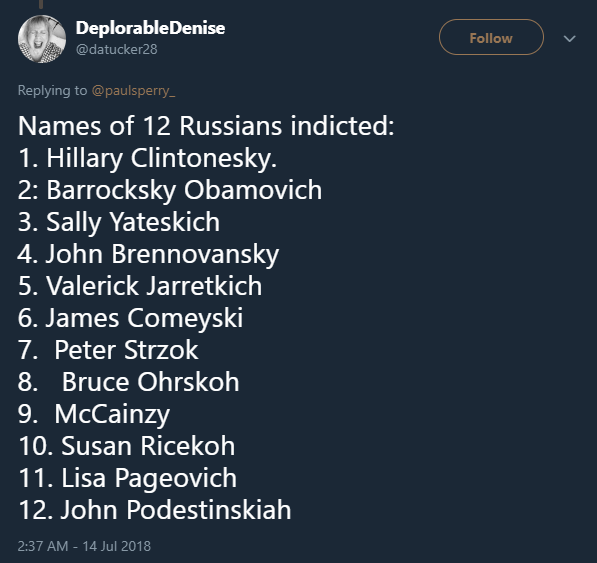
I still don't see how this is relevant to Trumps legitimate win in the 2016 Federal election. I see no way that 12 Russians could in any way shape or form influence anything remotely related to legitimate US federal election outcomes using 'hacking the DNC server' as a base for their shenanigans.
It actually appears that Rosenstein, like Obamas 'stop whining' comment, has just proved that Russian hacking didn't change votes in the 2016 federal election.
How many millions of taxpayer dollars, per Russian, does this amount to?
NB: Here are the names of the 12 hackers (may as well be innit??)........

originally posted by: toysforadults
a reply to: Kharron
He's talking about the amount of time it takes to upload gigs of data and that the transfer rate released by crowdstrike excess known upload rates via internet
The port for a USB can transfer higher amounts of data in less time
www.pcworld.com...
Read that article
L
Unbelievable. And after netdude explained a banality and contradicted nothing, you come in and do the same thing -- point me to a link to how USB 3.0 works and explain nothing about how Ante was wrong.
a reply to: theantediluvian
I'm not surprised at all that those servers were being accessed by foreign entities. It's my personal belief that she was selling access to the server to foreign entities and that's partly why she doesn't want to give them up as well.
However this does not prove that Trump was involved... it also doesn't prove what information was taken and to what extent and what was done with it.
I'm not surprised at all that those servers were being accessed by foreign entities. It's my personal belief that she was selling access to the server to foreign entities and that's partly why she doesn't want to give them up as well.
However this does not prove that Trump was involved... it also doesn't prove what information was taken and to what extent and what was done with it.
a reply to: Kharron
you asked for more information about what he was talking about which is painfully obvious in his post
he's talking about the upload/ download speed and the max capacity of the internet to transfer specific amounts of data at a specific interval and how it wasn't possible for them to transfer the data in the given time frame at the given rate
not our fault you can't grasp that and you could easily Google...
thehill.com...
read more here for your (dis)pleasure
you asked for more information about what he was talking about which is painfully obvious in his post
he's talking about the upload/ download speed and the max capacity of the internet to transfer specific amounts of data at a specific interval and how it wasn't possible for them to transfer the data in the given time frame at the given rate
not our fault you can't grasp that and you could easily Google...
thehill.com...
read more here for your (dis)pleasure
originally posted by: Kharron
originally posted by: toysforadults
a reply to: Kharron
He's talking about the amount of time it takes to upload gigs of data and that the transfer rate released by crowdstrike excess known upload rates via internet
The port for a USB can transfer higher amounts of data in less time
www.pcworld.com...
Read that article
L
Unbelievable. And after netdude explained a banality and contradicted nothing, you come in and do the same thing -- point me to a link to how USB 3.0 works and explain nothing about how Ante was wrong.
USB 3.0 or 3.1 only matters locally. Which is the main point in trying to educate on upload speeds. There is also the factor that using a shared internet connection is dependent on how many other devices are getting data at the same time.
Anti may be totally right, but as of yet, nothing has been offered to prove that, or prove my theory. (which is based on fact, not emotion)
a reply to: network dude
I would say it's safe to assume QOS services were enabled for the server and it had it's own line.
based on pure speculation but the had be able to do something right, right?
I would say it's safe to assume QOS services were enabled for the server and it had it's own line.
based on pure speculation but the had be able to do something right, right?
a reply to: theantediluvian
So, let me get this straight. If Russian's (who aren't citizens of our country) meddle with elections to get a favorable result, they are indicted, but if Democrats rig the ballot boxes to where Hillary would be selected by default, as well as, letting illegal immigrants from Mexico vote as well as dead people....it's ok?
So, let me get this straight. If Russian's (who aren't citizens of our country) meddle with elections to get a favorable result, they are indicted, but if Democrats rig the ballot boxes to where Hillary would be selected by default, as well as, letting illegal immigrants from Mexico vote as well as dead people....it's ok?
new topics
-
Israel attacking Iran again.
Middle East Issues: 47 minutes ago -
Michigan school district cancels lesson on gender identity and pronouns after backlash
Education and Media: 51 minutes ago -
When an Angel gets his or her wings
Religion, Faith, And Theology: 1 hours ago -
Comparing the theology of Paul and Hebrews
Religion, Faith, And Theology: 2 hours ago -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs: 3 hours ago -
Boston Dynamics say Farewell to Atlas
Science & Technology: 3 hours ago -
I hate dreaming
Rant: 4 hours ago -
Man sets himself on fire outside Donald Trump trial
Mainstream News: 6 hours ago -
Biden says little kids flip him the bird all the time.
Politicians & People: 6 hours ago -
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness: 6 hours ago
top topics
-
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness: 6 hours ago, 17 flags -
In an Historic First, In N Out Burger Permanently Closes a Location
Mainstream News: 8 hours ago, 14 flags -
Biden says little kids flip him the bird all the time.
Politicians & People: 6 hours ago, 8 flags -
A man of the people
Medical Issues & Conspiracies: 14 hours ago, 8 flags -
Man sets himself on fire outside Donald Trump trial
Mainstream News: 6 hours ago, 7 flags -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs: 3 hours ago, 5 flags -
4 plans of US elites to defeat Russia
New World Order: 16 hours ago, 4 flags -
Sheetz facing racial discrimination lawsuit for considering criminal history in hiring
Social Issues and Civil Unrest: 7 hours ago, 3 flags -
Boston Dynamics say Farewell to Atlas
Science & Technology: 3 hours ago, 3 flags -
Are you ready for the return of Jesus Christ? Have you been cleansed by His blood?
Religion, Faith, And Theology: 11 hours ago, 3 flags
active topics
-
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 51 • : TheMisguidedAngel -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 547 • : 777Vader -
Israel attacking Iran again.
Middle East Issues • 14 • : Solvedit -
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness • 64 • : KrustyKrab -
Michigan school district cancels lesson on gender identity and pronouns after backlash
Education and Media • 4 • : TzarChasm -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 403 • : Threadbarer -
Cat Movies
Movies • 19 • : 5thHead -
Man sets himself on fire outside Donald Trump trial
Mainstream News • 33 • : ByeByeAmericanPie -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs • 6 • : Ophiuchus1 -
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three • 104 • : CCoburn
