It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: drewlander
a reply to: Grambler
How could crowdstrike make this blunder you ask? Crowdstrike is owned by a Ukranian billionaire with ties to Clinton. Sounds like Russian meddling to me...
Basically if you see libs accuse another party of something its cuz they are already guilty of it.
YEP! The embarrassed Ukrainians "apologized" to Donald Trump for attempting to sabotage him, after he beat Hillary.
Dated 01/11/2017: www.politico.com...
The only possible explanation that isnt absolutely damning for the russian hack narrative is that the November 4 2017 AP story on the hacks is totally
wrong.
If this story is true, and crowdstrikes initial claims the alarm was first raised of a dnc hack when fancybear hacked the opposition files on trump from the DNC is wrong, then the whole russian narrative story is in shambles.
You know what could have avoided all of this?
THE FBI LOOKING AT THE SEVER, instead of taking the word of a democratic paid for company.
If the FBI had any integrity whatsoever, it would immediately find out who the source inside the DNC was for the AP article, and get to the bottom of how they knew the oppo files on trump came from the Podesta email.
Because if they are telling the truth, the russian hack narrative we have been fed is OVER.
If this story is true, and crowdstrikes initial claims the alarm was first raised of a dnc hack when fancybear hacked the opposition files on trump from the DNC is wrong, then the whole russian narrative story is in shambles.
You know what could have avoided all of this?
THE FBI LOOKING AT THE SEVER, instead of taking the word of a democratic paid for company.
If the FBI had any integrity whatsoever, it would immediately find out who the source inside the DNC was for the AP article, and get to the bottom of how they knew the oppo files on trump came from the Podesta email.
Because if they are telling the truth, the russian hack narrative we have been fed is OVER.
originally posted by: carewemust
originally posted by: drewlander
a reply to: Grambler
How could crowdstrike make this blunder you ask? Crowdstrike is owned by a Ukranian billionaire with ties to Clinton. Sounds like Russian meddling to me...
Basically if you see libs accuse another party of something its cuz they are already guilty of it.
YEP! The embarrassed Ukrainians "apologized" to Donald Trump for attempting to sabotage him, after he beat Hillary.
Dated 01/11/2017: www.politico.com...
Oh yes, remeber how Cohen or someone is so shady because he set up meetings with the Ukranians?
Yet here we have clinton team members working with ukranians to actively sabotage trumps campaign.
Were their informants placed becauise of this? Were there fisa warrants? How about invetsigations for collusion with a foriegn power?
Nope, I guess only trumps team needs that sort of "protection"
a reply to: drewlander
I read it again. I'm going to make a confession. I'm not sober. But I did read it again and I think I understand what is being said here. The fact that it took me three times, even not sober, leads me to believe that a lot of people are just taking for granted that this is a big deal without actually knowing exactly what is being said.
In the initial report on June 14th in WaPo, Shawn Henry said that the hackers stole oppo research. From the WaPo article:
Nowhere does Shawn Henry mention Guccifer 2.0 because he didn't actually exist when this interview was given. He also doesn't in anyway identify the "two files" (not the type, name, anything).
I don't think I've missed it but maybe I have. I do not see where CrowdStrike ever claimed that the document published by Guccifer 2.0 came from the DNC server let alone that it was what was referenced in the WaPo article.
In fact, I don't see from anything here how CrowdStrike could have reasonably determined that the file that "Guccifer 2.0" published didn't originate with the DNC. There's two problems here:
1. First off, it's quite possible that the same file existed on the DNC computers somewhere that was in the Podesta attachment. In fact, it's likely. It's even quite possible that the version of the file that was sent to Podesta was sent/forwarded to somebody at the DNC. Those would have the same RSID number referenced in both the Podesta attachment and the Guccifer 2.0 release.
The point is valid about linking the RSID, the edit time and the email time though. It would seem that the file G2 edited was the file was saved and then emailed to Podesta one minute later. But why would he save it one minute before sending to Podesta? Was he working on it? Was that a newer version than the one that was sent out to others earlier?
2. Secondly, without have the Podesta emails, they wouldn't have had that exact copy of the file to compare RSIDs, they could have just as easily assumed that the RSID number was a result of the edit by Guccifer 2.0 or some intermediary.
That's even more true for everyone else. The RSID doesn't identify anything in terms of the author/timedate/locale/etc it's just a unique identifier from an specific edit/save.
Now the argument from "Forensicator" seems to be that once the Podesta emails were released, it would be possible to ascertain from the RSIDs that the G2 published file was the file saved and sent to Podesta. It's not unreasonable to conclude that the G2 file was from the Podesta emails but it's also not quite as definitive as it's made out to be.
That document was released on 2016-11-08 btw (looking at the Podesta archive). Assuming there weren't files on the DNC computers with that RSID, it would still have been virtually impossible to notice this RSID correlation until then as it would required having that Podesta email.
Anyway, in conclusion:
1. It's not definitive, other perfectly plausible explanations are not ruled out.
2. There's little to no chance that it could have been noticed until 2016-11-08, about five months later.
3. It doesn't disprove anything, it's just an attempt at muddying the waters and trying to paint the CrowdStrike team as sloppy.
I read it again. I'm going to make a confession. I'm not sober. But I did read it again and I think I understand what is being said here. The fact that it took me three times, even not sober, leads me to believe that a lot of people are just taking for granted that this is a big deal without actually knowing exactly what is being said.
In the initial report on June 14th in WaPo, Shawn Henry said that the hackers stole oppo research. From the WaPo article:
The other, which the firm had named Fancy Bear, broke into the network in late April and targeted the opposition research files. It was this breach that set off the alarm. The hackers stole two files, Henry said. And they had access to the computers of the entire research staff — an average of about several dozen on any given day.
Nowhere does Shawn Henry mention Guccifer 2.0 because he didn't actually exist when this interview was given. He also doesn't in anyway identify the "two files" (not the type, name, anything).
I don't think I've missed it but maybe I have. I do not see where CrowdStrike ever claimed that the document published by Guccifer 2.0 came from the DNC server let alone that it was what was referenced in the WaPo article.
In fact, I don't see from anything here how CrowdStrike could have reasonably determined that the file that "Guccifer 2.0" published didn't originate with the DNC. There's two problems here:
1. First off, it's quite possible that the same file existed on the DNC computers somewhere that was in the Podesta attachment. In fact, it's likely. It's even quite possible that the version of the file that was sent to Podesta was sent/forwarded to somebody at the DNC. Those would have the same RSID number referenced in both the Podesta attachment and the Guccifer 2.0 release.
The point is valid about linking the RSID, the edit time and the email time though. It would seem that the file G2 edited was the file was saved and then emailed to Podesta one minute later. But why would he save it one minute before sending to Podesta? Was he working on it? Was that a newer version than the one that was sent out to others earlier?
2. Secondly, without have the Podesta emails, they wouldn't have had that exact copy of the file to compare RSIDs, they could have just as easily assumed that the RSID number was a result of the edit by Guccifer 2.0 or some intermediary.
That's even more true for everyone else. The RSID doesn't identify anything in terms of the author/timedate/locale/etc it's just a unique identifier from an specific edit/save.
Now the argument from "Forensicator" seems to be that once the Podesta emails were released, it would be possible to ascertain from the RSIDs that the G2 published file was the file saved and sent to Podesta. It's not unreasonable to conclude that the G2 file was from the Podesta emails but it's also not quite as definitive as it's made out to be.
That document was released on 2016-11-08 btw (looking at the Podesta archive). Assuming there weren't files on the DNC computers with that RSID, it would still have been virtually impossible to notice this RSID correlation until then as it would required having that Podesta email.
Anyway, in conclusion:
1. It's not definitive, other perfectly plausible explanations are not ruled out.
2. There's little to no chance that it could have been noticed until 2016-11-08, about five months later.
3. It doesn't disprove anything, it's just an attempt at muddying the waters and trying to paint the CrowdStrike team as sloppy.
a reply to: Grambler
That's not right. Think about what you're saying. In the WaPo article, Shawn Henry says that it was the exfiltration of "two files" that triggered the alarm. The fact that they are presumably oppo research related (from context of the article), does not in any way mean that either of the two files referenced were a copy of the Trump oppo doc published by Guccifer 2.0.
That's something everyone should be able to get. If that statement from the initial WaPo article the only "proof" that CrowdStrike said the doc Guccifer 2.0 published was from the DNC, then there's a big problem straight away.
Also see my last post.
Based on RSID, they'd only be able to prove that the file DID come from the DNC not that it did NOT come from the DNC. Keep in mind what an RSID is. Think of an RSID as a randomly generated unique session identifier. Where a "session" is what happens between when a file is opened and then saved. If there are no edits, nothing changes in the file. If there are edits, all of the edits are tagged with the RSID so that it's then possible to know which edits occurred together. But the RSID doesn't tell you anything about author/date/time/etc for the edit, it's basically just a random unique number.
Now it's possible that without making any additional changes to the document that was sent to Podesta, Carrk sent the file to people at the DNC and that they saved the attachment form their email. If they didn't make any changes, the RSID in the copy they had (which would be on a DNC computer, attached emails, whatever) would have the same RSID found in the copy that was attached to the email to Podesta.
You have to be leery of this #. I think most of it goes way above people's heads and the Forensicator person has a habit of ignoring plausible alternatives and overstating things, as he did with the analysis about the transfer speeds which was riddled with holes and made assumptions that are demonstrably disprovable.
Yet because it's not something the average person can follow enough to dissect (and it doesn't help that his writing style sucks), it's easy for people to just assume that it's legit af and the last word on whatever.
Anyway, I'm sure people will be repeating this for the next 2-3 years or longer unfortunately and citing it as proof and I'm probably not going to take the time to explain how they're wrong because frankly, it takes too long and it's generally a wasted effort.
If this story is true, and crowdstrikes initial claims the alarm was first raised of a dnc hack when fancybear hacked the opposition files on trump from the DNC is wrong, then the whole russian narrative story is in shambles.
That's not right. Think about what you're saying. In the WaPo article, Shawn Henry says that it was the exfiltration of "two files" that triggered the alarm. The fact that they are presumably oppo research related (from context of the article), does not in any way mean that either of the two files referenced were a copy of the Trump oppo doc published by Guccifer 2.0.
That's something everyone should be able to get. If that statement from the initial WaPo article the only "proof" that CrowdStrike said the doc Guccifer 2.0 published was from the DNC, then there's a big problem straight away.
Also see my last post.
Based on RSID, they'd only be able to prove that the file DID come from the DNC not that it did NOT come from the DNC. Keep in mind what an RSID is. Think of an RSID as a randomly generated unique session identifier. Where a "session" is what happens between when a file is opened and then saved. If there are no edits, nothing changes in the file. If there are edits, all of the edits are tagged with the RSID so that it's then possible to know which edits occurred together. But the RSID doesn't tell you anything about author/date/time/etc for the edit, it's basically just a random unique number.
Now it's possible that without making any additional changes to the document that was sent to Podesta, Carrk sent the file to people at the DNC and that they saved the attachment form their email. If they didn't make any changes, the RSID in the copy they had (which would be on a DNC computer, attached emails, whatever) would have the same RSID found in the copy that was attached to the email to Podesta.
You have to be leery of this #. I think most of it goes way above people's heads and the Forensicator person has a habit of ignoring plausible alternatives and overstating things, as he did with the analysis about the transfer speeds which was riddled with holes and made assumptions that are demonstrably disprovable.
Yet because it's not something the average person can follow enough to dissect (and it doesn't help that his writing style sucks), it's easy for people to just assume that it's legit af and the last word on whatever.
Anyway, I'm sure people will be repeating this for the next 2-3 years or longer unfortunately and citing it as proof and I'm probably not going to take the time to explain how they're wrong because frankly, it takes too long and it's generally a wasted effort.
edit on 2018-5-24 by
theantediluvian because: (no reason given)
edit on 2018-5-24 by theantediluvian because: (no reason given)
a reply to: theantediluvian
Funny...had the FBI just done their jobs instead of once again giving Hillary special treatment theyd have retained custody of the server and been able to provide reasonable forensic evidence.
Funny...had the FBI just done their jobs instead of once again giving Hillary special treatment theyd have retained custody of the server and been able to provide reasonable forensic evidence.
a reply to: Grambler
It wouldn't surprise me that there could be found a link in all of this stuff that also goes to someone withing the Cambridge Group . They seem to be the Big Boy Pros with all the right contacts in the right places for the right time . A very important Dot to keep ready to apply when trying to figure this convoluted stuff out .
It wouldn't surprise me that there could be found a link in all of this stuff that also goes to someone withing the Cambridge Group . They seem to be the Big Boy Pros with all the right contacts in the right places for the right time . A very important Dot to keep ready to apply when trying to figure this convoluted stuff out .
a reply to: theantediluvian
Lets skip the RSID stuff for now.
The part I want to focus on is where did the orginal opposition file on Trump come from.
Now your claim is that the Washington post article, that contains the orginal claims from corwdstrike, does not prove that they are referencing the same files when they say they were hacked from the DNC server.
That is not true.
here is the very beginning of the wash post artilce.
Those security experts would be, Crowdstrike, and they are admitting that files that were stolen were the opposition files on trump.
Now you claim "Well maybe these were other opposition files on trump, and not the ones intially released.
First, that doesn't even pass the smell test. Why wouldnt crowdstrike immediately make it clear that the files that were released in mid June were not part of the hack they had witnessed?
furthermore, if you read the AP article where the narrative changes, they fully admit that these were the files that crwdstrike was referring to, as they show that people were MISTAKEN in their belief the hack came from the DNC server when actually it was the Podesta email.
The narrative pushed up onto this Nov 4 2017 AP article was that the original Guccifer 2.0 leak of the opposition file on trump came from the DNC.
This jives with what crowdstrike had claimed. Now we know that was not true.
Now keep in mind, Podesta claimss to have not even known he was hacked until at the very earliest the summer of 2016, but wasnt certain until october.
This means that Crowdstrike would have witnessed the guccifer released files, and yet were unaware that they in fact were not files from the DNC server.
Yet they didnt claim that, and they never spoke up and said this was proof that another hack had occurred.
And the orginal crowdstrike claims from the washington Post article says it was fanccy bear that hacked this opposition files from the DNC server.
The prevailing narrative now is that Guccifer was in fact part of Fancy bear.
www.thedailybeast.com...
Are you claiming that claims of Guccifer being part of Fancy bear are wrong? Does that mean there is no proof that all of the Guccifer leaked documents actually came from russia?
You cant have it both ways.
either the hacking narrative has changed and was intially wrong becuase Fancy bear (of which Guccifer is alleged to be part of) got the oppositoon research on Trump from the Podesta emails and not the DNC, or Guccifer is not part of Fancy bear, and that part of the narrative is wrong.
Lets skip the RSID stuff for now.
The part I want to focus on is where did the orginal opposition file on Trump come from.
Now your claim is that the Washington post article, that contains the orginal claims from corwdstrike, does not prove that they are referencing the same files when they say they were hacked from the DNC server.
That is not true.
here is the very beginning of the wash post artilce.
Russian government hackers penetrated the computer network of the Democratic National Committee and gained access to the entire database of opposition research on GOP presidential candidate Donald Trump, according to committee officials and security experts who responded to the breach.
Those security experts would be, Crowdstrike, and they are admitting that files that were stolen were the opposition files on trump.
Now you claim "Well maybe these were other opposition files on trump, and not the ones intially released.
First, that doesn't even pass the smell test. Why wouldnt crowdstrike immediately make it clear that the files that were released in mid June were not part of the hack they had witnessed?
furthermore, if you read the AP article where the narrative changes, they fully admit that these were the files that crwdstrike was referring to, as they show that people were MISTAKEN in their belief the hack came from the DNC server when actually it was the Podesta email.
But there were signs of dishonesty from the start. The first document Guccifer 2.0 published on June 15 came not from the DNC as advertised but from Podesta’s inbox , according to a former DNC official who spoke on condition of anonymity because he was not authorized to speak to the press.
The narrative pushed up onto this Nov 4 2017 AP article was that the original Guccifer 2.0 leak of the opposition file on trump came from the DNC.
This jives with what crowdstrike had claimed. Now we know that was not true.
Now keep in mind, Podesta claimss to have not even known he was hacked until at the very earliest the summer of 2016, but wasnt certain until october.
This means that Crowdstrike would have witnessed the guccifer released files, and yet were unaware that they in fact were not files from the DNC server.
Yet they didnt claim that, and they never spoke up and said this was proof that another hack had occurred.
And the orginal crowdstrike claims from the washington Post article says it was fanccy bear that hacked this opposition files from the DNC server.
The prevailing narrative now is that Guccifer was in fact part of Fancy bear.
Working off the IP address, U.S. investigators identified Guccifer 2.0 as a particular GRU officer working out of the agency’s headquarters on Grizodubovoy Street in Moscow. (The Daily Beast’s sources did not disclose which particular officer worked as Guccifer.)
Security firms and declassified U.S. intelligence findings previously identified the GRU as the agency running “Fancy Bear,” the ten-year-old hacking organization behind the DNC email theft, as well as breaches at NATO, Obama’s White House, a French television station, the World Anti-Doping Agency, and countless NGOs, and militaries and civilian agencies in Europe, Central Asia, and the Caucasus.
www.thedailybeast.com...
Are you claiming that claims of Guccifer being part of Fancy bear are wrong? Does that mean there is no proof that all of the Guccifer leaked documents actually came from russia?
You cant have it both ways.
either the hacking narrative has changed and was intially wrong becuase Fancy bear (of which Guccifer is alleged to be part of) got the oppositoon research on Trump from the Podesta emails and not the DNC, or Guccifer is not part of Fancy bear, and that part of the narrative is wrong.
a reply to: bigfatfurrytexan
The amount of people that think you have to physically touch a computer to understand it is mind boggling. The FBI got a full image of it (an image is an exact copy of a computer's state at the time the copy is made) so they didnt need physical access which is why they didnt push for it.
The amount of people that think you have to physically touch a computer to understand it is mind boggling. The FBI got a full image of it (an image is an exact copy of a computer's state at the time the copy is made) so they didnt need physical access which is why they didnt push for it.
And eta,
I get what you are saying about the RSID.
For your suggestion to apply, that would mean that Fancybear had to hack the DNC and get the exact saem save file that he also phished from Podesta.
There are a few problems with this though.
First it means that eveyone that attrivuted the Guccfier drops to hacks of the DNC would be basing that solely on RSID numbers, whihc is flimsy at best (as you have shown) This would have been further reason to HAVE THE FBI LOOK AT THE SERVER!!!! instead of relying on third party sources.
Second, in the interview with Podesta I posted, he claims he initially wondered if he was hacked because he saw things beng released in the summer (by Guccifer) that were on his emails and not thenDNC.
techcrunch.com...
Yet again, Crowdstrike didnt speak up to say that these were seperate hacks.
I get what you are saying about the RSID.
For your suggestion to apply, that would mean that Fancybear had to hack the DNC and get the exact saem save file that he also phished from Podesta.
There are a few problems with this though.
First it means that eveyone that attrivuted the Guccfier drops to hacks of the DNC would be basing that solely on RSID numbers, whihc is flimsy at best (as you have shown) This would have been further reason to HAVE THE FBI LOOK AT THE SERVER!!!! instead of relying on third party sources.
Second, in the interview with Podesta I posted, he claims he initially wondered if he was hacked because he saw things beng released in the summer (by Guccifer) that were on his emails and not thenDNC.
Podesta: In the summer, when the DNC hack documents started coming out, there was a document in that release that didn’t seem like it would have made its way to the DNC and may have come from my email account. So at least the possibility I’d been hacked rose during the course of the summer.
techcrunch.com...
Yet again, Crowdstrike didnt speak up to say that these were seperate hacks.
originally posted by: Pyle
a reply to: bigfatfurrytexan
The amount of people that think you have to physically touch a computer to understand it is mind boggling. The FBI got a full image of it (an image is an exact copy of a computer's state at the time the copy is made) so they didnt need physical access which is why they didnt push for it.
Ridiculous!
I cant believe people fall for this.
There is not one good reason why the FBI wouldnt demand to see the server, or why the dnc wouldnt isnist that the fbi look at it.
Any number of mistakes, errors, or intentional misleading evidnece can occur thorugh digital copies.
If the physical server is not necessary, then why did the FBI take Hillarys server as evidnece in the investigation of her server? Surely they had no need for the physical server, right?
And surely then that they FBI losing chain of custody for that server for 5 weeks would be meaningless, right?
Of course that is not the case.
And as an aside, isnt this little tidbit funny.
techcrunch.com...
Funny, crowdstrikes president told Obama in 2008 about hacks from places like russia, yet Obama didnt seemed worried at all.
I
Henry, the president of CrowdStrike and a former executive assistant director at the FBI, also questioned the Bureau’s reaction to the hacks that plagued the Clinton campaign. Henry recalled personally notifying the Obama and McCain campaigns about breaches that occurred in the run-up to the 2008 election.
techcrunch.com...
Funny, crowdstrikes president told Obama in 2008 about hacks from places like russia, yet Obama didnt seemed worried at all.
I
a reply to: Grambler
The file in question is a single Word doc. It's not an "entire database." (or even a database file)
You're wrong. I'll try to explain this again.
We're talking about the difference between revisions of the same document, that's where the RSID comes in. You want to set the RSIDs aside but that doesn't makes sense, it's the corresponding RSIDs that are fundamental to the claim you're repeating.
Imagine that you and I are both sent the same MS Word doc. I edit it the copy of it I have, making a change somewhere, and then save it. My copy of the same document now carries an edit that is tagged with a unique identifier, the RSID. If you edit your copy of the file, even making the exact same change, it will have a different RSID corresponding to your "session."
The argument by "Forensicator" broken down to its simplest form:
1. The file was edited by Carrk 1 minute before it was sent to Podesta.
2. The RSID observed in the attached file from the Podesta email marks that edit.
3. The file published by Guccifer 2.0 (which itself had been manipulated) contained the same RSID.
4. Therefore the version of the document Guccifer 2.0 published must have come from Podesta's email.
Except, that if Carrk didn't make any more edits to his copy of the document before sending it to other people after Podesta, or if Podesta sent his copy to other people, and the recipients did not themselves edit the copy they'd received, the RSID would be present.
In other words, just because Podesta had a copy with the RSID present doesn't mean that other people didn't have the same copy of the document.
Furthermore, there's no way that CrowdStrike or anyone else could have looked at the file Guccifer 2.0 published and concluded that it didn't originate from the DNC network based on the RSID. So even we assume that a copy of the document with the RSID didn't exist on DNC computers (something we have no way of knowing), there'd be no way of knowing whether or not the RSID was the result of a subsequent edit made after exfilitration — and the file itself had been manipulated.
This is critical to the whole discussion.
No. The claim you're repeating is that the doc Guccifer 2.0 released MUST have been one of the two files that Shawn Henry referenced in the WaPo article. Based on what? The assumption that there was only a single Word doc of oppo research about Donald Trump on the DNC systems? That's not great.
Furthermore, as I attempted to explain above, it's also possible that the document in question was in fact one of the two referenced by Henry and it's also possible that it was the same revision as what was sent to Podesta (as identified by the RSID). It's impossible to know.
All of the speculation and discussion beyond this point is moot if this part isn't entirely understood.
Now your claim is that the Washington post article, that contains the orginal claims from corwdstrike, does not prove that they are referencing the same files when they say they were hacked from the DNC server.
That is not true.
here is the very beginning of the wash post artilce.
The file in question is a single Word doc. It's not an "entire database." (or even a database file)
Now you claim "Well maybe these were other opposition files on trump, and not the ones intially released.
First, that doesn't even pass the smell test. Why wouldnt crowdstrike immediately make it clear that the files that were released in mid June were not part of the hack they had witnessed?
You're wrong. I'll try to explain this again.
We're talking about the difference between revisions of the same document, that's where the RSID comes in. You want to set the RSIDs aside but that doesn't makes sense, it's the corresponding RSIDs that are fundamental to the claim you're repeating.
Imagine that you and I are both sent the same MS Word doc. I edit it the copy of it I have, making a change somewhere, and then save it. My copy of the same document now carries an edit that is tagged with a unique identifier, the RSID. If you edit your copy of the file, even making the exact same change, it will have a different RSID corresponding to your "session."
The argument by "Forensicator" broken down to its simplest form:
1. The file was edited by Carrk 1 minute before it was sent to Podesta.
2. The RSID observed in the attached file from the Podesta email marks that edit.
3. The file published by Guccifer 2.0 (which itself had been manipulated) contained the same RSID.
4. Therefore the version of the document Guccifer 2.0 published must have come from Podesta's email.
Except, that if Carrk didn't make any more edits to his copy of the document before sending it to other people after Podesta, or if Podesta sent his copy to other people, and the recipients did not themselves edit the copy they'd received, the RSID would be present.
In other words, just because Podesta had a copy with the RSID present doesn't mean that other people didn't have the same copy of the document.
Furthermore, there's no way that CrowdStrike or anyone else could have looked at the file Guccifer 2.0 published and concluded that it didn't originate from the DNC network based on the RSID. So even we assume that a copy of the document with the RSID didn't exist on DNC computers (something we have no way of knowing), there'd be no way of knowing whether or not the RSID was the result of a subsequent edit made after exfilitration — and the file itself had been manipulated.
This is critical to the whole discussion.
furthermore, if you read the AP article where the narrative changes, they fully admit that these were the files that crwdstrike was referring to, as they show that people were MISTAKEN in their belief the hack came from the DNC server when actually it was the Podesta email.
No. The claim you're repeating is that the doc Guccifer 2.0 released MUST have been one of the two files that Shawn Henry referenced in the WaPo article. Based on what? The assumption that there was only a single Word doc of oppo research about Donald Trump on the DNC systems? That's not great.
Furthermore, as I attempted to explain above, it's also possible that the document in question was in fact one of the two referenced by Henry and it's also possible that it was the same revision as what was sent to Podesta (as identified by the RSID). It's impossible to know.
All of the speculation and discussion beyond this point is moot if this part isn't entirely understood.
a reply to: Grambler
Nobody was basing anything on the RSID though. I feel like we need to take a step back for a second here. Have you read the first "Guccifer 2.0" post?
Guccifer 2.0 DNC’s servers hacked by a lone hacker
"Guccifer 2.0" makes the claim that the files came from the DNC and alludes to the WaPo article before embedding a number of documents, including the one in question.
As "Forensicator" conceded in (at your link):
He then goes on to say that they must have known in October. That's really the claim here. That when the files were released, they could then tell that the file published on July 15th by "Guccifer 2.0" contained the same RSID as the one that was emailed to Podesta.
Furthermore from the original Forensicator source:
That is completely correct. "They" cannot conclude that the Podesta emails were the actual source of the documents.
I'll note here that what was published was more than 5 Word docs. There were a total of 11 files published. 5 of them were Word docs, the other 6 were Excel spreadsheets which do NOT show up in the Podesta emails.
In other words, we have a second problem with the narrative that is being spun here: those Excel files (or versions of them) don't exist in the Podesta emails. If they weren't from the phished Podesta emails, where did they come from?
First it means that eveyone that attrivuted the Guccfier drops to hacks of the DNC would be basing that solely on RSID numbers, whihc is flimsy at best (as you have shown) This would have been further reason to HAVE THE FBI LOOK AT THE SERVER!!!! instead of relying on third party sources.
Nobody was basing anything on the RSID though. I feel like we need to take a step back for a second here. Have you read the first "Guccifer 2.0" post?
Guccifer 2.0 DNC’s servers hacked by a lone hacker
"Guccifer 2.0" makes the claim that the files came from the DNC and alludes to the WaPo article before embedding a number of documents, including the one in question.
As "Forensicator" conceded in (at your link):
Investigators would have been able to rapidly determine if there were textual differences between Guccifer 2.0’s document and the DNC’s. If there were no textual differences, an initial determination might have been difficult, because Guccifer 2.0 went to some trouble to obscure internal metadata, known as Revision Save ID’s (RSID’s), which can be used to uniquely identify sections of text that have been changed and added into a Word document.
He then goes on to say that they must have known in October. That's really the claim here. That when the files were released, they could then tell that the file published on July 15th by "Guccifer 2.0" contained the same RSID as the one that was emailed to Podesta.
Furthermore from the original Forensicator source:
2016-10-07] Wikileaks released the first batch of Podesta emails. Per our analysis, all five of Guccifer 2’s first five Word documents (and an additional document used as a template) can be matched with source documents that were included as attachments to Podesta’s emails. We do not conclude that Podesta’s emails were the actual source of Guccifer 2’s first five Word documents, but note that this conclusion cannot be ruled out.
That is completely correct. "They" cannot conclude that the Podesta emails were the actual source of the documents.
I'll note here that what was published was more than 5 Word docs. There were a total of 11 files published. 5 of them were Word docs, the other 6 were Excel spreadsheets which do NOT show up in the Podesta emails.
In other words, we have a second problem with the narrative that is being spun here: those Excel files (or versions of them) don't exist in the Podesta emails. If they weren't from the phished Podesta emails, where did they come from?
edit on 2018-5-24 by theantediluvian because:
(no reason given)
a reply to: Grambler
I moved this to a different post because I discovered it as I was composing my last post. I had been wondering how they had determined that the RSID in question (that exists in both the Podesta email and Guccifer 2.0 published copies) was a result of the Carrk edit.
Because I couldn't think of a way that this could readily achieved. Then I was thinking, "Well, every RSID that is in a document is in a list in the doc header so maybe they looked at the sequence?"
So I went to the original Forensicator post and discovered that no, that's not the case. In fact, scratch what credit I had given this claim due to undeserved benefit of the doubt.
Jesus.
Okay, let me try to explain this. They're not actually supporting their claim with some comparison/analysis of RSIDs. They're noting from metadata in the Podesta document, that it appears that an edit was made by Carrk before he sent the doc to Podesta.
That edit *should* have a corresponding RSID. But they don't know what edit was made so they don't know what RSID would correspond to the edit that Carrk made.
What they're effectively claiming is this:
1. The unnamed DNC source in the AP article is saying that it's now known that the document in question originated with the Podesta emails.
2. They hypothesize that this determination could have been made by a comparison of RSIDs by somebody who had all the DNC copies, the Guccifer 2.0 copy and the Podesta email copy. Which makes sense. If none of the local DNC copies of the file had an RSID that was present in both the Podesta email and Guccifer 2.0 copies, a fair conclusion is that the correlated RSID resulted from Carrk's edit which would in fact imply that the Guccifer 2.0 copy came from the Podesta email and not a local DNC copy.
3. They're then asserting that the comment from the unnamed DNC source indicates that such an analysis was in fact made at some point after the Podesta emails were published and it was then discovered that contrary to what was initially believed (and again, there was no way of determining otherwise), the Guccifer 2.0 copy came from the Podesta emails.
The unnamed DNC source, assuming the claim is accurate, doesn't say when this was discovered. We do know from the lawsuit that CrowdStrike did do the post mitigation forensic analysis for the lawsuit. We also know from the lawsuit, that they went scorched earth. They claim more than 140 decommissioned servers, 180 PCs wiped and like a dozen servers "rebuilt." Not much context there but it sounds like the "rebuilt" servers were virtualization hosts and the 140 servers were VMs. I'd assume shared several terabytes of shared storage. I wonder if VHDs from the shared storage were provided to the FBI? There'd be no real reason to turn over the physical virtualization hosts/storage.
Anyway, I'm going off on a tangent. The point here is that it assuming the DNC source in the AP article is correct, this fact could not have been known prior to the WikiLeaks publication at all and furthermore, it's anyone's guess except those involved, when they made this determination. Since the lawsuit was filed in mid-April, we can assume that all of the forensic analysis was done before then.
I guess the complaint here is that (again, assuming all this) that the DNC didn't then go back and set the record straight on the origins of the doc posted by Guccifer 2.0 as discussed in reports from 2016 and that this was their responsibility because... "official narrative" some other # "media proxies" blah blah blah?
And the proof of this "official narrative" (whatever that actually means) and the DNC's ownership of it is the initial WaPo article?
Give me a break.
At least that part of the discussion wasn't a complete waste. CrowdStrike never claimed that files Guccifer 2.0 released after the WaPo article were what Henry referenced in the article, Guccifer 2.0 made that claim. And there was no way for CrowdStrike or anyone else to disprove Guccifer 2.0's claim until at LEAST 5 months later when the Podesta emails were released.
And we're supposed to draw conclusions, without any additional information about the nature or timeline of the forensic analysis, about them potentially discovering this needle in a very large haystack and the unknown lag between its (assumed) discovery and the AP article?
But wait, there were no hacks!
And if there was no hack of the DNC, then how could there be a difference between files that weren't exfilitrated from the DNC by nonexistent hackers who didn't hack the DNC and those in the Podesta emails? Which begs the question why then would anyone from the DNC (who wasn't hacked) then make a point of saying that this file didn't come from the DNC which NOBODY could have EVER known unless there was a forensic analysis which compared local copies (preserved in backups because the whole network was hosed) to the Podesta email copy.
In a roundabout way, the attempt to muddy the waters and cast doubt on CrowdStrike actually suggests that there was a hack in contradiction to the claims by the very same people who pushed the not very great "gap time" analysis intended to prove that there was no hack in the first place.
Talk about people trying to "have it both ways."
I moved this to a different post because I discovered it as I was composing my last post. I had been wondering how they had determined that the RSID in question (that exists in both the Podesta email and Guccifer 2.0 published copies) was a result of the Carrk edit.
Because I couldn't think of a way that this could readily achieved. Then I was thinking, "Well, every RSID that is in a document is in a list in the doc header so maybe they looked at the sequence?"
So I went to the original Forensicator post and discovered that no, that's not the case. In fact, scratch what credit I had given this claim due to undeserved benefit of the doubt.
Based on our related research, we observe that all five of Guccifer 2’s early document disclosures can be sourced to the Wikileaks Podesta email collection. We show how 1.doc was derived from some version of the Trump opposition report, but do not have enough information to determine if it came from Podesta’s email or from some other version stored on a DNC server. The AP report cites an anonymous former DNC official as saying that Guccifer 2’s version of the Trump opposition report is derived from the version found in Podesta’s emails.
Jesus.
Okay, let me try to explain this. They're not actually supporting their claim with some comparison/analysis of RSIDs. They're noting from metadata in the Podesta document, that it appears that an edit was made by Carrk before he sent the doc to Podesta.
That edit *should* have a corresponding RSID. But they don't know what edit was made so they don't know what RSID would correspond to the edit that Carrk made.
What they're effectively claiming is this:
1. The unnamed DNC source in the AP article is saying that it's now known that the document in question originated with the Podesta emails.
2. They hypothesize that this determination could have been made by a comparison of RSIDs by somebody who had all the DNC copies, the Guccifer 2.0 copy and the Podesta email copy. Which makes sense. If none of the local DNC copies of the file had an RSID that was present in both the Podesta email and Guccifer 2.0 copies, a fair conclusion is that the correlated RSID resulted from Carrk's edit which would in fact imply that the Guccifer 2.0 copy came from the Podesta email and not a local DNC copy.
3. They're then asserting that the comment from the unnamed DNC source indicates that such an analysis was in fact made at some point after the Podesta emails were published and it was then discovered that contrary to what was initially believed (and again, there was no way of determining otherwise), the Guccifer 2.0 copy came from the Podesta emails.
The unnamed DNC source, assuming the claim is accurate, doesn't say when this was discovered. We do know from the lawsuit that CrowdStrike did do the post mitigation forensic analysis for the lawsuit. We also know from the lawsuit, that they went scorched earth. They claim more than 140 decommissioned servers, 180 PCs wiped and like a dozen servers "rebuilt." Not much context there but it sounds like the "rebuilt" servers were virtualization hosts and the 140 servers were VMs. I'd assume shared several terabytes of shared storage. I wonder if VHDs from the shared storage were provided to the FBI? There'd be no real reason to turn over the physical virtualization hosts/storage.
Anyway, I'm going off on a tangent. The point here is that it assuming the DNC source in the AP article is correct, this fact could not have been known prior to the WikiLeaks publication at all and furthermore, it's anyone's guess except those involved, when they made this determination. Since the lawsuit was filed in mid-April, we can assume that all of the forensic analysis was done before then.
I guess the complaint here is that (again, assuming all this) that the DNC didn't then go back and set the record straight on the origins of the doc posted by Guccifer 2.0 as discussed in reports from 2016 and that this was their responsibility because... "official narrative" some other # "media proxies" blah blah blah?
And the proof of this "official narrative" (whatever that actually means) and the DNC's ownership of it is the initial WaPo article?
Give me a break.
At least that part of the discussion wasn't a complete waste. CrowdStrike never claimed that files Guccifer 2.0 released after the WaPo article were what Henry referenced in the article, Guccifer 2.0 made that claim. And there was no way for CrowdStrike or anyone else to disprove Guccifer 2.0's claim until at LEAST 5 months later when the Podesta emails were released.
And we're supposed to draw conclusions, without any additional information about the nature or timeline of the forensic analysis, about them potentially discovering this needle in a very large haystack and the unknown lag between its (assumed) discovery and the AP article?
But wait, there were no hacks!
And if there was no hack of the DNC, then how could there be a difference between files that weren't exfilitrated from the DNC by nonexistent hackers who didn't hack the DNC and those in the Podesta emails? Which begs the question why then would anyone from the DNC (who wasn't hacked) then make a point of saying that this file didn't come from the DNC which NOBODY could have EVER known unless there was a forensic analysis which compared local copies (preserved in backups because the whole network was hosed) to the Podesta email copy.
In a roundabout way, the attempt to muddy the waters and cast doubt on CrowdStrike actually suggests that there was a hack in contradiction to the claims by the very same people who pushed the not very great "gap time" analysis intended to prove that there was no hack in the first place.
Talk about people trying to "have it both ways."
originally posted by: Pyle
a reply to: bigfatfurrytexan
The amount of people that think you have to physically touch a computer to understand it is mind boggling. The FBI got a full image of it (an image is an exact copy of a computer's state at the time the copy is made) so they didnt need physical access which is why they didnt push for it.
You can show us where the FBI got a full image right?
I hear different.
Ouchie
🤷
How could it be a hack if 20 megabytes per second was the transfer/copy speed of the files?
a reply to: BrennanHuff
That's another bogus talking point created by the same people. I've addressed it a few times so I'll just save myself the effort and quote myself.
The files that were "analyzed" didn't come from the DNC, they came from the DCCC, a point that is almost ALWAYS missed which is actually ironic considering the topic of this thread.
That's another bogus talking point created by the same people. I've addressed it a few times so I'll just save myself the effort and quote myself.
originally posted by: theantediluvian
originally posted by: jadedANDcynical
a reply to: Dudemo5
What you're not getting is the analysis done by the Forensicator is confirmed by Binny's statements.
There are two separate and unconnected entities (the Forensicator and Binny) that have come to the same conclusion.
The analysis by "The Forensicator" is bunk. First off, it has nothing to do with the DNC, a point that keeps being missed by people running around talking about it like it's the holy grail.
The files in the archive he looked at was released via torrent on or about Sept 13. They were files from the DCCC — from the DCCC hack. If you look at it again real quick, you'll notice that the mod times are all 2016-07-05 (6-7 weeks after the CrowdStrike announcement).
Most importantly, the theoretical transfer, assuming that's what is evidenced, could have happened anywhere:
* it could have occurred between two computers at the DCCC prior to the final archive being exfiltrated.
* it could have occurred between two computers on the hacker's own network.
* it could also have occurred between two interim boxes in between or even between the DCCC box and an interim destination.
You see this?
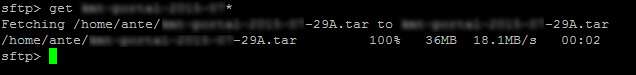
That's a transfer I did earlier today between a VPS in Houston, TX and another in Windsor, Ontario at a different ISP. I regularly get ~20MB/s between them.
The files that were "analyzed" didn't come from the DNC, they came from the DCCC, a point that is almost ALWAYS missed which is actually ironic considering the topic of this thread.
a reply to: BrennanHuff
A few other things:
Podesta's password was phished and it was for his Gmail account. So the dodgy transfer speed meme wouldn't apply in this case anyway if the file came from Carrk's email to Podesta.
If that's where the original file published by "Guccifer 2.0" came from, then that links the Podesta phishing with the DCCC hack because "Guccifer 2.0" is solidly linked to that already.
"Guccifer 2.0" provided two and half gigs of voter data stolen from the DCCC directly to FL GOP operative Aaron Nevins (after Nevins contact him on Twitter) and then also directed Roger Stone to it on Nevins's blog. Roger Stone viewed and comment on it but claims he didn't pass it along.
You can read about that here.
A few other things:
Podesta's password was phished and it was for his Gmail account. So the dodgy transfer speed meme wouldn't apply in this case anyway if the file came from Carrk's email to Podesta.
If that's where the original file published by "Guccifer 2.0" came from, then that links the Podesta phishing with the DCCC hack because "Guccifer 2.0" is solidly linked to that already.
"Guccifer 2.0" provided two and half gigs of voter data stolen from the DCCC directly to FL GOP operative Aaron Nevins (after Nevins contact him on Twitter) and then also directed Roger Stone to it on Nevins's blog. Roger Stone viewed and comment on it but claims he didn't pass it along.
You can read about that here.
new topics
-
Former Labour minister Frank Field dies aged 81
People: 1 hours ago -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 3 hours ago -
This is our Story
General Entertainment: 5 hours ago -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 8 hours ago -
Ode to Artemis
General Chit Chat: 8 hours ago
top topics
-
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 16 hours ago, 14 flags -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 8 hours ago, 12 flags -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 14 hours ago, 6 flags -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 12 hours ago, 6 flags -
Ditching physical money
History: 12 hours ago, 4 flags -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 3 hours ago, 4 flags -
Don't take advantage of people just because it seems easy it will backfire
Rant: 12 hours ago, 4 flags -
Ode to Artemis
General Chit Chat: 8 hours ago, 3 flags -
Former Labour minister Frank Field dies aged 81
People: 1 hours ago, 3 flags -
This is our Story
General Entertainment: 5 hours ago, 2 flags
active topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 13 • : Xtrozero -
So this is what Hamas considers 'freedom fighting' ...
War On Terrorism • 238 • : FlyersFan -
Deadpool and Wolverine
Movies • 6 • : confuzedcitizen -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 19 • : kwaka -
Breaking Baltimore, ship brings down bridge, mass casualties
Other Current Events • 473 • : bally001 -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs • 19 • : pianopraze -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 39 • : BedevereTheWise -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 46 • : DAVID64 -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 126 • : Xtrozero -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry • 9 • : crayzeed