It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: RazorV66
That 87 second time comes from "The Forensicator." "He" arrived at it this way:
- "He" *assumed* that what "he" was looking at was the result of a batch file transfer.
- "He" took the mod times from files in the archive from the DCCC (again, this is not anything to do with the DNC hack) and subtracted the oldest mod time from the newest.
You can see that as "begin time" and "end time" here:
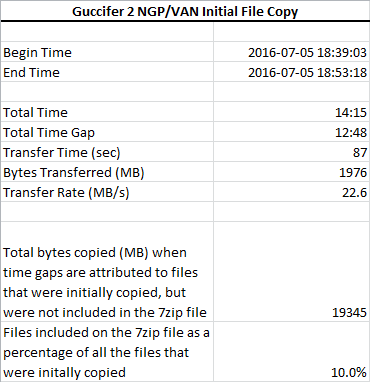
- That came out to be 14 minutes and 15 seconds. The 12 minutes and 48 seconds labeled "gap time" is him adding up all the spans ("gaps") between mod times.
- To support his assumption about a batch transfer, he further assumed that the explanation for the gaps was missing files — files copied as part of the hypothetical batch that weren't included in the archive. Another completely plausible explanation (which he concedes) is "think time" — that the person copied files, scrolled a bit, copied some more files, scrolled a bit, copied some more files, etc.
In other words, another perfectly plausible scenario is that times are *not* the result of a batch transfer at all.
- So then he subtracted the "gap time" total from the total time and came up with 87 seconds.
- He then divided 1976 MB (apparently the total size of all files considered) by 87 seconds to arrive at his estimated transfer rate.
- Extrapolating further on his chain of assumptions, he then multiplied the "gap time" by his estimated transfer rate and speculated that there were 19 gigs in his hypothetical batch and that 90% of the files in that batch were not included in the archive.
If Binney and his team couldn't replicate the speed, they can email me and I'll do it for them with two VPSes from two popular ISPs, in datacenters that are a couple thousand miles away from one another.
That 87 second time comes from "The Forensicator." "He" arrived at it this way:
- "He" *assumed* that what "he" was looking at was the result of a batch file transfer.
- "He" took the mod times from files in the archive from the DCCC (again, this is not anything to do with the DNC hack) and subtracted the oldest mod time from the newest.
You can see that as "begin time" and "end time" here:

- That came out to be 14 minutes and 15 seconds. The 12 minutes and 48 seconds labeled "gap time" is him adding up all the spans ("gaps") between mod times.
- To support his assumption about a batch transfer, he further assumed that the explanation for the gaps was missing files — files copied as part of the hypothetical batch that weren't included in the archive. Another completely plausible explanation (which he concedes) is "think time" — that the person copied files, scrolled a bit, copied some more files, scrolled a bit, copied some more files, etc.
In other words, another perfectly plausible scenario is that times are *not* the result of a batch transfer at all.
- So then he subtracted the "gap time" total from the total time and came up with 87 seconds.
- He then divided 1976 MB (apparently the total size of all files considered) by 87 seconds to arrive at his estimated transfer rate.
- Extrapolating further on his chain of assumptions, he then multiplied the "gap time" by his estimated transfer rate and speculated that there were 19 gigs in his hypothetical batch and that 90% of the files in that batch were not included in the archive.
If Binney and his team couldn't replicate the speed, they can email me and I'll do it for them with two VPSes from two popular ISPs, in datacenters that are a couple thousand miles away from one another.
edit on 2017-11-9 by theantediluvian because: (no reason given)
Unfortunately, it doesn't matter what facts you throw at a thread like this. They've got the thread title, which is all most people will bother
reading.
Bias confirmed! Sweet! It's another day in paradise!
Bias confirmed! Sweet! It's another day in paradise!
a reply to: JBurns
How do you know that there was any batch transfer in the first place? Assuming that there was, how do you know where either of the computers involved were located?
Why is the conclusion of Russian hackers so difficult for you to consider? It appears to challenge some deeply held world view or something.
What exactly are you looking for? Honest question.
This notion that there's "no evidence" is wrong. Even assuming you throw out everything from CrowdStrike. The NSA likely has details for the connections for at least the first few hops for one thing. There are a number of ISPs involved that have likely given evidence to investigators for another.
And let's not forget that the FBI reached out to warn the DNC that they were being hacked. So clearly the FBI was observing some sort of activity.
As far as publicly available information, I've been talking about some of this for months and it always falls on deaf ears because people are emotionally attached to the theory that Russia had nothing to do with the hack because they want to believe there was a "fake Russia narrative" even as evidence of Russian meddling has been revealed elsewhere. Even as it's become clear that at the very least, certain elements of the Russian government sought to influence the Trump team in meetings that were lied about time and time again.
One entity that independently obtained evidence of the phishing campaign against the DNC and a number of others, was Dell SecureWorks. I've written one of two planned threads about it following a deep dive by the AP, working with Dell SecureWorks.
The evidence they collected, as the phishing campaign was ongoing, centers around the Bitly shortened links that were sent in the phishing emails. See with Bitly, it's not only possible to tell when a shortened link was created and by whom, but how many times it has been clicked and when. They store all of this for the purposes of analytics.
They can for instance see when the link in the Podesta phishing email was created and when John Podesta clicked it. If I get a chance today at some point, I'll put together the second thread with the details, including how they concluded that those involved were likely Russian.
Then there is the ThreatConnect passive DNS data. You can read about how that's collected here. They've got several blog posts detailing their research on their site. Here's one about the DCCC hack.
Hell, there's even evidence right in the email in the archives at Wikileaks, a fact I've pointed out a number of times. One instance would be the email from Alexandra Chalupa to Luis Miranda where she includes a screenshot of the warning from Yahoo about her mailbox being the target of state sponsored hackers.
There's also the emails in the Podesta archive which show him being phished and of course, they line up with the SecureWorks data from Bitly.
And how exactly did an "insider" steal John Podesta's email from his Gmail mailbox? That of course doesn't make any sense. Then you've got the DNC and DCCC hacks. Same insider was the source for both of those? Or was there just an insider when it comes to the DNC? And what about all this evidence of phishing that's *all over the place* — unrelated?
How do you dismiss all of that?
Why not break into smaller chunks and transmit more slowly to avoid detection? Wouldn't you want to maintain access?
How do you know that there was any batch transfer in the first place? Assuming that there was, how do you know where either of the computers involved were located?
Why is the conclusion of an insider job so difficult for you to consider? It appears to challenge some deeply held world view or something.
Why is the conclusion of Russian hackers so difficult for you to consider? It appears to challenge some deeply held world view or something.
All we have so far is innuendo, suggestion, accusation and summary judgment supporting that belief.
One piece of substantial evidence is all it would take.... ?
What exactly are you looking for? Honest question.
This notion that there's "no evidence" is wrong. Even assuming you throw out everything from CrowdStrike. The NSA likely has details for the connections for at least the first few hops for one thing. There are a number of ISPs involved that have likely given evidence to investigators for another.
And let's not forget that the FBI reached out to warn the DNC that they were being hacked. So clearly the FBI was observing some sort of activity.
As far as publicly available information, I've been talking about some of this for months and it always falls on deaf ears because people are emotionally attached to the theory that Russia had nothing to do with the hack because they want to believe there was a "fake Russia narrative" even as evidence of Russian meddling has been revealed elsewhere. Even as it's become clear that at the very least, certain elements of the Russian government sought to influence the Trump team in meetings that were lied about time and time again.
One entity that independently obtained evidence of the phishing campaign against the DNC and a number of others, was Dell SecureWorks. I've written one of two planned threads about it following a deep dive by the AP, working with Dell SecureWorks.
The evidence they collected, as the phishing campaign was ongoing, centers around the Bitly shortened links that were sent in the phishing emails. See with Bitly, it's not only possible to tell when a shortened link was created and by whom, but how many times it has been clicked and when. They store all of this for the purposes of analytics.
They can for instance see when the link in the Podesta phishing email was created and when John Podesta clicked it. If I get a chance today at some point, I'll put together the second thread with the details, including how they concluded that those involved were likely Russian.
Then there is the ThreatConnect passive DNS data. You can read about how that's collected here. They've got several blog posts detailing their research on their site. Here's one about the DCCC hack.
Hell, there's even evidence right in the email in the archives at Wikileaks, a fact I've pointed out a number of times. One instance would be the email from Alexandra Chalupa to Luis Miranda where she includes a screenshot of the warning from Yahoo about her mailbox being the target of state sponsored hackers.
There's also the emails in the Podesta archive which show him being phished and of course, they line up with the SecureWorks data from Bitly.
And how exactly did an "insider" steal John Podesta's email from his Gmail mailbox? That of course doesn't make any sense. Then you've got the DNC and DCCC hacks. Same insider was the source for both of those? Or was there just an insider when it comes to the DNC? And what about all this evidence of phishing that's *all over the place* — unrelated?
How do you dismiss all of that?
Oh, this is the guy trump had meet with Mike Pompeo. Trump is looking for some alternative facts to throw out to his base about the hacking. This
has got to be the most desperate attempt at distraction yet.
Plus it speaks of a sick mind.
This is trumps thinking...I have the most comprehensive investigative agencies on the planet at my finger tips..yeah I think ill get my info from a conspiracy theorist crack pot.
He's hiding something. He is so desperate to make people look the other way. But this...
Plus it speaks of a sick mind.
This is trumps thinking...I have the most comprehensive investigative agencies on the planet at my finger tips..yeah I think ill get my info from a conspiracy theorist crack pot.
He's hiding something. He is so desperate to make people look the other way. But this...
originally posted by: Dudemo5
Except if you can see the data was downloaded, you can see to where. This is complete nonsense.
The whole thing is utter nonsense. Trump probably promised this guy some cash reward to say this.
They will believe him and not every intelligence agency that looked at this.
One guy. He got it right, the rest..why they're all amateurs. Lol.
But they can't see how utterly stupid this sounds...
edit on 1192017 by Sillyolme because: (no reason given)
a reply to: theantediluvian
I think you have made some effective arguments. The truth is, I have never doubted there were Russian government intrusions into DNC systems...or GOP systems...or members of Congress...or nearly every business. And not just the Russians, but the Chinese, the North Koreans, our allies and half a dozen other nations all routinely muck about...not to mention their citizens without state sanction.
Whether the Russians were specifically responsible for the email dump is another matter altogether. For me, the Russian collusion narrative is just a convenient pretext capitalizing on the pre-existing porous nature of computer networks everywhere. I no longer trust the investigative bodies, as they have proven repeatedly to be vulnerable to political influence.
Frankly, short of evidence that votes were switched, I really don't get the point that we should all get exasperated that everyone is trying to influence somebody all of the time....even through deception.
It would be good for people to always remain mindful of that fact. No amount of legislating will ever change that. People should conduct themselves accordingly.
So back on topic..I have yet to see proof the Russian government is responsible for the email hack.
I think you have made some effective arguments. The truth is, I have never doubted there were Russian government intrusions into DNC systems...or GOP systems...or members of Congress...or nearly every business. And not just the Russians, but the Chinese, the North Koreans, our allies and half a dozen other nations all routinely muck about...not to mention their citizens without state sanction.
Whether the Russians were specifically responsible for the email dump is another matter altogether. For me, the Russian collusion narrative is just a convenient pretext capitalizing on the pre-existing porous nature of computer networks everywhere. I no longer trust the investigative bodies, as they have proven repeatedly to be vulnerable to political influence.
Frankly, short of evidence that votes were switched, I really don't get the point that we should all get exasperated that everyone is trying to influence somebody all of the time....even through deception.
It would be good for people to always remain mindful of that fact. No amount of legislating will ever change that. People should conduct themselves accordingly.
So back on topic..I have yet to see proof the Russian government is responsible for the email hack.
edit on 9-11-2017 by loam because: (no
reason given)
I wonder if anyone has considered the hack may have involved more than one operative? One remote hacker to gain access to protected folders on the
server and one on site operative with a flash drive to grab as much data as possible in a short window.
These methods are seen in tv and film fiction all the time, squint,geek,hacker in the support van, ninja,Rambo,ghost on site to extract the goodies.
Yes I know they are just entertainment but the method if not the tech is not unfeasible
These methods are seen in tv and film fiction all the time, squint,geek,hacker in the support van, ninja,Rambo,ghost on site to extract the goodies.
Yes I know they are just entertainment but the method if not the tech is not unfeasible
a reply to: JBurns
Back in October :
Burr: Russia probe will expose erroneous reporting
Back in October :
Burr: Russia probe will expose erroneous reporting
Intelligence Committee Chairman Richard Burr (R-N.C.) stopped short of endorsing Trump's Thursday morning call for a congressional investigation of the media. But Burr did predict that the final product of his panel's bipartisan inquiry into Moscow's disruption of the 2016 election would illustrate factual errors in some media reports on the issue.
"We're not going to investigate news organizations, but we will use the findings of our report to let the American people hold every news organization accountable for what they portrayed as fact, in many cases without sources — at least, no sources that would admit to it," Burr told POLITICO.
"And I think, when we finish our report, we will find that quite a few news organizations ran stories that were not factual," he added.
originally posted by: Dudemo5
originally posted by: JBurns
a reply to: Dudemo5
But he didn't say anything about a destination or source IP. What he does say is that data was copied in two separate bursts, 12 minutes apart totaling 87 seconds. 16GB is a lot of data to copy in such a short time, and it is unlikely they would do so with such speed over the network/WAN. Doing so would certainly raise red flags, so it would've been split into much smaller chunks and possibly transmitted as another type of data (for instance, HTTP requests/responses).
By "it" what do you mean? The Windows event log? Or /var/log? My point is that USB file transfer wouldn't be documented the same way as data going across a network. Anything having to do with an IP address would be separate from local file transfer disk I/O stuff. You might have a hardware address that is specific to that USB device, but it wouldn't have an assigned IP in any way.
Right. The disk I/O stuff is separate from the network activity. However, we have the destination IP address, so clearly there was an IP address associated with the breach through which logs show significant outbound traffic.
No, the USB drive does not have an IP address.
Where did you get your facts from? If there was an IP associated with this "hack" then it's location will be easy to pinpoint. I had not heard of any of that information being released. I guess when you post your link to the data, I will have learned something new. Thanks in advance for proving your statement.
Why don't we just sit back and let the indictments show the answer?
originally posted by: network dude
originally posted by: Dudemo5
originally posted by: JBurns
a reply to: Dudemo5
But he didn't say anything about a destination or source IP. What he does say is that data was copied in two separate bursts, 12 minutes apart totaling 87 seconds. 16GB is a lot of data to copy in such a short time, and it is unlikely they would do so with such speed over the network/WAN. Doing so would certainly raise red flags, so it would've been split into much smaller chunks and possibly transmitted as another type of data (for instance, HTTP requests/responses).
By "it" what do you mean? The Windows event log? Or /var/log? My point is that USB file transfer wouldn't be documented the same way as data going across a network. Anything having to do with an IP address would be separate from local file transfer disk I/O stuff. You might have a hardware address that is specific to that USB device, but it wouldn't have an assigned IP in any way.
Right. The disk I/O stuff is separate from the network activity. However, we have the destination IP address, so clearly there was an IP address associated with the breach through which logs show significant outbound traffic.
No, the USB drive does not have an IP address.
Where did you get your facts from? If there was an IP associated with this "hack" then it's location will be easy to pinpoint. I had not heard of any of that information being released. I guess when you post your link to the data, I will have learned something new. Thanks in advance for proving your statement.
From: time.com...
Fancy Bear... was sending command and control instructions from a server with an Internet Protocol (IP) address of 176.31.112.10.
a reply to: theantediluvian
Then I would have been mistaken in my use of this item in supporting my argument.
Thank you for the clarification.
They were files from the DCCC — from the DCCC hack. If you look at it again real quick, you'll notice that the mod times are all 2016-07-05 (6-7 weeks after the CrowdStrike announcement).
Then I would have been mistaken in my use of this item in supporting my argument.
Thank you for the clarification.
originally posted by: Dudemo5
originally posted by: network dude
originally posted by: Dudemo5
originally posted by: JBurns
a reply to: Dudemo5
But he didn't say anything about a destination or source IP. What he does say is that data was copied in two separate bursts, 12 minutes apart totaling 87 seconds. 16GB is a lot of data to copy in such a short time, and it is unlikely they would do so with such speed over the network/WAN. Doing so would certainly raise red flags, so it would've been split into much smaller chunks and possibly transmitted as another type of data (for instance, HTTP requests/responses).
By "it" what do you mean? The Windows event log? Or /var/log? My point is that USB file transfer wouldn't be documented the same way as data going across a network. Anything having to do with an IP address would be separate from local file transfer disk I/O stuff. You might have a hardware address that is specific to that USB device, but it wouldn't have an assigned IP in any way.
Right. The disk I/O stuff is separate from the network activity. However, we have the destination IP address, so clearly there was an IP address associated with the breach through which logs show significant outbound traffic.
No, the USB drive does not have an IP address.
Where did you get your facts from? If there was an IP associated with this "hack" then it's location will be easy to pinpoint. I had not heard of any of that information being released. I guess when you post your link to the data, I will have learned something new. Thanks in advance for proving your statement.
From: time.com...
Fancy Bear... was sending command and control instructions from a server with an Internet Protocol (IP) address of 176.31.112.10.
I see London I see France
new topics
-
Tucker Carlson UFOs are piloted by spiritual entities with bases under the ocean and the ground
Aliens and UFOs: 9 minutes ago -
Hello from burritocat
Introductions: 1 hours ago -
An Apology From the Dunderbeck Sausage Company
Music: 4 hours ago -
Tucker on Joe Rogan talking Kona Blue and UFOs
Aliens and UFOs: 4 hours ago -
Remember These Attacks When President Trump 2.0 Retribution-Justice Commences.
2024 Elections: 5 hours ago -
Predicting The Future: The Satanic Temple v. Florida
Conspiracies in Religions: 5 hours ago -
WF Killer Patents & Secret Science Vol. 1 | Free Energy & Anti-Gravity Cover-Ups
General Conspiracies: 7 hours ago -
Hurt my hip; should I go see a Doctor
General Chit Chat: 8 hours ago -
Israel attacking Iran again.
Middle East Issues: 9 hours ago -
Michigan school district cancels lesson on gender identity and pronouns after backlash
Education and Media: 9 hours ago
top topics
-
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness: 15 hours ago, 18 flags -
In an Historic First, In N Out Burger Permanently Closes a Location
Mainstream News: 17 hours ago, 16 flags -
Michigan school district cancels lesson on gender identity and pronouns after backlash
Education and Media: 9 hours ago, 9 flags -
Man sets himself on fire outside Donald Trump trial
Mainstream News: 15 hours ago, 9 flags -
Biden says little kids flip him the bird all the time.
Politicians & People: 15 hours ago, 9 flags -
WF Killer Patents & Secret Science Vol. 1 | Free Energy & Anti-Gravity Cover-Ups
General Conspiracies: 7 hours ago, 8 flags -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs: 12 hours ago, 6 flags -
Remember These Attacks When President Trump 2.0 Retribution-Justice Commences.
2024 Elections: 5 hours ago, 6 flags -
Israel attacking Iran again.
Middle East Issues: 9 hours ago, 5 flags -
Boston Dynamics say Farewell to Atlas
Science & Technology: 12 hours ago, 4 flags
active topics
-
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 54 • : peretc96 -
Israel attacking Iran again.
Middle East Issues • 41 • : FlyersFan -
OUT OF THE BLUE Chilling moment pulsating blue cigar-shaped UFO is filmed hovering over PHX AZ
Aliens and UFOs • 43 • : burritocat -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry • 177 • : andy06shake -
Tucker Carlson UFOs are piloted by spiritual entities with bases under the ocean and the ground
Aliens and UFOs • 0 • : FlyersFan -
Hello from burritocat
Introductions • 2 • : stosh64 -
Truth Social goes public, be careful not to lose your money
Mainstream News • 120 • : Astyanax -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 550 • : brewtiger123 -
I hate dreaming
Rant • 8 • : FlyersFan -
The New, New ATS Members Photos thread. Part 3.
Members • 1654 • : 19Bones79
