It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: pavil
a reply to: theantediluvian
Now were back to phishing for passwords.......ok. Them Ruskies are high tech.
We're not "back to phishing for passwords" as nothing has changed in the interim that we'd being going "back" to anything, has it?
Since the hacks were announced, it has always been maintained that there were two separate hacks. The picture that has been developing for me is that the Cozy Bear attack that began earlier and that it was Cozy Bear who actually gained access to the network as it was their implants found on the servers.
That said, all phishing is not the same. This phishing campaign had 4,700 unique targets in 5 countries (United States, Ukraine, Russia, Georgia and Syria), spanning at least 3 languages. The targets were in a wide range of sectors from government to military to journalists.
The selection of the targets and logistics of the campaign indicate both a high level of sophistication and that a group of more than a few people was involved.
Anyone who get's phished, deserves it. It's not that hard to figure out.
Cool. Except phishing works. It worked for me and my friends 25 years ago on IRC and it works today, probably millions of times a year. If the presentation is good, the means for capture transparent enough and a wide enough net is cast, some idiot will always fall for it.
It's not always about the idiot who gets phished either. If you run a business and despite your best efforts some clown working for you gets phished and internal emails get leaked out. Did you deserve that? What about your customers? If their emails get leaked, did they deserve that as well?
What if the leak impacts a whole nation? Does the entire nation "deserve it?"
a reply to: the2ofusr1
So no, you can't actually articulate anything in support of your false claim? Just more of your feelings. Thanks for your reasoned discussion!
So no, you can't actually articulate anything in support of your false claim? Just more of your feelings. Thanks for your reasoned discussion!
a reply to: theantediluvian
This article proves how podesta fell for a phishing scam on his Gmail acount. It has nothing to do with the DNC server being hacked. In fact in the article they state that it used 2 passwords and one wouldn't give them access. So you kind of proved the opisit of what you intended. You showed a phishing scam couldn't get access to the DNC server.
This article proves how podesta fell for a phishing scam on his Gmail acount. It has nothing to do with the DNC server being hacked. In fact in the article they state that it used 2 passwords and one wouldn't give them access. So you kind of proved the opisit of what you intended. You showed a phishing scam couldn't get access to the DNC server.
a reply to: JinMI
It's a game of numbers. Most people don't open spam email either but enough do that it makes it worth doing. Phishing works or nobody would do it. We send out a guide on phishing to employees a couple times a year. It helps. We use 3rd party filtering and endpoint security. On top of all that, all of our web traffic is proxied and most of our users are in ACL with only absolutely necessary hosts whitelisted.
There's always some exception. There's always some person who is letting their guard down or doesn't any better.
HTTPS just means that the connection is encrypted and therefore, you *hope* not being sniffed along the way. Hackers can obtain certs just like anyone else. It's simple, cheap, doesn't require any documentation, etc.
Depending on the target and the level of sophistication of the attack, the attackers will do things like register domains that at a glance will look even more legitimate. Consider an example like thisismyemailserver.com. An attacker could register thisismyemailsserver.com and at a glance, how many would be fooled? How about myoutdoorgrills.com vs myoutdoorgriIls.com? Did you notice that the first L is actually an uppercase I?
In this case, the shortened URLs all opened up to addresses in the "googlesettings.com" domain which is a domain that people may mistake for a legitimate Google domain even if they are paying attention.
Why I think that the SecureWorks research is significant is that it is independent of anything to do with CrowdStrike, the FBI, DNC, etc. Furthermore, it draws on data from yet another independent party, Bitly.
I've never been one to view Assange as being as credible as a lot of other people seem to think he is. I've pointed out on a number of occasions that Wikileaks has promoted misinfo/disinfo from their Twitter feed.
That said, it's possible that Assange received the emails via a cutout and doesn't know any better. It's also at least possible that the emails he received didn't originate from the hacks. Though, In my opinion, fairly unlikely.
It's a game of numbers. Most people don't open spam email either but enough do that it makes it worth doing. Phishing works or nobody would do it. We send out a guide on phishing to employees a couple times a year. It helps. We use 3rd party filtering and endpoint security. On top of all that, all of our web traffic is proxied and most of our users are in ACL with only absolutely necessary hosts whitelisted.
There's always some exception. There's always some person who is letting their guard down or doesn't any better.
Before clicking on a link, you can observe the bottom left corner of the screen to make sure where your going is what is being presented. Also httpS: domains for security. There's just the simple common sense of not putting too much faith in the system as well.
HTTPS just means that the connection is encrypted and therefore, you *hope* not being sniffed along the way. Hackers can obtain certs just like anyone else. It's simple, cheap, doesn't require any documentation, etc.
Depending on the target and the level of sophistication of the attack, the attackers will do things like register domains that at a glance will look even more legitimate. Consider an example like thisismyemailserver.com. An attacker could register thisismyemailsserver.com and at a glance, how many would be fooled? How about myoutdoorgrills.com vs myoutdoorgriIls.com? Did you notice that the first L is actually an uppercase I?
In this case, the shortened URLs all opened up to addresses in the "googlesettings.com" domain which is a domain that people may mistake for a legitimate Google domain even if they are paying attention.
Aside from that, from the thread I did on CrowdStrike, I'm not sure we are being fed all of the information on what the FBI knew/knows or doesn't. In fact, there may be cause to say that they are having a few behind the scenes relations for all out plausible deniability.
Why I think that the SecureWorks research is significant is that it is independent of anything to do with CrowdStrike, the FBI, DNC, etc. Furthermore, it draws on data from yet another independent party, Bitly.
Also, this would make Assange a liar, no? Having stated multiple times that the leaks didn't come from Russia. Now, if that is true, then Wikileaks integrity is shot, over and done.
I've never been one to view Assange as being as credible as a lot of other people seem to think he is. I've pointed out on a number of occasions that Wikileaks has promoted misinfo/disinfo from their Twitter feed.
That said, it's possible that Assange received the emails via a cutout and doesn't know any better. It's also at least possible that the emails he received didn't originate from the hacks. Though, In my opinion, fairly unlikely.
a reply to: theantediluvian
I'm not even close to knowledgeable, but it's also been repeatedly stated that both the CIA and NSA had the ability to hack and leave a false trail pointing to anyone they wish with the purpose of misdirection or placing a false flag-like incident.
Is this true? Could it mitigate your thread?
Really. Just an ignorant and curious question.
I'm not even close to knowledgeable, but it's also been repeatedly stated that both the CIA and NSA had the ability to hack and leave a false trail pointing to anyone they wish with the purpose of misdirection or placing a false flag-like incident.
Is this true? Could it mitigate your thread?
Really. Just an ignorant and curious question.
edit on 4-11-2017 by nwtrucker because: (no reason given)
a reply to: theantediluvian
You didn't mention in who's reality
A legend in your own mind ?
The reality is that I've been continuously ahead of the curve.
You didn't mention in who's reality
A legend in your own mind ?
a reply to: dragonridr
Not at all. For one, it only said that the hillaryclinton.com email accounts used two-factor authentication. It didn't say anything about the DNC emails. Two-factor authentication isn't bulletproof either but that's a different conversation and probably not relevant to this topic.
There were multiple Gmail accounts phished. It's possible that DNC staffers used the same password for domain accounts (assuming the DNC uses Windows servers) as for the Gmail. It's also possible that domain passwords or passwords for other email accounts were emailed to the Gmail accounts. Which would be extremely bad form but then again, we know that Podesta's CAP domain password was sent via email. That would open up many lines of attack if their computers were remotely accessible.
It's also possible that Fancy Bear itself never got into the network proper. As I mentioned in an earlier post, the implants from the network are associated with another threat actor, "Cozy Bear." I think that seems likely to be the case.
It does however give some more details to Podesta being phished. I wonder who will be the first to argue that Seth Rich phished Podesta and others.
This article proves how podesta fell for a phishing scam on his Gmail acount. It has nothing to do with the DNC server being hacked. In fact in the article they state that it used 2 passwords and one wouldn't give them access. So you kind of proved the opisit of what you intended. You showed a phishing scam couldn't get access to the DNC server.
Not at all. For one, it only said that the hillaryclinton.com email accounts used two-factor authentication. It didn't say anything about the DNC emails. Two-factor authentication isn't bulletproof either but that's a different conversation and probably not relevant to this topic.
There were multiple Gmail accounts phished. It's possible that DNC staffers used the same password for domain accounts (assuming the DNC uses Windows servers) as for the Gmail. It's also possible that domain passwords or passwords for other email accounts were emailed to the Gmail accounts. Which would be extremely bad form but then again, we know that Podesta's CAP domain password was sent via email. That would open up many lines of attack if their computers were remotely accessible.
It's also possible that Fancy Bear itself never got into the network proper. As I mentioned in an earlier post, the implants from the network are associated with another threat actor, "Cozy Bear." I think that seems likely to be the case.
It does however give some more details to Podesta being phished. I wonder who will be the first to argue that Seth Rich phished Podesta and others.
originally posted by: IgnoranceIsntBlisss
a reply to: odzeandennz
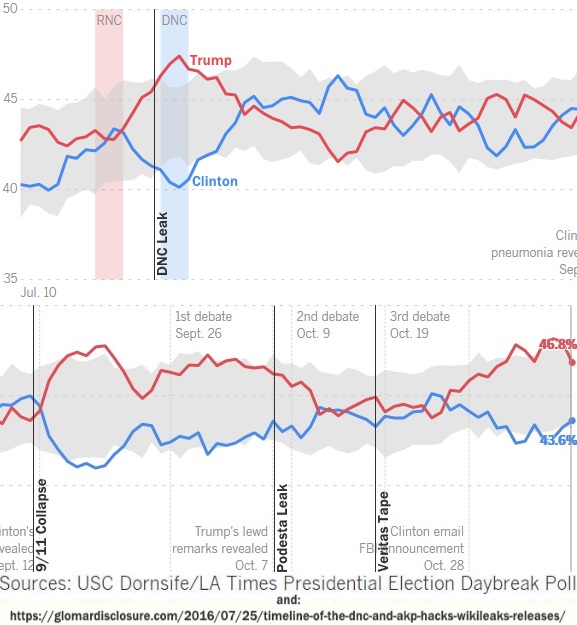
Leaks / Hacks / Tapes didnt seem to sway the DNC base in the slightest, neither qualitatively or quantitatively:
I was wondering why that graph seemed so off. It is that LA Times poll that polls mostly only conservatives and thus has a known bias. Still useful for gauging conservative support for Trump.
a reply to: theantediluvian
Two facor authentication means not only do they need a password but the device they are on has to be authorized on the server. Not impossible to get around if you hack into some ones device. But a phishing scam isnt going to pull it off. Unless the administrator was an idiot he should not have authorized any device until speaking to the user. So now to access clintons or DNC server you need to use an authorized device.
There is really only three ways to hack in to a server
Default settings– These settings such as default user id and passwords can be easily guessed by the attackers. Default settings might also allow performing certain tasks such as running commands on the server which can be exploited.
Misconfigurationof operating systems and networks – certain configuration such as allowing users to execute commands on the server can be dangerous if the user does not have a good password.
Bugs in the operating system and web servers– discovered bugs in the operating system or web server software can also be exploited to gain unauthorized access to the system.
A phishing scam lets you read emails but you still cant access the servers.
Ps if a hacker is good he willleave behind zero evidence as to his identity by using several proxy servers. Meaning you cant identify any real hackers just scammers
Two facor authentication means not only do they need a password but the device they are on has to be authorized on the server. Not impossible to get around if you hack into some ones device. But a phishing scam isnt going to pull it off. Unless the administrator was an idiot he should not have authorized any device until speaking to the user. So now to access clintons or DNC server you need to use an authorized device.
There is really only three ways to hack in to a server
Default settings– These settings such as default user id and passwords can be easily guessed by the attackers. Default settings might also allow performing certain tasks such as running commands on the server which can be exploited.
Misconfigurationof operating systems and networks – certain configuration such as allowing users to execute commands on the server can be dangerous if the user does not have a good password.
Bugs in the operating system and web servers– discovered bugs in the operating system or web server software can also be exploited to gain unauthorized access to the system.
A phishing scam lets you read emails but you still cant access the servers.
Ps if a hacker is good he willleave behind zero evidence as to his identity by using several proxy servers. Meaning you cant identify any real hackers just scammers
edit on 11/4/17 by dragonridr because: (no reason given)
a reply to: nwtrucker
The CIA/NSA/etc certainly have the capability to deflect attribution to another entity, including a foreign country. What you're referring to specifically is UMBRAGE. Essentially a library of tools in use by others which could be employed to throw off attribution.
But's just that one program. That sort of capability isn't confined strictly to the US or any state actor. There's a number of security teams that have their own collections of tools found in the wild. And that would be just an attempt to frame another group using/leaving behind tools associated with that group.
It could be argued in the case of the evidence provided by CrowdStrike for instance. It's at least possible that the implants they claimed to have discovered on DNC servers are actually something they found somewhere else and they are trying to pass them off as being involved in a Cozy Bear hack that wasn't.
Though, analysis of the implants they provided to other researchers indicated development beyond earlier versions of the same tools found in other hacks. Then again, that could just be them going the extra mile.
However, what CrowdStrike couldn't have faked is the Bitly data. Not unless Bitly was compromised or complicit. And even if that were the case, SecureWorks had been monitoring it for months so unless they're complicit in a conspiracy, that would mean that the data predates not only any involvement by CrowdStrike but goes back months before the most recent email stolen.
And that's just Dell SecureWorks and Bitly and this one thread of evidence for one part of what's alleged. What was the FBI tracking? What about evidence from ThreatConnect monitoring DNS requests? All of the ISPs cited as having been involved?
So at the very least, it seems implausible that there was no phishing, no hack, etc.
The question is then, who was behind it? Looking at what's available, it points to Russia. Could the USIC have been behind it and have framed Russia? Which agency/agencies would have done it and to what end? An extremely thorough, very lengthy false flag? Could it have been China camouflaging themselves as Russia? I suppose but there's no specific evidence pointing the China, NK, Israel or any of the other whattabouts.
Then we've got the context of everything else from the election that has come to light and points to Russia. Perhaps it's all a grand conspiracy involving dozens of government agencies and companies from lowly ISPs to Facebook and Twitter and hundreds or thousands of agents and employees.
If that's the case, we're so totally and inescapably f'd that it really doesn't matter.
The CIA/NSA/etc certainly have the capability to deflect attribution to another entity, including a foreign country. What you're referring to specifically is UMBRAGE. Essentially a library of tools in use by others which could be employed to throw off attribution.
But's just that one program. That sort of capability isn't confined strictly to the US or any state actor. There's a number of security teams that have their own collections of tools found in the wild. And that would be just an attempt to frame another group using/leaving behind tools associated with that group.
It could be argued in the case of the evidence provided by CrowdStrike for instance. It's at least possible that the implants they claimed to have discovered on DNC servers are actually something they found somewhere else and they are trying to pass them off as being involved in a Cozy Bear hack that wasn't.
Though, analysis of the implants they provided to other researchers indicated development beyond earlier versions of the same tools found in other hacks. Then again, that could just be them going the extra mile.
However, what CrowdStrike couldn't have faked is the Bitly data. Not unless Bitly was compromised or complicit. And even if that were the case, SecureWorks had been monitoring it for months so unless they're complicit in a conspiracy, that would mean that the data predates not only any involvement by CrowdStrike but goes back months before the most recent email stolen.
And that's just Dell SecureWorks and Bitly and this one thread of evidence for one part of what's alleged. What was the FBI tracking? What about evidence from ThreatConnect monitoring DNS requests? All of the ISPs cited as having been involved?
So at the very least, it seems implausible that there was no phishing, no hack, etc.
The question is then, who was behind it? Looking at what's available, it points to Russia. Could the USIC have been behind it and have framed Russia? Which agency/agencies would have done it and to what end? An extremely thorough, very lengthy false flag? Could it have been China camouflaging themselves as Russia? I suppose but there's no specific evidence pointing the China, NK, Israel or any of the other whattabouts.
Then we've got the context of everything else from the election that has come to light and points to Russia. Perhaps it's all a grand conspiracy involving dozens of government agencies and companies from lowly ISPs to Facebook and Twitter and hundreds or thousands of agents and employees.
If that's the case, we're so totally and inescapably f'd that it really doesn't matter.
a reply to: theantediluvian
I read the report that CrowdStrike put out. I solicit reports like this for companies I do work for and if ever I received a report like that I would refuse payment. Total hogwash. What makes more sense is the investigation from The Forensicator. The conclusion it reaches that this was an inside job are indisputable.
For your perusal: The Forensicator
An 87 second download @22.7 MegaBYTES/sec would not have been possible by a remote hacker with a huge pipe to the Internet. Case closed IMO
I read the report that CrowdStrike put out. I solicit reports like this for companies I do work for and if ever I received a report like that I would refuse payment. Total hogwash. What makes more sense is the investigation from The Forensicator. The conclusion it reaches that this was an inside job are indisputable.
For your perusal: The Forensicator
An 87 second download @22.7 MegaBYTES/sec would not have been possible by a remote hacker with a huge pipe to the Internet. Case closed IMO
a reply to: theantediluvian
I fell asleep twice trying to understand your technical dissertation...LOL.
I get what your saying, of a sort. Possible, but at this juncture? Impossible to say?
Carry on, sir, and thank you for the response.
I fell asleep twice trying to understand your technical dissertation...LOL.
I get what your saying, of a sort. Possible, but at this juncture? Impossible to say?
Carry on, sir, and thank you for the response.
edit on 4-11-2017 by nwtrucker because: (no reason given)
originally posted by: theantediluvian
a reply to: nwtrucker
If that's the case, we're so totally and inescapably f'd that it really doesn't matter.
You're getting warmer.
Your registration date says 2013, come out of the isolation suit already. The game is deeper than the bi-polar field you like to play on.
a reply to: theantediluvian
That's the case.
If that's the case, we're so totally and inescapably f'd that it really doesn't matter.
That's the case.
With everything coming out with Donna Brazile, I wonder who was on the inside of the DNC.
I believe there to be a spy within the DNC also. Third, or fourth man scenario. Maybe Clinton herself. It would have to be someone fairly high in the organization. I always wondered why Hilary Bleached bit and scoured, broke into pieces her computers. That would explain a lot about Hilary being in cahoots with Russia, with the Uranium Deal and all. Russian payments to her foundation was outrageously high.
I believe there to be a spy within the DNC also. Third, or fourth man scenario. Maybe Clinton herself. It would have to be someone fairly high in the organization. I always wondered why Hilary Bleached bit and scoured, broke into pieces her computers. That would explain a lot about Hilary being in cahoots with Russia, with the Uranium Deal and all. Russian payments to her foundation was outrageously high.
a reply to: Mike.Ockizard
I skimmed this when it came out but I hadn't something going on and I never got around to re-reading it and posting about it. I'm going over it now and I'll share my thoughts.
Lone wolf pretty much out the window for the phishing campaign. 4,700 specific targets in 5 countries, speaking 3 or more languages? These weren't just random targets mind you.
From another article in the series:
That would be one hell of a lone wolf in terms of his knowledge of useful targets in multiple countries, his expectation of being able to make use of emails in multiple languages, and interests perfectly aligned with the Kremlin. A lone wolf throwing a very large and very specific net. Possible? Sure. Probable? Not so much.
I'm actually surprised that you find this compelling? It's a poorly structured, largely incomprehensible chaining of assumptions. Let's just address what people keep talking about, shall we? This 22 MB/s business.
Before we proceed though, I would note that the date of these mod times is 2016-07-05 — July 5th? That's almost a month after CrowdStrike had given the hackers the boot. Please tell me I'm not the first to notice this. That's also weeks after Assange claimed to have emails that would hurt Clinton and weeks after "Guccifer 2.0" had already been releasing documents?
So why would anyone believe that any part of these file modifications occurred on DNC computers in the first place? That's nonsensical. And if it wasn't a hacker but rather a DNC staffer who just decided to risk his/her career weeks after a hack to steal a bunch of data, why wouldn't he get the latest? What's the date of the most recent emails? End of May?
And really? Cygwin? What maverick of forensics is using Cygwin? Jesus. I digress though, I was going to address the 22 MB/s thing.
That's not that fast. That's like 176 Mb/s. Let's pretend that the date makes sense and just for the sake of argument go by this rather unsupported notion that we've got files copied from the DNC to somewhere remote.
* Where were the DNC servers located? On site in the offices? Or were they hosted somewhere?
* What kind of connection did the DNC have?
* How do we know that point B was local to the hacker and not an interim server?
Oh wait, is that even what he's actually claiming? It seems like what he's ACTUALLY claiming is that the files were copied across a LAN on 7/5. So what about a scenario where they were compiled locally and then exfiltrated using an implant which preserves the mod times?
What exactly is the author saying in this mess here?
That doesn't even make sense. If you subtract the the most recent mod time from the earliest, you get a span. Okay. That doesn't necessarily mean there was a batch at all. There's no file time to indicate a "start" for the theoretical start time.
So the first assumption is that the span represents a batch file transfer.
The problem there of course is that that if the files were copied in a single batch, the time between last mod times doesn't make sense for the theory because the start of each transfer would fall within a second of the last mod of the file transferred immediately before.
So the obvious solution is to then invent theoretical missing files to fill in the gaps? And how would one determine the size and number of files in the gaps?
What did the author do? Subtract the gaps from the total time and arrive at what he presumed to be the length of time to transfer the files remaining from the assumed file transfer (the files actually present in the archive) and then from there estimate a total transfer size to account for the span between oldest/newest mod times?
How could you rule out somebody just scrolling through a directory and copying what they wanted? Hold on, the author allows for just that possibility:
I certainly wouldn't point to this as any reason to say "case closed." It's not even remotely definitive. Relies on a TON of assumptions and ignores more plausible scenarios. Also, there's that 7/5 date thing.
Maybe I missed something that you saw?
I skimmed this when it came out but I hadn't something going on and I never got around to re-reading it and posting about it. I'm going over it now and I'll share my thoughts.
Forensicator viewed Guccifer 2 as a lone wolf hacker who lived somewhere in Eastern Europe or Russia; he used a Russian-aligned VPN service to mask his IP address.
Lone wolf pretty much out the window for the phishing campaign. 4,700 specific targets in 5 countries, speaking 3 or more languages? These weren't just random targets mind you.
From another article in the series:
In the United States, which was Russia’s Cold War rival, Fancy Bear tried to pry open at least 573 inboxes belonging to those in the top echelons of the country’s diplomatic and security services: then-Secretary of State John Kerry, former Secretary of State Colin Powell, then-NATO Supreme Commander, U.S. Air Force Gen. Philip Breedlove, and one of his predecessors, U.S. Army Gen. Wesley Clark.
The list skewed toward workers for defense contractors such as Boeing, Raytheon and Lockheed Martin or senior intelligence figures, prominent Russia watchers and — especially — Democrats. More than 130 party workers, campaign staffers and supporters of the party were targeted, including Podesta and other members of Clinton’s inner circle.
The AP also found a handful of Republican targets.
In Ukraine, which is fighting a grinding war against Russia-backed separatists, Fancy Bear attempted to break into at least 545 accounts, including those of President Petro Poroshenko and his son Alexei, half a dozen current and former ministers such as Interior Minister Arsen Avakov and as many as two dozen current and former lawmakers.
The list includes Serhiy Leshchenko, an opposition parliamentarian who helped uncover the off-the-books payments allegedly made to Trump campaign chairman Paul Manafort — whose indictment was unsealed Monday in Washington.
In Russia, Fancy Bear focused on government opponents and dozens of journalists. Among the targets were oil tycoon-turned-Kremlin foe Mikhail Khodorkovsky, who spent a decade in prison and now lives in exile, and Pussy Riot’s Maria Alekhina. Along with them were 100 more civil society figures, including anti-corruption campaigner Alexei Navalny and his lieutenants.
That would be one hell of a lone wolf in terms of his knowledge of useful targets in multiple countries, his expectation of being able to make use of emails in multiple languages, and interests perfectly aligned with the Kremlin. A lone wolf throwing a very large and very specific net. Possible? Sure. Probable? Not so much.
I'm actually surprised that you find this compelling? It's a poorly structured, largely incomprehensible chaining of assumptions. Let's just address what people keep talking about, shall we? This 22 MB/s business.
Before we proceed though, I would note that the date of these mod times is 2016-07-05 — July 5th? That's almost a month after CrowdStrike had given the hackers the boot. Please tell me I'm not the first to notice this. That's also weeks after Assange claimed to have emails that would hurt Clinton and weeks after "Guccifer 2.0" had already been releasing documents?
So why would anyone believe that any part of these file modifications occurred on DNC computers in the first place? That's nonsensical. And if it wasn't a hacker but rather a DNC staffer who just decided to risk his/her career weeks after a hack to steal a bunch of data, why wouldn't he get the latest? What's the date of the most recent emails? End of May?
And really? Cygwin? What maverick of forensics is using Cygwin? Jesus. I digress though, I was going to address the 22 MB/s thing.
That's not that fast. That's like 176 Mb/s. Let's pretend that the date makes sense and just for the sake of argument go by this rather unsupported notion that we've got files copied from the DNC to somewhere remote.
* Where were the DNC servers located? On site in the offices? Or were they hosted somewhere?
* What kind of connection did the DNC have?
* How do we know that point B was local to the hacker and not an interim server?
Oh wait, is that even what he's actually claiming? It seems like what he's ACTUALLY claiming is that the files were copied across a LAN on 7/5. So what about a scenario where they were compiled locally and then exfiltrated using an implant which preserves the mod times?
What exactly is the author saying in this mess here?
Conclusion 5: The lengthy time gaps suggest that many additional files were initially copied en masse and that only a small subset of that collection was selected for inclusion into the final 7zip archive file (that was subsequently published by Guccifer 2). Given the calculations above, if 1.98 GB were copied at a rate of 22.6 MB/s and all the time gaps were attributed to additional file copying then approximately 19.3 GB in total were initially copied. In this hypothetical scenario, the 7zip archive represents only about 10% of the total amount of data that was initially collected.
That doesn't even make sense. If you subtract the the most recent mod time from the earliest, you get a span. Okay. That doesn't necessarily mean there was a batch at all. There's no file time to indicate a "start" for the theoretical start time.
So the first assumption is that the span represents a batch file transfer.
The problem there of course is that that if the files were copied in a single batch, the time between last mod times doesn't make sense for the theory because the start of each transfer would fall within a second of the last mod of the file transferred immediately before.
So the obvious solution is to then invent theoretical missing files to fill in the gaps? And how would one determine the size and number of files in the gaps?
What did the author do? Subtract the gaps from the total time and arrive at what he presumed to be the length of time to transfer the files remaining from the assumed file transfer (the files actually present in the archive) and then from there estimate a total transfer size to account for the span between oldest/newest mod times?
How could you rule out somebody just scrolling through a directory and copying what they wanted? Hold on, the author allows for just that possibility:
Initially when this data was analyzed, the “time gaps” were attributed to “think time”, where it was assumed that the individual who collected the files would copy the files in small batches and in between each batch would need some “think time” to find or decide on the next batch to copy. This may be an equally valid way to explain the presence of time gaps at various junctures in the top-level files and folders. However, in this analysis we will assume that a much larger collection of files were initially copied on 7/5/2016; the files in the final .7z file (the subject of this analysis) represent only a small percentage of all the files that were initially collected.
I certainly wouldn't point to this as any reason to say "case closed." It's not even remotely definitive. Relies on a TON of assumptions and ignores more plausible scenarios. Also, there's that 7/5 date thing.
Maybe I missed something that you saw?
edit on 2017-11-5 by theantediluvian because: (no reason given)
a reply to: dragonridr
Clearly you didn't read my response very carefully. It only ever mentions two-factor auth in terms of the hillaryclinton.com email addresses from the first round. No where is it said the the DNC used two-factor auth. You're hung up on that for no real reason.
The next bit bolsters my initial suspicion that you didn't read my response and instead are just talking to yourself. I literally told you how phishing can lead to access to a computer. This part?
25 years ago as kids on IRC, my friends and I used to phish university accounts all day long. We'd nick collide the help bots, take over their nicks and respond to help requests with our own scripted message, asking victims to supply their passwords to continue.
Then with user@host and password in hand, we'd telnet in. Back then, passwd files weren't shadowed so you'd grab the passwd file and run it through Crack or similar against your k-rad custom dictionary file. In the meantime, start running through the local exploits which were both more plentiful and less likely to be patched, look for misconfigured permissions, etc. We literally got into and rooted hundreds of boxes this way.
From there, we'd patch the servers (this is before and just as rootkits became a thing). Some of the patching was to avoid detection and some to harvest even more accounts for remote machines and then there were sniffers which were super handy in a time when hubs were a thing and most traffic wasn't encrypted.
That's just nonsense. Hackers get caught in the act all the time. It's like some crap from the movies where you sit around with your friends and "hack the Gibson" in some epic minutes long battle for control. Most of the time, you get in and you stay in as long as you can go undiscovered.
I think you've been watching too many movies/TV.
Two facor authentication means not only do they need a password but the device they are on has to be authorized on the server. Not impossible to get around if you hack into some ones device. But a phishing scam isnt going to pull it off. Unless the administrator was an idiot he should not have authorized any device until speaking to the user. So now to access clintons or DNC server you need to use an authorized device.
Clearly you didn't read my response very carefully. It only ever mentions two-factor auth in terms of the hillaryclinton.com email addresses from the first round. No where is it said the the DNC used two-factor auth. You're hung up on that for no real reason.
The next bit bolsters my initial suspicion that you didn't read my response and instead are just talking to yourself. I literally told you how phishing can lead to access to a computer. This part?
There were multiple Gmail accounts phished. It's possible that DNC staffers used the same password for domain accounts (assuming the DNC uses Windows servers) as for the Gmail. It's also possible that domain passwords or passwords for other email accounts were emailed to the Gmail accounts. Which would be extremely bad form but then again, we know that Podesta's CAP domain password was sent via email. That would open up many lines of attack if their computers were remotely accessible.
25 years ago as kids on IRC, my friends and I used to phish university accounts all day long. We'd nick collide the help bots, take over their nicks and respond to help requests with our own scripted message, asking victims to supply their passwords to continue.
Then with user@host and password in hand, we'd telnet in. Back then, passwd files weren't shadowed so you'd grab the passwd file and run it through Crack or similar against your k-rad custom dictionary file. In the meantime, start running through the local exploits which were both more plentiful and less likely to be patched, look for misconfigured permissions, etc. We literally got into and rooted hundreds of boxes this way.
From there, we'd patch the servers (this is before and just as rootkits became a thing). Some of the patching was to avoid detection and some to harvest even more accounts for remote machines and then there were sniffers which were super handy in a time when hubs were a thing and most traffic wasn't encrypted.
Ps if a hacker is good he willleave behind zero evidence as to his identity by using several proxy servers. Meaning you cant identify any real hackers just scammers
That's just nonsense. Hackers get caught in the act all the time. It's like some crap from the movies where you sit around with your friends and "hack the Gibson" in some epic minutes long battle for control. Most of the time, you get in and you stay in as long as you can go undiscovered.
I think you've been watching too many movies/TV.
a reply to: theantediluvian
Your confusing finding out a hacker in your system with trying to ID a hacker. A hacker will attempt to avoid detection by IDS systems (INTRUSION DETECTION SYSTEMS). There is two ways these can work they can look for specific signatures on a network or monitor traffic for abnormal traffic. Thanks to cloudstrike we know the DNC server was set up to look for signatures. So they are looking for the software installed. Problem is that's easy to hide from the server you can break it up in to packets or When SSL, SSH, and IPSec encrypted tunnels are established they prevent the NIDS from being able to interpret the packet’s true payload.
Buy let's say they are detected the administrator will get an alert and lock it down. But no where in there is the ability to ID the hacker. You will get an address for the attack but it will be a proxy server. And even if you get past that one and get another address that will be a proxy server as well.
So how can you identify the hacker If caught by what software they attempted to use problem is that software is always made available by its creators on hacker sites. Because the more people that use the lower your risk of being Identified. This is why I think the NSS just recently said there hacking kit was hacked odd yes? So back to this what we know according to cloud strike it was Russian software used with a Russian keyboard. Problem is there is thousands of hackers that would meet that description with zero contact with Russia.
So we can assume just because the hack came from Germany using a Russian keyboard means anything at all considering most of the hackers in the world operate out of eastern Europe and of course China. If you like conspiracies a major hot spot is Ukraine to tie it into manafort.
So your can indeed detect an intrusion if the hacker makes a mistake but you can never truly tell who did it.
Your confusing finding out a hacker in your system with trying to ID a hacker. A hacker will attempt to avoid detection by IDS systems (INTRUSION DETECTION SYSTEMS). There is two ways these can work they can look for specific signatures on a network or monitor traffic for abnormal traffic. Thanks to cloudstrike we know the DNC server was set up to look for signatures. So they are looking for the software installed. Problem is that's easy to hide from the server you can break it up in to packets or When SSL, SSH, and IPSec encrypted tunnels are established they prevent the NIDS from being able to interpret the packet’s true payload.
Buy let's say they are detected the administrator will get an alert and lock it down. But no where in there is the ability to ID the hacker. You will get an address for the attack but it will be a proxy server. And even if you get past that one and get another address that will be a proxy server as well.
So how can you identify the hacker If caught by what software they attempted to use problem is that software is always made available by its creators on hacker sites. Because the more people that use the lower your risk of being Identified. This is why I think the NSS just recently said there hacking kit was hacked odd yes? So back to this what we know according to cloud strike it was Russian software used with a Russian keyboard. Problem is there is thousands of hackers that would meet that description with zero contact with Russia.
So we can assume just because the hack came from Germany using a Russian keyboard means anything at all considering most of the hackers in the world operate out of eastern Europe and of course China. If you like conspiracies a major hot spot is Ukraine to tie it into manafort.
So your can indeed detect an intrusion if the hacker makes a mistake but you can never truly tell who did it.
new topics
-
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 20 minutes ago -
This is our Story
General Entertainment: 3 hours ago -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 5 hours ago -
Ode to Artemis
General Chit Chat: 6 hours ago -
Ditching physical money
History: 9 hours ago -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 9 hours ago -
Don't take advantage of people just because it seems easy it will backfire
Rant: 10 hours ago -
VirginOfGrand says hello
Introductions: 10 hours ago -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 11 hours ago
top topics
-
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media: 13 hours ago, 14 flags -
Police clash with St George’s Day protesters at central London rally
Social Issues and Civil Unrest: 16 hours ago, 10 flags -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 5 hours ago, 10 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 17 hours ago, 7 flags -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 11 hours ago, 6 flags -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 9 hours ago, 5 flags -
Ditching physical money
History: 9 hours ago, 4 flags -
Don't take advantage of people just because it seems easy it will backfire
Rant: 10 hours ago, 4 flags -
God lived as a Devil Dog.
Short Stories: 15 hours ago, 3 flags -
VirginOfGrand says hello
Introductions: 10 hours ago, 2 flags
active topics
-
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 45 • : burritocat -
Ditching physical money
History • 14 • : DerBeobachter2 -
British TV Presenter Refuses To Use Guest's Preferred Pronouns
Education and Media • 129 • : KrustyKrab -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 1 • : burritocat -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 27 • : Consvoli -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 637 • : burritocat -
The Reality of the Laser
Military Projects • 33 • : ADVISOR -
Terrifying Encounters With The Black Eyed Kids
Paranormal Studies • 71 • : FlyersFan -
This is our Story
General Entertainment • 1 • : Encia22 -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs • 17 • : vance2