It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
5
share:
bitcoinist.com...
Police say it was a criminal network, used by criminals for criminal business.
Blackberry devices cost $1,500 per piece and you could only PGP text messaging with it. Mike was removed.
Moreover Dutch TV News (NIEUWSUUR) said that the Police could also decrypt the millions of messages on the busted servers in Canada and The Netherlands, strange because when PGP has been implemented properly the 20,000 private keys are only on the devices not on the servers. Could be bluff.
#bigbrothheriswatchingyou cannot think there must be total awareness / total control, because this would destroy doing business completely and mission critical info could easily fall in the wrong hands, could be sold to the highest bidder by police moles, secret service moles or mole cells (the secret service mafia inside the secret service, even unknown to decent hardworking honest secret service employees)
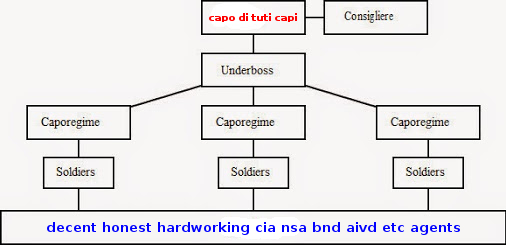
(NB: capo-di-tutti-capi is mafia godfather)
Lets for argument sake say, that the Dutch Police could indeed decrypt the millions of messages send in this PGP network, then the text messages are not worth anything as evidence in court, who says that rival cyber criminals, or police or secret services mole cells or the alleged (this PGP network) criminals it self did not tamper with the evidence on behave of the highest bidder?
The Blackberry devices seem to be save for man-on-client malware, that means that #bigbrotheriswatchingyou cannot look over you shoulder as it were while your typing the message (which is not yet encrypted).
PS: I don't think that all this PGP network users are criminals, could also be honest business men that do not want that competitors know of their mission critical info
Police say it was a criminal network, used by criminals for criminal business.
Blackberry devices cost $1,500 per piece and you could only PGP text messaging with it. Mike was removed.
Moreover Dutch TV News (NIEUWSUUR) said that the Police could also decrypt the millions of messages on the busted servers in Canada and The Netherlands, strange because when PGP has been implemented properly the 20,000 private keys are only on the devices not on the servers. Could be bluff.
#bigbrothheriswatchingyou cannot think there must be total awareness / total control, because this would destroy doing business completely and mission critical info could easily fall in the wrong hands, could be sold to the highest bidder by police moles, secret service moles or mole cells (the secret service mafia inside the secret service, even unknown to decent hardworking honest secret service employees)

(NB: capo-di-tutti-capi is mafia godfather)
Lets for argument sake say, that the Dutch Police could indeed decrypt the millions of messages send in this PGP network, then the text messages are not worth anything as evidence in court, who says that rival cyber criminals, or police or secret services mole cells or the alleged (this PGP network) criminals it self did not tamper with the evidence on behave of the highest bidder?
The Blackberry devices seem to be save for man-on-client malware, that means that #bigbrotheriswatchingyou cannot look over you shoulder as it were while your typing the message (which is not yet encrypted).
PS: I don't think that all this PGP network users are criminals, could also be honest business men that do not want that competitors know of their mission critical info
a reply to: galien8
This was your response when someone asked you for sources when you showed the same capo di tuti in that other thread
I wont bother even trying to understand your premise, because you would then respond with your other famous insight
capo di stonzo
This was your response when someone asked you for sources when you showed the same capo di tuti in that other thread
Its an hypothesis inspired by dream theme anagrams.
I wont bother even trying to understand your premise, because you would then respond with your other famous insight
because we suffer overpopulation, all major problems in the world are overpopulation problems.
capo di stonzo
originally posted by: TheConstruKctionofLight
capo di stonzo
ado coon spitz
ado spitz coon
ado stoop zinc
ado zinc stoop
catnip sod zoo
catnip zoo sod
codon is topaz
codon topaz is
coin sod topaz
coin stood zap
coin topaz sod
coin zap stood
coon ado spitz
coon spitz ado
disco no topaz
disco on topaz
disco onto zap
disco pant zoo
disco topaz no
disco topaz on
disco zap onto
disco zoo pant
do scion topaz
do sonic topaz
do topaz scion
do topaz sonic
dopant sic zoo
dopant zoo sic
icon sod topaz
icon stood zap
icon topaz sod
icon zap stood
is codon topaz
is topaz codon
no disco topaz
no post zodiac
no spot zodiac
no stop zodiac
no topaz disco
no zodiac post
no zodiac spot
no zodiac stop
not sop zodiac
not zodiac sop
on disco topaz
on post zodiac
on spot zodiac
on stop zodiac
on topaz disco
on zodiac post
on zodiac spot
on zodiac stop
onto disco zap
onto zap disco
opt son zodiac
opt zodiac son
optic sand zoo
optic zoo sand
pant disco zoo
pant zoo disco
pont so zodiac
pont zodiac so
post no zodiac
post on zodiac
post zodiac no
post zodiac on
pot son zodiac
pot zodiac son
sand optic zoo
sand topic zoo
sand zoo optic
sand zoo topic
scion do topaz
scion topaz do
sic dopant zoo
sic zoo dopant
so pont zodiac
so zodiac pont
sod catnip zoo
sod coin topaz
sod icon topaz
sod topaz coin
sod topaz icon
sod zoo catnip
son opt zodiac
son pot zodiac
son top zodiac
son zodiac opt
son zodiac pot
son zodiac top
sonic do topaz
sonic topaz do
sop not zodiac
sop ton zodiac
sop zodiac not
sop zodiac ton
spitz ado coon
spitz coon ado
spot no zodiac
spot on zodiac
spot zodiac no
spot zodiac on
stood coin zap
stood icon zap
stood zap coin
stood zap icon
stoop ado zinc
stoop zinc ado
stop no zodiac
stop on zodiac
stop zodiac no
stop zodiac on
ton sop zodiac
ton zodiac sop
top son zodiac
top zodiac son
topaz codon is
topaz coin sod
topaz disco no
topaz disco on
topaz do scion
topaz do sonic
topaz icon sod
topaz is codon
topaz no disco
topaz on disco
topaz scion do
topaz sod coin
topaz sod icon
topaz sonic do
topic sand zoo
topic zoo sand
zap coin stood
zap disco onto
zap icon stood
zap onto disco
zap stood coin
zap stood icon
zinc ado stoop
zinc stoop ado
zodiac no post
zodiac no spot
zodiac no stop
zodiac not sop
zodiac on post
zodiac on spot
zodiac on stop
zodiac opt son
zodiac pont so
zodiac post no
zodiac post on
zodiac pot son
zodiac so pont
zodiac son opt
zodiac son pot
zodiac son top
zodiac sop not
zodiac sop ton
zodiac spot no
zodiac spot on
zodiac stop no
zodiac stop on
zodiac ton sop
zodiac top son
zoo catnip sod
zoo disco pant
zoo dopant sic
zoo optic sand
zoo pant disco
zoo sand optic
zoo sand topic
zoo sic dopant
zoo sod catnip
zoo topic sand
originally posted by: wizdumb1986
I actually know a lot of drug dealers use blaxkberry.
a reply to: galien8
Obama had blackberry as president
edit on 2017-3-11 by galien8 because: emoticon
Blackberry were very much in the news as they claimed that they couldn't get the messages off the server then it seemed to go quiet which normally
means someones worked out a way of getting the system to turn up the goods.
Like most encryption system trust is the hardest part to get so that when you encrypt a message only that person can decrypt it without loads of effort, man in the middle attacks are quite common especially as all it requires is a bit of setup and then the server can automate the rest of it so its bob thinking he's sending it to alice but someone else is decrtypting it and then sending a copy to whoever and then using what alice thinks is the right key the message and it can be automated, theres a truth that if you have a method of getting keys to the other person without them getting intercepted you might as well use that as your message medium.
Like most encryption system trust is the hardest part to get so that when you encrypt a message only that person can decrypt it without loads of effort, man in the middle attacks are quite common especially as all it requires is a bit of setup and then the server can automate the rest of it so its bob thinking he's sending it to alice but someone else is decrtypting it and then sending a copy to whoever and then using what alice thinks is the right key the message and it can be automated, theres a truth that if you have a method of getting keys to the other person without them getting intercepted you might as well use that as your message medium.
edit on 11-3-2017 by Maxatoria because: (no reason given)
Remote protocols are built in to pretty much every device for connectivity to even occur...
What does such a thing mean? An agency can view anything remotely on any device as if they were themselves the user in real time; even take screen shots using the remote protocols.
If the device manufacturer is compliant with authorities; something typically required in standard regulation legalise such as FCC non interference for even things such as spark plugs having to be compliant.
There is no such thing as non hackible; even data that has been purged or erased is typically still there... when the manufacturer themselves are compliant? No hacking is even required no matter what encryption hexkey protocols used.
Older devices are even funnier than current ones; the same sort of thing was going on pre major cell network days around the Pager.
If it is electronic? It can be seen even if not connected to the internet via the wifi function? You are still connected to the internet. Such devices are only not connected when the battery is out; however the CMOS battery is enough power to pop a signal to give the devices location for 3 to 5 years unplugged.
It isn't some "game" of staying ahead of being watched; it's honestly staying ahead of the game of those hacking for nefarious purposes; aka to steal your identity, intellectual property etc. the authorities are not after such things; however if you are a suspect they will screw your system up just as bad as any hacker might.
Best to be on the up and up; online and off.
What does such a thing mean? An agency can view anything remotely on any device as if they were themselves the user in real time; even take screen shots using the remote protocols.
If the device manufacturer is compliant with authorities; something typically required in standard regulation legalise such as FCC non interference for even things such as spark plugs having to be compliant.
There is no such thing as non hackible; even data that has been purged or erased is typically still there... when the manufacturer themselves are compliant? No hacking is even required no matter what encryption hexkey protocols used.
Older devices are even funnier than current ones; the same sort of thing was going on pre major cell network days around the Pager.
If it is electronic? It can be seen even if not connected to the internet via the wifi function? You are still connected to the internet. Such devices are only not connected when the battery is out; however the CMOS battery is enough power to pop a signal to give the devices location for 3 to 5 years unplugged.
It isn't some "game" of staying ahead of being watched; it's honestly staying ahead of the game of those hacking for nefarious purposes; aka to steal your identity, intellectual property etc. the authorities are not after such things; however if you are a suspect they will screw your system up just as bad as any hacker might.
Best to be on the up and up; online and off.
originally posted by: Maxatoria
...Like most encryption system trust is the hardest part to get so that when you encrypt a message only that person can decrypt it without loads of effort, man in the middle attacks are quite common especially as all it requires is a bit of setup and then the server can automate the rest of it so its bob thinking he's sending it to alice but someone else is decrtypting it...
Actually you say that PGP (AES) 2048 bit or maybe even (very much) higher is not secure enough against man-in-the-middle? I think that to crack 2048 bit PGP in a couple of minutes would require the whole computing capacity of the internet
originally posted by: BigBrotherDarkness
What does such a thing mean? An agency can view anything remotely on any device as if they were themselves the user in real time; even take screen shots using the remote protocols.
these blackberries could have been made with no software viruses or hardware viruses, no intended software day zero exploits or intended hardware day zero exploits (at least yet unknown).
Could be that there was no man-on-client possible (which would be ideal) unless you have a CCTV around to spy on you
a reply to: galien8
No one really cares what you do online unless it is some illegal activity from you or someone else doing illegal activity... except maybe a spouse or loved one may care as far as infidelity and trust goes...
There are those looking for statistics in marketing... those are typically just cookie related; however certificates allow such compliation for research purposes such as the Hellenistic and or Thawte certs. No one says you have to allow any of those certs many of them are outdated and allow exploits into root access.
Make sure your BIOS is up to date; encrypted and password protected to help avoid undermining the root protocols that take place before booting into the OS as not doing so can allow a device to be cloned.
I get hacked on all the time; for nefarious purposes, from cloned phones, to identity and even bank theft from my account. It can take awhile for the proper authorities to realize it is not you so they will start to hack and screw your stuff up just as bad if not worse.
It was a real nuisance at first, but I have work arounds to avoid intellectual property from being stolen.
The current best defence for those not so internet savy(basically without a degree in it) is to just stay offline or not use it for personal business you want to keep your intellectual and financial safe always look for the HTTP protocol in the address bar, and for certs at the bottom of the page for keeping things secure, take screen shots and print them for a record of transactions etc.
I could go into more detail; but for those wishing to remain hidden online for purposes with ill intent? Regardless if they believe it ill or not? I will not go into such things.
No one really cares what you do online unless it is some illegal activity from you or someone else doing illegal activity... except maybe a spouse or loved one may care as far as infidelity and trust goes...
There are those looking for statistics in marketing... those are typically just cookie related; however certificates allow such compliation for research purposes such as the Hellenistic and or Thawte certs. No one says you have to allow any of those certs many of them are outdated and allow exploits into root access.
Make sure your BIOS is up to date; encrypted and password protected to help avoid undermining the root protocols that take place before booting into the OS as not doing so can allow a device to be cloned.
I get hacked on all the time; for nefarious purposes, from cloned phones, to identity and even bank theft from my account. It can take awhile for the proper authorities to realize it is not you so they will start to hack and screw your stuff up just as bad if not worse.
It was a real nuisance at first, but I have work arounds to avoid intellectual property from being stolen.
The current best defence for those not so internet savy(basically without a degree in it) is to just stay offline or not use it for personal business you want to keep your intellectual and financial safe always look for the HTTP protocol in the address bar, and for certs at the bottom of the page for keeping things secure, take screen shots and print them for a record of transactions etc.
I could go into more detail; but for those wishing to remain hidden online for purposes with ill intent? Regardless if they believe it ill or not? I will not go into such things.
originally posted by: BigBrotherDarkness
a reply to: galien8
Make sure your BIOS is up to date; encrypted and password protected to help avoid undermining the root protocols that take place before booting into the OS as not doing so can allow a device to be cloned.
Good idea, but I got 7 year old PC cannot update / upgrade BIOS anymore (no software), but I did set strong passwords for user and admin, should I reflash BIOS (like format it and rebuild to get rid of rootkit viruses) if this was possible?
a reply to: galien8
Just take the CMOS battery out(looks like a large watch battery sometimes in green shrink tubing) and cross the jumpers to flash it or leave the CMOS battery out for two or three days as power drains out of the capacitors, keep it off line while reinstalling the updated bios also make sure the check all of that stuff before install, then put the new OS etc on... linux is a nice choice for older machines ARCH is a pretty stable build.
Of course format the drive before reinstallations. You should be alright for an average user; if you have things you want to protect from theft then a good firewall with solid IP tables.
Just take the CMOS battery out(looks like a large watch battery sometimes in green shrink tubing) and cross the jumpers to flash it or leave the CMOS battery out for two or three days as power drains out of the capacitors, keep it off line while reinstalling the updated bios also make sure the check all of that stuff before install, then put the new OS etc on... linux is a nice choice for older machines ARCH is a pretty stable build.
Of course format the drive before reinstallations. You should be alright for an average user; if you have things you want to protect from theft then a good firewall with solid IP tables.
originally posted by: BigBrotherDarkness
a reply to: galien8
Of course format the drive before reinstallations. You should be alright for an average user; if you have things you want to protect from theft then a good firewall with solid IP tables.
Some in the Debian LINUX forum say there is not enough spare memory space in BIOS for a nice rootkit keylogger virus, it would need software in the BIOS to be online, so I thought hackers cannot do very much virus wise with the BIOS?
originally posted by: galien8
originally posted by: Maxatoria
...Like most encryption system trust is the hardest part to get so that when you encrypt a message only that person can decrypt it without loads of effort, man in the middle attacks are quite common especially as all it requires is a bit of setup and then the server can automate the rest of it so its bob thinking he's sending it to alice but someone else is decrtypting it...
Actually you say that PGP (AES) 2048 bit or maybe even (very much) higher is not secure enough against man-in-the-middle? I think that to crack 2048 bit PGP in a couple of minutes would require the whole computing capacity of the internet
You have a trust issue with this sort of thing, unless you exchange keys physically and are able to be sure who you are dealing with then then you hit a problem as who you think you are talking to is a NSA etc box which just decodes and stores the message before re-coding it for the final stretch of the journey..The initial key transfer is the problem to create that trust.
It doesn't matter how good the encryption method is if someone else who is not supposed to know the decryption method has the relevant keys.
originally posted by: Maxatoria
originally posted by: galien8
originally posted by: Maxatoria
...Like most encryption system trust is the hardest part to get so that when you encrypt a message only that person can decrypt it without loads of effort, man in the middle attacks are quite common especially as all it requires is a bit of setup and then the server can automate the rest of it so its bob thinking he's sending it to alice but someone else is decrtypting it...
Actually you say that PGP (AES) 2048 bit or maybe even (very much) higher is not secure enough against man-in-the-middle? I think that to crack 2048 bit PGP in a couple of minutes would require the whole computing capacity of the internet
It doesn't matter how good the encryption method is if someone else who is not supposed to know the decryption method has the relevant keys.
You mean that for example the NSA is already in your device (man-on-client) so they will have your private key? Well yeah then everything is lost, mole cells within the NSA will sell your mission critical info on the market to the highest bidder by stealing candy from a baby and rip off money from a beggar "well I'm only 6 months old " "I made a bad investment " "Well we put a Google 10 million servers data center on your single IPAD "
originally posted by: BigBrotherDarkness
a reply to: galien8
160k of memory can hold a whole volume of enclopedia's in text form. It was a jawdropper back in the 80's with those 5.25" floppies... just how many lines of code do you think that would amount to?
OK but how much does the genuine intended BIOS software use itself? Because my BIOS does a lot of things Clock, Boot Order, settings for Hard Disks ...
new topics
-
Electrical tricks for saving money
Education and Media: 16 minutes ago -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 1 hours ago -
Sunak spinning the sickness figures
Other Current Events: 2 hours ago -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 2 hours ago -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 4 hours ago -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 5 hours ago -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 7 hours ago -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 9 hours ago
top topics
-
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 16 hours ago, 8 flags -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 12 hours ago, 8 flags -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 5 hours ago, 7 flags -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 1 hours ago, 6 flags -
Former Labour minister Frank Field dies aged 81
People: 14 hours ago, 4 flags -
Bobiverse
Fantasy & Science Fiction: 12 hours ago, 3 flags -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 9 hours ago, 3 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 2 hours ago, 3 flags -
Sunak spinning the sickness figures
Other Current Events: 2 hours ago, 3 flags -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 4 hours ago, 2 flags
active topics
-
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest • 10 • : Macenroe82 -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 41 • : TheMisguidedAngel -
Naked Eye Supernova Erupting in the T Coronae Borealis
Space Exploration • 13 • : Therealbeverage -
The Real Reason Behind the Sean Combes Exposure
Political Conspiracies • 45 • : ThatSmellsStrange -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News • 14 • : lilzazz -
Electrical tricks for saving money
Education and Media • 0 • : annonentity -
Late Night with the Devil - a really good unusual modern horror film.
Movies • 4 • : DBCowboy -
Hate makes for strange bedfellows
US Political Madness • 41 • : Solvedit -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues • 11 • : DBCowboy -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 124 • : Justoneman
5
