It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: pr0ph3t
You've been PWNED,
Not trying to scare you, but backup your stuff and reinstall windows or linux or dualboot or Apple ( jaguar donkey bird ).
Whenever you see a cmd prompt do the jig on your screen and you didn't open a soft that utilizes a cmd connection like some bitcoin miners will use a cmd prompt and some gfx cards will too like that, but if you were just browsing, yeah you might have an exploited system or be part of a botnet now
AND NO ANTIVIRUS will see.
I also did some searching and found Notepad++ was implicated as well as being exploited. There is a patch as well if you need, Notepad++ Patch
** Also this dumps should ALWAYS be looked at with wary eyes, it isn't too hard to imagine that if this info isn't wanted to be seen by others, that one might put a surprise in or many so if it was leaked, there was a contingency plan.**
You can also use a screen sharing service like Gyazo it will let you select what you want to be created as a image and will save on their servers, nothing to do with your PC. Gyazo - Screen sharing
You've been PWNED,
Not trying to scare you, but backup your stuff and reinstall windows or linux or dualboot or Apple ( jaguar donkey bird ).
Whenever you see a cmd prompt do the jig on your screen and you didn't open a soft that utilizes a cmd connection like some bitcoin miners will use a cmd prompt and some gfx cards will too like that, but if you were just browsing, yeah you might have an exploited system or be part of a botnet now
AND NO ANTIVIRUS will see.
I also did some searching and found Notepad++ was implicated as well as being exploited. There is a patch as well if you need, Notepad++ Patch
** Also this dumps should ALWAYS be looked at with wary eyes, it isn't too hard to imagine that if this info isn't wanted to be seen by others, that one might put a surprise in or many so if it was leaked, there was a contingency plan.**
You can also use a screen sharing service like Gyazo it will let you select what you want to be created as a image and will save on their servers, nothing to do with your PC. Gyazo - Screen sharing
edit on 9-3-2017 by Tranceopticalinclined because:
(no reason given)
edit on 9-3-2017 by Tranceopticalinclined because: (no reason given)
originally posted by: pr0ph3t
Just also adding, when extracting the file, Wireshark.exe can be visibly seen as one of the things that extracts...
ibb.co...
OK, so you have a potential infection on your computer .......... and you want me to open a screenie that your computer has created, how do i know it aint cross contaminated?
Thanks but no thanks, don't need to see the screenie, i believe you. Hope you find out what the F it is / was
a reply to: corblimeyguvnor
My apologies, As I said I don't often post, usually just to vent some anger at the mental things people bang on about.. so for you and others' sake, I have added it here...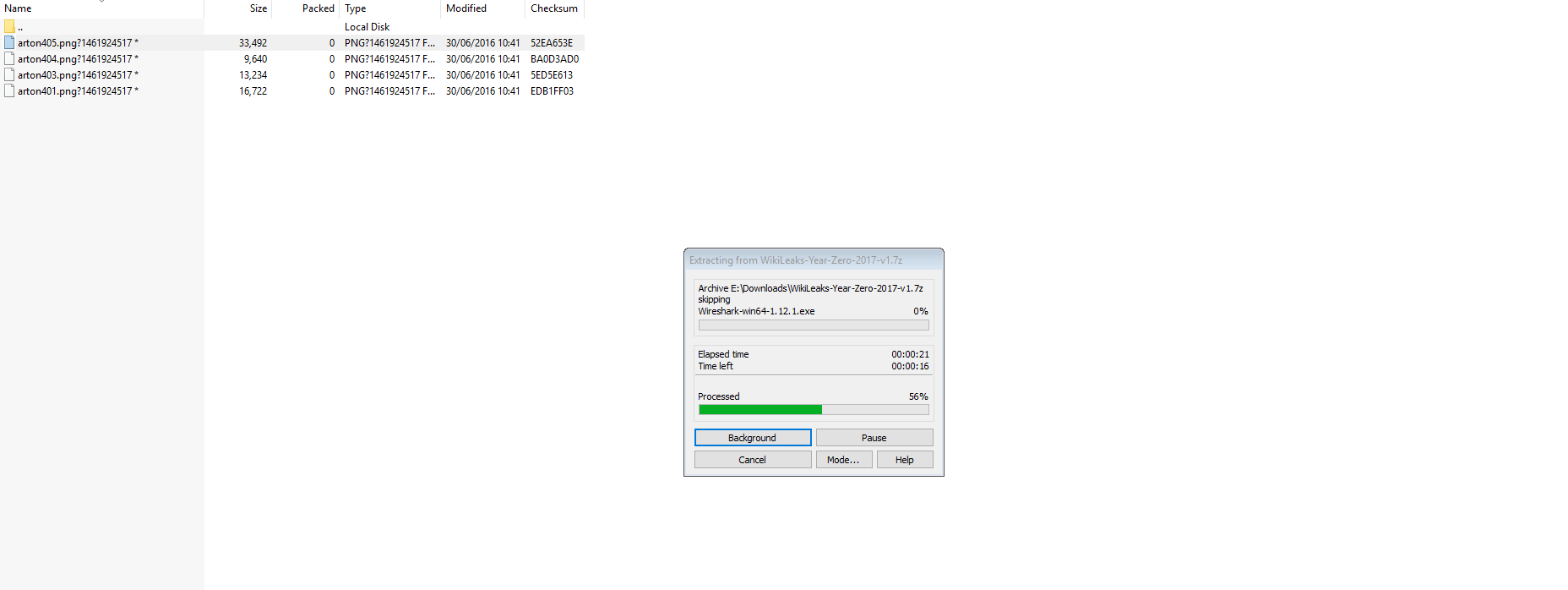
My apologies, As I said I don't often post, usually just to vent some anger at the mental things people bang on about.. so for you and others' sake, I have added it here...

originally posted by: pr0ph3t
a reply to: intrptr
Yeah exactly mate, this is what I'm saying. I don't think wikileaks would put something like that in there at all, I think someone has either released it "on their behalf", or tampered with it... Either way, this is not like other releases!
Probably because its more truthful..?
Someone else said in the vault 7 thread that people should wait for the techies to work thru the files and then review results.
Good advice
Good advice
originally posted by: pr0ph3t
a reply to: intrptr
Erm... I think we have all ascertained this fact. At no point have I said they aren't truthful? You're losing me here dude.
For instance the file dumps from the 'Gubment' don't contain malware... just the ones they don't want you reading. They would hide them if they could but Wiki leaks and Assange himself are currently untouchable.
Compare that to what they did to Manning and Mega Upload (Kim.com) and what they'd like to do to Snowden and Assange...
...even a simple release like Collateral Murder (one video) stirs the hornets nest of the deep secret state.
a reply to: pr0ph3t
Ouch, sounds bad...you should always check the exif metadata before opening anything. If you see any suspicious base64 encodings, better not click on it as it's most likely malware, hidden executables, just like in your case. Might want to look into Exiftool.
I have not yet looked into Vault 7 subject so sorry for asking, but was there any SHA checksum posted by wikileaks so you can verify the file integrity? Because what you've downloaded might not be exactly the same to the original file. We are talking the whole compressed file here. Everything inside could potentially be compromised just like wikileaks. You never know these days.
Anyway, If I were you, I'd save most needed files on a USB and nuke the hard drive. Better safe than sorry.
Also know, that if this is an alphabet agency we are talking about, no anti-virus gonna find anything...as they are, just like the best of hackers, always one step ahead
Ouch, sounds bad...you should always check the exif metadata before opening anything. If you see any suspicious base64 encodings, better not click on it as it's most likely malware, hidden executables, just like in your case. Might want to look into Exiftool.
I have not yet looked into Vault 7 subject so sorry for asking, but was there any SHA checksum posted by wikileaks so you can verify the file integrity? Because what you've downloaded might not be exactly the same to the original file. We are talking the whole compressed file here. Everything inside could potentially be compromised just like wikileaks. You never know these days.
Anyway, If I were you, I'd save most needed files on a USB and nuke the hard drive. Better safe than sorry.
Also know, that if this is an alphabet agency we are talking about, no anti-virus gonna find anything...as they are, just like the best of hackers, always one step ahead
a reply to: Op3nM1nd3d
I obtained it direct from the wikileaks post on twitter, and no, there were no SHA checksums, just a direct link to a torrent file, which then downloaded a file named WikiLeaks-Year-Zero-2017-v1.7z... Ooooh the joys of reformatting so many drives...
I obtained it direct from the wikileaks post on twitter, and no, there were no SHA checksums, just a direct link to a torrent file, which then downloaded a file named WikiLeaks-Year-Zero-2017-v1.7z... Ooooh the joys of reformatting so many drives...
Never open a file on your live machine.
Use something like Qubes on an
air gapped machine.
Sorry for your predicament but its a lesson
learned the hard way.
Oh by the way air gapped machines can be
compromised easily by use of Ethernet over
Power Transmission Lines.
Yep, your power supply.
Never use a 2 way device in the same room as
your computer, invest in some long cables and
A KVM put your PC in another room.
Start reading in the documents how the files
Avoid detection you can still find the files.
Peace
P.S.
Back in the good old days I would find the .exe files
open them in Notepad then delete the contents and
save the files back to the drive.
They usually use more than one file. On boot the first
file checks to see if a second file exist, if not it
re-installs the second file etc. .
My clients used to freak out , I would tell them hey
you won't get the same Virus/Malware again by
not removing the files and just altering them.
Use something like Qubes on an
air gapped machine.
Sorry for your predicament but its a lesson
learned the hard way.
Oh by the way air gapped machines can be
compromised easily by use of Ethernet over
Power Transmission Lines.
Yep, your power supply.
Never use a 2 way device in the same room as
your computer, invest in some long cables and
A KVM put your PC in another room.
Start reading in the documents how the files
Avoid detection you can still find the files.
Peace
P.S.
Back in the good old days I would find the .exe files
open them in Notepad then delete the contents and
save the files back to the drive.
They usually use more than one file. On boot the first
file checks to see if a second file exist, if not it
re-installs the second file etc. .
My clients used to freak out , I would tell them hey
you won't get the same Virus/Malware again by
not removing the files and just altering them.
edit on 9-3-2017 by TucsonOne because: Add
edit on 9-3-2017 by TucsonOne
because: sp
a reply to: Tranceopticalinclined
Yea most coders are too lazy to include
"File Comparison" in their code.
Most end users still click those file attachments.
Oh by the way Malware in images has been around
for a couple of years. Yahoo advertisements got
hit 3 years ago.
I used to "smuggle" screen shots out of my company
for insurance purposes only, by changing them into
.txt files , to stop the email filters from flagging.
Peace
Yea most coders are too lazy to include
"File Comparison" in their code.
Most end users still click those file attachments.
Oh by the way Malware in images has been around
for a couple of years. Yahoo advertisements got
hit 3 years ago.
I used to "smuggle" screen shots out of my company
for insurance purposes only, by changing them into
.txt files , to stop the email filters from flagging.
Peace
edit on 9-3-2017 by TucsonOne because: sp
a reply to: TucsonOne
From what I read about spying over a power supply cable, it's limited to proximity of your device. Even so, I don't think they can get much out this way, let alone infect your system. I mean there are no data transmission protocols so only thing they could actually get are signals generated by your inputs which are accompanied by random noise. So good luck figuring out what just happened...
I would assume this is used as a last resort. Plenty of more viable hacking and surveillance techniques out there.
From what I read about spying over a power supply cable, it's limited to proximity of your device. Even so, I don't think they can get much out this way, let alone infect your system. I mean there are no data transmission protocols so only thing they could actually get are signals generated by your inputs which are accompanied by random noise. So good luck figuring out what just happened...
I would assume this is used as a last resort. Plenty of more viable hacking and surveillance techniques out there.
Anyone accessing those files should be doing so not only on a "disposable" machine, but also disconnected from any networks after you have downloaded
it. No matter how malicious software is it cant recieve instructions or be used by anyone else while offline. Also if done on a semi-garbage laptop
there is no worry of damage done to any important systems.
I would highly advise against dowbloading theae types of files to any important machines or devices, and do not OPEN them until AFTER you disconnect from the net.
It wouldnt hurt to use a virtual OS either.
I would highly advise against dowbloading theae types of files to any important machines or devices, and do not OPEN them until AFTER you disconnect from the net.
It wouldnt hurt to use a virtual OS either.
From WL
Did you look into the png file to see if it was an actual png image file. Maybe it was a link file that execute cmd to run another exe file. Guess there wasn't enough time to see if cmd failed due to a missing file.
edit:
Of course, this is at their site. The torrent is probably live.
Archive attachments (zip, tar.gz, ...) are replaced with a PDF listing all the file names in the archive. As the archive content is assessed it may be made available; until then the archive is redacted.
Attachments with other binary content are replaced by a hex dump of the content to prevent accidental invocation of binaries that may have been infected with weaponized CIA malware. As the content is assessed it may be made available; until then the content is redacted.
Binary files of non-public origin are only available as dumps to prevent accidental invocation of CIA malware infected binaries.
Did you look into the png file to see if it was an actual png image file. Maybe it was a link file that execute cmd to run another exe file. Guess there wasn't enough time to see if cmd failed due to a missing file.
edit:
Of course, this is at their site. The torrent is probably live.
edit on 3/9/2017 by roadgravel because: (no reason given)
a reply to: Op3nM1nd3d
I really hate Wikileaks for a reference but,
en.wikipedia.org...
Sorry I'm a bit oldschool and Grumpy Lol.
My first laptop was a Toshiba 3100e, I still have it.
It had a Fn to change between 6/12mhz.
OS was DOS and I installed win 3.1 got it to
run in enhanced mode lol.
Dedicated arcade machines like Defender, Robotron,
Joust ran at 25mhz in the 80s
I really hate Wikileaks for a reference but,
en.wikipedia.org...
Sorry I'm a bit oldschool and Grumpy Lol.
My first laptop was a Toshiba 3100e, I still have it.
It had a Fn to change between 6/12mhz.
OS was DOS and I installed win 3.1 got it to
run in enhanced mode lol.
Dedicated arcade machines like Defender, Robotron,
Joust ran at 25mhz in the 80s
edit on 9-3-2017 by TucsonOne because: add
new topics
-
Who guards the guards
US Political Madness: 1 hours ago -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 3 hours ago -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs: 8 hours ago -
1980s Arcade
General Chit Chat: 10 hours ago -
Deadpool and Wolverine
Movies: 11 hours ago
top topics
-
Lawsuit Seeks to ‘Ban the Jab’ in Florida
Diseases and Pandemics: 15 hours ago, 20 flags -
Starburst galaxy M82 - Webb Vs Hubble
Space Exploration: 17 hours ago, 13 flags -
CIA botched its handling of sexual assault allegations, House intel report says
Breaking Alternative News: 13 hours ago, 8 flags -
15 Unhealthiest Sodas On The Market
Health & Wellness: 17 hours ago, 6 flags -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs: 8 hours ago, 6 flags -
1980s Arcade
General Chit Chat: 10 hours ago, 4 flags -
Deadpool and Wolverine
Movies: 11 hours ago, 3 flags -
Teenager makes chess history becoming the youngest challenger for the world championship crown
Other Current Events: 12 hours ago, 3 flags -
Who guards the guards
US Political Madness: 1 hours ago, 1 flags -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 3 hours ago, 0 flags
active topics
-
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 622 • : Lazy88 -
Scientists Say Even Insects May Be Sentient
Science & Technology • 55 • : AdultMaleHumanUK -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 201 • : TheWoker -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 610 • : Justoneman -
Lawsuit Seeks to ‘Ban the Jab’ in Florida
Diseases and Pandemics • 24 • : VariedcodeSole -
23,000 Dead People Registered Within a Two Week Period In One State
US Political Madness • 40 • : IndieA -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs • 7 • : pianopraze -
CIA botched its handling of sexual assault allegations, House intel report says
Breaking Alternative News • 6 • : watchitburn -
They Killed Dr. Who for Good
Rant • 63 • : grey580 -
House Overwhelmingly Passes Funding for Ukraine, Israel and Taiwan
US Political Madness • 58 • : IndieA
