It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: eluryh22
originally posted by: Vasa Croe
a reply to: eluryh22
All I have read is they claim the intelligence community (which apparently has a lot more organizations than I ever knew about) figured it out because code blocks matched up with a Russian hack of other countries previously.
Now call me crazy, but had I been caught previously breaking into a countries secure data, and being that I was smart enough to do that, I believe I would write some new code to do it the next time.
If it is indeed a code block that is the evidence then I would look to those that found the exploit in the first place and who they distributed that information to. It would be quite easy to just re-use that block in a chunk of code and blame it on whomever originally wrote that code right? Or is that above the intelligence communities head to think that a hacker group smart enough to break into secure servers would be smart enough to lead them down a false trail?
Now we're getting somewhere. I find this fascinating because I know nothing about this world of cyber espionage.
So are you saying that the U.S. is seeing evidence of a break-in using a code from a previous Russian sanctioned break-in so they are saying it has to be them?
Or, if I'm understanding your post correctly, it would make little sense for the Russians to use a same code more than once because it would be like leaving the same fingerprints on a second crime scene that would obviously implicate them in both?
Is it possible that the first code was either stolen from the Russians or sold by (perhaps a disgruntled or greedy) tech person within the Russian government for the third party to use for whatever it was they were going to use it for?
I apologize if my questions are stupid.... but the extent of my understanding of "codes" is more or less limited to formulas in Excel and getting my emulators-roms to talk to eachother.
Not stupid questions at all. I have read a lot on the subject of the Russian hacks and all I have been able to discern is that multiple ethical hacking agencies have found code blocks within the hacks of the DNC that match up to hacks known from a previous Russian hack that was already outed years ago.
Now I do have to say I have a bit more education on code than most and a lot more on digital security than most as that is my background. I have worked for ethical hacking companies and have been lead engineer/project manager on numerous projects within DISA and Global Combat Support in multiple locations in the US working on virtualization and security within. I have also worked closely with the PCI to support secure transactions and auditing.
As a "hacker" myself, I do not consider myself great by any stretch of the imagination. I am thorough and have a great sense of forethought. By that I mean I can look at a company's current situation and envision the outcome of that situation for them in the future based on my understanding of how quickly hackers adapt to security patches and how determined they are to find holes in systems.
I do know of a few instances in my career where hackers have used certain code blocks of other hackers simply to throw a kink into the mix if their hack is found. It is typically something that has not yet been found but has been known in the community. Usually when something is found, that find is incorporated into the security so if it pops up it will be eliminated before it is ever a threat. This is a multi pronged approach though. I do not know what the DNC's infrastructure setup was at all. From what I have read it was mostly private servers that were hacked and likely housed in large datacenters with multiple virtual servers hosted on a single physical server. Now this is where it gets funny....the ease of which you can exploit even a Tier 4 datacenter.
I did a penetration test one time where a company hired me to try to break into their systems from the outside. I thought about the scenario for about 10 seconds and accepted the challenge. The reason I did is because of a hacker I read about that created the original "black box" security device. I knew I could "update" an idea from his repertoire and easily obtain whatever I wanted internally in their datacenter. I came back to their office approximately 27 hours later and presented them with data directly from the CEO's PC and company trade secrets on formulas from their servers.
Of course they were shocked and really wanted to know how. And of course being hired to ethically hack their site, I told them. They were taken WAY off guard at how easy it was.
So the story I read and "updated" was about this hacker that was caught and turned to ethical hacking and creating security devices to deter those he was working with previously. He had used a very simple technique that worked on the curiosity of the one thing you can't completely control....the human brain. He would walk into a company office building and leave a floppy disk in the bathroom labeled "Salary Report". He knew that execs in these buildings typically had their own facilities in their offices or on their floors and played on the curiosity of those employed way under them but were connected to the same network they were on and the datacenters were on. naturally someone would pick up the floppy, insert it and click on the "salary report" file inside. Now he had done his homework and actually created fake salary reports on individuals that actually worked at the company so once opened it would not raise any eyebrows as to validity and the person viewing would not tell about is because they believed they had come upon a secret they could use. Once it was opened the trojan was planted and access was gained.
My reinvention of this was simple. I knew that gaining access to a datacenter from the inside would be REALLY hard without fake credentials or actually having to find a way into their pipe from the outside. I took 50 thumb drives and loaded them with multiple trojans written by my company that were known only to us. I created the same type of file on it named "Salary Report" and simply used my knowledge of the companies employees to create fake reports. It took about 4 hours to do this at my office then upload on all 50 drives. I went back to the datacenter VERY early in the morning....around 4 am...and I dropped these drives all over the grounds in different areas outside of the building. Some in communal areas, some in smoking areas, some in the parking lot, etc....within 6 hours I had my first hit with access. Out of the 50 drives I dropped, 27 were opened.
So my point in all of this story is that it does not take a genius to figure out how to make a complicated problem easy. If your code is all completely new except for a block or two that is the same as a known intrusion then you have just implicated the one that originally wrote that code.
a reply to: RomeByFire
Either they think we are as dumb as dishwater, or they don't give a damn about what we think, because they plan to do whatever they want regardless.
Meanwhile, the DNC server hack in question had essentially zero impact on the election:
Either they think we are as dumb as dishwater, or they don't give a damn about what we think, because they plan to do whatever they want regardless.
I think before any of you go too far we should wait and see what comes of this. Russia may have hacked the DNC and others in an effort to sway public
opinion with leaks, but they may not have directly affected the vote.
These calls of civil war and such are concerning. Have people gone full-retard?
I know I'm on a conspiracy site, but some of you really need to get a #ing grip.
These calls of civil war and such are concerning. Have people gone full-retard?
I know I'm on a conspiracy site, but some of you really need to get a #ing grip.
originally posted by: CB328
Show me ONE proof that this happened, one
I will take the word of the FBI and CIA over any anonymous poster on the internet. Especially considering that for the entire modern history of Russia they've had a huge intelligence system that is constantly spying on us like we spy on them.
Well therein is the problem. The source of the OP is anonymous and says that the CIA director released a statement that said what the anonymous source says it did. Then went on to claim that Comey believed the same.
So I guess you will take the word of an anonymous source as long as it fits your view?
(post by theantediluvian removed for a manners violation)
originally posted by: schuyler
Just FYI when I saw this headline I went back to places I had seen a news story earlier today tat reported Russian hacker attempts on the RNC that were repulsed because the RNC had better security. Now tat I go back all those links have disappeared. What's up with that, I wonder? They were on Bing's "auto news" feature at the bottom of the screen.
EDIT TO ADD: I found it. Ruskies tried to hack RNC and failed
But to the point: So far all I have heard is that "Russia hacked the emails."
Were the emails real? Yes.
Were the emails changed at all? No.
So what's the problem?
Did they get in through Hillary's server? The one she used to circumvent the scrutiny of our government, and maybe opened the door for Russia to get in? Maybe they are looking in the wrong place and blaming the wrong candidate.
a reply to: theantediluvian
Is this to say everyone who disagrees with the lefts ideology is stupid?
Is this to say everyone who disagrees with the lefts ideology is stupid?
originally posted by: IgnoranceIsntBlisss
a reply to: theantediluvian
You have evidence of Russia doing the Podesta hack? Surprised you'd sit on such a bombshell. Maybe you can get on CNN with it.
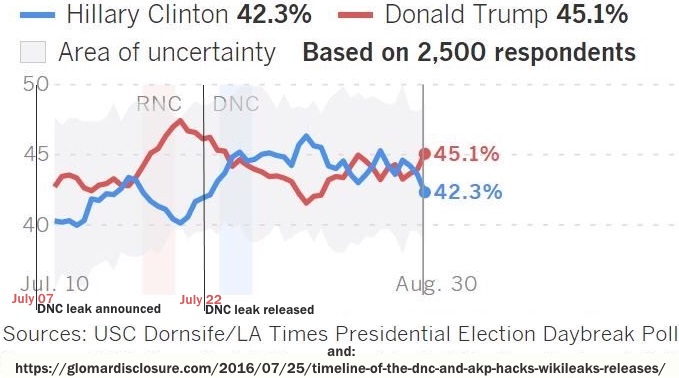
Meanwhile, the DNC Hack was released the week before the DNC Convention. Look at the graph, her poll ratings actually went up following it, not the other way around. LA Times ended up being the most accurate poll, no?
If you'd like to pull up the "Catholic Spring" emails for us, that'd be fantabulous!!!
Actually if you look at the graph before the RNC Clinton had a big drop which started around July 22nd when wikileaks first publised the DNC emails. So thank you for proving that you dont know how to read graphs. (PS that graph is # Jul. 10-Aug 30 with no other dates to help estimate time.)
originally posted by: Pyle
Actually if you look at the graph before the RNC Clinton had a big drop which started around July 22nd when wikileaks first publised the DNC emails. So thank you for proving that you dont know how to read graphs. (PS that graph is # Jul. 10-Aug 30 with no other dates to help estimate time.)
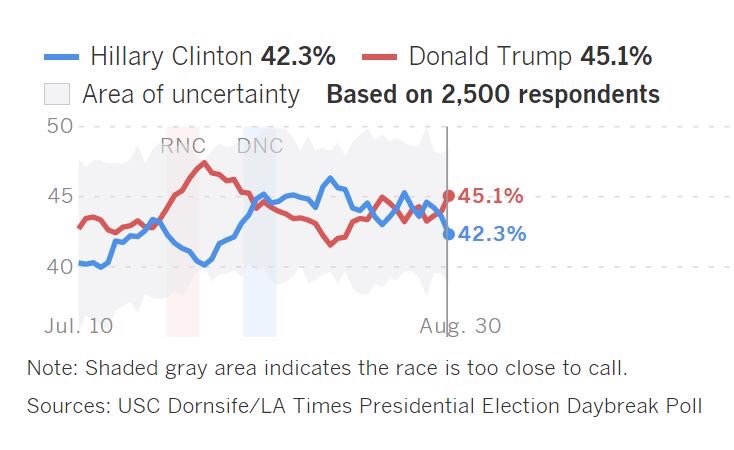
DNC Convention was from July 25 through to July 28, 2016:
en.wikipedia.org...
The poll data graph has the conventions highlighted in red (RNC) & blue (DNC).
They actually announced it in July 7th, but all we see after that is it go up until the RNC convention happenings bumped it up, which quickly fizzled off, and then went up surrounding the leak release ordeal.
glomardisclosure.com...
Any questions?
edit on 16-12-2016 by IgnoranceIsntBlisss because: (no reason given)
a reply to: CB328
You'll take thw word of the CIA? So they were totally 100% dead on in their assesment that Iraq not only had weapons of mass destruction, but they were also attempting to build nukes? So, with that being the case, the George W was 100% right to invade Iraq then? Because my fellow forum member, you can't have it both ways. Either the CIA is right, or they're not.
You'll take thw word of the CIA? So they were totally 100% dead on in their assesment that Iraq not only had weapons of mass destruction, but they were also attempting to build nukes? So, with that being the case, the George W was 100% right to invade Iraq then? Because my fellow forum member, you can't have it both ways. Either the CIA is right, or they're not.
Does Putin support the policies of the Democrats, Clinton, Obama, and the left; or the policies of Trump? If you take the view he is for Obama Care,
and other left policies and plans, then the hack was to tarnish the Republicans and Trump. That is it was a smear attack to help Clinton win. He is
trying to neutralize the right wing. Something the author of the book "The Perestroika Deception" predicted years ago.
www.amazon.com...
www.amazon.com...
originally posted by: Xcathdra
originally posted by: everyone
originally posted by: Xcathdra
I dont know whats more hilarious... The article itself or the 7000 + comments bellow the article picking it apart and calling it fake news.
Good to know and thanks for posting that.
Not sure if i still need to ask this but, Where is the source where the FBI says all of this?
There is not one. The FBI / CIA refused to comment for the article, which is a red flag. Secondly the article holds positions that Obama settled in his press conference. 3rd the FBI / DOJ already stated there is no evidence Russia tried to tip the election in favor of Trump. They also stated there is no links between Trump and Putin.
The Washington compost seems to be just making # up now.
I am starting to think that maybe these articles exist for the blackhats as polls so they can poll their chances on whether or not that can get away with it if they would come out with false statements and say they do indeed think what the WaPo claims.
originally posted by: CriticalStinker
a reply to: everyone
Which garners the question why they are willing to say this happened without the proof.
If it's because it's "classified" I fail to understand. They let the secret out, doing such will have all the same ramifications as providing the evidence.
True, there is a reason why wikileaks has to poerate in the way they do. But somehow these talking heads can do this without breaking a sweat and we are supposed to believe it?
Well it actually turns out that is exactly what they think:
What a joke right !
It backfired though:
originally posted by: projectvxn
a reply to: muse7
You people keep flirting with civil war with your Russian conspiracy theories.
Be careful what you ask for.
You're one of the smarter people on this site. I find I agree with most of your views, but this is one time I think you're letting yourself get heated for no reason.
The Obama administration said on Friday Nov 25th that despite Russian attempts to undermine the presidential election, it has concluded that the results “accurately reflect the will of the American people.”
President Obama repeated this message in his press conference today.
Full stop. That's it.
Even in the bizarre case of an electoral college tie or a vote of no confidence, guess what would happen?
The House of Representatives would elect the President from the 3 Presidential candidates who received the most Electoral votes. Each state delegation has one vote. The Senate would elect the Vice President from the 2 Vice Presidential candidates with the most Electoral votes. Each Senator would cast one vote for Vice President. If the House of Representatives fails to elect a President by Inauguration Day, the Vice-President Elect serves as acting President until the deadlock is resolved in the House.
Given that the Republican Party controls more state delegations than the Democrats do, that would seem to be a recipe for a Trump presidency.
This is NOT a partisan issue.
DNI has not changed their official stance about the DNC hacks.
Below is an official statement on the official DNI intelligence website saying as much...
www.dni.gov...
www.dni.gov...
When and if that changes, DNI will issue a public statement.
What you are hearing here on ATS is a bunch of loudmouth confabulators distorting the news because they are looking for a fight or they are so hopelessly tied up in the word "Trump" (not even the actual person Trump) that they lose their minds when anything tangentially related to the campaign gets brought up out of some irrational fear that somehow it will invalidate the election.
Don't let yourself get worked up over something that isn't even real.
originally posted by: theantediluvian
a reply to: Restricted
There are no innocents in these Mud Pit threads. Run along with your hypocritical whining.
Not to interfere with your amazing wit and intelligently condescending attitude per your usual Mud Pit posts, but you may want to take a look at the forum this is posted in again....(hint: it's not in the Mud Pit)
(post by Restricted removed for a manners violation)
a reply to: Vasa Croe
In the case of APT28/Fancy Bear, the evidence is actually more than just the implants retrieved from the DNC systems being obviously derivative of known versions of X-Agent & X-Tunnel from previous hacks. SecureWorks had independent evidence of the spearphishing attack on the DNC and members of the Hillary Campaign from that time frame. There was at least one hardcoded C2 IP that was previously found hardcodde in samples from the German parliament hack as well as a SSL cert identified that was used in both.
There is good forensic evidence linking the DNC and DCCC hacks to the German Bundestag hack and others. I compiled some of it here.
The evidence of the identity of the threat actors was solid but what is less conclusive is who APT28 & APT29 actually are. FireEye I thought made a compelling case for APT28 being Russian state-sponsored (either part of working for the Russian intelligence apparatus) back in 2014.
I think this is what the FBI has been hung up on. That and the fact that there's no direct evidence (that we know of) that whatever was obtained from either of the two DNC hacks is what was published by Wikileaks except for the "Guccifer 2.0" post from June 15th where it's stated matter-of-factly that documents from the DNC hack were given to Wikileaks for release. There's also some circumstantial evidence by way of time frame.
The DNC emails released by Wikileaks go up through May 25th — which is about two weeks before CrowdStrike pulled the plug after "weeks" of monitoring the activity of the intruders. If Wikileaks had released emails from after that point, it would tend to favor a hypothesis ruling out APT28 or APT29 being the source.
If the CIA has human intelligence to boot, that's pretty much a wrap for me. It doesn't mean that we should have a new election or that the electors should elect HRC but it really disturbs me that so many people are completely choosing to deny what's right in front of their faces based on emotion. It's way more disturbing that the man who is going to our president in a little over a month is actively denying it too. He needs to get on the right side of this thing. Hopefully once he's sworn in, he won't feel that he has something to lose by doing so.
In the case of APT28/Fancy Bear, the evidence is actually more than just the implants retrieved from the DNC systems being obviously derivative of known versions of X-Agent & X-Tunnel from previous hacks. SecureWorks had independent evidence of the spearphishing attack on the DNC and members of the Hillary Campaign from that time frame. There was at least one hardcoded C2 IP that was previously found hardcodde in samples from the German parliament hack as well as a SSL cert identified that was used in both.
There is good forensic evidence linking the DNC and DCCC hacks to the German Bundestag hack and others. I compiled some of it here.
The evidence of the identity of the threat actors was solid but what is less conclusive is who APT28 & APT29 actually are. FireEye I thought made a compelling case for APT28 being Russian state-sponsored (either part of working for the Russian intelligence apparatus) back in 2014.
I think this is what the FBI has been hung up on. That and the fact that there's no direct evidence (that we know of) that whatever was obtained from either of the two DNC hacks is what was published by Wikileaks except for the "Guccifer 2.0" post from June 15th where it's stated matter-of-factly that documents from the DNC hack were given to Wikileaks for release. There's also some circumstantial evidence by way of time frame.
The DNC emails released by Wikileaks go up through May 25th — which is about two weeks before CrowdStrike pulled the plug after "weeks" of monitoring the activity of the intruders. If Wikileaks had released emails from after that point, it would tend to favor a hypothesis ruling out APT28 or APT29 being the source.
If the CIA has human intelligence to boot, that's pretty much a wrap for me. It doesn't mean that we should have a new election or that the electors should elect HRC but it really disturbs me that so many people are completely choosing to deny what's right in front of their faces based on emotion. It's way more disturbing that the man who is going to our president in a little over a month is actively denying it too. He needs to get on the right side of this thing. Hopefully once he's sworn in, he won't feel that he has something to lose by doing so.
new topics
-
Comparing the theology of Paul and Hebrews
Religion, Faith, And Theology: 17 minutes ago -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs: 1 hours ago -
Boston Dynamics say Farewell to Atlas
Science & Technology: 1 hours ago -
I hate dreaming
Rant: 2 hours ago -
Is the origin for the Eye of Horus the pineal gland?
Philosophy and Metaphysics: 3 hours ago -
Man sets himself on fire outside Donald Trump trial
Mainstream News: 4 hours ago -
Biden says little kids flip him the bird all the time.
2024 Elections: 4 hours ago -
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness: 4 hours ago -
Sheetz facing racial discrimination lawsuit for considering criminal history in hiring
Social Issues and Civil Unrest: 4 hours ago -
In an Historic First, In N Out Burger Permanently Closes a Location
Mainstream News: 6 hours ago
top topics
-
In an Historic First, In N Out Burger Permanently Closes a Location
Mainstream News: 6 hours ago, 14 flags -
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness: 4 hours ago, 11 flags -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events: 17 hours ago, 8 flags -
A man of the people
Medical Issues & Conspiracies: 12 hours ago, 8 flags -
Man sets himself on fire outside Donald Trump trial
Mainstream News: 4 hours ago, 7 flags -
Biden says little kids flip him the bird all the time.
2024 Elections: 4 hours ago, 6 flags -
4 plans of US elites to defeat Russia
New World Order: 13 hours ago, 4 flags -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs: 1 hours ago, 4 flags -
Is the origin for the Eye of Horus the pineal gland?
Philosophy and Metaphysics: 3 hours ago, 4 flags -
Sheetz facing racial discrimination lawsuit for considering criminal history in hiring
Social Issues and Civil Unrest: 4 hours ago, 3 flags
active topics
-
The defamation of Mary Magdalene
Religion, Faith, And Theology • 15 • : Solvedit -
A man of the people
Medical Issues & Conspiracies • 9 • : tarantulabite1 -
Silent Moments --In Memory of Beloved Member TDDA
Short Stories • 47 • : Naftalin -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 38 • : DBCowboy -
George Knapp AMA on DI
Area 51 and other Facilities • 28 • : theshadowknows -
Pentagon acknowledges secret UFO project, the Kona Blue program | Vargas Reports
Aliens and UFOs • 4 • : Ophiuchus1 -
Comparing the theology of Paul and Hebrews
Religion, Faith, And Theology • 0 • : DISRAELI2 -
12 jurors selected in Trump criminal trial
US Political Madness • 107 • : Xtrozero -
Man sets himself on fire outside Donald Trump trial
Mainstream News • 30 • : HatesFreshAir -
The Democrats Take Control the House - Look what happened while you were sleeping
US Political Madness • 36 • : DBCowboy