It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:

Found here on twitter
Looks like the DNC decided that they would start with the 'Russia hacked us because Donald Trump' propaganda before another set of emails is about to be released.
Of course, they are also suggesting that there could be fake documents (like the last leak? Oh wait, DNC never denied authenticity) and will have a lot of malware (AKA - please don't look at them, you know, for your safety...nothing to see here)
I'm guessing these new emails will be released within the next couple days since they are heavy hitting already with their propaganda bat. My understanding is that Assange plans to release what he has in batches as they are processed.
Ghost
Edit: Looks like the hacked emails have been released
edit on 13-9-2016 by ghostrager because: (no reason given)
first I would tell her to prove that it was the Russians and second I would say so what.
edit on 9/13/2016 by carewemust because: (no reason
given)
how did the DNC get the documents before the general public did from WikiLeaks? There's a DNC goes lying again they know nothing but lying.
Donna brazile is stupid anyway. I'm sure if an enterprising person wanted to take a find a lot of dirt on that you know what.
Thats some fine damage limitation propaganda right there,
Looks like the DNC is in a chaotic state of panic to me....
Looks like the DNC is in a chaotic state of panic to me....
Oh dnc. so leaky. hackers reporting the news.
the news agencies suppressing and muddying the truth.
hillary might be dead.
will the emails show a search for voodoo priests to revive clinton?
further collusion with the media to bash trump?
money laundering?
hiring protestors?
who has downloaded them?
the news agencies suppressing and muddying the truth.
hillary might be dead.
will the emails show a search for voodoo priests to revive clinton?
further collusion with the media to bash trump?
money laundering?
hiring protestors?
who has downloaded them?
a reply to: dashen
Looks like the emails were released today by Guccifer 2.0 and contain a list of donors and finances:
RT
This could get very interesting to see where the money is coming from and going
Looks like the emails were released today by Guccifer 2.0 and contain a list of donors and finances:
RT
The notorious hacker then shared a trove of documents ostensibly obtained via a breach of the DNC’s cybersecurity. According to Forbes, a password and login was given to them, and the documents they accessed appeared to show details of DNC donors and finances as well as the information technology setup to protect the sensitive data.
This could get very interesting to see where the money is coming from and going
a reply to: carewemust
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election? Do you imagine that the GOP documents would be somehow different? That they aren't up to all the same shenanigans?
What's the motivation for trying to tip the scales to Trump through strategic document releases?
first I would tell her to prove that it was the Russians and second I would say so what.
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election? Do you imagine that the GOP documents would be somehow different? That they aren't up to all the same shenanigans?
What's the motivation for trying to tip the scales to Trump through strategic document releases?
edit on 2016-9-13 by theantediluvian because:
(no reason given)
a reply to: theantediluvian
Sure does, let's ask the DNC what they think; I'm sure the repubs do it too, start a thread on that and find us their docs, ok?
Furthermore, from the horse's mouth:
Forbes
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election?
Sure does, let's ask the DNC what they think; I'm sure the repubs do it too, start a thread on that and find us their docs, ok?

edit on 13-9-2016 by jadedANDcynical because: forgot quote tags
Furthermore, from the horse's mouth:
"Hello everyone. This is Guccifer 2.0. I’m sure you know me because my name is in the conference program list. As I see it, this is the place to discuss cyber security and cyber threats. And may be to propose some solutions.
Let’s figure out who poses the real threat to begin with. Cyber security firms are quick to blame hackers for their activity. Yeah, they cause a lot of troubles for business and politics.
But, who poses a real cyber threat? What do you think? Is it Guccifer? Or Snowden? Or Assange? Or Lazar?
No.
It seems obvious. It’s plain as day you would say. But still my answer is no.
Large IT companies pose a real cyber threat nowadays. You may perfectly know some of them or may not. But their responsibility for the future of our world is growing from day to day. And I will explain to you why.
So. What’s wrong with large IT companies?
First. On their way to a global progress and big money they are collecting users’ personal data, which is the same as spying on people, because many of us don’t even realise they track us online and collect our info. Companies store these data making it vulnerable for leaks.
Second. They create conditions that make people store their info in cloud services. It seems convenient but it’s extremely vulnerable because it’s thousand times easier to steal the data from the cloud than from a personal cell phone for instance.
The next reason, and the crucial one, is software vulnerability. Tech companies hurry to finish the work and earn money. So they break development cycle very often omitting the stage of testing. As a result, clients have raw products installed on their systems and networks with a great number of bugs and holes.
Fourth. It’s well known that all large companies look forward to receiving governmental contracts. They develop governmental websites, communication systems, electronic voting systems, and so on and have their products installed to critical infrastructure objects on the national level.
They are aggressively lobbying their interests. You can see it at the diagram that they spent millions of dollars for lobbying. That doesn’t mean they will produce better software. That means they will get even more money in return.
Fifth. This is censorship. For example Twitter censors unwelcome users. I can judge it by myself here. You can see how Guccifer 2 hashtag unnaturally abruptly stops trending. It seems impossible that all Twitter users just stop twitting about Guccifer 2 leaks, in a moment. That’s why people started Guccifer 3, 4, 5 hashtags to avoid censorship. People also told me their twits were not shown in the Twitter live wall unlike to their account’s wall.
So, the cyber aggressiveness is progressing nowadays. The number of cyber attacks is steadily growing. What’s the reason? What’s wrong with the cyber defense?
Well. they take wrong measures. They search for cyber criminals, sentence them. But two more hackers appear instead of one convicted. The real problem is inside. This is just the same as in offline world. This is not enough to prosecute criminals. It requires preventive measures, to fight criminality by elimination of the possibility of crime.
So, what’s the right question we should ask about cyber crime?
Who hacked a system?
Wrong. The right question is: who made it possible that a system was hacked? In this regard, what question should you ask me?
How I hacked the DNC???
Now you know this is a wrong question. Who made it possible, that I hacked into the DNC? This is the question. And I suppose, you already know the answer. This is NGP VAN Company that operates the DNC network. And this is its CEO Stu Trevelyan who is really responsible for the breach.
Their software is full of holes. And you knew about it even before I came on stage.
You may remember Josh Uretsky, the national data director for Sander’s presidential campaign. He was fired in December, 2015 after improperly accessing proprietary data in the DNC system. As it was agreed, he was intentionally searching for voter information belonging to other campaigns.
However, he is not to blame. The real reason voter information became available for non-authorized users was NGP VAN’s raw software which had holes and errors in the code. And this is the same reason I managed to get access to the DNC network. Vulnerabilities in the NGP VAN software installed on its server which they have plenty of. #! Yeah?
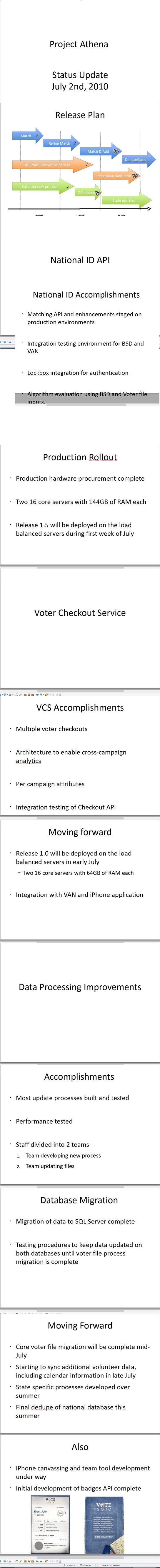
This scheme shows how NGP VAN is incorporated in the DNC infrastructure. It’s for detailed examination, if you are interested. And here are a couple of NGP VAN’s documents from their network. If you r interested in their internal documents, you can have them via the link on the screen. The password is usual. It’s also on the screen. You may also ask the conference producers for them later.
So, as you see there’s no need to breach into separate users accounts or separate systems. You just need to hack their tech company. This is the feature.
Big IT companies lead us to a disaster. In their pursuit for money they release raw software, so their clients are highly vulnerable. It became usual to blame everything on hackers while IT companies just pretend they are working hard to patch bugs and to plug holes. And they even ask for more and more money to correct their own mistakes.
As a result they pose a threat to the critical infrastructure elements and the national security as a whole. Total computerization along with inadequate software development may cause a lot of troubles. That’s why it’s better to use paper sometimes.
We should start now to prevent electronic apocalypse and rise of the machines in the future. Or else it would be too late. As the financial corporations are ruling the world now so the IT companies will rule it in the near future.
What should we do?
You would tell me I could report a bug to the company as it’s commonly done. What do you think they would answer me? Thanks? Or this is not crucial? Or maybe they would even give me some money. Yeah. But what could it change?
Nothing. Yeah. Really. Nothing at all.
We need to shake the situation, to make our voices sound. Yeah, I know if they find me I’m doomed to live like Assange, Snowden, Manning or Lazar. In exile or in prison.
But it’s worth it for they are the heroes, heroes of new era.
Thanks for ur attention
See you online!"
Forbes
edit on 13-9-2016 by jadedANDcynical because: (no reason given)
originally posted by: theantediluvian
a reply to: carewemust
first I would tell her to prove that it was the Russians and second I would say so what.
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election? Do you imagine that the GOP documents would be somehow different? That they aren't up to all the same shenanigans?
What's the motivation for trying to tip the scales to Trump through strategic document releases?
First of all it is not clear where the hacks came from. Second if people like Snowden or whomever hacked and is leaking this stuff to show the obfuscation, lies, and all the other non democratic thing that are occurring then I say yes! We deserve the truth and our govt, our media, and all other info we get about he powers that be need to exposed. Don't you want want a just country no matter what party you support?
a reply to: theantediluvian
A simplistic reason might be that the Clintons are just hated, especially Hillary.
What's the motivation for trying to tip the scales to Trump through strategic document releases?
A simplistic reason might be that the Clintons are just hated, especially Hillary.
a reply to: ghostrager
"There's one person that stands to benefit...Donald Trump." lol. If I used "who benefits?" as a litmus test, then I would have to say that the Democratic Party is behind every mass gun shooting and race-driven crime given a headline.
"There's one person that stands to benefit...Donald Trump." lol. If I used "who benefits?" as a litmus test, then I would have to say that the Democratic Party is behind every mass gun shooting and race-driven crime given a headline.
edit on 13-9-2016 by MotherMayEye because: (no reason given)
originally posted by: jadedANDcynical
a reply to: theantediluvian
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election?
Sure does, let's ask the DNC what they think; I'm sure the repubs do it too, start a thread on that and find us their docs, ok?
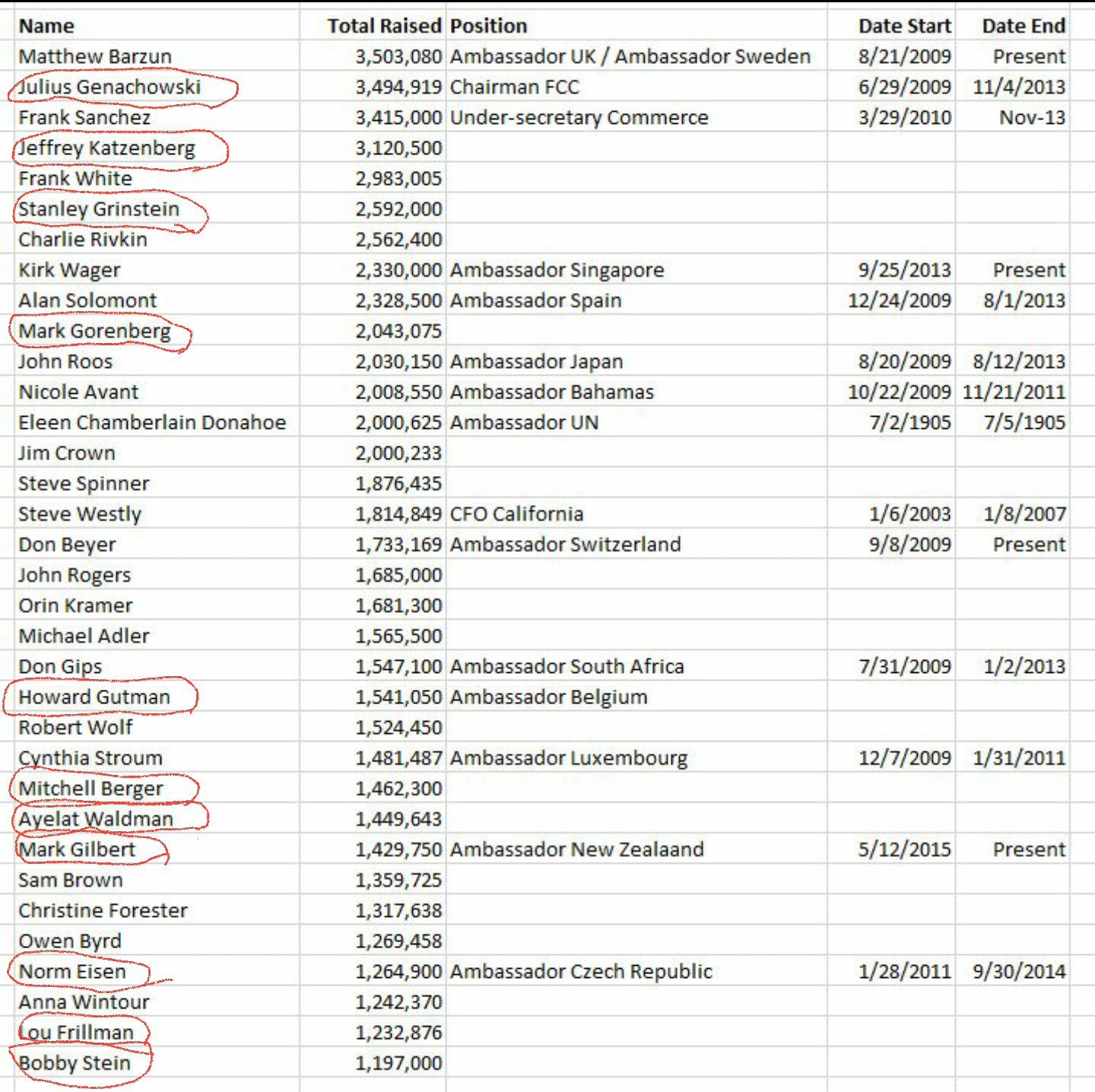
Nailed it! What about the Obama appointed ambassadors raising millions in foreign countries? Sure that money ain't coming out of their pockets!
a reply to: theantediluvian
No it doesn't bother them.
The Republican Nominee is praising theSoviet Premier Russian President as being a great leader.
A raving madness has taken about 30-40% of the country ... and the rest of us are just crazy.
No it doesn't bother them.
The Republican Nominee is praising the
A raving madness has taken about 30-40% of the country ... and the rest of us are just crazy.
originally posted by: theantediluvian
a reply to: carewemust
first I would tell her to prove that it was the Russians and second I would say so what.
Does it honestly not concern you that foreigners — whether it's the Russians or not, it's 100% foreigners regardless — are trying to influence the outcome of our election?
Aren't Hillary's DREAMERS just "foreigners" enlisted to help influence the outcome of the election?
Democrats turning on their former beloved Soviet socialist parasite, err I mean paradise, is hilarious...
It must be so conflicting for a Saul Alinsky acolyte such as Hillary to be at odds with the home of the original radical leftist, V.I. Lenin!!
Back to the op...didn't Assange hint that Seth Rich was the leak?!?
Anyhow, if I were Pagliani I would make sure my life insurance was paid up...
Having powerful dirt on the Clinton Dynasty is not a recipe for a long life...
-Chris
It must be so conflicting for a Saul Alinsky acolyte such as Hillary to be at odds with the home of the original radical leftist, V.I. Lenin!!
Back to the op...didn't Assange hint that Seth Rich was the leak?!?
Anyhow, if I were Pagliani I would make sure my life insurance was paid up...
Having powerful dirt on the Clinton Dynasty is not a recipe for a long life...
-Chris
new topics
-
George Knapp AMA on DI
Area 51 and other Facilities: 3 hours ago -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 3 hours ago -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 5 hours ago -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 6 hours ago -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 8 hours ago -
Do we live in a simulation similar to The Matrix 1999?
ATS Skunk Works: 9 hours ago -
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 10 hours ago -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 11 hours ago -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 11 hours ago
top topics
-
BREAKING: O’Keefe Media Uncovers who is really running the White House
US Political Madness: 10 hours ago, 23 flags -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness: 11 hours ago, 18 flags -
George Knapp AMA on DI
Area 51 and other Facilities: 3 hours ago, 16 flags -
African "Newcomers" Tell NYC They Don't Like the Free Food or Shelter They've Been Given
Social Issues and Civil Unrest: 16 hours ago, 12 flags -
Russia Flooding
Fragile Earth: 17 hours ago, 7 flags -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest: 11 hours ago, 7 flags -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry: 15 hours ago, 6 flags -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 5 hours ago, 6 flags -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs: 8 hours ago, 5 flags -
The Tories may be wiped out after the Election - Serves them Right
Regional Politics: 6 hours ago, 3 flags
active topics
-
The Tories may be wiped out after the Election - Serves them Right
Regional Politics • 19 • : alwaysbeenhere2 -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 365 • : xuenchen -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 125 • : KrustyKrab -
MULTIPLE SKYMASTER MESSAGES GOING OUT
World War Three • 30 • : Astrocometus -
Biden--My Uncle Was Eaten By Cannibals
US Political Madness • 40 • : Kaiju666 -
Alabama Man Detonated Explosive Device Outside of the State Attorney General’s Office
Social Issues and Civil Unrest • 57 • : watchitburn -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs • 6 • : visitedbythem -
Russian intelligence officer: explosions at defense factories in the USA and Wales may be sabotage
Weaponry • 165 • : andy06shake -
Silent Moments --In Memory of Beloved Member TDDA
Short Stories • 43 • : Naftalin -
What do you do to get to sleep and stay asleep ??
Health & Wellness • 108 • : TheGoondockSaint