It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Never let a good crisis go to waste? This and or there was something known about that was originally hidden due to being potentially damming to the
whole case-Such as the FBI or other "knew" of the planned attacks?
Snowden is supporting Apple and even a Google CEO.
Source
Snowden is supporting Apple and even a Google CEO.
"The technical changes the @FBI demands would make it possible to break into an iPhone (5C or older) in a half hour," Snowden tweeted.
"The @FBI is creating a world where citizens rely on #Apple to defend their rights, rather than the other way around," Snowden tweeted.
Google CEO Sundar Pichai took a public stand in support of Apple in a series of tweets late Wednesday, saying "forcing companies to enable hacking could compromise users’ privacy" and would set a "troubling precedent."
Source
edit on 19-2-2016 by dreamingawake because: (no reason given)
a reply to: dreamingawake
i think i agree with you here. Obviously security/privacy is an issue but asking for a backdoor isn't something that's usually argued about in the public forum. Which leads me to believe there's something else going on here that the FBI doesn't want known. As i stated in my post, if they wanna check out who he was contacting they can do that through records, its not like they have to prove he did it lol. My gut tells me whatever it is, goes well beyond the shooting this person was involved in.
i think i agree with you here. Obviously security/privacy is an issue but asking for a backdoor isn't something that's usually argued about in the public forum. Which leads me to believe there's something else going on here that the FBI doesn't want known. As i stated in my post, if they wanna check out who he was contacting they can do that through records, its not like they have to prove he did it lol. My gut tells me whatever it is, goes well beyond the shooting this person was involved in.
And Apple could have recovered information from the phone had the Apple ID passcode not been changed, Apple said.
If the phone was taken to a location where it recognized the Wi-Fi network, such as the San Bernardino shooters' home, it could have been backed up to the cloud, Apple suggested.
Am I the only one who picked up on this?
In other words... stop uploading stuff to Apple's cloud networks. That statement makes it pretty clear that Apple will turn your cloud information over to the government.
a reply to: EternalSolace
Yes, that seems to be the case. If it's on a server then a warrant can get access.
Yes, that seems to be the case. If it's on a server then a warrant can get access.
edit on 2/19/2016 by roadgravel because: (no reason
given)
originally posted by: EternalSolace
And Apple could have recovered information from the phone had the Apple ID passcode not been changed, Apple said.
If the phone was taken to a location where it recognized the Wi-Fi network, such as the San Bernardino shooters' home, it could have been backed up to the cloud, Apple suggested.
Am I the only one who picked up on this?
In other words... stop uploading stuff to Apple's cloud networks. That statement makes it pretty clear that Apple will turn your cloud information over to the government.
You weren't aware of that already? I'm astounded.... What do you think the privacy changes in Europe are about? Countries don't want Apple giving their citizens personal data to the FBI.
And even in the US, the FBI has been able to retrieve this information through warrants, CALEA, and Prism for many years
originally posted by: roadgravel
A county investigator reset the password,
That seems like a major mistake unless the same iPhone password enables some other access. Some guy who shouldn't have been touching the phone or this whole thing is BS. Password conveniently forgotten?
I think Apple is slowly letting the cat out of the bag purposely.
Something seems a bit strange here. I have an iPhone and there are 3 different pass codes. Your Apple ID has a pass code that you use to log into the Apple store (iTunes) and you need it to make changes on the phone, but you can only do it if the phone is plugged into (cable req’d) the computer you last backed it up to, Wi-Fi will not work. There is another pass code but it is just the screen lock code which automatically kicks in after a set time of non-use. It stops anyone from using the phone if lost or stolen. The 3rd pass code is used if you decide to encrypt the backup of the iPhone which also encrypts the passwords of accounts used on the iPhone such as email accounts, which is good if you are backing up to the cloud.
You can get the Apple ID pass code from Apple but they have no access to the screen lock code or the backup encryption code(they are selected by you).
So what do they really want, a back door to the screen lock code or a way into every encrypted backup on the cloud ?
a reply to: Sargeras
I'm not 100% positive, but I think if you forget your passcode you plug it into your computer and sync with iTunes to somehow unlock it. Could be wrong though. I know my husband did something like that for my child who "forgot" their passcode.
I'm not 100% positive, but I think if you forget your passcode you plug it into your computer and sync with iTunes to somehow unlock it. Could be wrong though. I know my husband did something like that for my child who "forgot" their passcode.
originally posted by: paraphi
What does the FBI want? They don't want a backdoor. The "backdoor" argument comes from Apple, not the FBI.
They want:
1. Apple to change the config so the phone does not erase itself following failed password attempts. Just for this phone.
2. A process to automate the process to run the 100,000 combinations, thus saving time. The FBI say Apple can do this If they like.
A backdoor in essence, that would by extension be applicable to any similar-model iPhone not using the secure enclave (I still need to look into how that affects things). So yes, a security workaround AKA backdoor to allow future access to any related device.
And yes, Apple definitely COULD develop the modified version of iOS to do this. They just don't want to given the very slippery slope presented to all other devices it would also work on.
Sidenote: 999,999 combinations - if he was only using a six-digit passcode. If he was using an alphanumeric passcode of any impressive length (assuming wasn't), they can essentially piss off regarding any actual attempts at brute forcing regardless.
originally posted by: VimanaExplorer
iCloud backups are done using user's password I think. But local files on iOS are hardware encrypted on device itself. The iCloud password encrypted using old password, and new password (one way hash) can't decrypt already encrypted data using old password. Thats how I understand. So that data is forever lost. So now they instead want local data via a solution from Apple.
Yes to local content encryption, no to iCloud backups/passwords. Anything in iCloud backups, Apple can and will provide with the proper legal requirements - the issue appears to be that the existing iCloud backup was older and so wouldn't contain data closer to the attack.
As to the password change...and this I wasn't aware of...apparently it just prevents the phone from any further automatic iCloud backups that might have been available otherwise when device on wifi plugged in with screen off. Good to know, apparently you have to reenable automatic backups manually after changing your Apple ID password?
Looks like Apple's local encryption is rock solid, never backup your data to iCloud if you care about privacy.
Fine from a privacy standpoint for any casual user (who uses a solid password and applies available account security options wisely), but if you're likely to come under legal scrutiny, 100% correct. Cloud services are generally verboten from an OPSEC perspective depending on your threat level.
a reply to: Sargeras
Yes and no. You have to reset the whole *device* to factory condition by wiping the device (either with iCloud remote wipe or recovery mode restore in iTunes). Would definitely not help with data recovery.
Though I do believe that the iPhone, like most electronic equipment, has a way to reset the passcode to factory specks in case you change it and lose the passcode.
Yes and no. You have to reset the whole *device* to factory condition by wiping the device (either with iCloud remote wipe or recovery mode restore in iTunes). Would definitely not help with data recovery.
originally posted by: Grayarea
Your Apple ID has a pass code that you use to log into the Apple store (iTunes) and you need it to make changes on the phone, but you can only do it if the phone is plugged into (cable req’d) the computer you last backed it up to, Wi-Fi will not work.
Could you clarify the italicized bit? You should be able to use your Apple ID password whenever required as long as you have a network connection.
The FBI
A department of Government keeping secrets, has no business speaking on social decisions.
Mike Grouchy
A department of Government keeping secrets, has no business speaking on social decisions.
Mike Grouchy
originally posted by: Praetorius
originally posted by: Grayarea
Your Apple ID has a pass code that you use to log into the Apple store (iTunes) and you need it to make changes on the phone, but you can only do it if the phone is plugged into (cable req’d) the computer you last backed it up to, Wi-Fi will not work.
Could you clarify the italicized bit? You should be able to use your Apple ID password whenever required as long as you have a network connection.
To make changes on the iPhone you need to be logged into iTunes on the computer you last backed up your iPhone to, the screen on the phone can remain locked but you must use the cable.
originally posted by: Grayarea
Your Apple ID has a pass code that you use to log into the Apple store (iTunes) and you need it to make changes on the phone, but you can only do it if the phone is plugged into (cable req’d) the computer you last backed it up to, Wi-Fi will not work.
originally posted by: Praetorius
Could you clarify the italicized bit? You should be able to use your Apple ID password whenever required as long as you have a network connection.
Works this way:
1. Find the original user's authentication token from a Windows or Mac OS machine they've used which has itunes. You don't actually need the user's computer for this, you can just snatch the token from an image / offline storage.
2. Plug the locked phone in, sync with itunes and use the token to access the backups
3. Enjoy datas
Second method:
1. Find user's original Apple password
2. Proxy the user's location so you don't trigger two step authentication
3. Enjoy datas with no iphone required
The backups don't contain everything, but they contain 95% of what you would want anyway.
Whilst the phone data is encrypted, the icloud data is not. The cloud is also no longer optional. Cloud data is only protected by your apple passsword / authentication token. Given people write their apple password to memory every time they login to itunes or whatever it's a pretty reliable way to get information when you have warrants.
Here's the docs related to my friend's RCMP data retrieval process.
30 pages in total. Requested through access to information
software used to do it BitPim/Device Seizure/Mobiedit/Datailo/Oxygen phone manager/Nokia PC Suite and SIMcon

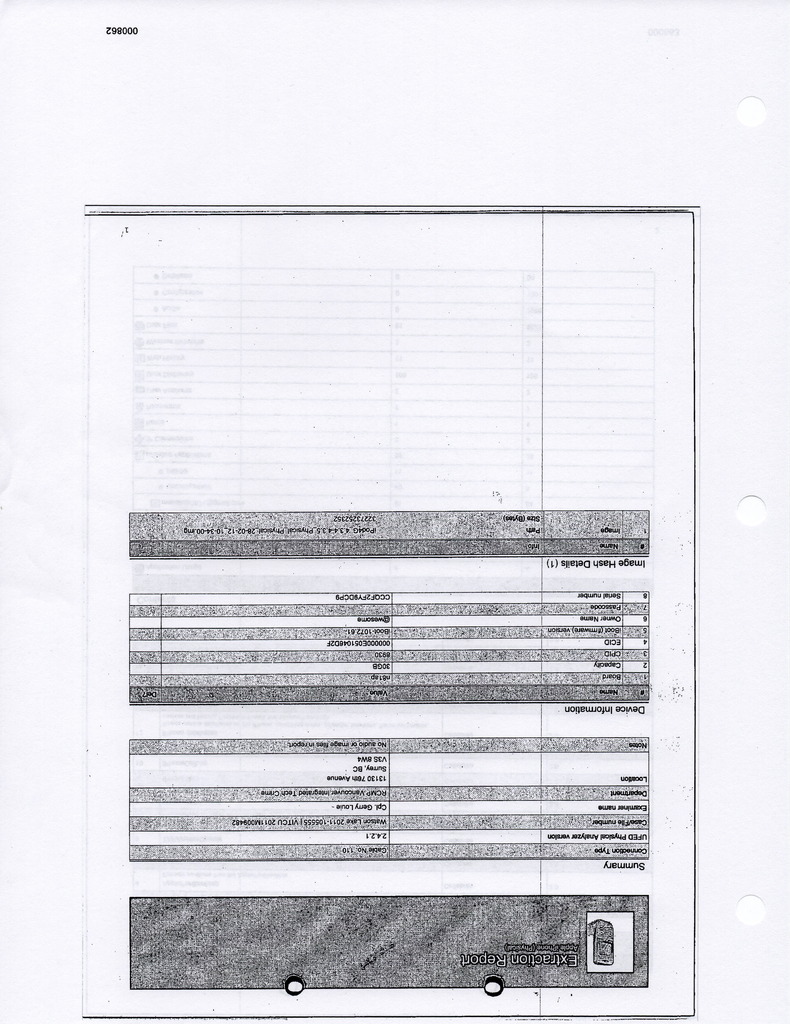
Ill see if he has more info...
30 pages in total. Requested through access to information
software used to do it BitPim/Device Seizure/Mobiedit/Datailo/Oxygen phone manager/Nokia PC Suite and SIMcon


Ill see if he has more info...
The phone was encrypted the os is set up to give you 10 attempts then it scrubs the files. Apple can't give them a backdoor there isn't one its 128 bit encryption based off phone id and whatever the password was that was entered. The OS will only decode the information if it matches the phone id . Technically even Apple can't decode it though I think their is a way they could cheat and get the info. If they created a ram disk with the same phone id and a rewritten OS that can allow endless attempts you could eventually brute force your way in. Even if it took 10000 attempts.
originally posted by: Grayarea
originally posted by: roadgravel
A county investigator reset the password,
That seems like a major mistake unless the same iPhone password enables some other access. Some guy who shouldn't have been touching the phone or this whole thing is BS. Password conveniently forgotten?
I think Apple is slowly letting the cat out of the bag purposely.
Something seems a bit strange here. I have an iPhone and there are 3 different pass codes. Your Apple ID has a pass code that you use to log into the Apple store (iTunes) and you need it to make changes on the phone, but you can only do it if the phone is plugged into (cable req’d) the computer you last backed it up to, Wi-Fi will not work. There is another pass code but it is just the screen lock code which automatically kicks in after a set time of non-use. It stops anyone from using the phone if lost or stolen. The 3rd pass code is used if you decide to encrypt the backup of the iPhone which also encrypts the passwords of accounts used on the iPhone such as email accounts, which is good if you are backing up to the cloud.
You can get the Apple ID pass code from Apple but they have no access to the screen lock code or the backup encryption code(they are selected by you).
So what do they really want, a back door to the screen lock code or a way into every encrypted backup on the cloud ?
As far as the government using this technique to spy on people unlikely it could take months to hack if he used alpha numeric instead of 4 digit ID.Apple refusal is more in that I fibt think they want to give the government a copy of the OS that they could use to circumvent the delete feature. So apple is trying the well we cant do it which is tehnically true only thr phobe can decrypt the data. The data wull not decrypt on any other device it will only work if the phone id is the same . If that's the case give the phone to apple let them do it and everyone is happy.
Now the apple ID is interesting since that cab be reset online which begs the question was it the government or someone else????
originally posted by: paraphi
What does the FBI want? They don't want a backdoor. The "backdoor" argument comes from Apple, not the FBI.
They want:
1. Apple to change the config so the phone does not erase itself following failed password attempts. Just for this phone.
2. A process to automate the process to run the 100,000 combinations, thus saving time. The FBI say Apple can do this If they like.
Why would whatever they come up with work only for this phone and not others?
Theres more than one way to skin a cat, right? I think most of us here agree in this specific situation.
So with that in mind, what the FBI is requesting of Apple is definitely troubling.
Im with Apple on this one, and agree with Snowden. Why would anyone trust the FBI?
So with that in mind, what the FBI is requesting of Apple is definitely troubling.
Im with Apple on this one, and agree with Snowden. Why would anyone trust the FBI?
new topics
-
Bobiverse
Fantasy & Science Fiction: 25 minutes ago -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 30 minutes ago -
Former Labour minister Frank Field dies aged 81
People: 2 hours ago -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 4 hours ago -
This is our Story
General Entertainment: 7 hours ago -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 9 hours ago -
Ode to Artemis
General Chit Chat: 10 hours ago
top topics
-
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections: 9 hours ago, 13 flags -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections: 15 hours ago, 6 flags -
One Flame Throwing Robot Dog for Christmas Please!
Weaponry: 13 hours ago, 6 flags -
Don't take advantage of people just because it seems easy it will backfire
Rant: 14 hours ago, 4 flags -
Ditching physical money
History: 13 hours ago, 4 flags -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 4 hours ago, 4 flags -
Ode to Artemis
General Chit Chat: 10 hours ago, 3 flags -
Former Labour minister Frank Field dies aged 81
People: 2 hours ago, 3 flags -
VirginOfGrand says hello
Introductions: 14 hours ago, 2 flags -
This is our Story
General Entertainment: 7 hours ago, 2 flags
active topics
-
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7131 • : baddmove -
President BIDEN Vows to Make Americans Pay More Federal Taxes in 2025 - Political Suicide.
2024 Elections • 28 • : CarlLaFong -
So this is what Hamas considers 'freedom fighting' ...
War On Terrorism • 250 • : FlyersFan -
Russia Ukraine Update Thread - part 3
World War Three • 5725 • : BernnieJGato -
NASA Researchers Discover a Parallel Universe That Runs Backwards through Time - Alongside Us
Space Exploration • 70 • : seekshelter -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 21 • : network dude -
IDF Intel Chief Resigns Over Hamas attack
Middle East Issues • 43 • : TheWoker -
University student disciplined after saying veganism is wrong and gender fluidity is stupid
Education and Media • 44 • : confuzedcitizen -
Who guards the guards
US Political Madness • 6 • : covent -
Remember These Attacks When President Trump 2.0 Retribution-Justice Commences.
2024 Elections • 53 • : Justoneman
