It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
2
share:
Mods: If this is posted in the wrong forum, please move. I'm not sure about the correct forum for this, as it spans over political, computer sciences,
conspiracies and so on.
Ctrl, alt, delete: Bundestag considers network reboot after hacks
Source
Over the past 4 weeks, after the detection by some personel of some "unusual activities on the internal network" of the Bundestag (about the same political thing as the US Congress), the hackers have achieved complete control over the network, gaining administrator priviledges, complete access to the LDAP and Windows Active Directory Servers!
The German Federal Office for Information Security (BSI) has recommended "the replacement of all 20,000 Bundestag computers."
Just imagine the same for the US Congress!
Who is behind this? Noone knows (besides the hackers, of course), and the usual suspects are named (Russia, NSA, Israel, Iran, etc.).
Ctrl, alt, delete: Bundestag considers network reboot after hacks
Source
Over the past 4 weeks, after the detection by some personel of some "unusual activities on the internal network" of the Bundestag (about the same political thing as the US Congress), the hackers have achieved complete control over the network, gaining administrator priviledges, complete access to the LDAP and Windows Active Directory Servers!
The German Federal Office for Information Security (BSI) has recommended "the replacement of all 20,000 Bundestag computers."
Just imagine the same for the US Congress!
Who is behind this? Noone knows (besides the hackers, of course), and the usual suspects are named (Russia, NSA, Israel, Iran, etc.).
edit on
11 6 2015 by ManFromEurope because: (no reason given)
Whomever it was, after 4 weeks one would imagine that they got the information that they were after and probably a great deal more.
This should drop the prices of second computers in Germany for quite a while. Grab a bargain. You will never know who is watching.
Surely though, it is a massive overkill. Dump the hard drives and re-install the O/S and Bios for a clean slate. Would be a lot cheaper.
P
This should drop the prices of second computers in Germany for quite a while. Grab a bargain. You will never know who is watching.
Surely though, it is a massive overkill. Dump the hard drives and re-install the O/S and Bios for a clean slate. Would be a lot cheaper.
P
a reply to: ManFromEurope
I don't understand why people connect private information to the Internet.
Maybe someone can explain this to me.
I don't understand why people connect private information to the Internet.
Maybe someone can explain this to me.
originally posted by: 1000Lakes
a reply to: ManFromEurope
I don't understand why people connect private information to the Internet.
Maybe someone can explain this to me.
because people have become dum,theres no other reason,,why would you connect a nuclear power station to the net but they have.
why do people store there stuff in a cloud(same problem here.)
it makes sense to have two systems one for internet + 1 for doing your important stuff or storing data like,pictures,files,songs,secrets that is not connected to the network .
if you do not do this then expect to be hacked,i have no sympathy for those that urinate into the wind...........
Well if these machines are running Intel chips "unit 1" has been running a little warm for a while now.
Not sure how you disconnect the human interface from the internet these days?
Sequester all the decision makers?
Not sure how you disconnect the human interface from the internet these days?
Sequester all the decision makers?
originally posted by: 1000Lakes
a reply to: ManFromEurope
I don't understand why people connect private information to the Internet.
Maybe someone can explain this to me.
Usually departments have both green zone and red zone networks. All departments have their own public websites along with computers used for research collaboration with universities. They'll call these green zones.
The problem is securing the red-zone computer network. You can have separate cables, computers, and maybe even copper cladding on the exterior wall like some banks do. But then the problem is getting information to and from this network. They'l set up one or two PC's to work as an airlock, so that it is only accessible from one direction on each network eg. read-only, write-only.
Bozo the user decides he wants to do some work at home. So he gets a memory stick and copies the files from his secure network to his USB stick. In the process, whatever malware was on his home PC gets transferred to that network, and it sends out web-spiders and crawlers to find network configurations and interesting files, stashed them away somewhere and waits for the chance to send the data out. It waits until the USB stick is on a public network and sends out the data.
Or somebody just sticks a bluetooth USB dongle or even charges up their mobile phone. Some cheap phones would automatically reconfigure the PC's routing tables to use the mobile phone network for internet access.
a reply to: pheonix358
Being that they are using Corporate owned OS, services, and hardware manufactured in foreign countries, all that will do is give them a false sense of security.
Surely though, it is a massive overkill. Dump the hard drives and re-install the O/S and Bios for a clean slate. Would be a lot cheaper.
Being that they are using Corporate owned OS, services, and hardware manufactured in foreign countries, all that will do is give them a false sense of security.
a reply to: interupt42
Let´s buy new hardware and make sure it´s cottonmouthed...
BADUSB exploit/ USBexploit in common....You left one device, one stick and the # begins again.
DUH this is embarassing. You would think here in Germany with all the technology we could have some decent IT guys watching over this. Then the scandal with the mobile phones. I feel like I´m dreaming, never would have believed that our gorvernment, who should know better, can mess it up like that. Almost sounds intentionally.....
Edit; I heard on radio, I think it was last week that there were still pakets flowing out and that they can do nothing about it.
In an event like this, cut the #ing cables for god sake. What is more evil, taking down the bundestag network for 2-3 days fixing and finding the issue or let valuable secret data flow out.
Let´s buy new hardware and make sure it´s cottonmouthed...
BADUSB exploit/ USBexploit in common....You left one device, one stick and the # begins again.
DUH this is embarassing. You would think here in Germany with all the technology we could have some decent IT guys watching over this. Then the scandal with the mobile phones. I feel like I´m dreaming, never would have believed that our gorvernment, who should know better, can mess it up like that. Almost sounds intentionally.....
Edit; I heard on radio, I think it was last week that there were still pakets flowing out and that they can do nothing about it.
In an event like this, cut the #ing cables for god sake. What is more evil, taking down the bundestag network for 2-3 days fixing and finding the issue or let valuable secret data flow out.
edit on 17-6-2015 by verschickter because: (no reason given)
a reply to: verschickter
The problem is far worse than that. The issue is not leaving one contaminated device , but rather gov't agencies using foreign manufactured electronic devices with sensitive systems. That makes all the devices suspect.
Who is to say that the foreign manufacture of the chips and components didn't put in back doors at the hardware level? This is a rather large complex problem that is often overlooked .
You left one device, one stick and the # begins again.
The problem is far worse than that. The issue is not leaving one contaminated device , but rather gov't agencies using foreign manufactured electronic devices with sensitive systems. That makes all the devices suspect.
Who is to say that the foreign manufacture of the chips and components didn't put in back doors at the hardware level? This is a rather large complex problem that is often overlooked .
a reply to: interupt42
My first sentences. You should have read it to the end.
Google cottonmouth for example. It describes what you want to teach me.
You are welcome.
My first sentences. You should have read it to the end.
Google cottonmouth for example. It describes what you want to teach me.

You are welcome.
edit on 17-6-2015 by verschickter because: (no reason given)
a reply to: verschickter
Wasn't trying to teach, and reread my post where I say its worse than just a device being comprised like a USB .
My point is that the system are far more compromised than just with a USB exploits such as the cottonmouth exploit. The system themselves even without any USB ports could likely be compromised at the motherboard, chip, and other electronic components level. It would be difficult to catch a back door at the hardware level that are designed within manufacturers quality specifications.
Wasn't trying to teach, and reread my post where I say its worse than just a device being comprised like a USB .
My point is that the system are far more compromised than just with a USB exploits such as the cottonmouth exploit. The system themselves even without any USB ports could likely be compromised at the motherboard, chip, and other electronic components level. It would be difficult to catch a back door at the hardware level that are designed within manufacturers quality specifications.
edit on 38630America/ChicagoWed, 17 Jun 2015 12:38:24 -0500000000p3042 by interupt42 because: (no reason given)
a reply to: interupt42
I did not exclude them. Just buy a company that manufactures usb soldering racks and start shipping out. Nearly every computer (that would be a valuable target, except maybe machines used for nuclear affairs) on this world has USB aviable in some version and if not you can use this machine as a bridge.
If you think I´m not aware of the samsung scandal
or if you think I would discard something like that
or did not come to that conclusion myself, you might chance your way of thinking.
Do you think someone who´s into badusb would not know that?
Funny
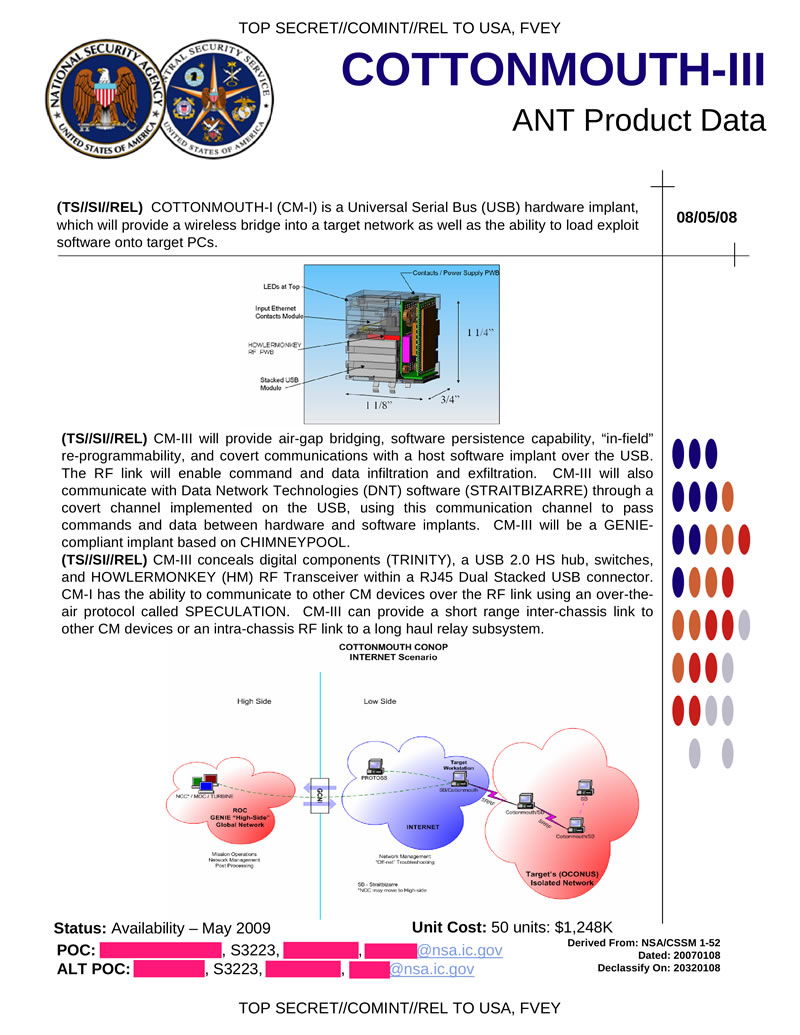
BTW it´s not "the cottonmouth exploit". Cottonmouth is a modified rack with a wifi bridge. The controller on that rack is modified to load a certain driver that uses a vulnerability in the USB protocol that is exploited (now named badusb, had other names before it went public like now. There is no easier way getting into a system if you have that. You don´t need the machine to be on a network. You have your own RF connection to it.
I did not exclude them. Just buy a company that manufactures usb soldering racks and start shipping out. Nearly every computer (that would be a valuable target, except maybe machines used for nuclear affairs) on this world has USB aviable in some version and if not you can use this machine as a bridge.
If you think I´m not aware of the samsung scandal
or if you think I would discard something like that
or did not come to that conclusion myself, you might chance your way of thinking.
Do you think someone who´s into badusb would not know that?
Funny
BTW it´s not "the cottonmouth exploit". Cottonmouth is a modified rack with a wifi bridge. The controller on that rack is modified to load a certain driver that uses a vulnerability in the USB protocol that is exploited (now named badusb, had other names before it went public like now. There is no easier way getting into a system if you have that. You don´t need the machine to be on a network. You have your own RF connection to it.
edit
on 17-6-2015 by verschickter because: (no reason given)
a reply to: verschickter
There has been alien technology in the water since 4X17.

Intel sky lake, which lake?
There has been alien technology in the water since 4X17.

Intel sky lake, which lake?
new topics
-
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 18 minutes ago -
God lived as a Devil Dog.
Short Stories: 34 minutes ago -
Happy St George's day you bigots!
Breaking Alternative News: 2 hours ago -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 3 hours ago -
Hate makes for strange bedfellows
US Political Madness: 5 hours ago -
Who guards the guards
US Political Madness: 7 hours ago -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 9 hours ago
top topics
-
Hate makes for strange bedfellows
US Political Madness: 5 hours ago, 14 flags -
whistleblower Captain Bill Uhouse on the Kingman UFO recovery
Aliens and UFOs: 14 hours ago, 11 flags -
Who guards the guards
US Political Madness: 7 hours ago, 10 flags -
1980s Arcade
General Chit Chat: 16 hours ago, 7 flags -
Deadpool and Wolverine
Movies: 17 hours ago, 4 flags -
TLDR post about ATS and why I love it and hope we all stay together somewhere
General Chit Chat: 3 hours ago, 3 flags -
Has Tesla manipulated data logs to cover up auto pilot crash?
Automotive Discussion: 9 hours ago, 2 flags -
Happy St George's day you bigots!
Breaking Alternative News: 2 hours ago, 2 flags -
God lived as a Devil Dog.
Short Stories: 34 minutes ago, 1 flags -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People: 18 minutes ago, 0 flags
active topics
-
God lived as a Devil Dog.
Short Stories • 1 • : FlyersFan -
Republican Voters Against Trump
2024 Elections • 285 • : Annee -
Happy St George's day you bigots!
Breaking Alternative News • 13 • : BedevereTheWise -
"We're All Hamas" Heard at Columbia University Protests
Social Issues and Civil Unrest • 243 • : FlyersFan -
Candidate TRUMP Now Has Crazy Judge JUAN MERCHAN After Him - The Stormy Daniels Hush-Money Case.
Political Conspiracies • 725 • : Justoneman -
SC Jack Smith is Using Subterfuge Tricks with Donald Trumps Upcoming Documents Trial.
Dissecting Disinformation • 108 • : Threadbarer -
So this is what Hamas considers 'freedom fighting' ...
War On Terrorism • 226 • : FlyersFan -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 616 • : cherokeetroy -
Geddy Lee in Conversation with Alex Lifeson - My Effin’ Life
People • 0 • : gortex -
British TV Presenter Refuses To Use Guest's Preferred Pronouns
Education and Media • 114 • : Annee
2
