It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
0
share:
A security researcher told the FBI in February he was able to commandeer a plane's control system mid-flight, according to a warrant application filed last month.
Source

Chris Roberts is a prominent hacker and security researcher. He founded One World Labs, a security intelligence firm that identifies risks before they’re exploited. While aboard a United airlines flight, he tweeted this...
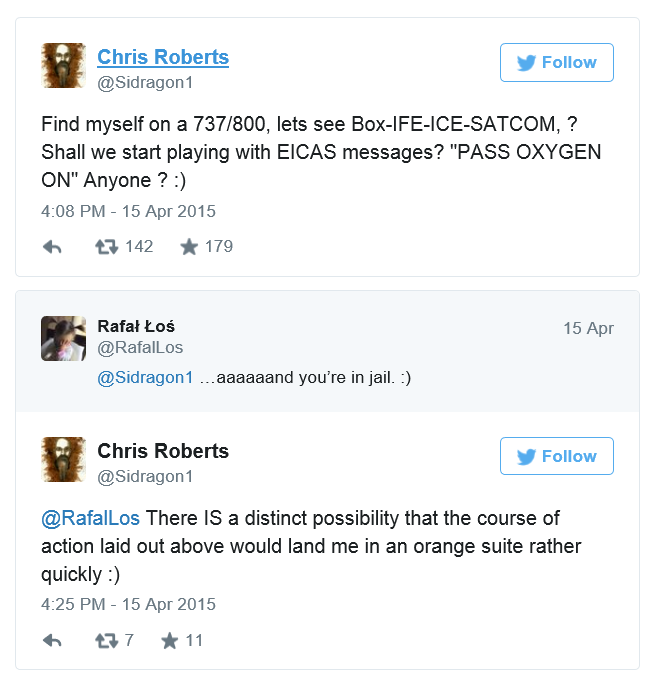
The tweet was meant as a sarcastic joke; a reference to how he had tried for years to get Boeing and Airbus to heed warnings about security issues with their passenger communications systems. His tweet about the Engine Indicator Crew Alert System, or EICAS, was a reference to research he’d done years ago on vulnerabilities in inflight infotainment networks, vulnerabilities that could allow an attacker to access cabin controls and deploy a plane’s oxygen masks.
While it may sound funny, he claims to have accessed the plane’s IFE systems which then gave him access to other systems using default IDs and passwords.
He obtained physical access to the networks through the Seat Electronic Box, or SEB. These are installed two to a row, on each side of the aisle under passenger seats, on certain planes. After removing the cover to the SEB by “wiggling and Squeezing the box,” Roberts told agents he attached a Cat6 ethernet cable, with a modified connector, to the box and to his laptop and then used default IDs and passwords to gain access to the inflight entertainment system. Once on that network, he was able to gain access to other systems on the planes.
Upon landing, he was detained by two FBI agents and local police for questioning. Below is what the they reportedly confiscated. The FBI filed for a warrant two days after questioning Mr. Roberts.

The FBI is directly accusing him of controlling the airplane by overwriting code on the plane’s Thrust Management Computer, acknowledging that it is indeed possible. Robert claims he only caused the plane to climb during a simulated test on a virtual environment he built with a colleague. He says he did access in-flight networks about 15 times during various flights between 2011 and 2014, but had only explored and observed the data traffic.
“He stated that he thereby caused one of the airplane engines to climb resulting in a lateral or sideways movement of the plane during one of these flights,” FBI Special Agent Mark Hurley wrote in his warrant application. “He also stated that he used Vortex software after comprising/exploiting or ‘hacking’ the airplane’s networks. He used the software to monitor traffic from the cockpit system.”
Roberts has not yet been charged with any crime while the warrant to search his property is pending. The FBI is hoping to find hard evidence of his involvement in altering the plane's flight control systems. I tend to believe his public display is being used to draw attention to the issue. Are we really that vulnerable?
Roberts began investigating aviation security about six years ago after he and a research colleague got hold of publicly available flight manuals and wiring diagrams for various planes. The documents showed how inflight entertainment systems one some planes were connected to the passenger satellite phone network, which included functions for operating some cabin control systems. These systems were in turn connected to the plane avionics systems. They built a test lab using demo software obtained from infotainment vendors and others in order to explore what they could to the networks.
In 2010, Roberts gave a presentation about hacking planes and cars at the BSides security conference in Las Vegas. Another presentation followed two years later. He also spoke directly to airplane manufacturers about the problems with their systems. “We had conversations with two main airplane builders as well as with two of the top providers of infotainment systems and it never went anywhere,” he told WIRED last month.
Last February, the FBI in Denver, where Roberts is based, requested a meeting. They discussed his research for an hour, and returned a couple weeks later for a discussion that lasted several more hours. They wanted to know what was possible and what exactly he and his colleague had done. Roberts disclosed that he and his colleague had sniffed the data traffic on more than a dozen flights after connecting their laptops to the infotainment networks.
“We researched further than that,” he told WIRED last month. “We were within the fuel balancing system and the thrust control system. We watched the packets and data going across the network to see where it was going.”
Eventually, Roberts and his research partner determined that it would take a convoluted set of hacks to seriously subvert an avionics system, but they believed it could be done. He insisted to WIRED last month, however, that they did not “mess around with that except on simulation systems.” In simulations, for example, Roberts said they were able to turn the engine controls from cruise to climb, “which definitely had the desired effect on the system—the plane sped up and the nose of the airplane went up.”
This guy seems to think so. He is refusing to comment about the FBI’s accusations and I will definitely be keeping watch as this develops. Airplanes were used to bring this country to it’s knees and other strange occurrences have happened as of late. These vulnerabilities have been known for years and the airline manufactures have chosen to do nothing about them. Any guess why?
His Twitter page: Link
edit on 17-5-2015 by eisegesis because: (no reason given)
new topics
-
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events: 14 minutes ago -
12 jurors selected in Trump criminal trial
US Political Madness: 2 hours ago -
Iran launches Retalliation Strike 4.18.24
World War Three: 3 hours ago -
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three: 3 hours ago -
George Knapp AMA on DI
Area 51 and other Facilities: 9 hours ago -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs: 9 hours ago -
Louisiana Lawmakers Seek to Limit Public Access to Government Records
Political Issues: 11 hours ago
0
