It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Bougess !
The FBI NSA are just saying this
so you will go back to thinking you are safe.
you are NOT.
they are still watching you.
all you do and all the time.
The FBI NSA are just saying this
so you will go back to thinking you are safe.
you are NOT.
they are still watching you.
all you do and all the time.
Do not even for a second think that the FBI cannot get information from your smartphone (android or IOS). Trust me, the FBI, NSA, CIA or any other
alphabet name can access your information if needed.
The claim that your information is "encrypted" to a level that the FBI cannot gain access is a flat LIE. Period.
The claim that your information is "encrypted" to a level that the FBI cannot gain access is a flat LIE. Period.
originally posted by: Wolvesandsheeple
Joke of a reporter
Check out this whiney reporter. I love how any time the people in charge want to trample all over us, they start shouting "terrorism" and "think of the children". Of course, he MUST mention crimes against children, or else this whiney piece of "reporting" would not be complete.
I also find it hilarious how he places his full trust and faith in Congress to protect our rights ro privacy.
What a sham!
If you look at the comments it is a good indication of people waking up to this garbage.
Wolves and Sheeple
He's not a reporter at all. That was written by Cyrus Vance, Jr, son of Cyrus Vance the failure of a Secretary of State under Jimmy Carter. I may be related to them, but if it's ever confirmed I will deny it, and so will they. His daddy quit his day job as Secretary of State over the failed hostage rescue mission in Iran in 1980. His emphasis was on talking things out - maybe he wanted to bore the opposition to death.
It looks like his son ain't no brighter.
I particularly liked this passage from the article:
While these maneuvers may be a welcome change for those who seek greater privacy controls, the unintended victors will ultimately be criminals, who are now free to hide evidence on their phones despite valid warrants to search them.
"What's that? you have a valid warrant to search you say? Well have at it, then! Huh? You ran across something you can't decrypt? How's that MY problem? I'm not the one searching, YOU are - get to it! After all, it's YOUR job - don't ask me to do it for you, 'cause I ain't getting paid for it, and you have a valid warrant to search - not to discover!"
He goes on to bemoan the fact that personal privacy is enshrined in the constitution - and that ought to be enough, according to Mr. Vance. In a perfect world, it would be, but beyond the fact that we have always had to safeguard our OWN constitutional rights, the current trend in casual violation of those rights calls for something stricter to be wielded by the populace, something that will aid them in enforcing those rights, and encryption fits that bill. I have seen search warrants served with my own eyes that were not completely filled out until AFTER the search, when they knew what it was they wanted to put on the warrant to satisfy the Rule of Particularities. Furthermore, judges and magistrates routinely issue rubber-stamp warrants, so merely requiring a warrant is no longer a safeguard to privacy.
Cyrus Vance Jr., in common with most of his ilk, is not against personal privacy per se - he's only against YOURS, and mine.
originally posted by: nenothtu
No, not in the US.
Here we have that 4th Amendment problem preventing illegal search and seizure, compounded with the 5th Amendment, preventing compulsion of testimony concerning your self. They can obtain a warrant to seize any papers and effects, but cannot obtain a warrant to force you to speak. If the passphrase is memorized and never written down anywhere, then it's in your head, and the only way to get it out is to force you to speak, which is constitutionally prohibited.
Oh, they can browbeat and promise all kinds of dire consequences if you don't, but where the rubber meets the road, they can't force you to speak at all. If you stand firm, they are bound, gagged, and stymied. If you open your mouth and lie to them, however...
There have actually been several court cases in the US about this issue and the courts have come down 50/50, some of them will jail you on contempt until you hand over the password. The solution is to do the same thing the people in the UK do which is to create a hidden partition with TrueCrypt that has the real data, and a fake one that just looks like stuff you wanted to keep secret. They can force you to turn over a password, but if you do and they don't find anything they can't compel you to turn over the second password unless they happen to know it's there.
a reply to: Aazadan
I've done that, and it works wonders - but these days, I intend to force a Constitutional issue (to get it settled by the Supremes, and straight in EVERYBODY'S head so the 50/50 thing isn't a problem any more - everyone will know just where they stand) if that game is ever run on me again, so the plausible deniability partition within a partition isn't as much of a draw for me. I can see why people in the UK, as well as activists in the "rubber hose interrogatory" countries would use it quite a lot.
I use a passphrase between 36 and 48 characters long, has every sort of character thrown into it, and a complex memorization scheme to keep the apparently "random" string straight in my head. Sometimes that scheme is a little TOO complex, however, memory fails me, and I can't get into my own stuff. Thank God that I haven't forgotten the passphrase for grandma's Top Secret Chocolate Chip Cookie Recipe! On the other hand, all of the missile codes for Cheyenne Mountain are entirely lost to posterity now...
I've done that, and it works wonders - but these days, I intend to force a Constitutional issue (to get it settled by the Supremes, and straight in EVERYBODY'S head so the 50/50 thing isn't a problem any more - everyone will know just where they stand) if that game is ever run on me again, so the plausible deniability partition within a partition isn't as much of a draw for me. I can see why people in the UK, as well as activists in the "rubber hose interrogatory" countries would use it quite a lot.
I use a passphrase between 36 and 48 characters long, has every sort of character thrown into it, and a complex memorization scheme to keep the apparently "random" string straight in my head. Sometimes that scheme is a little TOO complex, however, memory fails me, and I can't get into my own stuff. Thank God that I haven't forgotten the passphrase for grandma's Top Secret Chocolate Chip Cookie Recipe! On the other hand, all of the missile codes for Cheyenne Mountain are entirely lost to posterity now...
edit on 2014/10/2 by nenothtu because: (no reason given)
originally posted by: nenothtu
a reply to: Aazadan
I've done that, and it works wonders - but these days, I intend to force a Constitutional issue (to get it settled by the Supremes, and straight in EVERYBODY'S head so the 50/50 thing isn't a problem any more - everyone will know just where they stand) if that game is ever run on me again, so the plausible deniability partition within a partition isn't as much of a draw for me. I can see why people in the UK, as well as activists in the "rubber hose interrogatory" countries would use it quite a lot.
I use a passphrase between 36 and 48 characters long, has every sort of character thrown into it, and a complex memorization scheme to keep the apparently "random" string straight in my head. Sometimes that scheme is a little TOO complex, however, memory fails me, and I can't get into my own stuff. Thank God that I haven't forgotten the passphrase for grandma's Top Secret Chocolate Chip Cookie Recipe! On the other hand, all of the missile codes for Cheyenne Mountain are entirely lost to posterity now...
If I had the money I think I would intentionally break the law and force the issue. Whether or not it gets to the Supreme Court isn't for me to say (many worthy cases don't get heard), but I assure you it would reach atleast the state level on appeals.
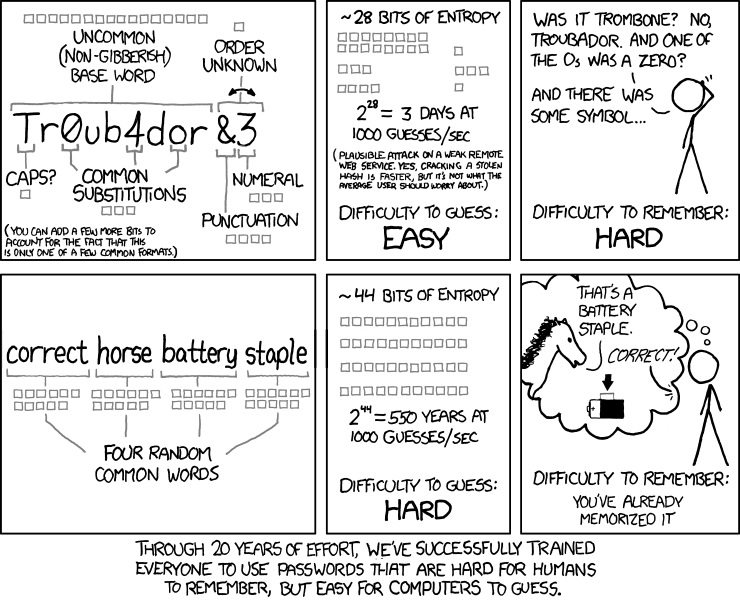
I know where you're coming from with the pass phrase but you have to be careful about getting too complex with the passphrase. To a computer abc123 and jqp720 are equally difficult but one is significantly easier than the other for a human to remember, similarly abcdefghijklmnopqrstuvwxyz and rfjtkadjfolakijgfoeajfgdkl are the same difficulty. The only difference is that one comes before the other alphabetically which means one will be solved sooner in certain algorithms.
With enough degrees of entropy the challenge isn't to fool a computer... computers are very exploitable. The challenge is to fool a human that writes a modified dictionary or to avoid being coerced into giving up the password. With any good password the person who knows it is the weak link, not the password itself.
new topics
-
Electrical tricks for saving money
Education and Media: 58 minutes ago -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 2 hours ago -
Sunak spinning the sickness figures
Other Current Events: 2 hours ago -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 3 hours ago -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 4 hours ago -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 6 hours ago -
The Good News According to Jesus - Episode 1
Religion, Faith, And Theology: 8 hours ago -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 10 hours ago
top topics
-
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs: 17 hours ago, 8 flags -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest: 6 hours ago, 8 flags -
Florida man's trip overseas ends in shock over $143,000 T-Mobile phone bill
Social Issues and Civil Unrest: 13 hours ago, 8 flags -
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News: 2 hours ago, 7 flags -
Former Labour minister Frank Field dies aged 81
People: 15 hours ago, 4 flags -
Bobiverse
Fantasy & Science Fiction: 13 hours ago, 3 flags -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three: 10 hours ago, 3 flags -
Nearly 70% Of Americans Want Talks To End War In Ukraine
Political Issues: 3 hours ago, 3 flags -
Sunak spinning the sickness figures
Other Current Events: 2 hours ago, 3 flags -
Late Night with the Devil - a really good unusual modern horror film.
Movies: 4 hours ago, 2 flags
active topics
-
VP's Secret Service agent brawls with other agents at Andrews
Mainstream News • 19 • : NoCorruptionAllowed -
VirginOfGrand says hello
Introductions • 5 • : burritocat -
The Reality of the Laser
Military Projects • 44 • : Zaphod58 -
SETI chief says US has no evidence for alien technology. 'And we never have'
Aliens and UFOs • 42 • : Boomer1947 -
NASA Researchers Discover a Parallel Universe That Runs Backwards through Time - Alongside Us
Space Exploration • 71 • : charlyv -
Sunak spinning the sickness figures
Other Current Events • 4 • : annonentity -
Cats Used as Live Bait to Train Ferocious Pitbulls in Illegal NYC Dogfighting
Social Issues and Civil Unrest • 12 • : Hakaiju -
HORRIBLE !! Russian Soldier Drinking Own Urine To Survive In Battle
World War Three • 28 • : budzprime69 -
Huge ancient city found in the Amazon.
Ancient & Lost Civilizations • 61 • : Therealbeverage -
Should Biden Replace Harris With AOC On the 2024 Democrat Ticket?
2024 Elections • 49 • : Therealbeverage